About the Execution of ITS-Tools for LeafsetExtension-PT-S08C2
| Execution Summary | |||||
| Max Memory Used (MB) |
Time wait (ms) | CPU Usage (ms) | I/O Wait (ms) | Computed Result | Execution Status |
| 3139.672 | 448057.00 | 399968.00 | 28343.60 | TTFFFFTTTFTTFFTF | normal |
Execution Chart
We display below the execution chart for this examination (boot time has been removed).
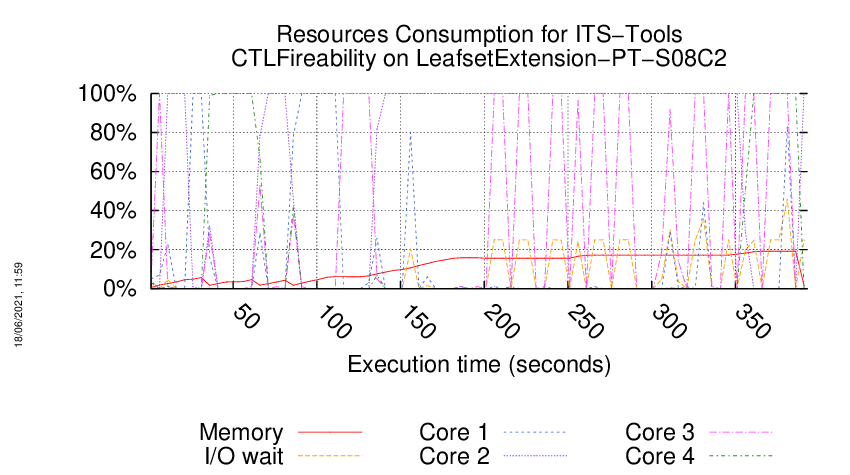
Trace from the execution
Formatting '/data/fkordon/mcc2021-input.r292-tall-162124156500474.qcow2', fmt=qcow2 size=4294967296 backing_file='/data/fkordon/mcc2021-input.qcow2' encryption=off cluster_size=65536 lazy_refcounts=off
Waiting for the VM to be ready (probing ssh)
..............................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................
=====================================================================
Generated by BenchKit 2-4028
Executing tool itstools
Input is LeafsetExtension-PT-S08C2, examination is CTLFireability
Time confinement is 3600 seconds
Memory confinement is 16384 MBytes
Number of cores is 4
Run identifier is r292-tall-162124156500474
=====================================================================
--------------------
preparation of the directory to be used:
/home/mcc/execution
total 1.1M
-rw-r--r-- 1 mcc users 31K May 15 08:57 CTLCardinality.txt
-rw-r--r-- 1 mcc users 122K May 15 08:57 CTLCardinality.xml
-rw-r--r-- 1 mcc users 34K May 15 08:57 CTLFireability.txt
-rw-r--r-- 1 mcc users 121K May 15 08:57 CTLFireability.xml
-rw-r--r-- 1 mcc users 6.0K May 12 07:58 LTLCardinality.txt
-rw-r--r-- 1 mcc users 29K May 12 07:58 LTLCardinality.xml
-rw-r--r-- 1 mcc users 3.6K May 12 07:58 LTLFireability.txt
-rw-r--r-- 1 mcc users 18K May 12 07:58 LTLFireability.xml
-rw-r--r-- 1 mcc users 1 May 12 08:13 NewModel
-rw-r--r-- 1 mcc users 5.4K May 11 18:43 ReachabilityCardinality.txt
-rw-r--r-- 1 mcc users 21K May 11 18:43 ReachabilityCardinality.xml
-rw-r--r-- 1 mcc users 4.5K May 11 15:49 ReachabilityFireability.txt
-rw-r--r-- 1 mcc users 17K May 11 15:49 ReachabilityFireability.xml
-rw-r--r-- 1 mcc users 1.8K May 12 04:40 UpperBounds.txt
-rw-r--r-- 1 mcc users 3.8K May 12 04:40 UpperBounds.xml
-rw-r--r-- 1 mcc users 6 May 12 08:13 equiv_col
-rw-r--r-- 1 mcc users 6 May 12 08:13 instance
-rw-r--r-- 1 mcc users 6 May 12 08:13 iscolored
-rw-r--r-- 1 mcc users 647K May 12 08:13 model.pnml
--------------------
content from stdout:
=== Data for post analysis generated by BenchKit (invocation template)
The expected result is a vector of booleans
BOOL_VECTOR
here is the order used to build the result vector(from text file)
FORMULA_NAME LeafsetExtension-PT-S08C2-CTLFireability-00
FORMULA_NAME LeafsetExtension-PT-S08C2-CTLFireability-01
FORMULA_NAME LeafsetExtension-PT-S08C2-CTLFireability-02
FORMULA_NAME LeafsetExtension-PT-S08C2-CTLFireability-03
FORMULA_NAME LeafsetExtension-PT-S08C2-CTLFireability-04
FORMULA_NAME LeafsetExtension-PT-S08C2-CTLFireability-05
FORMULA_NAME LeafsetExtension-PT-S08C2-CTLFireability-06
FORMULA_NAME LeafsetExtension-PT-S08C2-CTLFireability-07
FORMULA_NAME LeafsetExtension-PT-S08C2-CTLFireability-08
FORMULA_NAME LeafsetExtension-PT-S08C2-CTLFireability-09
FORMULA_NAME LeafsetExtension-PT-S08C2-CTLFireability-10
FORMULA_NAME LeafsetExtension-PT-S08C2-CTLFireability-11
FORMULA_NAME LeafsetExtension-PT-S08C2-CTLFireability-12
FORMULA_NAME LeafsetExtension-PT-S08C2-CTLFireability-13
FORMULA_NAME LeafsetExtension-PT-S08C2-CTLFireability-14
FORMULA_NAME LeafsetExtension-PT-S08C2-CTLFireability-15
=== Now, execution of the tool begins
BK_START 1621299064673
Running Version 0
[2021-05-18 00:51:06] [INFO ] Running its-tools with arguments : [-pnfolder, /home/mcc/execution, -examination, CTLFireability, -spotpath, /home/mcc/BenchKit/bin//..//ltlfilt, -z3path, /home/mcc/BenchKit/bin//..//z3/bin/z3, -yices2path, /home/mcc/BenchKit/bin//..//yices/bin/yices, -its, -ltsmin, -greatspnpath, /home/mcc/BenchKit/bin//..//greatspn/, -order, META, -manyOrder, -smt, -timeout, 3600]
[2021-05-18 00:51:06] [INFO ] Parsing pnml file : /home/mcc/execution/model.pnml
[2021-05-18 00:51:06] [INFO ] Load time of PNML (sax parser for PT used): 86 ms
[2021-05-18 00:51:06] [INFO ] Transformed 462 places.
[2021-05-18 00:51:06] [INFO ] Transformed 409 transitions.
[2021-05-18 00:51:06] [INFO ] Parsed PT model containing 462 places and 409 transitions in 139 ms.
Parsed 16 properties from file /home/mcc/execution/CTLFireability.xml in 14 ms.
Support contains 318 out of 462 places. Attempting structural reductions.
Starting structural reductions, iteration 0 : 462/462 places, 409/409 transitions.
Reduce places removed 85 places and 0 transitions.
Iterating post reduction 0 with 85 rules applied. Total rules applied 85 place count 377 transition count 409
Discarding 7 places :
Symmetric choice reduction at 1 with 7 rule applications. Total rules 92 place count 370 transition count 402
Iterating global reduction 1 with 7 rules applied. Total rules applied 99 place count 370 transition count 402
Applied a total of 99 rules in 30 ms. Remains 370 /462 variables (removed 92) and now considering 402/409 (removed 7) transitions.
// Phase 1: matrix 402 rows 370 cols
[2021-05-18 00:51:07] [INFO ] Computed 30 place invariants in 30 ms
[2021-05-18 00:51:07] [INFO ] Implicit Places using invariants in 199 ms returned []
// Phase 1: matrix 402 rows 370 cols
[2021-05-18 00:51:07] [INFO ] Computed 30 place invariants in 12 ms
[2021-05-18 00:51:07] [INFO ] Implicit Places using invariants and state equation in 240 ms returned []
Implicit Place search using SMT with State Equation took 468 ms to find 0 implicit places.
// Phase 1: matrix 402 rows 370 cols
[2021-05-18 00:51:07] [INFO ] Computed 30 place invariants in 17 ms
[2021-05-18 00:51:07] [INFO ] Dead Transitions using invariants and state equation in 222 ms returned []
Finished structural reductions, in 1 iterations. Remains : 370/462 places, 402/409 transitions.
[2021-05-18 00:51:08] [INFO ] Flatten gal took : 61 ms
[2021-05-18 00:51:08] [INFO ] Flatten gal took : 33 ms
[2021-05-18 00:51:08] [INFO ] Input system was already deterministic with 402 transitions.
Finished random walk after 6576 steps, including 354 resets, run visited all 106 properties in 51 ms. (steps per millisecond=128 )
Drop transitions removed 34 transitions
Trivial Post-agglo rules discarded 34 transitions
Performed 34 trivial Post agglomeration. Transition count delta: 34
Iterating post reduction 0 with 34 rules applied. Total rules applied 34 place count 370 transition count 368
Reduce places removed 34 places and 0 transitions.
Performed 57 Post agglomeration using F-continuation condition.Transition count delta: 57
Iterating post reduction 1 with 91 rules applied. Total rules applied 125 place count 336 transition count 311
Reduce places removed 57 places and 0 transitions.
Iterating post reduction 2 with 57 rules applied. Total rules applied 182 place count 279 transition count 311
Performed 8 Pre agglomeration using Quasi-Persistent + Divergent Free condition..
Pre-agglomeration after 3 with 8 Pre rules applied. Total rules applied 182 place count 279 transition count 303
Deduced a syphon composed of 8 places in 1 ms
Reduce places removed 8 places and 0 transitions.
Iterating global reduction 3 with 16 rules applied. Total rules applied 198 place count 271 transition count 303
Discarding 28 places :
Symmetric choice reduction at 3 with 28 rule applications. Total rules 226 place count 243 transition count 275
Iterating global reduction 3 with 28 rules applied. Total rules applied 254 place count 243 transition count 275
Discarding 3 places :
Symmetric choice reduction at 3 with 3 rule applications. Total rules 257 place count 240 transition count 272
Iterating global reduction 3 with 3 rules applied. Total rules applied 260 place count 240 transition count 272
Performed 3 Post agglomeration using F-continuation condition.Transition count delta: 3
Deduced a syphon composed of 3 places in 0 ms
Reduce places removed 3 places and 0 transitions.
Iterating global reduction 3 with 6 rules applied. Total rules applied 266 place count 237 transition count 269
Discarding 5 places :
Symmetric choice reduction at 3 with 5 rule applications. Total rules 271 place count 232 transition count 264
Iterating global reduction 3 with 5 rules applied. Total rules applied 276 place count 232 transition count 264
Discarding 2 places :
Symmetric choice reduction at 3 with 2 rule applications. Total rules 278 place count 230 transition count 262
Iterating global reduction 3 with 2 rules applied. Total rules applied 280 place count 230 transition count 262
Applied a total of 280 rules in 93 ms. Remains 230 /370 variables (removed 140) and now considering 262/402 (removed 140) transitions.
[2021-05-18 00:51:08] [INFO ] Flatten gal took : 14 ms
[2021-05-18 00:51:08] [INFO ] Flatten gal took : 19 ms
[2021-05-18 00:51:08] [INFO ] Input system was already deterministic with 262 transitions.
[2021-05-18 00:51:08] [INFO ] Flatten gal took : 16 ms
[2021-05-18 00:51:08] [INFO ] Flatten gal took : 14 ms
[2021-05-18 00:51:08] [INFO ] Time to serialize gal into /tmp/CTLFireability2061825213298959641.gal : 11 ms
[2021-05-18 00:51:08] [INFO ] Time to serialize properties into /tmp/CTLFireability3157811293925003875.ctl : 1 ms
Invoking ITS tools like this :CommandLine [args=[/home/mcc/BenchKit/itstools/plugins/fr.lip6.move.gal.itstools.binaries_1.0.0.202104292328/bin/its-ctl-linux64, --gc-threshold, 2000000, --quiet, -i, /tmp/CTLFireability2061825213298959641.gal, -t, CGAL, -ctl, /tmp/CTLFireability3157811293925003875.ctl, --gen-order, FOLLOW], workingDir=/home/mcc/execution]
its-ctl command run as :
/home/mcc/BenchKit/itstools/plugins/fr.lip6.move.gal.itstools.binaries_1.0.0.202104292328/bin/its-ctl-linux64 --gc-threshold 2000000 --quiet -i /tmp/CTLFireability2061825213298959641.gal -t CGAL -ctl /tmp/CTLFireability3157811293925003875.ctl --gen-order FOLLOW
No direction supplied, using forward translation only.
Parsed 1 CTL formulae.
Model ,|S| ,Time ,Mem(kb) ,fin. SDD ,fin. DDD ,peak SDD ,peak DDD ,SDD Hom ,SDD cache peak ,DDD Hom ,DDD cachepeak ,SHom cache
reachable,46981,1.55897,60148,2,23242,5,177161,6,0,1172,282570,0
Converting to forward existential form...Done !
original formula: AF((!(A(((((((((((((Node5HasAskedItsLeafSetToRxToReplaceNode8>=1)&&(LeafSetOfRxIsSentToNode5>=1))||(Node3HasTheLeafSetOfLxToReplaceNode2>=1))||((Node0IsActive>=1)&&(Node4DontAnswerToAnyNode>=1)))||((Node1WantsToManageTheBreakDownOfNode7>=1)&&(NoNodeManageTheBreakDownOfNode7>=1)))||((Node3IsActive>=1)&&(Node8DontAnswerToAnyNode>=1)))||((Node2WantsToManageTheBreakDownOfNode3>=1)&&(NoNodeManageTheBreakDownOfNode3>=1)))||(Node7HasTheLeafSetOfRxToReplaceNode8>=1))||((Node0IsActive>=1)&&(Node7DontAnswerToAnyNode>=1)))||(Node6HasTheLeafSetOfLxToReplaceNode0>=1))||((BreakDownReservoir>=1)&&(Node6IsActive>=1))) * EF(((((((((((Node3ManageTheBreakDownOfNode7>=1)||((RequestOfNode4IsSentToLx>=1)&&(LxIsActiveAndNotInTheLeafSet>=1)))||((Node3IsActive>=1)&&(Node7DontAnswerToAnyNode>=1)))||(Node4HasTheLeafSetOfRxToReplaceNode7>=1))||(Node7HasTheLeafSetOfLxToReplaceNode2>=1))||((NoNodeManageTheBreakDownOfNode2>=1)&&(Node7WantsToManageTheBreakDownOfNode2>=1)))||(Node8HasTheLeafSetOfLxToReplaceNode1>=1))||((Node1HasAskedItsLeafSetToRxToReplaceNode7>=1)&&(LeafSetOfRxIsSentToNode1>=1)))||(Node3HasTheLeafSetOfRxToReplaceNode5>=1))||((Node4DontAnswerToAnyNode>=1)&&(Node5IsActive>=1))))) U (AF(((((((((((Node0WantsToManageTheBreakDownOfNode3>=1)&&(NoNodeManageTheBreakDownOfNode3>=1))||((Node2IsActive>=1)&&(Node6DontAnswerToAnyNode>=1)))||((Node3WantsToManageTheBreakDownOfNode5>=1)&&(NoNodeManageTheBreakDownOfNode5>=1)))||((Node3HasAskedItsLeafSetToRxToReplaceNode7>=1)&&(LeafSetOfRxIsSentToNode3>=1)))||(Node3HasTheLeafSetOfRxToReplaceNode6>=1))||((Node1DontAnswerToAnyNode>=1)&&(Node7IsActive>=1)))||((NoNodeManageTheBreakDownOfNode0>=1)&&(Node4WantsToManageTheBreakDownOfNode0>=1)))||((Node4IsActive>=1)&&(Node8DontAnswerToAnyNode>=1)))||((NoNodeManageTheBreakDownOfNode3>=1)&&(Node4WantsToManageTheBreakDownOfNode3>=1)))) + A(((((((((((RequestOfNode2IsSentToRx>=1)&&(RxIsActiveAndNotInTheLeafSet>=1))||((Node2WantsToManageTheBreakDownOfNode6>=1)&&(NoNodeManageTheBreakDownOfNode6>=1)))||((RequestOfNode4IsSentToLx>=1)&&(LxIsActiveAndNotInTheLeafSet>=1)))||((Node3HasAskedItsLeafSetToLxToReplaceNode1>=1)&&(LeafSetOfLxIsSentToNode3>=1)))||((Node2HasAskedItsLeafSetToRxToReplaceNode5>=1)&&(LeafSetOfRxIsSentToNode2>=1)))||((Node5DontAnswerToAnyNode>=1)&&(Node8IsActive>=1)))||(Node0ManageTheBreakDownOfNode2>=1))||((Node0DontAnswerToAnyNode>=1)&&(Node5IsActive>=1)))||((Node4HasAskedItsLeafSetToRxToReplaceNode6>=1)&&(LeafSetOfRxIsSentToNode4>=1))) U ((Node0IsActive>=1)&&(Node4DontAnswerToAnyNode>=1)))))) * (A((((Node3ManageTheBreakDownOfNode0>=1)||((Node6HasAskedItsLeafSetToLxToReplaceNode3>=1)&&(LeafSetOfLxIsSentToNode6>=1)))&&((((((((((NoNodeManageTheBreakDownOfNode7>=1)&&(Node8WantsToManageTheBreakDownOfNode7>=1))||((RequestOfNode5IsSentToRx>=1)&&(RxIsActiveAndNotInTheLeafSet>=1)))||((Node1DontAnswerToAnyNode>=1)&&(Node6IsActive>=1)))||(Node4ManageTheBreakDownOfNode1>=1))||((Node8HasAskedItsLeafSetToLxToReplaceNode0>=1)&&(LeafSetOfLxIsSentToNode8>=1)))||((Node0WantsToManageTheBreakDownOfNode8>=1)&&(NoNodeManageTheBreakDownOfNode8>=1)))||((NoNodeManageTheBreakDownOfNode1>=1)&&(Node5WantsToManageTheBreakDownOfNode1>=1)))||(Node0ManageTheBreakDownOfNode3>=1))||(Node8HasTheLeafSetOfLxToReplaceNode0>=1))) U ((((((((((Node7ManageTheBreakDownOfNode0>=1)||(Node6ManageTheBreakDownOfNode3>=1))||((RequestOfNode4IsSentToRx>=1)&&(RxIsActiveAndNotInTheLeafSet>=1)))||((Node3HasAskedItsLeafSetToRxToReplaceNode6>=1)&&(LeafSetOfRxIsSentToNode3>=1)))||((Node7HasAskedItsLeafSetToLxToReplaceNode2>=1)&&(LeafSetOfLxIsSentToNode7>=1)))||(Node0HasTheLeafSetOfLxToReplaceNode1>=1))||(Node8HasTheLeafSetOfRxToReplaceNode4>=1))||((Node7HasAskedItsLeafSetToLxToReplaceNode1>=1)&&(LeafSetOfLxIsSentToNode7>=1)))||((Node3DontAnswerToAnyNode>=1)&&(Node6IsActive>=1)))||((Node3HasAskedItsLeafSetToRxToReplaceNode8>=1)&&(LeafSetOfRxIsSentToNode3>=1)))) + ((((((((Node6ManageTheBreakDownOfNode3<1)&&(Node4HasTheLeafSetOfLxToReplaceNode3<1))&&(Node2HasTheLeafSetOfRxToReplaceNode7<1))&&(Node6ManageTheBreakDownOfNode1<1))&&(Node2ManageTheBreakDownOfNode5<1))&&((Node8HasAskedItsLeafSetToRxToReplaceNode7<1)||(LeafSetOfRxIsSentToNode8<1)))&&((Node1DontAnswerToAnyNode<1)||(Node8IsActive<1)))&&((Node2WantsToManageTheBreakDownOfNode3<1)||(NoNodeManageTheBreakDownOfNode3<1))))))
=> equivalent forward existential formula: [FwdG(Init,!((!(!((E(!((!(EG(!(((((((((((Node0WantsToManageTheBreakDownOfNode3>=1)&&(NoNodeManageTheBreakDownOfNode3>=1))||((Node2IsActive>=1)&&(Node6DontAnswerToAnyNode>=1)))||((Node3WantsToManageTheBreakDownOfNode5>=1)&&(NoNodeManageTheBreakDownOfNode5>=1)))||((Node3HasAskedItsLeafSetToRxToReplaceNode7>=1)&&(LeafSetOfRxIsSentToNode3>=1)))||(Node3HasTheLeafSetOfRxToReplaceNode6>=1))||((Node1DontAnswerToAnyNode>=1)&&(Node7IsActive>=1)))||((NoNodeManageTheBreakDownOfNode0>=1)&&(Node4WantsToManageTheBreakDownOfNode0>=1)))||((Node4IsActive>=1)&&(Node8DontAnswerToAnyNode>=1)))||((NoNodeManageTheBreakDownOfNode3>=1)&&(Node4WantsToManageTheBreakDownOfNode3>=1)))))) + !((E(!(((Node0IsActive>=1)&&(Node4DontAnswerToAnyNode>=1))) U (!(((((((((((RequestOfNode2IsSentToRx>=1)&&(RxIsActiveAndNotInTheLeafSet>=1))||((Node2WantsToManageTheBreakDownOfNode6>=1)&&(NoNodeManageTheBreakDownOfNode6>=1)))||((RequestOfNode4IsSentToLx>=1)&&(LxIsActiveAndNotInTheLeafSet>=1)))||((Node3HasAskedItsLeafSetToLxToReplaceNode1>=1)&&(LeafSetOfLxIsSentToNode3>=1)))||((Node2HasAskedItsLeafSetToRxToReplaceNode5>=1)&&(LeafSetOfRxIsSentToNode2>=1)))||((Node5DontAnswerToAnyNode>=1)&&(Node8IsActive>=1)))||(Node0ManageTheBreakDownOfNode2>=1))||((Node0DontAnswerToAnyNode>=1)&&(Node5IsActive>=1)))||((Node4HasAskedItsLeafSetToRxToReplaceNode6>=1)&&(LeafSetOfRxIsSentToNode4>=1)))) * !(((Node0IsActive>=1)&&(Node4DontAnswerToAnyNode>=1))))) + EG(!(((Node0IsActive>=1)&&(Node4DontAnswerToAnyNode>=1)))))))) U (!(((((((((((((Node5HasAskedItsLeafSetToRxToReplaceNode8>=1)&&(LeafSetOfRxIsSentToNode5>=1))||(Node3HasTheLeafSetOfLxToReplaceNode2>=1))||((Node0IsActive>=1)&&(Node4DontAnswerToAnyNode>=1)))||((Node1WantsToManageTheBreakDownOfNode7>=1)&&(NoNodeManageTheBreakDownOfNode7>=1)))||((Node3IsActive>=1)&&(Node8DontAnswerToAnyNode>=1)))||((Node2WantsToManageTheBreakDownOfNode3>=1)&&(NoNodeManageTheBreakDownOfNode3>=1)))||(Node7HasTheLeafSetOfRxToReplaceNode8>=1))||((Node0IsActive>=1)&&(Node7DontAnswerToAnyNode>=1)))||(Node6HasTheLeafSetOfLxToReplaceNode0>=1))||((BreakDownReservoir>=1)&&(Node6IsActive>=1))) * E(TRUE U ((((((((((Node3ManageTheBreakDownOfNode7>=1)||((RequestOfNode4IsSentToLx>=1)&&(LxIsActiveAndNotInTheLeafSet>=1)))||((Node3IsActive>=1)&&(Node7DontAnswerToAnyNode>=1)))||(Node4HasTheLeafSetOfRxToReplaceNode7>=1))||(Node7HasTheLeafSetOfLxToReplaceNode2>=1))||((NoNodeManageTheBreakDownOfNode2>=1)&&(Node7WantsToManageTheBreakDownOfNode2>=1)))||(Node8HasTheLeafSetOfLxToReplaceNode1>=1))||((Node1HasAskedItsLeafSetToRxToReplaceNode7>=1)&&(LeafSetOfRxIsSentToNode1>=1)))||(Node3HasTheLeafSetOfRxToReplaceNode5>=1))||((Node4DontAnswerToAnyNode>=1)&&(Node5IsActive>=1)))))) * !((!(EG(!(((((((((((Node0WantsToManageTheBreakDownOfNode3>=1)&&(NoNodeManageTheBreakDownOfNode3>=1))||((Node2IsActive>=1)&&(Node6DontAnswerToAnyNode>=1)))||((Node3WantsToManageTheBreakDownOfNode5>=1)&&(NoNodeManageTheBreakDownOfNode5>=1)))||((Node3HasAskedItsLeafSetToRxToReplaceNode7>=1)&&(LeafSetOfRxIsSentToNode3>=1)))||(Node3HasTheLeafSetOfRxToReplaceNode6>=1))||((Node1DontAnswerToAnyNode>=1)&&(Node7IsActive>=1)))||((NoNodeManageTheBreakDownOfNode0>=1)&&(Node4WantsToManageTheBreakDownOfNode0>=1)))||((Node4IsActive>=1)&&(Node8DontAnswerToAnyNode>=1)))||((NoNodeManageTheBreakDownOfNode3>=1)&&(Node4WantsToManageTheBreakDownOfNode3>=1)))))) + !((E(!(((Node0IsActive>=1)&&(Node4DontAnswerToAnyNode>=1))) U (!(((((((((((RequestOfNode2IsSentToRx>=1)&&(RxIsActiveAndNotInTheLeafSet>=1))||((Node2WantsToManageTheBreakDownOfNode6>=1)&&(NoNodeManageTheBreakDownOfNode6>=1)))||((RequestOfNode4IsSentToLx>=1)&&(LxIsActiveAndNotInTheLeafSet>=1)))||((Node3HasAskedItsLeafSetToLxToReplaceNode1>=1)&&(LeafSetOfLxIsSentToNode3>=1)))||((Node2HasAskedItsLeafSetToRxToReplaceNode5>=1)&&(LeafSetOfRxIsSentToNode2>=1)))||((Node5DontAnswerToAnyNode>=1)&&(Node8IsActive>=1)))||(Node0ManageTheBreakDownOfNode2>=1))||((Node0DontAnswerToAnyNode>=1)&&(Node5IsActive>=1)))||((Node4HasAskedItsLeafSetToRxToReplaceNode6>=1)&&(LeafSetOfRxIsSentToNode4>=1)))) * !(((Node0IsActive>=1)&&(Node4DontAnswerToAnyNode>=1))))) + EG(!(((Node0IsActive>=1)&&(Node4DontAnswerToAnyNode>=1)))))))))) + EG(!((!(EG(!(((((((((((Node0WantsToManageTheBreakDownOfNode3>=1)&&(NoNodeManageTheBreakDownOfNode3>=1))||((Node2IsActive>=1)&&(Node6DontAnswerToAnyNode>=1)))||((Node3WantsToManageTheBreakDownOfNode5>=1)&&(NoNodeManageTheBreakDownOfNode5>=1)))||((Node3HasAskedItsLeafSetToRxToReplaceNode7>=1)&&(LeafSetOfRxIsSentToNode3>=1)))||(Node3HasTheLeafSetOfRxToReplaceNode6>=1))||((Node1DontAnswerToAnyNode>=1)&&(Node7IsActive>=1)))||((NoNodeManageTheBreakDownOfNode0>=1)&&(Node4WantsToManageTheBreakDownOfNode0>=1)))||((Node4IsActive>=1)&&(Node8DontAnswerToAnyNode>=1)))||((NoNodeManageTheBreakDownOfNode3>=1)&&(Node4WantsToManageTheBreakDownOfNode3>=1)))))) + !((E(!(((Node0IsActive>=1)&&(Node4DontAnswerToAnyNode>=1))) U (!(((((((((((RequestOfNode2IsSentToRx>=1)&&(RxIsActiveAndNotInTheLeafSet>=1))||((Node2WantsToManageTheBreakDownOfNode6>=1)&&(NoNodeManageTheBreakDownOfNode6>=1)))||((RequestOfNode4IsSentToLx>=1)&&(LxIsActiveAndNotInTheLeafSet>=1)))||((Node3HasAskedItsLeafSetToLxToReplaceNode1>=1)&&(LeafSetOfLxIsSentToNode3>=1)))||((Node2HasAskedItsLeafSetToRxToReplaceNode5>=1)&&(LeafSetOfRxIsSentToNode2>=1)))||((Node5DontAnswerToAnyNode>=1)&&(Node8IsActive>=1)))||(Node0ManageTheBreakDownOfNode2>=1))||((Node0DontAnswerToAnyNode>=1)&&(Node5IsActive>=1)))||((Node4HasAskedItsLeafSetToRxToReplaceNode6>=1)&&(LeafSetOfRxIsSentToNode4>=1)))) * !(((Node0IsActive>=1)&&(Node4DontAnswerToAnyNode>=1))))) + EG(!(((Node0IsActive>=1)&&(Node4DontAnswerToAnyNode>=1)))))))))))) * (!((E(!(((((((((((Node7ManageTheBreakDownOfNode0>=1)||(Node6ManageTheBreakDownOfNode3>=1))||((RequestOfNode4IsSentToRx>=1)&&(RxIsActiveAndNotInTheLeafSet>=1)))||((Node3HasAskedItsLeafSetToRxToReplaceNode6>=1)&&(LeafSetOfRxIsSentToNode3>=1)))||((Node7HasAskedItsLeafSetToLxToReplaceNode2>=1)&&(LeafSetOfLxIsSentToNode7>=1)))||(Node0HasTheLeafSetOfLxToReplaceNode1>=1))||(Node8HasTheLeafSetOfRxToReplaceNode4>=1))||((Node7HasAskedItsLeafSetToLxToReplaceNode1>=1)&&(LeafSetOfLxIsSentToNode7>=1)))||((Node3DontAnswerToAnyNode>=1)&&(Node6IsActive>=1)))||((Node3HasAskedItsLeafSetToRxToReplaceNode8>=1)&&(LeafSetOfRxIsSentToNode3>=1)))) U (!((((Node3ManageTheBreakDownOfNode0>=1)||((Node6HasAskedItsLeafSetToLxToReplaceNode3>=1)&&(LeafSetOfLxIsSentToNode6>=1)))&&((((((((((NoNodeManageTheBreakDownOfNode7>=1)&&(Node8WantsToManageTheBreakDownOfNode7>=1))||((RequestOfNode5IsSentToRx>=1)&&(RxIsActiveAndNotInTheLeafSet>=1)))||((Node1DontAnswerToAnyNode>=1)&&(Node6IsActive>=1)))||(Node4ManageTheBreakDownOfNode1>=1))||((Node8HasAskedItsLeafSetToLxToReplaceNode0>=1)&&(LeafSetOfLxIsSentToNode8>=1)))||((Node0WantsToManageTheBreakDownOfNode8>=1)&&(NoNodeManageTheBreakDownOfNode8>=1)))||((NoNodeManageTheBreakDownOfNode1>=1)&&(Node5WantsToManageTheBreakDownOfNode1>=1)))||(Node0ManageTheBreakDownOfNode3>=1))||(Node8HasTheLeafSetOfLxToReplaceNode0>=1)))) * !(((((((((((Node7ManageTheBreakDownOfNode0>=1)||(Node6ManageTheBreakDownOfNode3>=1))||((RequestOfNode4IsSentToRx>=1)&&(RxIsActiveAndNotInTheLeafSet>=1)))||((Node3HasAskedItsLeafSetToRxToReplaceNode6>=1)&&(LeafSetOfRxIsSentToNode3>=1)))||((Node7HasAskedItsLeafSetToLxToReplaceNode2>=1)&&(LeafSetOfLxIsSentToNode7>=1)))||(Node0HasTheLeafSetOfLxToReplaceNode1>=1))||(Node8HasTheLeafSetOfRxToReplaceNode4>=1))||((Node7HasAskedItsLeafSetToLxToReplaceNode1>=1)&&(LeafSetOfLxIsSentToNode7>=1)))||((Node3DontAnswerToAnyNode>=1)&&(Node6IsActive>=1)))||((Node3HasAskedItsLeafSetToRxToReplaceNode8>=1)&&(LeafSetOfRxIsSentToNode3>=1)))))) + EG(!(((((((((((Node7ManageTheBreakDownOfNode0>=1)||(Node6ManageTheBreakDownOfNode3>=1))||((RequestOfNode4IsSentToRx>=1)&&(RxIsActiveAndNotInTheLeafSet>=1)))||((Node3HasAskedItsLeafSetToRxToReplaceNode6>=1)&&(LeafSetOfRxIsSentToNode3>=1)))||((Node7HasAskedItsLeafSetToLxToReplaceNode2>=1)&&(LeafSetOfLxIsSentToNode7>=1)))||(Node0HasTheLeafSetOfLxToReplaceNode1>=1))||(Node8HasTheLeafSetOfRxToReplaceNode4>=1))||((Node7HasAskedItsLeafSetToLxToReplaceNode1>=1)&&(LeafSetOfLxIsSentToNode7>=1)))||((Node3DontAnswerToAnyNode>=1)&&(Node6IsActive>=1)))||((Node3HasAskedItsLeafSetToRxToReplaceNode8>=1)&&(LeafSetOfRxIsSentToNode3>=1))))))) + ((((((((Node6ManageTheBreakDownOfNode3<1)&&(Node4HasTheLeafSetOfLxToReplaceNode3<1))&&(Node2HasTheLeafSetOfRxToReplaceNode7<1))&&(Node6ManageTheBreakDownOfNode1<1))&&(Node2ManageTheBreakDownOfNode5<1))&&((Node8HasAskedItsLeafSetToRxToReplaceNode7<1)||(LeafSetOfRxIsSentToNode8<1)))&&((Node1DontAnswerToAnyNode<1)||(Node8IsActive<1)))&&((Node2WantsToManageTheBreakDownOfNode3<1)||(NoNodeManageTheBreakDownOfNode3<1)))))))] = FALSE
Reverse transition relation is NOT exact ! Due to transitions t2, t5, t8, t9, t18, t29, t34, t40, t42, t46, t52, t54, t57, t62, t71, t72, t75, t77, t81, t83, t92, t94, t101, t104, t106, t113, t116, t121, t128, t136, t138, t142, t148, t151, t156, t193, t194, t195, t196, t197, t198, t199, t200, t201, t202, t203, t204, t205, t206, t207, t208, t209, t210, t211, t214, t215, t216, t217, t218, t219, t220, t221, t223, t224, t225, t226, t227, t228, t229, t230, t231, t232, t235, t236, t237, t238, t239, t241, t242, t243, t244, t246, t247, t249, t250, t251, t252, t253, t254, t255, Intersection with reachable at each step enabled. (destroyed/reverse/intersect/total) :0/172/90/262
Detected timeout of ITS tools.
[2021-05-18 00:51:38] [INFO ] Flatten gal took : 13 ms
[2021-05-18 00:51:38] [INFO ] Applying decomposition
[2021-05-18 00:51:38] [INFO ] Flatten gal took : 19 ms
Converted graph to binary with : CommandLine [args=[/home/mcc/BenchKit/itstools/plugins/fr.lip6.move.gal.louvain.binaries_1.0.0.202104292328/bin/convert-linux64, -i, /tmp/graph547141922096593678.txt, -o, /tmp/graph547141922096593678.bin, -w, /tmp/graph547141922096593678.weights], workingDir=null]
Built communities with : CommandLine [args=[/home/mcc/BenchKit/itstools/plugins/fr.lip6.move.gal.louvain.binaries_1.0.0.202104292328/bin/louvain-linux64, /tmp/graph547141922096593678.bin, -l, -1, -v, -w, /tmp/graph547141922096593678.weights, -q, 0, -e, 0.001], workingDir=null]
[2021-05-18 00:51:38] [INFO ] Decomposing Gal with order
[2021-05-18 00:51:38] [INFO ] Rewriting arrays to variables to allow decomposition.
[2021-05-18 00:51:38] [INFO ] Removed a total of 169 redundant transitions.
[2021-05-18 00:51:38] [INFO ] Flatten gal took : 54 ms
[2021-05-18 00:51:38] [INFO ] Fuse similar labels procedure discarded/fused a total of 12 labels/synchronizations in 9 ms.
[2021-05-18 00:51:38] [INFO ] Time to serialize gal into /tmp/CTLFireability3817995522322363299.gal : 7 ms
[2021-05-18 00:51:38] [INFO ] Time to serialize properties into /tmp/CTLFireability7439739226996661938.ctl : 1 ms
Invoking ITS tools like this :CommandLine [args=[/home/mcc/BenchKit/itstools/plugins/fr.lip6.move.gal.itstools.binaries_1.0.0.202104292328/bin/its-ctl-linux64, --gc-threshold, 2000000, --quiet, -i, /tmp/CTLFireability3817995522322363299.gal, -t, CGAL, -ctl, /tmp/CTLFireability7439739226996661938.ctl], workingDir=/home/mcc/execution]
its-ctl command run as :
/home/mcc/BenchKit/itstools/plugins/fr.lip6.move.gal.itstools.binaries_1.0.0.202104292328/bin/its-ctl-linux64 --gc-threshold 2000000 --quiet -i /tmp/CTLFireability3817995522322363299.gal -t CGAL -ctl /tmp/CTLFireability7439739226996661938.ctl
No direction supplied, using forward translation only.
Parsed 1 CTL formulae.
Model ,|S| ,Time ,Mem(kb) ,fin. SDD ,fin. DDD ,peak SDD ,peak DDD ,SDD Hom ,SDD cache peak ,DDD Hom ,DDD cachepeak ,SHom cache
reachable,46981,13.4686,338728,8569,4335,182403,109293,1043,1.59396e+06,245,3.14637e+06,0
Converting to forward existential form...Done !
original formula: AF((!(A(((((((((((((i6.u32.Node5HasAskedItsLeafSetToRxToReplaceNode8>=1)&&(i2.u45.LeafSetOfRxIsSentToNode5>=1))||(i8.u46.Node3HasTheLeafSetOfLxToReplaceNode2>=1))||((i0.u0.Node0IsActive>=1)&&(i4.i0.u29.Node4DontAnswerToAnyNode>=1)))||((i1.u7.Node1WantsToManageTheBreakDownOfNode7>=1)&&(i5.i1.u28.NoNodeManageTheBreakDownOfNode7>=1)))||((i4.i0.u16.Node3IsActive>=1)&&(i6.u4.Node8DontAnswerToAnyNode>=1)))||((i3.u10.Node2WantsToManageTheBreakDownOfNode3>=1)&&(i4.i0.u25.NoNodeManageTheBreakDownOfNode3>=1)))||(i2.u8.Node7HasTheLeafSetOfRxToReplaceNode8>=1))||((i0.u0.Node0IsActive>=1)&&(i5.i1.u3.Node7DontAnswerToAnyNode>=1)))||(i8.u46.Node6HasTheLeafSetOfLxToReplaceNode0>=1))||((i5.i1.u33.BreakDownReservoir>=1)&&(i7.u34.Node6IsActive>=1))) * EF(((((((((((i6.u19.Node3ManageTheBreakDownOfNode7>=1)||((i4.i1.u24.RequestOfNode4IsSentToLx>=1)&&(i8.u46.LxIsActiveAndNotInTheLeafSet>=1)))||((i4.i0.u16.Node3IsActive>=1)&&(i5.i1.u3.Node7DontAnswerToAnyNode>=1)))||(i2.u8.Node4HasTheLeafSetOfRxToReplaceNode7>=1))||(i8.u46.Node7HasTheLeafSetOfLxToReplaceNode2>=1))||((i8.u41.NoNodeManageTheBreakDownOfNode2>=1)&&(i8.u41.Node7WantsToManageTheBreakDownOfNode2>=1)))||(i8.u46.Node8HasTheLeafSetOfLxToReplaceNode1>=1))||((i1.u7.Node1HasAskedItsLeafSetToRxToReplaceNode7>=1)&&(i2.u8.LeafSetOfRxIsSentToNode1>=1)))||(i2.u8.Node3HasTheLeafSetOfRxToReplaceNode5>=1))||((i4.i0.u29.Node4DontAnswerToAnyNode>=1)&&(i5.i1.u30.Node5IsActive>=1))))) U (AF(((((((((((i0.u2.Node0WantsToManageTheBreakDownOfNode3>=1)&&(i4.i0.u25.NoNodeManageTheBreakDownOfNode3>=1))||((i3.u10.Node2IsActive>=1)&&(i5.i0.u37.Node6DontAnswerToAnyNode>=1)))||((i4.i0.u16.Node3WantsToManageTheBreakDownOfNode5>=1)&&(i6.u26.NoNodeManageTheBreakDownOfNode5>=1)))||((i6.u19.Node3HasAskedItsLeafSetToRxToReplaceNode7>=1)&&(i2.u8.LeafSetOfRxIsSentToNode3>=1)))||(i2.u8.Node3HasTheLeafSetOfRxToReplaceNode6>=1))||((i9.u9.Node1DontAnswerToAnyNode>=1)&&(i5.i0.u38.Node7IsActive>=1)))||((i4.i0.u39.NoNodeManageTheBreakDownOfNode0>=1)&&(i4.i1.u23.Node4WantsToManageTheBreakDownOfNode0>=1)))||((i4.i1.u22.Node4IsActive>=1)&&(i6.u4.Node8DontAnswerToAnyNode>=1)))||((i4.i0.u25.NoNodeManageTheBreakDownOfNode3>=1)&&(i4.i1.u22.Node4WantsToManageTheBreakDownOfNode3>=1)))) + A(((((((((((i3.u11.RequestOfNode2IsSentToRx>=1)&&(i2.u8.RxIsActiveAndNotInTheLeafSet>=1))||((i3.u12.Node2WantsToManageTheBreakDownOfNode6>=1)&&(i5.i0.u18.NoNodeManageTheBreakDownOfNode6>=1)))||((i4.i1.u24.RequestOfNode4IsSentToLx>=1)&&(i8.u46.LxIsActiveAndNotInTheLeafSet>=1)))||((i8.u17.Node3HasAskedItsLeafSetToLxToReplaceNode1>=1)&&(i8.u46.LeafSetOfLxIsSentToNode3>=1)))||((i3.u11.Node2HasAskedItsLeafSetToRxToReplaceNode5>=1)&&(i2.u8.LeafSetOfRxIsSentToNode2>=1)))||((i5.i1.u33.Node5DontAnswerToAnyNode>=1)&&(i9.u42.Node8IsActive>=1)))||(i0.u1.Node0ManageTheBreakDownOfNode2>=1))||((i4.i0.u5.Node0DontAnswerToAnyNode>=1)&&(i5.i1.u30.Node5IsActive>=1)))||((i5.i0.u27.Node4HasAskedItsLeafSetToRxToReplaceNode6>=1)&&(i2.u8.LeafSetOfRxIsSentToNode4>=1))) U ((i0.u0.Node0IsActive>=1)&&(i4.i0.u29.Node4DontAnswerToAnyNode>=1)))))) * (A((((i4.i0.u15.Node3ManageTheBreakDownOfNode0>=1)||((i7.u36.Node6HasAskedItsLeafSetToLxToReplaceNode3>=1)&&(i8.u46.LeafSetOfLxIsSentToNode6>=1)))&&((((((((((i5.i1.u28.NoNodeManageTheBreakDownOfNode7>=1)&&(i5.i1.u44.Node8WantsToManageTheBreakDownOfNode7>=1))||((i2.u45.RequestOfNode5IsSentToRx>=1)&&(i2.u8.RxIsActiveAndNotInTheLeafSet>=1)))||((i9.u9.Node1DontAnswerToAnyNode>=1)&&(i7.u34.Node6IsActive>=1)))||(i4.i1.u24.Node4ManageTheBreakDownOfNode1>=1))||((i9.u43.Node8HasAskedItsLeafSetToLxToReplaceNode0>=1)&&(i8.u46.LeafSetOfLxIsSentToNode8>=1)))||((i0.u0.Node0WantsToManageTheBreakDownOfNode8>=1)&&(i6.u20.NoNodeManageTheBreakDownOfNode8>=1)))||((i8.u17.NoNodeManageTheBreakDownOfNode1>=1)&&(i9.u9.Node5WantsToManageTheBreakDownOfNode1>=1)))||(i0.u2.Node0ManageTheBreakDownOfNode3>=1))||(i8.u46.Node8HasTheLeafSetOfLxToReplaceNode0>=1))) U ((((((((((i4.i0.u39.Node7ManageTheBreakDownOfNode0>=1)||(i7.u36.Node6ManageTheBreakDownOfNode3>=1))||((i5.i0.u27.RequestOfNode4IsSentToRx>=1)&&(i2.u8.RxIsActiveAndNotInTheLeafSet>=1)))||((i5.i0.u18.Node3HasAskedItsLeafSetToRxToReplaceNode6>=1)&&(i2.u8.LeafSetOfRxIsSentToNode3>=1)))||((i8.u41.Node7HasAskedItsLeafSetToLxToReplaceNode2>=1)&&(i8.u46.LeafSetOfLxIsSentToNode7>=1)))||(i8.u46.Node0HasTheLeafSetOfLxToReplaceNode1>=1))||(i2.u8.Node8HasTheLeafSetOfRxToReplaceNode4>=1))||((i8.u40.Node7HasAskedItsLeafSetToLxToReplaceNode1>=1)&&(i8.u46.LeafSetOfLxIsSentToNode7>=1)))||((i1.u21.Node3DontAnswerToAnyNode>=1)&&(i7.u34.Node6IsActive>=1)))||((i6.u20.Node3HasAskedItsLeafSetToRxToReplaceNode8>=1)&&(i2.u8.LeafSetOfRxIsSentToNode3>=1)))) + ((((((((i7.u36.Node6ManageTheBreakDownOfNode3<1)&&(i8.u46.Node4HasTheLeafSetOfLxToReplaceNode3<1))&&(i2.u8.Node2HasTheLeafSetOfRxToReplaceNode7<1))&&(i7.u35.Node6ManageTheBreakDownOfNode1<1))&&(i3.u11.Node2ManageTheBreakDownOfNode5<1))&&((i5.i1.u44.Node8HasAskedItsLeafSetToRxToReplaceNode7<1)||(i2.u8.LeafSetOfRxIsSentToNode8<1)))&&((i9.u9.Node1DontAnswerToAnyNode<1)||(i9.u42.Node8IsActive<1)))&&((i3.u10.Node2WantsToManageTheBreakDownOfNode3<1)||(i4.i0.u25.NoNodeManageTheBreakDownOfNode3<1))))))
=> equivalent forward existential formula: [FwdG(Init,!((!(!((E(!((!(EG(!(((((((((((i0.u2.Node0WantsToManageTheBreakDownOfNode3>=1)&&(i4.i0.u25.NoNodeManageTheBreakDownOfNode3>=1))||((i3.u10.Node2IsActive>=1)&&(i5.i0.u37.Node6DontAnswerToAnyNode>=1)))||((i4.i0.u16.Node3WantsToManageTheBreakDownOfNode5>=1)&&(i6.u26.NoNodeManageTheBreakDownOfNode5>=1)))||((i6.u19.Node3HasAskedItsLeafSetToRxToReplaceNode7>=1)&&(i2.u8.LeafSetOfRxIsSentToNode3>=1)))||(i2.u8.Node3HasTheLeafSetOfRxToReplaceNode6>=1))||((i9.u9.Node1DontAnswerToAnyNode>=1)&&(i5.i0.u38.Node7IsActive>=1)))||((i4.i0.u39.NoNodeManageTheBreakDownOfNode0>=1)&&(i4.i1.u23.Node4WantsToManageTheBreakDownOfNode0>=1)))||((i4.i1.u22.Node4IsActive>=1)&&(i6.u4.Node8DontAnswerToAnyNode>=1)))||((i4.i0.u25.NoNodeManageTheBreakDownOfNode3>=1)&&(i4.i1.u22.Node4WantsToManageTheBreakDownOfNode3>=1)))))) + !((E(!(((i0.u0.Node0IsActive>=1)&&(i4.i0.u29.Node4DontAnswerToAnyNode>=1))) U (!(((((((((((i3.u11.RequestOfNode2IsSentToRx>=1)&&(i2.u8.RxIsActiveAndNotInTheLeafSet>=1))||((i3.u12.Node2WantsToManageTheBreakDownOfNode6>=1)&&(i5.i0.u18.NoNodeManageTheBreakDownOfNode6>=1)))||((i4.i1.u24.RequestOfNode4IsSentToLx>=1)&&(i8.u46.LxIsActiveAndNotInTheLeafSet>=1)))||((i8.u17.Node3HasAskedItsLeafSetToLxToReplaceNode1>=1)&&(i8.u46.LeafSetOfLxIsSentToNode3>=1)))||((i3.u11.Node2HasAskedItsLeafSetToRxToReplaceNode5>=1)&&(i2.u8.LeafSetOfRxIsSentToNode2>=1)))||((i5.i1.u33.Node5DontAnswerToAnyNode>=1)&&(i9.u42.Node8IsActive>=1)))||(i0.u1.Node0ManageTheBreakDownOfNode2>=1))||((i4.i0.u5.Node0DontAnswerToAnyNode>=1)&&(i5.i1.u30.Node5IsActive>=1)))||((i5.i0.u27.Node4HasAskedItsLeafSetToRxToReplaceNode6>=1)&&(i2.u8.LeafSetOfRxIsSentToNode4>=1)))) * !(((i0.u0.Node0IsActive>=1)&&(i4.i0.u29.Node4DontAnswerToAnyNode>=1))))) + EG(!(((i0.u0.Node0IsActive>=1)&&(i4.i0.u29.Node4DontAnswerToAnyNode>=1)))))))) U (!(((((((((((((i6.u32.Node5HasAskedItsLeafSetToRxToReplaceNode8>=1)&&(i2.u45.LeafSetOfRxIsSentToNode5>=1))||(i8.u46.Node3HasTheLeafSetOfLxToReplaceNode2>=1))||((i0.u0.Node0IsActive>=1)&&(i4.i0.u29.Node4DontAnswerToAnyNode>=1)))||((i1.u7.Node1WantsToManageTheBreakDownOfNode7>=1)&&(i5.i1.u28.NoNodeManageTheBreakDownOfNode7>=1)))||((i4.i0.u16.Node3IsActive>=1)&&(i6.u4.Node8DontAnswerToAnyNode>=1)))||((i3.u10.Node2WantsToManageTheBreakDownOfNode3>=1)&&(i4.i0.u25.NoNodeManageTheBreakDownOfNode3>=1)))||(i2.u8.Node7HasTheLeafSetOfRxToReplaceNode8>=1))||((i0.u0.Node0IsActive>=1)&&(i5.i1.u3.Node7DontAnswerToAnyNode>=1)))||(i8.u46.Node6HasTheLeafSetOfLxToReplaceNode0>=1))||((i5.i1.u33.BreakDownReservoir>=1)&&(i7.u34.Node6IsActive>=1))) * E(TRUE U ((((((((((i6.u19.Node3ManageTheBreakDownOfNode7>=1)||((i4.i1.u24.RequestOfNode4IsSentToLx>=1)&&(i8.u46.LxIsActiveAndNotInTheLeafSet>=1)))||((i4.i0.u16.Node3IsActive>=1)&&(i5.i1.u3.Node7DontAnswerToAnyNode>=1)))||(i2.u8.Node4HasTheLeafSetOfRxToReplaceNode7>=1))||(i8.u46.Node7HasTheLeafSetOfLxToReplaceNode2>=1))||((i8.u41.NoNodeManageTheBreakDownOfNode2>=1)&&(i8.u41.Node7WantsToManageTheBreakDownOfNode2>=1)))||(i8.u46.Node8HasTheLeafSetOfLxToReplaceNode1>=1))||((i1.u7.Node1HasAskedItsLeafSetToRxToReplaceNode7>=1)&&(i2.u8.LeafSetOfRxIsSentToNode1>=1)))||(i2.u8.Node3HasTheLeafSetOfRxToReplaceNode5>=1))||((i4.i0.u29.Node4DontAnswerToAnyNode>=1)&&(i5.i1.u30.Node5IsActive>=1)))))) * !((!(EG(!(((((((((((i0.u2.Node0WantsToManageTheBreakDownOfNode3>=1)&&(i4.i0.u25.NoNodeManageTheBreakDownOfNode3>=1))||((i3.u10.Node2IsActive>=1)&&(i5.i0.u37.Node6DontAnswerToAnyNode>=1)))||((i4.i0.u16.Node3WantsToManageTheBreakDownOfNode5>=1)&&(i6.u26.NoNodeManageTheBreakDownOfNode5>=1)))||((i6.u19.Node3HasAskedItsLeafSetToRxToReplaceNode7>=1)&&(i2.u8.LeafSetOfRxIsSentToNode3>=1)))||(i2.u8.Node3HasTheLeafSetOfRxToReplaceNode6>=1))||((i9.u9.Node1DontAnswerToAnyNode>=1)&&(i5.i0.u38.Node7IsActive>=1)))||((i4.i0.u39.NoNodeManageTheBreakDownOfNode0>=1)&&(i4.i1.u23.Node4WantsToManageTheBreakDownOfNode0>=1)))||((i4.i1.u22.Node4IsActive>=1)&&(i6.u4.Node8DontAnswerToAnyNode>=1)))||((i4.i0.u25.NoNodeManageTheBreakDownOfNode3>=1)&&(i4.i1.u22.Node4WantsToManageTheBreakDownOfNode3>=1)))))) + !((E(!(((i0.u0.Node0IsActive>=1)&&(i4.i0.u29.Node4DontAnswerToAnyNode>=1))) U (!(((((((((((i3.u11.RequestOfNode2IsSentToRx>=1)&&(i2.u8.RxIsActiveAndNotInTheLeafSet>=1))||((i3.u12.Node2WantsToManageTheBreakDownOfNode6>=1)&&(i5.i0.u18.NoNodeManageTheBreakDownOfNode6>=1)))||((i4.i1.u24.RequestOfNode4IsSentToLx>=1)&&(i8.u46.LxIsActiveAndNotInTheLeafSet>=1)))||((i8.u17.Node3HasAskedItsLeafSetToLxToReplaceNode1>=1)&&(i8.u46.LeafSetOfLxIsSentToNode3>=1)))||((i3.u11.Node2HasAskedItsLeafSetToRxToReplaceNode5>=1)&&(i2.u8.LeafSetOfRxIsSentToNode2>=1)))||((i5.i1.u33.Node5DontAnswerToAnyNode>=1)&&(i9.u42.Node8IsActive>=1)))||(i0.u1.Node0ManageTheBreakDownOfNode2>=1))||((i4.i0.u5.Node0DontAnswerToAnyNode>=1)&&(i5.i1.u30.Node5IsActive>=1)))||((i5.i0.u27.Node4HasAskedItsLeafSetToRxToReplaceNode6>=1)&&(i2.u8.LeafSetOfRxIsSentToNode4>=1)))) * !(((i0.u0.Node0IsActive>=1)&&(i4.i0.u29.Node4DontAnswerToAnyNode>=1))))) + EG(!(((i0.u0.Node0IsActive>=1)&&(i4.i0.u29.Node4DontAnswerToAnyNode>=1)))))))))) + EG(!((!(EG(!(((((((((((i0.u2.Node0WantsToManageTheBreakDownOfNode3>=1)&&(i4.i0.u25.NoNodeManageTheBreakDownOfNode3>=1))||((i3.u10.Node2IsActive>=1)&&(i5.i0.u37.Node6DontAnswerToAnyNode>=1)))||((i4.i0.u16.Node3WantsToManageTheBreakDownOfNode5>=1)&&(i6.u26.NoNodeManageTheBreakDownOfNode5>=1)))||((i6.u19.Node3HasAskedItsLeafSetToRxToReplaceNode7>=1)&&(i2.u8.LeafSetOfRxIsSentToNode3>=1)))||(i2.u8.Node3HasTheLeafSetOfRxToReplaceNode6>=1))||((i9.u9.Node1DontAnswerToAnyNode>=1)&&(i5.i0.u38.Node7IsActive>=1)))||((i4.i0.u39.NoNodeManageTheBreakDownOfNode0>=1)&&(i4.i1.u23.Node4WantsToManageTheBreakDownOfNode0>=1)))||((i4.i1.u22.Node4IsActive>=1)&&(i6.u4.Node8DontAnswerToAnyNode>=1)))||((i4.i0.u25.NoNodeManageTheBreakDownOfNode3>=1)&&(i4.i1.u22.Node4WantsToManageTheBreakDownOfNode3>=1)))))) + !((E(!(((i0.u0.Node0IsActive>=1)&&(i4.i0.u29.Node4DontAnswerToAnyNode>=1))) U (!(((((((((((i3.u11.RequestOfNode2IsSentToRx>=1)&&(i2.u8.RxIsActiveAndNotInTheLeafSet>=1))||((i3.u12.Node2WantsToManageTheBreakDownOfNode6>=1)&&(i5.i0.u18.NoNodeManageTheBreakDownOfNode6>=1)))||((i4.i1.u24.RequestOfNode4IsSentToLx>=1)&&(i8.u46.LxIsActiveAndNotInTheLeafSet>=1)))||((i8.u17.Node3HasAskedItsLeafSetToLxToReplaceNode1>=1)&&(i8.u46.LeafSetOfLxIsSentToNode3>=1)))||((i3.u11.Node2HasAskedItsLeafSetToRxToReplaceNode5>=1)&&(i2.u8.LeafSetOfRxIsSentToNode2>=1)))||((i5.i1.u33.Node5DontAnswerToAnyNode>=1)&&(i9.u42.Node8IsActive>=1)))||(i0.u1.Node0ManageTheBreakDownOfNode2>=1))||((i4.i0.u5.Node0DontAnswerToAnyNode>=1)&&(i5.i1.u30.Node5IsActive>=1)))||((i5.i0.u27.Node4HasAskedItsLeafSetToRxToReplaceNode6>=1)&&(i2.u8.LeafSetOfRxIsSentToNode4>=1)))) * !(((i0.u0.Node0IsActive>=1)&&(i4.i0.u29.Node4DontAnswerToAnyNode>=1))))) + EG(!(((i0.u0.Node0IsActive>=1)&&(i4.i0.u29.Node4DontAnswerToAnyNode>=1)))))))))))) * (!((E(!(((((((((((i4.i0.u39.Node7ManageTheBreakDownOfNode0>=1)||(i7.u36.Node6ManageTheBreakDownOfNode3>=1))||((i5.i0.u27.RequestOfNode4IsSentToRx>=1)&&(i2.u8.RxIsActiveAndNotInTheLeafSet>=1)))||((i5.i0.u18.Node3HasAskedItsLeafSetToRxToReplaceNode6>=1)&&(i2.u8.LeafSetOfRxIsSentToNode3>=1)))||((i8.u41.Node7HasAskedItsLeafSetToLxToReplaceNode2>=1)&&(i8.u46.LeafSetOfLxIsSentToNode7>=1)))||(i8.u46.Node0HasTheLeafSetOfLxToReplaceNode1>=1))||(i2.u8.Node8HasTheLeafSetOfRxToReplaceNode4>=1))||((i8.u40.Node7HasAskedItsLeafSetToLxToReplaceNode1>=1)&&(i8.u46.LeafSetOfLxIsSentToNode7>=1)))||((i1.u21.Node3DontAnswerToAnyNode>=1)&&(i7.u34.Node6IsActive>=1)))||((i6.u20.Node3HasAskedItsLeafSetToRxToReplaceNode8>=1)&&(i2.u8.LeafSetOfRxIsSentToNode3>=1)))) U (!((((i4.i0.u15.Node3ManageTheBreakDownOfNode0>=1)||((i7.u36.Node6HasAskedItsLeafSetToLxToReplaceNode3>=1)&&(i8.u46.LeafSetOfLxIsSentToNode6>=1)))&&((((((((((i5.i1.u28.NoNodeManageTheBreakDownOfNode7>=1)&&(i5.i1.u44.Node8WantsToManageTheBreakDownOfNode7>=1))||((i2.u45.RequestOfNode5IsSentToRx>=1)&&(i2.u8.RxIsActiveAndNotInTheLeafSet>=1)))||((i9.u9.Node1DontAnswerToAnyNode>=1)&&(i7.u34.Node6IsActive>=1)))||(i4.i1.u24.Node4ManageTheBreakDownOfNode1>=1))||((i9.u43.Node8HasAskedItsLeafSetToLxToReplaceNode0>=1)&&(i8.u46.LeafSetOfLxIsSentToNode8>=1)))||((i0.u0.Node0WantsToManageTheBreakDownOfNode8>=1)&&(i6.u20.NoNodeManageTheBreakDownOfNode8>=1)))||((i8.u17.NoNodeManageTheBreakDownOfNode1>=1)&&(i9.u9.Node5WantsToManageTheBreakDownOfNode1>=1)))||(i0.u2.Node0ManageTheBreakDownOfNode3>=1))||(i8.u46.Node8HasTheLeafSetOfLxToReplaceNode0>=1)))) * !(((((((((((i4.i0.u39.Node7ManageTheBreakDownOfNode0>=1)||(i7.u36.Node6ManageTheBreakDownOfNode3>=1))||((i5.i0.u27.RequestOfNode4IsSentToRx>=1)&&(i2.u8.RxIsActiveAndNotInTheLeafSet>=1)))||((i5.i0.u18.Node3HasAskedItsLeafSetToRxToReplaceNode6>=1)&&(i2.u8.LeafSetOfRxIsSentToNode3>=1)))||((i8.u41.Node7HasAskedItsLeafSetToLxToReplaceNode2>=1)&&(i8.u46.LeafSetOfLxIsSentToNode7>=1)))||(i8.u46.Node0HasTheLeafSetOfLxToReplaceNode1>=1))||(i2.u8.Node8HasTheLeafSetOfRxToReplaceNode4>=1))||((i8.u40.Node7HasAskedItsLeafSetToLxToReplaceNode1>=1)&&(i8.u46.LeafSetOfLxIsSentToNode7>=1)))||((i1.u21.Node3DontAnswerToAnyNode>=1)&&(i7.u34.Node6IsActive>=1)))||((i6.u20.Node3HasAskedItsLeafSetToRxToReplaceNode8>=1)&&(i2.u8.LeafSetOfRxIsSentToNode3>=1)))))) + EG(!(((((((((((i4.i0.u39.Node7ManageTheBreakDownOfNode0>=1)||(i7.u36.Node6ManageTheBreakDownOfNode3>=1))||((i5.i0.u27.RequestOfNode4IsSentToRx>=1)&&(i2.u8.RxIsActiveAndNotInTheLeafSet>=1)))||((i5.i0.u18.Node3HasAskedItsLeafSetToRxToReplaceNode6>=1)&&(i2.u8.LeafSetOfRxIsSentToNode3>=1)))||((i8.u41.Node7HasAskedItsLeafSetToLxToReplaceNode2>=1)&&(i8.u46.LeafSetOfLxIsSentToNode7>=1)))||(i8.u46.Node0HasTheLeafSetOfLxToReplaceNode1>=1))||(i2.u8.Node8HasTheLeafSetOfRxToReplaceNode4>=1))||((i8.u40.Node7HasAskedItsLeafSetToLxToReplaceNode1>=1)&&(i8.u46.LeafSetOfLxIsSentToNode7>=1)))||((i1.u21.Node3DontAnswerToAnyNode>=1)&&(i7.u34.Node6IsActive>=1)))||((i6.u20.Node3HasAskedItsLeafSetToRxToReplaceNode8>=1)&&(i2.u8.LeafSetOfRxIsSentToNode3>=1))))))) + ((((((((i7.u36.Node6ManageTheBreakDownOfNode3<1)&&(i8.u46.Node4HasTheLeafSetOfLxToReplaceNode3<1))&&(i2.u8.Node2HasTheLeafSetOfRxToReplaceNode7<1))&&(i7.u35.Node6ManageTheBreakDownOfNode1<1))&&(i3.u11.Node2ManageTheBreakDownOfNode5<1))&&((i5.i1.u44.Node8HasAskedItsLeafSetToRxToReplaceNode7<1)||(i2.u8.LeafSetOfRxIsSentToNode8<1)))&&((i9.u9.Node1DontAnswerToAnyNode<1)||(i9.u42.Node8IsActive<1)))&&((i3.u10.Node2WantsToManageTheBreakDownOfNode3<1)||(i4.i0.u25.NoNodeManageTheBreakDownOfNode3<1)))))))] = FALSE
Reverse transition relation is NOT exact ! Due to transitions t9, t18, t29, t34, t42, t54, t77, t83, t121, t128, t193, t194, t195, t196, t198, t199, t200, t202, t203, t204, t205, t206, t207, t208, t210, t214, t216, t217, t218, t219, t220, t221, t223, t224, t226, t227, t228, t230, t231, t235, t237, t238, t239, t241, t242, t243, t244, t247, t249, t250, t251, t252, t253, t255, i0.t8, i0.t5, i2.u8.t40, i2.u8.t57, i2.u8.t62, i2.u8.t92, i2.u8.t142, i2.u8.t156, i2.u8.t254, i4.t71, i4.i0.t197, i4.i0.u15.t46, i4.i1.t72, i4.i1.u24.t75, i5.t138, i5.t104, i5.i0.t232, i5.i1.t101, i5.i1.t106, i6.t94, i7.t116, i8.t246, i8.t229, i8.t211, i8.u46.t2, i8.u46.t52, i8.u46.t81, i8.u46.t113, i8.u46.t136, i8.u46.t148, i8.u46.t151, i8.u46.t236, Intersection with reachable at each step enabled. (destroyed/reverse/intersect/total) :0/170/86/256
Detected timeout of ITS tools.
Drop transitions removed 50 transitions
Trivial Post-agglo rules discarded 50 transitions
Performed 50 trivial Post agglomeration. Transition count delta: 50
Iterating post reduction 0 with 50 rules applied. Total rules applied 50 place count 370 transition count 352
Reduce places removed 50 places and 0 transitions.
Performed 61 Post agglomeration using F-continuation condition.Transition count delta: 61
Iterating post reduction 1 with 111 rules applied. Total rules applied 161 place count 320 transition count 291
Reduce places removed 61 places and 0 transitions.
Iterating post reduction 2 with 61 rules applied. Total rules applied 222 place count 259 transition count 291
Performed 11 Pre agglomeration using Quasi-Persistent + Divergent Free condition..
Pre-agglomeration after 3 with 11 Pre rules applied. Total rules applied 222 place count 259 transition count 280
Deduced a syphon composed of 11 places in 1 ms
Reduce places removed 11 places and 0 transitions.
Iterating global reduction 3 with 22 rules applied. Total rules applied 244 place count 248 transition count 280
Discarding 36 places :
Symmetric choice reduction at 3 with 36 rule applications. Total rules 280 place count 212 transition count 244
Iterating global reduction 3 with 36 rules applied. Total rules applied 316 place count 212 transition count 244
Discarding 4 places :
Symmetric choice reduction at 3 with 4 rule applications. Total rules 320 place count 208 transition count 240
Iterating global reduction 3 with 4 rules applied. Total rules applied 324 place count 208 transition count 240
Discarding 1 places :
Implicit places reduction removed 1 places
Iterating post reduction 3 with 1 rules applied. Total rules applied 325 place count 207 transition count 240
Discarding 1 places :
Symmetric choice reduction at 4 with 1 rule applications. Total rules 326 place count 206 transition count 239
Iterating global reduction 4 with 1 rules applied. Total rules applied 327 place count 206 transition count 239
Performed 3 Post agglomeration using F-continuation condition.Transition count delta: 3
Deduced a syphon composed of 3 places in 1 ms
Reduce places removed 3 places and 0 transitions.
Iterating global reduction 4 with 6 rules applied. Total rules applied 333 place count 203 transition count 236
Discarding 6 places :
Symmetric choice reduction at 4 with 6 rule applications. Total rules 339 place count 197 transition count 230
Iterating global reduction 4 with 6 rules applied. Total rules applied 345 place count 197 transition count 230
Discarding 1 places :
Symmetric choice reduction at 4 with 1 rule applications. Total rules 346 place count 196 transition count 229
Iterating global reduction 4 with 1 rules applied. Total rules applied 347 place count 196 transition count 229
Applied a total of 347 rules in 57 ms. Remains 196 /370 variables (removed 174) and now considering 229/402 (removed 173) transitions.
[2021-05-18 00:52:08] [INFO ] Flatten gal took : 10 ms
[2021-05-18 00:52:08] [INFO ] Flatten gal took : 11 ms
[2021-05-18 00:52:09] [INFO ] Input system was already deterministic with 229 transitions.
[2021-05-18 00:52:09] [INFO ] Flatten gal took : 12 ms
[2021-05-18 00:52:09] [INFO ] Flatten gal took : 11 ms
[2021-05-18 00:52:09] [INFO ] Time to serialize gal into /tmp/CTLFireability16668839898792474704.gal : 2 ms
[2021-05-18 00:52:09] [INFO ] Time to serialize properties into /tmp/CTLFireability10753824424834321791.ctl : 12 ms
Invoking ITS tools like this :CommandLine [args=[/home/mcc/BenchKit/itstools/plugins/fr.lip6.move.gal.itstools.binaries_1.0.0.202104292328/bin/its-ctl-linux64, --gc-threshold, 2000000, --quiet, -i, /tmp/CTLFireability16668839898792474704.gal, -t, CGAL, -ctl, /tmp/CTLFireability10753824424834321791.ctl, --gen-order, FOLLOW], workingDir=/home/mcc/execution]
its-ctl command run as :
/home/mcc/BenchKit/itstools/plugins/fr.lip6.move.gal.itstools.binaries_1.0.0.202104292328/bin/its-ctl-linux64 --gc-threshold 2000000 --quiet -i /tmp/CTLFireability16668839898792474704.gal -t CGAL -ctl /tmp/CTLFireability10753824424834321791.ctl --gen-order FOLLOW
No direction supplied, using forward translation only.
Parsed 1 CTL formulae.
Model ,|S| ,Time ,Mem(kb) ,fin. SDD ,fin. DDD ,peak SDD ,peak DDD ,SDD Hom ,SDD cache peak ,DDD Hom ,DDD cachepeak ,SHom cache
reachable,36740,1.31035,46604,2,18545,5,134392,6,0,1003,216070,0
Converting to forward existential form...Done !
original formula: EF((EG(((Node4HasAskedItsLeafSetToRxToReplaceNode8>=1)&&(LeafSetOfRxIsSentToNode4>=1))) * (((((((((Node6HasTheLeafSetOfLxToReplaceNode2>=1)||(Node3ManageTheBreakDownOfNode4>=1))||(Node7ManageTheBreakDownOfNode4>=1)) + AF(E(((((((((((Node1HasTheLeafSetOfLxToReplaceNode3>=1)||((Node1DontAnswerToAnyNode>=1)&&(Node3IsActive>=1)))||((Node0HasAskedItsLeafSetToRxToReplaceNode7>=1)&&(LeafSetOfRxIsSentToNode0>=1)))||((NoNodeManageTheBreakDownOfNode5>=1)&&(Node8WantsToManageTheBreakDownOfNode5>=1)))||((Node3WantsToManageTheBreakDownOfNode5>=1)&&(NoNodeManageTheBreakDownOfNode5>=1)))||((NoNodeManageTheBreakDownOfNode6>=1)&&(Node8WantsToManageTheBreakDownOfNode6>=1)))||((Node2HasAskedItsLeafSetToLxToReplaceNode4>=1)&&(LeafSetOfLxIsSentToNode2>=1)))||((Node0WantsToManageTheBreakDownOfNode8>=1)&&(NoNodeManageTheBreakDownOfNode8>=1)))||((Node7HasAskedItsLeafSetToLxToReplaceNode1>=1)&&(LeafSetOfLxIsSentToNode7>=1)))||((Node3HasAskedItsLeafSetToLxToReplaceNode4>=1)&&(LeafSetOfLxIsSentToNode3>=1))) U (((Node0HasTheLeafSetOfLxToReplaceNode1>=1)||(Node0ManageTheBreakDownOfNode5>=1))||((Node5IsActive>=1)&&(Node8DontAnswerToAnyNode>=1)))))) + ((Node1WantsToManageTheBreakDownOfNode6>=1)&&(NoNodeManageTheBreakDownOfNode6>=1))) + ((Node0WantsToManageTheBreakDownOfNode7>=1)&&(NoNodeManageTheBreakDownOfNode7>=1))) + ((BreakDownReservoir>=1)&&(Node8IsActive>=1))) + ((((((RequestOfNode8IsSentToLx<1)||(LxIsActiveAndNotInTheLeafSet<1))&&((Node3IsActive<1)||(Node8DontAnswerToAnyNode<1)))&&((RequestOfNode7IsSentToLx<1)||(LxIsActiveAndNotInTheLeafSet<1)))&&((Node0IsActive<1)||(Node8DontAnswerToAnyNode<1)))&&((Node4WantsToManageTheBreakDownOfNode7<1)||(NoNodeManageTheBreakDownOfNode7<1)))) + (EG(((((((((((Node0WantsToManageTheBreakDownOfNode3>=1)&&(NoNodeManageTheBreakDownOfNode3>=1))||((NoNodeManageTheBreakDownOfNode6>=1)&&(Node8WantsToManageTheBreakDownOfNode6>=1)))||((Node4DontAnswerToAnyNode>=1)&&(Node6IsActive>=1)))||((NoNodeManageTheBreakDownOfNode0>=1)&&(Node8WantsToManageTheBreakDownOfNode0>=1)))||(Node2HasTheLeafSetOfLxToReplaceNode1>=1))||(Node3ManageTheBreakDownOfNode2>=1))||(Node2HasTheLeafSetOfRxToReplaceNode6>=1))||((Node1IsActive>=1)&&(Node7DontAnswerToAnyNode>=1)))||((Node3HasAskedItsLeafSetToRxToReplaceNode8>=1)&&(LeafSetOfRxIsSentToNode3>=1)))) * (((((Node7ManageTheBreakDownOfNode1>=1)||(Node5ManageTheBreakDownOfNode8>=1))||((Node0IsActive>=1)&&(Node1DontAnswerToAnyNode>=1)))||((Node4HasAskedItsLeafSetToLxToReplaceNode2>=1)&&(LeafSetOfLxIsSentToNode4>=1)))||((Node4HasAskedItsLeafSetToLxToReplaceNode1>=1)&&(LeafSetOfLxIsSentToNode4>=1)))))))
=> equivalent forward existential formula: (((((([((FwdU(Init,TRUE) * EG(((Node4HasAskedItsLeafSetToRxToReplaceNode8>=1)&&(LeafSetOfRxIsSentToNode4>=1)))) * (((Node6HasTheLeafSetOfLxToReplaceNode2>=1)||(Node3ManageTheBreakDownOfNode4>=1))||(Node7ManageTheBreakDownOfNode4>=1)))] != FALSE + [((FwdU(Init,TRUE) * EG(((Node4HasAskedItsLeafSetToRxToReplaceNode8>=1)&&(LeafSetOfRxIsSentToNode4>=1)))) * !(EG(!(E(((((((((((Node1HasTheLeafSetOfLxToReplaceNode3>=1)||((Node1DontAnswerToAnyNode>=1)&&(Node3IsActive>=1)))||((Node0HasAskedItsLeafSetToRxToReplaceNode7>=1)&&(LeafSetOfRxIsSentToNode0>=1)))||((NoNodeManageTheBreakDownOfNode5>=1)&&(Node8WantsToManageTheBreakDownOfNode5>=1)))||((Node3WantsToManageTheBreakDownOfNode5>=1)&&(NoNodeManageTheBreakDownOfNode5>=1)))||((NoNodeManageTheBreakDownOfNode6>=1)&&(Node8WantsToManageTheBreakDownOfNode6>=1)))||((Node2HasAskedItsLeafSetToLxToReplaceNode4>=1)&&(LeafSetOfLxIsSentToNode2>=1)))||((Node0WantsToManageTheBreakDownOfNode8>=1)&&(NoNodeManageTheBreakDownOfNode8>=1)))||((Node7HasAskedItsLeafSetToLxToReplaceNode1>=1)&&(LeafSetOfLxIsSentToNode7>=1)))||((Node3HasAskedItsLeafSetToLxToReplaceNode4>=1)&&(LeafSetOfLxIsSentToNode3>=1))) U (((Node0HasTheLeafSetOfLxToReplaceNode1>=1)||(Node0ManageTheBreakDownOfNode5>=1))||((Node5IsActive>=1)&&(Node8DontAnswerToAnyNode>=1))))))))] != FALSE) + [((FwdU(Init,TRUE) * EG(((Node4HasAskedItsLeafSetToRxToReplaceNode8>=1)&&(LeafSetOfRxIsSentToNode4>=1)))) * ((Node1WantsToManageTheBreakDownOfNode6>=1)&&(NoNodeManageTheBreakDownOfNode6>=1)))] != FALSE) + [((FwdU(Init,TRUE) * EG(((Node4HasAskedItsLeafSetToRxToReplaceNode8>=1)&&(LeafSetOfRxIsSentToNode4>=1)))) * ((Node0WantsToManageTheBreakDownOfNode7>=1)&&(NoNodeManageTheBreakDownOfNode7>=1)))] != FALSE) + [((FwdU(Init,TRUE) * EG(((Node4HasAskedItsLeafSetToRxToReplaceNode8>=1)&&(LeafSetOfRxIsSentToNode4>=1)))) * ((BreakDownReservoir>=1)&&(Node8IsActive>=1)))] != FALSE) + [((FwdU(Init,TRUE) * EG(((Node4HasAskedItsLeafSetToRxToReplaceNode8>=1)&&(LeafSetOfRxIsSentToNode4>=1)))) * ((((((RequestOfNode8IsSentToLx<1)||(LxIsActiveAndNotInTheLeafSet<1))&&((Node3IsActive<1)||(Node8DontAnswerToAnyNode<1)))&&((RequestOfNode7IsSentToLx<1)||(LxIsActiveAndNotInTheLeafSet<1)))&&((Node0IsActive<1)||(Node8DontAnswerToAnyNode<1)))&&((Node4WantsToManageTheBreakDownOfNode7<1)||(NoNodeManageTheBreakDownOfNode7<1))))] != FALSE) + [FwdG(((FwdU(Init,TRUE) * EG(((Node4HasAskedItsLeafSetToRxToReplaceNode8>=1)&&(LeafSetOfRxIsSentToNode4>=1)))) * (((((Node7ManageTheBreakDownOfNode1>=1)||(Node5ManageTheBreakDownOfNode8>=1))||((Node0IsActive>=1)&&(Node1DontAnswerToAnyNode>=1)))||((Node4HasAskedItsLeafSetToLxToReplaceNode2>=1)&&(LeafSetOfLxIsSentToNode4>=1)))||((Node4HasAskedItsLeafSetToLxToReplaceNode1>=1)&&(LeafSetOfLxIsSentToNode4>=1)))),((((((((((Node0WantsToManageTheBreakDownOfNode3>=1)&&(NoNodeManageTheBreakDownOfNode3>=1))||((NoNodeManageTheBreakDownOfNode6>=1)&&(Node8WantsToManageTheBreakDownOfNode6>=1)))||((Node4DontAnswerToAnyNode>=1)&&(Node6IsActive>=1)))||((NoNodeManageTheBreakDownOfNode0>=1)&&(Node8WantsToManageTheBreakDownOfNode0>=1)))||(Node2HasTheLeafSetOfLxToReplaceNode1>=1))||(Node3ManageTheBreakDownOfNode2>=1))||(Node2HasTheLeafSetOfRxToReplaceNode6>=1))||((Node1IsActive>=1)&&(Node7DontAnswerToAnyNode>=1)))||((Node3HasAskedItsLeafSetToRxToReplaceNode8>=1)&&(LeafSetOfRxIsSentToNode3>=1))))] != FALSE)
Reverse transition relation is NOT exact ! Due to transitions t3, t5, t7, t10, t19, t21, t22, t32, t38, t44, t47, t75, t77, t80, t85, t89, t92, t94, t100, t106, t108, t110, t116, t119, t121, t123, t124, t154, t155, t156, t157, t158, t159, t161, t162, t163, t164, t165, t166, t167, t168, t169, t171, t172, t173, t174, t175, t176, t177, t178, t179, t180, t181, t182, t183, t184, t185, t186, t187, t188, t189, t190, t191, t192, t193, t194, t195, t196, t197, t198, t199, t200, t201, t202, t203, t205, t206, t208, t209, t211, t212, t213, t215, t216, t217, t218, t219, t220, t221, t222, Intersection with reachable at each step enabled. (destroyed/reverse/intersect/total) :0/139/90/229
dead was empty
(forward)formula 0,0,19.6549,580392,1,0,689,2.75866e+06,494,305,6683,1.85575e+06,614
FORMULA LeafsetExtension-PT-S08C2-CTLFireability-13 FALSE TECHNIQUES DECISION_DIAGRAMS TOPOLOGICAL
Formula is FALSE !
***************************************
[2021-05-18 00:52:28] [INFO ] Flatten gal took : 19 ms
[2021-05-18 00:52:28] [INFO ] Flatten gal took : 42 ms
[2021-05-18 00:52:29] [INFO ] Applying decomposition
[2021-05-18 00:52:29] [INFO ] Flatten gal took : 18 ms
Converted graph to binary with : CommandLine [args=[/home/mcc/BenchKit/itstools/plugins/fr.lip6.move.gal.louvain.binaries_1.0.0.202104292328/bin/convert-linux64, -i, /tmp/graph18116187683953762014.txt, -o, /tmp/graph18116187683953762014.bin, -w, /tmp/graph18116187683953762014.weights], workingDir=null]
Built communities with : CommandLine [args=[/home/mcc/BenchKit/itstools/plugins/fr.lip6.move.gal.louvain.binaries_1.0.0.202104292328/bin/louvain-linux64, /tmp/graph18116187683953762014.bin, -l, -1, -v, -w, /tmp/graph18116187683953762014.weights, -q, 0, -e, 0.001], workingDir=null]
[2021-05-18 00:52:29] [INFO ] Decomposing Gal with order
[2021-05-18 00:52:29] [INFO ] Rewriting arrays to variables to allow decomposition.
[2021-05-18 00:52:29] [INFO ] Removed a total of 213 redundant transitions.
[2021-05-18 00:52:29] [INFO ] Flatten gal took : 52 ms
[2021-05-18 00:52:29] [INFO ] Fuse similar labels procedure discarded/fused a total of 4 labels/synchronizations in 10 ms.
[2021-05-18 00:52:29] [INFO ] Time to serialize gal into /tmp/CTLFireability9958652229795878339.gal : 4 ms
[2021-05-18 00:52:29] [INFO ] Time to serialize properties into /tmp/CTLFireability4664874533309118382.ctl : 12 ms
Invoking ITS tools like this :CommandLine [args=[/home/mcc/BenchKit/itstools/plugins/fr.lip6.move.gal.itstools.binaries_1.0.0.202104292328/bin/its-ctl-linux64, --gc-threshold, 2000000, --quiet, -i, /tmp/CTLFireability9958652229795878339.gal, -t, CGAL, -ctl, /tmp/CTLFireability4664874533309118382.ctl], workingDir=/home/mcc/execution]
its-ctl command run as :
/home/mcc/BenchKit/itstools/plugins/fr.lip6.move.gal.itstools.binaries_1.0.0.202104292328/bin/its-ctl-linux64 --gc-threshold 2000000 --quiet -i /tmp/CTLFireability9958652229795878339.gal -t CGAL -ctl /tmp/CTLFireability4664874533309118382.ctl
No direction supplied, using forward translation only.
Parsed 15 CTL formulae.
Model ,|S| ,Time ,Mem(kb) ,fin. SDD ,fin. DDD ,peak SDD ,peak DDD ,SDD Hom ,SDD cache peak ,DDD Hom ,DDD cachepeak ,SHom cache
reachable,107584,28.7509,749144,15462,9324,244107,449983,1199,1.41927e+06,403,1.15116e+07,0
Converting to forward existential form...Done !
original formula: AF(EX(E((AG(((((((i2.i1.u71.Node7HasAskedItsLeafSetToLxToReplaceNode2>=1)&&(u87.LeafSetOfLxIsSentToNode7>=1))||((i6.i1.u20.Node1HasAskedItsLeafSetToRxToReplaceNode8>=1)&&(i11.u88.LeafSetOfRxIsSentToNode1>=1)))||((i7.i2.u83.Node8HasAskedItsLeafSetToRxToReplaceNode5>=1)&&(i11.u86.LeafSetOfRxIsSentToNode8>=1)))||(u87.Node6HasTheLeafSetOfLxToReplaceNode3>=1))||(u87.Node8HasTheLeafSetOfLxToReplaceNode3>=1))) * EG((((((((((i7.i0.u8.Node0HasAskedItsLeafSetToRxToReplaceNode6>=1)&&(i11.u88.LeafSetOfRxIsSentToNode0>=1))||((i5.u6.Node0WantsToManageTheBreakDownOfNode4>=1)&&(i5.u6.NoNodeManageTheBreakDownOfNode4>=1)))||(i11.u88.Node7HasTheLeafSetOfRxToReplaceNode6>=1))||(i11.u88.Node2HasTheLeafSetOfRxToReplaceNode7>=1))||((i0.i2.u24.Node2WantsToManageTheBreakDownOfNode3>=1)&&(i0.i2.u5.NoNodeManageTheBreakDownOfNode3>=1)))||(i0.i0.u69.Node7ManageTheBreakDownOfNode1>=1))||((i1.u36.Node3HasAskedItsLeafSetToRxToReplaceNode5>=1)&&(i11.u88.LeafSetOfRxIsSentToNode3>=1)))||((i7.i1.u40.Node4IsActive>=1)&&(i6.i1.u10.Node8DontAnswerToAnyNode>=1))))) U (AX(((((((i6.i0.u9.Node0ManageTheBreakDownOfNode7>=1)||((i0.i1.u22.Node0DontAnswerToAnyNode>=1)&&(i9.u70.Node7IsActive>=1)))||(i9.u74.Node7ManageTheBreakDownOfNode5>=1))||(u87.Node7HasTheLeafSetOfLxToReplaceNode2>=1))||((i0.i0.u23.NoNodeManageTheBreakDownOfNode1>=1)&&(i0.i0.u69.Node7WantsToManageTheBreakDownOfNode1>=1)))||((i0.i1.u22.Node0DontAnswerToAnyNode>=1)&&(i4.u61.Node6IsActive>=1)))) + AX(((((u87.LxIsActiveAndNotInTheLeafSet>=1)&&(u87.ANodeFromTheLeafSetOfLxIsACtiveInTheLeafSet>=1))||(i7.i0.u8.Node0ManageTheBreakDownOfNode6>=1))||(u87.LxHasReceivedTheRequestOfNode0>=1)))))))
=> equivalent forward existential formula: [FwdG(Init,!(EX(E((!(E(TRUE U !(((((((i2.i1.u71.Node7HasAskedItsLeafSetToLxToReplaceNode2>=1)&&(u87.LeafSetOfLxIsSentToNode7>=1))||((i6.i1.u20.Node1HasAskedItsLeafSetToRxToReplaceNode8>=1)&&(i11.u88.LeafSetOfRxIsSentToNode1>=1)))||((i7.i2.u83.Node8HasAskedItsLeafSetToRxToReplaceNode5>=1)&&(i11.u86.LeafSetOfRxIsSentToNode8>=1)))||(u87.Node6HasTheLeafSetOfLxToReplaceNode3>=1))||(u87.Node8HasTheLeafSetOfLxToReplaceNode3>=1))))) * EG((((((((((i7.i0.u8.Node0HasAskedItsLeafSetToRxToReplaceNode6>=1)&&(i11.u88.LeafSetOfRxIsSentToNode0>=1))||((i5.u6.Node0WantsToManageTheBreakDownOfNode4>=1)&&(i5.u6.NoNodeManageTheBreakDownOfNode4>=1)))||(i11.u88.Node7HasTheLeafSetOfRxToReplaceNode6>=1))||(i11.u88.Node2HasTheLeafSetOfRxToReplaceNode7>=1))||((i0.i2.u24.Node2WantsToManageTheBreakDownOfNode3>=1)&&(i0.i2.u5.NoNodeManageTheBreakDownOfNode3>=1)))||(i0.i0.u69.Node7ManageTheBreakDownOfNode1>=1))||((i1.u36.Node3HasAskedItsLeafSetToRxToReplaceNode5>=1)&&(i11.u88.LeafSetOfRxIsSentToNode3>=1)))||((i7.i1.u40.Node4IsActive>=1)&&(i6.i1.u10.Node8DontAnswerToAnyNode>=1))))) U (!(EX(!(((((((i6.i0.u9.Node0ManageTheBreakDownOfNode7>=1)||((i0.i1.u22.Node0DontAnswerToAnyNode>=1)&&(i9.u70.Node7IsActive>=1)))||(i9.u74.Node7ManageTheBreakDownOfNode5>=1))||(u87.Node7HasTheLeafSetOfLxToReplaceNode2>=1))||((i0.i0.u23.NoNodeManageTheBreakDownOfNode1>=1)&&(i0.i0.u69.Node7WantsToManageTheBreakDownOfNode1>=1)))||((i0.i1.u22.Node0DontAnswerToAnyNode>=1)&&(i4.u61.Node6IsActive>=1)))))) + !(EX(!(((((u87.LxIsActiveAndNotInTheLeafSet>=1)&&(u87.ANodeFromTheLeafSetOfLxIsACtiveInTheLeafSet>=1))||(i7.i0.u8.Node0ManageTheBreakDownOfNode6>=1))||(u87.LxHasReceivedTheRequestOfNode0>=1))))))))))] = FALSE
Reverse transition relation is NOT exact ! Due to transitions t169, t194, t203, t234, t284, t289, t354, t363, u87.t5, u87.t10, u87.t15, u87.t20, u87.t46, u87.t51, u87.t56, u87.t61, u87.t87, u87.t92, u87.t97, u87.t102, u87.t129, u87.t134, u87.t139, u87.t144, u87.t170, u87.t175, u87.t180, u87.t185, u87.t210, u87.t215, u87.t220, u87.t225, u87.t250, u87.t255, u87.t260, u87.t265, u87.t294, u87.t299, u87.t304, u87.t330, u87.t335, u87.t340, u87.t345, i5.u50.t124, i5.u50.t205, i11.t190, i11.u88.t25, i11.u88.t30, i11.u88.t35, i11.u88.t40, i11.u88.t66, i11.u88.t71, i11.u88.t76, i11.u88.t81, i11.u88.t107, i11.u88.t112, i11.u88.t117, i11.u88.t122, i11.u88.t149, i11.u88.t154, i11.u88.t159, i11.u88.t164, i11.u88.t199, i11.u88.t230, i11.u88.t239, i11.u88.t244, i11.u88.t270, i11.u88.t275, i11.u88.t280, i11.u88.t309, i11.u88.t314, i11.u88.t319, i11.u88.t324, i11.u88.t350, i11.u88.t359, Intersection with reachable at each step enabled. (destroyed/reverse/intersect/total) :0/325/75/400
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
(forward)formula 0,1,88.0993,2094192,1,0,1.08035e+06,594960,5266,5.58597e+06,2173,2.48983e+07,7325350
FORMULA LeafsetExtension-PT-S08C2-CTLFireability-00 TRUE TECHNIQUES DECISION_DIAGRAMS TOPOLOGICAL USE_NUPN
Formula is TRUE !
***************************************
original formula: ((EG(((u87.Node8HasTheLeafSetOfLxToReplaceNode3<1) + ((((((((((((((((u87.Node4HasTheLeafSetOfLxToReplaceNode2<1)&&((i7.i2.u27.NoNodeManageTheBreakDownOfNode5<1)||(i7.i2.u59.Node8WantsToManageTheBreakDownOfNode5<1)))&&((i7.i1.u45.Node4WantsToManageTheBreakDownOfNode5<1)||(i7.i2.u27.NoNodeManageTheBreakDownOfNode5<1)))&&((i5.u55.RequestOfNode5IsSentToRx<1)||(i11.u88.RxIsActiveAndNotInTheLeafSet<1))) * !(EF(((((((((i3.u85.Node8HasAskedItsLeafSetToRxToReplaceNode7>=1)&&(i11.u86.LeafSetOfRxIsSentToNode8>=1))||(i3.u66.Node6ManageTheBreakDownOfNode7>=1))||((i2.i0.u12.Node1HasAskedItsLeafSetToLxToReplaceNode0>=1)&&(u87.LeafSetOfLxIsSentToNode1>=1)))||((i7.i1.u40.Node4WantsToManageTheBreakDownOfNode6>=1)&&(i7.i0.u47.NoNodeManageTheBreakDownOfNode6>=1)))||((i6.i1.u30.Node2HasAskedItsLeafSetToRxToReplaceNode8>=1)&&(i11.u88.LeafSetOfRxIsSentToNode2>=1)))||(u87.Node5HasTheLeafSetOfLxToReplaceNode1>=1))||((i2.i1.u3.Node2DontAnswerToAnyNode>=1)&&(i10.u78.Node8IsActive>=1)))))) * ((((((i0.i0.u2.Node0WantsToManageTheBreakDownOfNode1>=1)&&(i0.i0.u23.NoNodeManageTheBreakDownOfNode1>=1))||((i1.u31.Node3IsActive>=1)&&(i5.u50.Node4DontAnswerToAnyNode>=1)))||(i11.u88.Node3HasTheLeafSetOfRxToReplaceNode5>=1))||((i2.i1.u4.NoNodeManageTheBreakDownOfNode2>=1)&&(i2.i1.u34.Node3WantsToManageTheBreakDownOfNode2>=1)))||((i8.u53.Node5HasAskedItsLeafSetToLxToReplaceNode2>=1)&&(u87.LeafSetOfLxIsSentToNode5>=1)))) * ((i7.i2.u21.Node2IsActive<1)||(i7.i0.u8.Node6DontAnswerToAnyNode<1))) * ((i6.i1.u30.Node2HasAskedItsLeafSetToRxToReplaceNode8<1)||(i11.u88.LeafSetOfRxIsSentToNode2<1))) * ((i1.u31.Node3IsActive<1)||(i5.u50.Node4DontAnswerToAnyNode<1))) * (i7.i2.u65.Node6ManageTheBreakDownOfNode5<1)) * ((i3.u48.Node4HasAskedItsLeafSetToRxToReplaceNode7<1)||(i11.u46.LeafSetOfRxIsSentToNode4<1))) * (i11.u88.Node6HasTheLeafSetOfRxToReplaceNode4<1)) * ((i8.u51.RequestOfNode5IsSentToLx<1)||(u87.LxIsActiveAndNotInTheLeafSet<1))) * ((i7.i1.u45.Node4HasAskedItsLeafSetToRxToReplaceNode5<1)||(i11.u46.LeafSetOfRxIsSentToNode4<1))) * ((i0.i0.u2.Node0HasAskedItsLeafSetToLxToReplaceNode1<1)||(u87.LeafSetOfLxIsSentToNode0<1))) * ((i8.u52.Node5IsActive<1)||(i3.u18.Node7DontAnswerToAnyNode<1))))) + AG(AX(AF(((((((i7.i0.u28.RequestOfNode2IsSentToRx>=1)&&(i11.u88.RxIsActiveAndNotInTheLeafSet>=1))||(u87.Node2HasTheLeafSetOfLxToReplaceNode3>=1))||((i0.i0.u2.Node0HasAskedItsLeafSetToLxToReplaceNode1>=1)&&(u87.LeafSetOfLxIsSentToNode0>=1)))||((i7.i0.u47.Node4HasAskedItsLeafSetToRxToReplaceNode6>=1)&&(i11.u46.LeafSetOfRxIsSentToNode4>=1)))&&(((i11.u88.Node0HasTheLeafSetOfRxToReplaceNode8>=1)||((i0.i1.u68.NoNodeManageTheBreakDownOfNode0>=1)&&(i8.u51.Node5WantsToManageTheBreakDownOfNode0>=1)))||((i3.u18.Node4WantsToManageTheBreakDownOfNode7>=1)&&(i3.u48.NoNodeManageTheBreakDownOfNode7>=1)))))))) + EG((((((i3.u48.NoNodeManageTheBreakDownOfNode7>=1)&&(i3.u85.Node8WantsToManageTheBreakDownOfNode7>=1))||((i4.u61.Node6IsActive>=1)&&(i6.i1.u10.Node8DontAnswerToAnyNode>=1)))||(i7.i2.u16.Node1ManageTheBreakDownOfNode5>=1))||((i7.i0.u8.Node0WantsToManageTheBreakDownOfNode6>=1)&&(i7.i0.u47.NoNodeManageTheBreakDownOfNode6>=1)))))
=> equivalent forward existential formula: [FwdG(EY(FwdU(((Init * !(EG((((((i3.u48.NoNodeManageTheBreakDownOfNode7>=1)&&(i3.u85.Node8WantsToManageTheBreakDownOfNode7>=1))||((i4.u61.Node6IsActive>=1)&&(i6.i1.u10.Node8DontAnswerToAnyNode>=1)))||(i7.i2.u16.Node1ManageTheBreakDownOfNode5>=1))||((i7.i0.u8.Node0WantsToManageTheBreakDownOfNode6>=1)&&(i7.i0.u47.NoNodeManageTheBreakDownOfNode6>=1)))))) * !(EG(((u87.Node8HasTheLeafSetOfLxToReplaceNode3<1) + ((((((((((((((((u87.Node4HasTheLeafSetOfLxToReplaceNode2<1)&&((i7.i2.u27.NoNodeManageTheBreakDownOfNode5<1)||(i7.i2.u59.Node8WantsToManageTheBreakDownOfNode5<1)))&&((i7.i1.u45.Node4WantsToManageTheBreakDownOfNode5<1)||(i7.i2.u27.NoNodeManageTheBreakDownOfNode5<1)))&&((i5.u55.RequestOfNode5IsSentToRx<1)||(i11.u88.RxIsActiveAndNotInTheLeafSet<1))) * !(E(TRUE U ((((((((i3.u85.Node8HasAskedItsLeafSetToRxToReplaceNode7>=1)&&(i11.u86.LeafSetOfRxIsSentToNode8>=1))||(i3.u66.Node6ManageTheBreakDownOfNode7>=1))||((i2.i0.u12.Node1HasAskedItsLeafSetToLxToReplaceNode0>=1)&&(u87.LeafSetOfLxIsSentToNode1>=1)))||((i7.i1.u40.Node4WantsToManageTheBreakDownOfNode6>=1)&&(i7.i0.u47.NoNodeManageTheBreakDownOfNode6>=1)))||((i6.i1.u30.Node2HasAskedItsLeafSetToRxToReplaceNode8>=1)&&(i11.u88.LeafSetOfRxIsSentToNode2>=1)))||(u87.Node5HasTheLeafSetOfLxToReplaceNode1>=1))||((i2.i1.u3.Node2DontAnswerToAnyNode>=1)&&(i10.u78.Node8IsActive>=1)))))) * ((((((i0.i0.u2.Node0WantsToManageTheBreakDownOfNode1>=1)&&(i0.i0.u23.NoNodeManageTheBreakDownOfNode1>=1))||((i1.u31.Node3IsActive>=1)&&(i5.u50.Node4DontAnswerToAnyNode>=1)))||(i11.u88.Node3HasTheLeafSetOfRxToReplaceNode5>=1))||((i2.i1.u4.NoNodeManageTheBreakDownOfNode2>=1)&&(i2.i1.u34.Node3WantsToManageTheBreakDownOfNode2>=1)))||((i8.u53.Node5HasAskedItsLeafSetToLxToReplaceNode2>=1)&&(u87.LeafSetOfLxIsSentToNode5>=1)))) * ((i7.i2.u21.Node2IsActive<1)||(i7.i0.u8.Node6DontAnswerToAnyNode<1))) * ((i6.i1.u30.Node2HasAskedItsLeafSetToRxToReplaceNode8<1)||(i11.u88.LeafSetOfRxIsSentToNode2<1))) * ((i1.u31.Node3IsActive<1)||(i5.u50.Node4DontAnswerToAnyNode<1))) * (i7.i2.u65.Node6ManageTheBreakDownOfNode5<1)) * ((i3.u48.Node4HasAskedItsLeafSetToRxToReplaceNode7<1)||(i11.u46.LeafSetOfRxIsSentToNode4<1))) * (i11.u88.Node6HasTheLeafSetOfRxToReplaceNode4<1)) * ((i8.u51.RequestOfNode5IsSentToLx<1)||(u87.LxIsActiveAndNotInTheLeafSet<1))) * ((i7.i1.u45.Node4HasAskedItsLeafSetToRxToReplaceNode5<1)||(i11.u46.LeafSetOfRxIsSentToNode4<1))) * ((i0.i0.u2.Node0HasAskedItsLeafSetToLxToReplaceNode1<1)||(u87.LeafSetOfLxIsSentToNode0<1))) * ((i8.u52.Node5IsActive<1)||(i3.u18.Node7DontAnswerToAnyNode<1))))))),TRUE)),!(((((((i7.i0.u28.RequestOfNode2IsSentToRx>=1)&&(i11.u88.RxIsActiveAndNotInTheLeafSet>=1))||(u87.Node2HasTheLeafSetOfLxToReplaceNode3>=1))||((i0.i0.u2.Node0HasAskedItsLeafSetToLxToReplaceNode1>=1)&&(u87.LeafSetOfLxIsSentToNode0>=1)))||((i7.i0.u47.Node4HasAskedItsLeafSetToRxToReplaceNode6>=1)&&(i11.u46.LeafSetOfRxIsSentToNode4>=1)))&&(((i11.u88.Node0HasTheLeafSetOfRxToReplaceNode8>=1)||((i0.i1.u68.NoNodeManageTheBreakDownOfNode0>=1)&&(i8.u51.Node5WantsToManageTheBreakDownOfNode0>=1)))||((i3.u18.Node4WantsToManageTheBreakDownOfNode7>=1)&&(i3.u48.NoNodeManageTheBreakDownOfNode7>=1))))))] = FALSE
(forward)formula 1,1,97.4407,2297932,1,0,1.28659e+06,695671,6599,6.09191e+06,2225,2.59245e+07,8335157
FORMULA LeafsetExtension-PT-S08C2-CTLFireability-01 TRUE TECHNIQUES DECISION_DIAGRAMS TOPOLOGICAL USE_NUPN
Formula is TRUE !
***************************************
original formula: E(!(EX((AG(((((u87.Node3HasTheLeafSetOfLxToReplaceNode0>=1)||((u87.LxIsActiveAndNotInTheLeafSet>=1)&&(u87.ANodeFromTheLeafSetOfLxIsACtiveInTheLeafSet>=1)))||((i5.u50.Node4DontAnswerToAnyNode>=1)&&(i9.u70.Node7IsActive>=1)))||((i7.i2.u27.NoNodeManageTheBreakDownOfNode5>=1)&&(i9.u74.Node7WantsToManageTheBreakDownOfNode5>=1)))) + AX(EF(((((((i0.i1.u22.Node2HasAskedItsLeafSetToLxToReplaceNode0>=1)&&(u87.LeafSetOfLxIsSentToNode2>=1))||((i0.i0.u23.NoNodeManageTheBreakDownOfNode1>=1)&&(i10.u78.Node8WantsToManageTheBreakDownOfNode1>=1)))||((i0.i0.u42.Node4HasAskedItsLeafSetToLxToReplaceNode1>=1)&&(u87.LeafSetOfLxIsSentToNode4>=1)))||((i6.i1.u10.Node0WantsToManageTheBreakDownOfNode8>=1)&&(i6.i1.u11.NoNodeManageTheBreakDownOfNode8>=1)))||(i11.u88.Node2HasTheLeafSetOfRxToReplaceNode8>=1))))))) U A((E(AF((((((((((i7.i0.u8.Node6DontAnswerToAnyNode>=1)&&(i10.u78.Node8IsActive>=1))||(i9.u75.Node7ManageTheBreakDownOfNode6>=1))||((i0.i2.u25.RequestOfNode2IsSentToLx>=1)&&(u87.LxIsActiveAndNotInTheLeafSet>=1)))||(i5.u50.RightNodeHasDetectedBreakDownOfMaster>=1))||((i7.i0.u47.NoNodeManageTheBreakDownOfNode6>=1)&&(i9.u75.Node7WantsToManageTheBreakDownOfNode6>=1)))||(i6.i1.u11.Node0ManageTheBreakDownOfNode8>=1))||((i2.i1.u3.Node2DontAnswerToAnyNode>=1)&&(i8.u52.Node5IsActive>=1)))||((i0.i0.u23.NoNodeManageTheBreakDownOfNode1>=1)&&(i0.i0.u42.Node4WantsToManageTheBreakDownOfNode1>=1)))) U ((((((((((i0.i0.u2.Node0WantsToManageTheBreakDownOfNode1<1)||(i0.i0.u23.NoNodeManageTheBreakDownOfNode1<1))&&(i8.u53.Node5ManageTheBreakDownOfNode2<1))&&((i2.i0.u14.Node1HasAskedItsLeafSetToLxToReplaceNode3<1)||(u87.LeafSetOfLxIsSentToNode1<1)))&&((i1.u31.Node3IsActive<1)||(i6.i1.u10.Node8DontAnswerToAnyNode<1)))&&((i6.i0.u0.Node0IsActive<1)||(i6.i1.u10.Node8DontAnswerToAnyNode<1)))&&((i0.i0.u23.Node2HasAskedItsLeafSetToLxToReplaceNode1<1)||(u87.LeafSetOfLxIsSentToNode2<1)))&&((i6.i0.u0.Node0IsActive<1)||(i7.i0.u8.Node6DontAnswerToAnyNode<1)))&&((i7.i2.u21.Node2IsActive<1)||(i0.i2.u24.Node3DontAnswerToAnyNode<1))) * AG((((((((((i2.i1.u3.Node0WantsToManageTheBreakDownOfNode2>=1)&&(i2.i1.u4.NoNodeManageTheBreakDownOfNode2>=1))||((i4.u60.Node6HasAskedItsLeafSetToLxToReplaceNode0>=1)&&(u87.LeafSetOfLxIsSentToNode6>=1)))||((i8.u51.Node5HasAskedItsLeafSetToLxToReplaceNode0>=1)&&(u87.LeafSetOfLxIsSentToNode5>=1)))||(i6.i1.u30.Node2ManageTheBreakDownOfNode8>=1))||(u87.Node8HasTheLeafSetOfLxToReplaceNode2>=1))||(i11.u88.Node5HasTheLeafSetOfRxToReplaceNode4>=1))||(u87.Node6HasTheLeafSetOfLxToReplaceNode1>=1))||((i0.i2.u24.Node3DontAnswerToAnyNode>=1)&&(i9.u70.Node7IsActive>=1)))))) + ((((((((((i4.u63.Node6ManageTheBreakDownOfNode3<1)&&(i6.i1.u30.Node2ManageTheBreakDownOfNode8<1))&&(i11.u88.Node6HasTheLeafSetOfRxToReplaceNode5<1))&&(i11.u88.Node5HasTheLeafSetOfRxToReplaceNode4<1))&&(u87.LxHasReceivedTheRequestOfNode4<1))&&(i6.i1.u58.Node5ManageTheBreakDownOfNode8<1)) * AX(((((((((i3.u29.Node2ManageTheBreakDownOfNode7>=1)||((i2.i1.u3.Node0WantsToManageTheBreakDownOfNode2>=1)&&(i2.i1.u4.NoNodeManageTheBreakDownOfNode2>=1)))||(i11.u88.RxHasReceivedTheRequestOfNode3>=1))||(i5.u6.Node0ManageTheBreakDownOfNode4>=1))||((i5.u55.RequestOfNode5IsSentToRx>=1)&&(i11.u88.RxIsActiveAndNotInTheLeafSet>=1)))||(i0.i0.u69.Node7ManageTheBreakDownOfNode1>=1))||((i4.u61.Node6IsActive>=1)&&(i3.u18.Node7DontAnswerToAnyNode>=1)))&&(((((((((i11.u46.RxHasReceivedTheRequestOfNode4>=1)||((i7.i2.u21.Node2IsActive>=1)&&(i6.i1.u10.Node8DontAnswerToAnyNode>=1)))||(u87.Node1HasTheLeafSetOfLxToReplaceNode4>=1))||((i5.u82.Node8HasAskedItsLeafSetToRxToReplaceNode4>=1)&&(i11.u86.LeafSetOfRxIsSentToNode8>=1)))||((i0.i2.u25.Node2HasAskedItsLeafSetToLxToReplaceNode3>=1)&&(u87.LeafSetOfLxIsSentToNode2>=1)))||(u87.LxHasReceivedTheRequestOfNode6>=1))||(u87.Node7HasTheLeafSetOfLxToReplaceNode3>=1))||(i11.u88.Node2HasTheLeafSetOfRxToReplaceNode6>=1))||(u87.Node8HasTheLeafSetOfLxToReplaceNode3>=1))))) * ((i1.u38.Node3WantsToManageTheBreakDownOfNode7<1)||(i3.u48.NoNodeManageTheBreakDownOfNode7<1))) * ((i0.i1.u68.NoNodeManageTheBreakDownOfNode0<1)||(i8.u51.Node5WantsToManageTheBreakDownOfNode0<1))) * ((i0.i1.u22.Node0DontAnswerToAnyNode<1)||(i4.u61.Node6IsActive<1)))) U AG(((((((i11.u88.RxHasReceivedTheRequestOfNode7>=1)||(i11.u88.RxHasReceivedTheRequestOfNode5>=1))||((i1.u38.Node3HasAskedItsLeafSetToRxToReplaceNode7>=1)&&(i11.u88.LeafSetOfRxIsSentToNode3>=1)))||((i0.i1.u22.Node0DontAnswerToAnyNode>=1)&&(i4.u61.Node6IsActive>=1)))||((i7.i2.u21.Node2WantsToManageTheBreakDownOfNode5>=1)&&(i7.i2.u27.NoNodeManageTheBreakDownOfNode5>=1)))||((i1.u39.Node3HasAskedItsLeafSetToRxToReplaceNode8>=1)&&(i11.u88.LeafSetOfRxIsSentToNode3>=1))))))
=> equivalent forward existential formula: [((FwdU(Init,!(EX((!(E(TRUE U !(((((u87.Node3HasTheLeafSetOfLxToReplaceNode0>=1)||((u87.LxIsActiveAndNotInTheLeafSet>=1)&&(u87.ANodeFromTheLeafSetOfLxIsACtiveInTheLeafSet>=1)))||((i5.u50.Node4DontAnswerToAnyNode>=1)&&(i9.u70.Node7IsActive>=1)))||((i7.i2.u27.NoNodeManageTheBreakDownOfNode5>=1)&&(i9.u74.Node7WantsToManageTheBreakDownOfNode5>=1)))))) + !(EX(!(E(TRUE U ((((((i0.i1.u22.Node2HasAskedItsLeafSetToLxToReplaceNode0>=1)&&(u87.LeafSetOfLxIsSentToNode2>=1))||((i0.i0.u23.NoNodeManageTheBreakDownOfNode1>=1)&&(i10.u78.Node8WantsToManageTheBreakDownOfNode1>=1)))||((i0.i0.u42.Node4HasAskedItsLeafSetToLxToReplaceNode1>=1)&&(u87.LeafSetOfLxIsSentToNode4>=1)))||((i6.i1.u10.Node0WantsToManageTheBreakDownOfNode8>=1)&&(i6.i1.u11.NoNodeManageTheBreakDownOfNode8>=1)))||(i11.u88.Node2HasTheLeafSetOfRxToReplaceNode8>=1)))))))))) * !(EG(!(!(E(TRUE U !(((((((i11.u88.RxHasReceivedTheRequestOfNode7>=1)||(i11.u88.RxHasReceivedTheRequestOfNode5>=1))||((i1.u38.Node3HasAskedItsLeafSetToRxToReplaceNode7>=1)&&(i11.u88.LeafSetOfRxIsSentToNode3>=1)))||((i0.i1.u22.Node0DontAnswerToAnyNode>=1)&&(i4.u61.Node6IsActive>=1)))||((i7.i2.u21.Node2WantsToManageTheBreakDownOfNode5>=1)&&(i7.i2.u27.NoNodeManageTheBreakDownOfNode5>=1)))||((i1.u39.Node3HasAskedItsLeafSetToRxToReplaceNode8>=1)&&(i11.u88.LeafSetOfRxIsSentToNode3>=1)))))))))) * !(E(!(!(E(TRUE U !(((((((i11.u88.RxHasReceivedTheRequestOfNode7>=1)||(i11.u88.RxHasReceivedTheRequestOfNode5>=1))||((i1.u38.Node3HasAskedItsLeafSetToRxToReplaceNode7>=1)&&(i11.u88.LeafSetOfRxIsSentToNode3>=1)))||((i0.i1.u22.Node0DontAnswerToAnyNode>=1)&&(i4.u61.Node6IsActive>=1)))||((i7.i2.u21.Node2WantsToManageTheBreakDownOfNode5>=1)&&(i7.i2.u27.NoNodeManageTheBreakDownOfNode5>=1)))||((i1.u39.Node3HasAskedItsLeafSetToRxToReplaceNode8>=1)&&(i11.u88.LeafSetOfRxIsSentToNode3>=1))))))) U (!((E(!(EG(!((((((((((i7.i0.u8.Node6DontAnswerToAnyNode>=1)&&(i10.u78.Node8IsActive>=1))||(i9.u75.Node7ManageTheBreakDownOfNode6>=1))||((i0.i2.u25.RequestOfNode2IsSentToLx>=1)&&(u87.LxIsActiveAndNotInTheLeafSet>=1)))||(i5.u50.RightNodeHasDetectedBreakDownOfMaster>=1))||((i7.i0.u47.NoNodeManageTheBreakDownOfNode6>=1)&&(i9.u75.Node7WantsToManageTheBreakDownOfNode6>=1)))||(i6.i1.u11.Node0ManageTheBreakDownOfNode8>=1))||((i2.i1.u3.Node2DontAnswerToAnyNode>=1)&&(i8.u52.Node5IsActive>=1)))||((i0.i0.u23.NoNodeManageTheBreakDownOfNode1>=1)&&(i0.i0.u42.Node4WantsToManageTheBreakDownOfNode1>=1)))))) U ((((((((((i0.i0.u2.Node0WantsToManageTheBreakDownOfNode1<1)||(i0.i0.u23.NoNodeManageTheBreakDownOfNode1<1))&&(i8.u53.Node5ManageTheBreakDownOfNode2<1))&&((i2.i0.u14.Node1HasAskedItsLeafSetToLxToReplaceNode3<1)||(u87.LeafSetOfLxIsSentToNode1<1)))&&((i1.u31.Node3IsActive<1)||(i6.i1.u10.Node8DontAnswerToAnyNode<1)))&&((i6.i0.u0.Node0IsActive<1)||(i6.i1.u10.Node8DontAnswerToAnyNode<1)))&&((i0.i0.u23.Node2HasAskedItsLeafSetToLxToReplaceNode1<1)||(u87.LeafSetOfLxIsSentToNode2<1)))&&((i6.i0.u0.Node0IsActive<1)||(i7.i0.u8.Node6DontAnswerToAnyNode<1)))&&((i7.i2.u21.Node2IsActive<1)||(i0.i2.u24.Node3DontAnswerToAnyNode<1))) * !(E(TRUE U !((((((((((i2.i1.u3.Node0WantsToManageTheBreakDownOfNode2>=1)&&(i2.i1.u4.NoNodeManageTheBreakDownOfNode2>=1))||((i4.u60.Node6HasAskedItsLeafSetToLxToReplaceNode0>=1)&&(u87.LeafSetOfLxIsSentToNode6>=1)))||((i8.u51.Node5HasAskedItsLeafSetToLxToReplaceNode0>=1)&&(u87.LeafSetOfLxIsSentToNode5>=1)))||(i6.i1.u30.Node2ManageTheBreakDownOfNode8>=1))||(u87.Node8HasTheLeafSetOfLxToReplaceNode2>=1))||(i11.u88.Node5HasTheLeafSetOfRxToReplaceNode4>=1))||(u87.Node6HasTheLeafSetOfLxToReplaceNode1>=1))||((i0.i2.u24.Node3DontAnswerToAnyNode>=1)&&(i9.u70.Node7IsActive>=1)))))))) + ((((((((((i4.u63.Node6ManageTheBreakDownOfNode3<1)&&(i6.i1.u30.Node2ManageTheBreakDownOfNode8<1))&&(i11.u88.Node6HasTheLeafSetOfRxToReplaceNode5<1))&&(i11.u88.Node5HasTheLeafSetOfRxToReplaceNode4<1))&&(u87.LxHasReceivedTheRequestOfNode4<1))&&(i6.i1.u58.Node5ManageTheBreakDownOfNode8<1)) * !(EX(!(((((((((i3.u29.Node2ManageTheBreakDownOfNode7>=1)||((i2.i1.u3.Node0WantsToManageTheBreakDownOfNode2>=1)&&(i2.i1.u4.NoNodeManageTheBreakDownOfNode2>=1)))||(i11.u88.RxHasReceivedTheRequestOfNode3>=1))||(i5.u6.Node0ManageTheBreakDownOfNode4>=1))||((i5.u55.RequestOfNode5IsSentToRx>=1)&&(i11.u88.RxIsActiveAndNotInTheLeafSet>=1)))||(i0.i0.u69.Node7ManageTheBreakDownOfNode1>=1))||((i4.u61.Node6IsActive>=1)&&(i3.u18.Node7DontAnswerToAnyNode>=1)))&&(((((((((i11.u46.RxHasReceivedTheRequestOfNode4>=1)||((i7.i2.u21.Node2IsActive>=1)&&(i6.i1.u10.Node8DontAnswerToAnyNode>=1)))||(u87.Node1HasTheLeafSetOfLxToReplaceNode4>=1))||((i5.u82.Node8HasAskedItsLeafSetToRxToReplaceNode4>=1)&&(i11.u86.LeafSetOfRxIsSentToNode8>=1)))||((i0.i2.u25.Node2HasAskedItsLeafSetToLxToReplaceNode3>=1)&&(u87.LeafSetOfLxIsSentToNode2>=1)))||(u87.LxHasReceivedTheRequestOfNode6>=1))||(u87.Node7HasTheLeafSetOfLxToReplaceNode3>=1))||(i11.u88.Node2HasTheLeafSetOfRxToReplaceNode6>=1))||(u87.Node8HasTheLeafSetOfLxToReplaceNode3>=1))))))) * ((i1.u38.Node3WantsToManageTheBreakDownOfNode7<1)||(i3.u48.NoNodeManageTheBreakDownOfNode7<1))) * ((i0.i1.u68.NoNodeManageTheBreakDownOfNode0<1)||(i8.u51.Node5WantsToManageTheBreakDownOfNode0<1))) * ((i0.i1.u22.Node0DontAnswerToAnyNode<1)||(i4.u61.Node6IsActive<1))))) * !(!(E(TRUE U !(((((((i11.u88.RxHasReceivedTheRequestOfNode7>=1)||(i11.u88.RxHasReceivedTheRequestOfNode5>=1))||((i1.u38.Node3HasAskedItsLeafSetToRxToReplaceNode7>=1)&&(i11.u88.LeafSetOfRxIsSentToNode3>=1)))||((i0.i1.u22.Node0DontAnswerToAnyNode>=1)&&(i4.u61.Node6IsActive>=1)))||((i7.i2.u21.Node2WantsToManageTheBreakDownOfNode5>=1)&&(i7.i2.u27.NoNodeManageTheBreakDownOfNode5>=1)))||((i1.u39.Node3HasAskedItsLeafSetToRxToReplaceNode8>=1)&&(i11.u88.LeafSetOfRxIsSentToNode3>=1)))))))))))] != FALSE
(forward)formula 2,0,130.362,2300424,1,0,1.29705e+06,699380,4131,6.14187e+06,1252,2.59804e+07,2303512
FORMULA LeafsetExtension-PT-S08C2-CTLFireability-02 FALSE TECHNIQUES DECISION_DIAGRAMS TOPOLOGICAL USE_NUPN
Formula is FALSE !
***************************************
original formula: E(EF(((((i11.u88.Node2HasTheLeafSetOfRxToReplaceNode8>=1)||((i2.i1.u4.NoNodeManageTheBreakDownOfNode2>=1)&&(i8.u53.Node5WantsToManageTheBreakDownOfNode2>=1))) + (A((((((((((((i5.u6.NoNodeManageTheBreakDownOfNode4>=1)&&(i5.u55.Node5WantsToManageTheBreakDownOfNode4>=1))||((i6.i0.u0.Node0IsActive>=1)&&(i2.i1.u3.Node2DontAnswerToAnyNode>=1)))||(i0.i1.u41.Node4ManageTheBreakDownOfNode0>=1))||((i1.u31.Node3IsActive>=1)&&(i7.i2.u59.Node5DontAnswerToAnyNode>=1)))||((i0.i0.u1.Node1DontAnswerToAnyNode>=1)&&(i4.u61.Node6IsActive>=1)))||((i0.i0.u1.BreakDownReservoir>=1)&&(i2.i0.u12.Node1IsActive>=1)))||(i7.i2.u16.Node1ManageTheBreakDownOfNode5>=1))||((i0.i1.u22.Node0DontAnswerToAnyNode>=1)&&(i2.i0.u12.Node1IsActive>=1)))||(i5.u82.Node8ManageTheBreakDownOfNode4>=1))||((i8.u53.Node5HasAskedItsLeafSetToLxToReplaceNode2>=1)&&(u87.LeafSetOfLxIsSentToNode5>=1))) U (((((((((i6.i0.u9.Node0ManageTheBreakDownOfNode7>=1)||((i5.u82.Node8HasAskedItsLeafSetToRxToReplaceNode4>=1)&&(i11.u86.LeafSetOfRxIsSentToNode8>=1)))||(i11.u88.Node1HasTheLeafSetOfRxToReplaceNode7>=1))||((i2.i1.u3.Node2DontAnswerToAnyNode>=1)&&(i7.i1.u40.Node4IsActive>=1)))||((i2.i1.u3.Node2DontAnswerToAnyNode>=1)&&(i1.u31.Node3IsActive>=1)))||((i7.i2.u65.Node6HasAskedItsLeafSetToRxToReplaceNode5>=1)&&(i11.u88.LeafSetOfRxIsSentToNode6>=1)))||(u87.Node2HasTheLeafSetOfLxToReplaceNode4>=1))||(i11.u88.Node0HasTheLeafSetOfRxToReplaceNode8>=1))||((i2.i0.u12.Node1IsActive>=1)&&(i6.i1.u10.Node8DontAnswerToAnyNode>=1)))) * EF(((((((i2.i1.u4.Node0HasAskedItsLeafSetToLxToReplaceNode2>=1)&&(u87.LeafSetOfLxIsSentToNode0>=1))||((i2.i1.u4.NoNodeManageTheBreakDownOfNode2>=1)&&(i2.i1.u71.Node7WantsToManageTheBreakDownOfNode2>=1)))||(i11.u88.Node7HasTheLeafSetOfRxToReplaceNode8>=1))||((i7.i2.u21.Node2WantsToManageTheBreakDownOfNode5>=1)&&(i7.i2.u27.NoNodeManageTheBreakDownOfNode5>=1)))||((i6.i1.u67.Node6HasAskedItsLeafSetToRxToReplaceNode8>=1)&&(i11.u88.LeafSetOfRxIsSentToNode6>=1)))))) * ((((((((((((((((i11.u88.Node5HasTheLeafSetOfRxToReplaceNode8>=1)||(i11.u88.Node7HasTheLeafSetOfRxToReplaceNode6>=1))||(i8.u51.Node5ManageTheBreakDownOfNode0>=1))||(i4.u62.Node6ManageTheBreakDownOfNode2>=1))||(i0.i2.u44.Node4ManageTheBreakDownOfNode3>=1))||(u87.LxHasReceivedTheRequestOfNode7>=1)) + AF(((((u87.Node5HasTheLeafSetOfLxToReplaceNode2>=1)||(u87.Node1HasTheLeafSetOfLxToReplaceNode0>=1))||(i11.u88.Node3HasTheLeafSetOfRxToReplaceNode8>=1))||(i1.u39.Node3ManageTheBreakDownOfNode8>=1)))) + ((i7.i0.u8.Node0HasAskedItsLeafSetToRxToReplaceNode6>=1)&&(i11.u88.LeafSetOfRxIsSentToNode0>=1))) + ((i7.i0.u84.Node8HasAskedItsLeafSetToRxToReplaceNode6>=1)&&(i11.u86.LeafSetOfRxIsSentToNode8>=1))) + ((i5.u64.Node6HasAskedItsLeafSetToRxToReplaceNode4>=1)&&(i11.u88.LeafSetOfRxIsSentToNode6>=1))) + ((i7.i1.u49.Node4WantsToManageTheBreakDownOfNode8>=1)&&(i6.i1.u11.NoNodeManageTheBreakDownOfNode8>=1))) + ((i7.i2.u83.RequestOfNode8IsSentToRx>=1)&&(i11.u88.RxIsActiveAndNotInTheLeafSet>=1))) + ((i1.u31.Node3IsActive>=1)&&(i3.u18.Node7DontAnswerToAnyNode>=1))) + ((i0.i0.u1.BreakDownReservoir>=1)&&(i1.u31.Node3IsActive>=1))) + ((i1.u39.Node3HasAskedItsLeafSetToRxToReplaceNode8>=1)&&(i11.u88.LeafSetOfRxIsSentToNode3>=1))) + ((AF((((((i11.u88.Node8HasTheLeafSetOfRxToReplaceNode6>=1)||((i1.u31.Node3IsActive>=1)&&(i5.u50.Node4DontAnswerToAnyNode>=1)))||((i3.u48.Node4HasAskedItsLeafSetToRxToReplaceNode7>=1)&&(i11.u46.LeafSetOfRxIsSentToNode4>=1)))||(u87.Node1HasTheLeafSetOfLxToReplaceNode2>=1))||((i4.u61.Node6IsActive>=1)&&(i3.u18.Node7DontAnswerToAnyNode>=1)))) * (((((u87.Node3HasTheLeafSetOfLxToReplaceNode4>=1) + E((((((((((i3.u29.Node2ManageTheBreakDownOfNode7>=1)||((i0.i2.u5.Node0HasAskedItsLeafSetToLxToReplaceNode3>=1)&&(u87.LeafSetOfLxIsSentToNode0>=1)))||((i7.i2.u59.Node5DontAnswerToAnyNode>=1)&&(i4.u61.Node6IsActive>=1)))||((i0.i0.u1.BreakDownReservoir>=1)&&(i2.i0.u12.Node1IsActive>=1)))||(u87.LxHasReceivedTheRequestOfNode8>=1))||((i0.i0.u23.NoNodeManageTheBreakDownOfNode1>=1)&&(i0.i0.u33.Node3WantsToManageTheBreakDownOfNode1>=1)))||((i2.i0.u12.Node1IsActive>=1)&&(i5.u50.Node4DontAnswerToAnyNode>=1)))||((i6.i0.u0.Node0IsActive>=1)&&(i3.u18.Node7DontAnswerToAnyNode>=1)))||((i0.i0.u23.Node2HasAskedItsLeafSetToLxToReplaceNode1>=1)&&(u87.LeafSetOfLxIsSentToNode2>=1))) U (((i10.u77.Node8HasAskedItsLeafSetToLxToReplaceNode0>=1)&&(u87.LeafSetOfLxIsSentToNode8>=1))||((i3.u19.Node1HasAskedItsLeafSetToRxToReplaceNode7>=1)&&(i11.u88.LeafSetOfRxIsSentToNode1>=1))))) + ((i7.i2.u21.Node2IsActive>=1)&&(i6.i1.u10.Node8DontAnswerToAnyNode>=1))) + ((i6.i1.u58.Node5HasAskedItsLeafSetToRxToReplaceNode8>=1)&&(i11.u88.LeafSetOfRxIsSentToNode5>=1))) + ((i0.i2.u24.Node3DontAnswerToAnyNode>=1)&&(i9.u70.Node7IsActive>=1)))) * ((((((((i11.u88.Node6HasTheLeafSetOfRxToReplaceNode7>=1)||(i3.u19.Node1ManageTheBreakDownOfNode7>=1))||(i6.i0.u7.Node0ManageTheBreakDownOfNode5>=1))||((i5.u6.NoNodeManageTheBreakDownOfNode4>=1)&&(i5.u82.Node8WantsToManageTheBreakDownOfNode4>=1)))||((i0.i0.u2.Node0WantsToManageTheBreakDownOfNode1>=1)&&(i0.i0.u23.NoNodeManageTheBreakDownOfNode1>=1)))||((i6.i0.u0.Node0IsActive>=1)&&(i3.u18.Node7DontAnswerToAnyNode>=1)))||((i0.i2.u5.NoNodeManageTheBreakDownOfNode3>=1)&&(i0.i2.u44.Node4WantsToManageTheBreakDownOfNode3>=1)))||((i2.i0.u12.Node1IsActive>=1)&&(i3.u18.Node7DontAnswerToAnyNode>=1))))))) U (!(EF((((((((((((((((((((((((((((i9.u76.Node7WantsToManageTheBreakDownOfNode8>=1)&&(i6.i1.u11.NoNodeManageTheBreakDownOfNode8>=1))||(i9.u75.Node7ManageTheBreakDownOfNode6>=1))||(i3.u57.Node5ManageTheBreakDownOfNode7>=1))||(i0.i2.u72.Node7ManageTheBreakDownOfNode3>=1))||((i0.i1.u22.Node0DontAnswerToAnyNode>=1)&&(i9.u70.Node7IsActive>=1)))||(u87.Node3HasTheLeafSetOfLxToReplaceNode4>=1))||(i2.i1.u4.Node0ManageTheBreakDownOfNode2>=1))||((i8.u52.Node5IsActive>=1)&&(i6.i1.u10.Node8DontAnswerToAnyNode>=1)))||(i5.u64.Node6ManageTheBreakDownOfNode4>=1))&&((i3.u57.Node5ManageTheBreakDownOfNode7>=1)||((i7.i2.u21.Node2IsActive>=1)&&(i3.u18.Node7DontAnswerToAnyNode>=1))))||(i2.i0.u13.Node1ManageTheBreakDownOfNode2>=1))||(u87.Node6HasTheLeafSetOfLxToReplaceNode1>=1))||(i1.u39.Node3ManageTheBreakDownOfNode8>=1))||(i6.i0.u9.Node0ManageTheBreakDownOfNode7>=1))||(i11.u88.RxHasReceivedTheRequestOfNode1>=1))||((i2.i1.u4.NoNodeManageTheBreakDownOfNode2>=1)&&(i2.i1.u34.Node3WantsToManageTheBreakDownOfNode2>=1)))||((i0.i1.u68.NoNodeManageTheBreakDownOfNode0>=1)&&(i0.i1.u41.Node4WantsToManageTheBreakDownOfNode0>=1)))||(i7.i2.u16.Node1ManageTheBreakDownOfNode5>=1))||((i6.i1.u10.Node0WantsToManageTheBreakDownOfNode8>=1)&&(i6.i1.u11.NoNodeManageTheBreakDownOfNode8>=1)))||((i3.u57.Node5HasAskedItsLeafSetToRxToReplaceNode7>=1)&&(i11.u88.LeafSetOfRxIsSentToNode5>=1)))||((i7.i2.u83.RequestOfNode8IsSentToRx>=1)&&(i11.u88.RxIsActiveAndNotInTheLeafSet>=1)))||((i0.i0.u1.BreakDownReservoir>=1)&&(i6.i0.u0.Node0IsActive>=1)))||(u87.Node4HasTheLeafSetOfLxToReplaceNode3>=1))||((i0.i0.u23.NoNodeManageTheBreakDownOfNode1>=1)&&(i0.i0.u69.Node7WantsToManageTheBreakDownOfNode1>=1)))||(i11.u88.Node1HasTheLeafSetOfRxToReplaceNode6>=1))||(i2.i0.u14.Node1ManageTheBreakDownOfNode3>=1)))) * EG(EX(E(((((((((i7.i0.u28.RequestOfNode2IsSentToRx>=1)&&(i11.u88.RxIsActiveAndNotInTheLeafSet>=1))||(i0.i1.u68.Node7ManageTheBreakDownOfNode0>=1))||(i8.u51.Node5ManageTheBreakDownOfNode0>=1))||((i7.i2.u83.RequestOfNode8IsSentToRx>=1)&&(i11.u88.RxIsActiveAndNotInTheLeafSet>=1)))||((i0.i0.u69.RequestOfNode7IsSentToLx>=1)&&(u87.LxIsActiveAndNotInTheLeafSet>=1)))||(i10.u79.Node8ManageTheBreakDownOfNode1>=1))||(i0.i0.u33.Node3ManageTheBreakDownOfNode1>=1)) U ((((((((((i2.i1.u4.NoNodeManageTheBreakDownOfNode2>=1)&&(i4.u62.Node6WantsToManageTheBreakDownOfNode2>=1))||((i7.i0.u56.Node5WantsToManageTheBreakDownOfNode6>=1)&&(i7.i0.u47.NoNodeManageTheBreakDownOfNode6>=1)))||((i0.i0.u1.BreakDownReservoir>=1)&&(i7.i2.u21.Node2IsActive>=1)))||(i11.u88.Node8HasTheLeafSetOfRxToReplaceNode4>=1))||((i0.i2.u5.NoNodeManageTheBreakDownOfNode3>=1)&&(i0.i2.u44.Node4WantsToManageTheBreakDownOfNode3>=1)))||(i1.u37.Node3ManageTheBreakDownOfNode6>=1))||(u87.LxHasReceivedTheRequestOfNode3>=1))||((i0.i1.u22.Node0DontAnswerToAnyNode>=1)&&(i1.u31.Node3IsActive>=1)))||(i11.u88.RxHasReceivedTheRequestOfNode7>=1)))))))
=> equivalent forward existential formula: [FwdG((FwdU(Init,E(TRUE U ((((i11.u88.Node2HasTheLeafSetOfRxToReplaceNode8>=1)||((i2.i1.u4.NoNodeManageTheBreakDownOfNode2>=1)&&(i8.u53.Node5WantsToManageTheBreakDownOfNode2>=1))) + (!((E(!((((((((((i6.i0.u9.Node0ManageTheBreakDownOfNode7>=1)||((i5.u82.Node8HasAskedItsLeafSetToRxToReplaceNode4>=1)&&(i11.u86.LeafSetOfRxIsSentToNode8>=1)))||(i11.u88.Node1HasTheLeafSetOfRxToReplaceNode7>=1))||((i2.i1.u3.Node2DontAnswerToAnyNode>=1)&&(i7.i1.u40.Node4IsActive>=1)))||((i2.i1.u3.Node2DontAnswerToAnyNode>=1)&&(i1.u31.Node3IsActive>=1)))||((i7.i2.u65.Node6HasAskedItsLeafSetToRxToReplaceNode5>=1)&&(i11.u88.LeafSetOfRxIsSentToNode6>=1)))||(u87.Node2HasTheLeafSetOfLxToReplaceNode4>=1))||(i11.u88.Node0HasTheLeafSetOfRxToReplaceNode8>=1))||((i2.i0.u12.Node1IsActive>=1)&&(i6.i1.u10.Node8DontAnswerToAnyNode>=1)))) U (!((((((((((((i5.u6.NoNodeManageTheBreakDownOfNode4>=1)&&(i5.u55.Node5WantsToManageTheBreakDownOfNode4>=1))||((i6.i0.u0.Node0IsActive>=1)&&(i2.i1.u3.Node2DontAnswerToAnyNode>=1)))||(i0.i1.u41.Node4ManageTheBreakDownOfNode0>=1))||((i1.u31.Node3IsActive>=1)&&(i7.i2.u59.Node5DontAnswerToAnyNode>=1)))||((i0.i0.u1.Node1DontAnswerToAnyNode>=1)&&(i4.u61.Node6IsActive>=1)))||((i0.i0.u1.BreakDownReservoir>=1)&&(i2.i0.u12.Node1IsActive>=1)))||(i7.i2.u16.Node1ManageTheBreakDownOfNode5>=1))||((i0.i1.u22.Node0DontAnswerToAnyNode>=1)&&(i2.i0.u12.Node1IsActive>=1)))||(i5.u82.Node8ManageTheBreakDownOfNode4>=1))||((i8.u53.Node5HasAskedItsLeafSetToLxToReplaceNode2>=1)&&(u87.LeafSetOfLxIsSentToNode5>=1)))) * !((((((((((i6.i0.u9.Node0ManageTheBreakDownOfNode7>=1)||((i5.u82.Node8HasAskedItsLeafSetToRxToReplaceNode4>=1)&&(i11.u86.LeafSetOfRxIsSentToNode8>=1)))||(i11.u88.Node1HasTheLeafSetOfRxToReplaceNode7>=1))||((i2.i1.u3.Node2DontAnswerToAnyNode>=1)&&(i7.i1.u40.Node4IsActive>=1)))||((i2.i1.u3.Node2DontAnswerToAnyNode>=1)&&(i1.u31.Node3IsActive>=1)))||((i7.i2.u65.Node6HasAskedItsLeafSetToRxToReplaceNode5>=1)&&(i11.u88.LeafSetOfRxIsSentToNode6>=1)))||(u87.Node2HasTheLeafSetOfLxToReplaceNode4>=1))||(i11.u88.Node0HasTheLeafSetOfRxToReplaceNode8>=1))||((i2.i0.u12.Node1IsActive>=1)&&(i6.i1.u10.Node8DontAnswerToAnyNode>=1)))))) + EG(!((((((((((i6.i0.u9.Node0ManageTheBreakDownOfNode7>=1)||((i5.u82.Node8HasAskedItsLeafSetToRxToReplaceNode4>=1)&&(i11.u86.LeafSetOfRxIsSentToNode8>=1)))||(i11.u88.Node1HasTheLeafSetOfRxToReplaceNode7>=1))||((i2.i1.u3.Node2DontAnswerToAnyNode>=1)&&(i7.i1.u40.Node4IsActive>=1)))||((i2.i1.u3.Node2DontAnswerToAnyNode>=1)&&(i1.u31.Node3IsActive>=1)))||((i7.i2.u65.Node6HasAskedItsLeafSetToRxToReplaceNode5>=1)&&(i11.u88.LeafSetOfRxIsSentToNode6>=1)))||(u87.Node2HasTheLeafSetOfLxToReplaceNode4>=1))||(i11.u88.Node0HasTheLeafSetOfRxToReplaceNode8>=1))||((i2.i0.u12.Node1IsActive>=1)&&(i6.i1.u10.Node8DontAnswerToAnyNode>=1))))))) * E(TRUE U ((((((i2.i1.u4.Node0HasAskedItsLeafSetToLxToReplaceNode2>=1)&&(u87.LeafSetOfLxIsSentToNode0>=1))||((i2.i1.u4.NoNodeManageTheBreakDownOfNode2>=1)&&(i2.i1.u71.Node7WantsToManageTheBreakDownOfNode2>=1)))||(i11.u88.Node7HasTheLeafSetOfRxToReplaceNode8>=1))||((i7.i2.u21.Node2WantsToManageTheBreakDownOfNode5>=1)&&(i7.i2.u27.NoNodeManageTheBreakDownOfNode5>=1)))||((i6.i1.u67.Node6HasAskedItsLeafSetToRxToReplaceNode8>=1)&&(i11.u88.LeafSetOfRxIsSentToNode6>=1)))))) * ((((((((((((((((i11.u88.Node5HasTheLeafSetOfRxToReplaceNode8>=1)||(i11.u88.Node7HasTheLeafSetOfRxToReplaceNode6>=1))||(i8.u51.Node5ManageTheBreakDownOfNode0>=1))||(i4.u62.Node6ManageTheBreakDownOfNode2>=1))||(i0.i2.u44.Node4ManageTheBreakDownOfNode3>=1))||(u87.LxHasReceivedTheRequestOfNode7>=1)) + !(EG(!(((((u87.Node5HasTheLeafSetOfLxToReplaceNode2>=1)||(u87.Node1HasTheLeafSetOfLxToReplaceNode0>=1))||(i11.u88.Node3HasTheLeafSetOfRxToReplaceNode8>=1))||(i1.u39.Node3ManageTheBreakDownOfNode8>=1)))))) + ((i7.i0.u8.Node0HasAskedItsLeafSetToRxToReplaceNode6>=1)&&(i11.u88.LeafSetOfRxIsSentToNode0>=1))) + ((i7.i0.u84.Node8HasAskedItsLeafSetToRxToReplaceNode6>=1)&&(i11.u86.LeafSetOfRxIsSentToNode8>=1))) + ((i5.u64.Node6HasAskedItsLeafSetToRxToReplaceNode4>=1)&&(i11.u88.LeafSetOfRxIsSentToNode6>=1))) + ((i7.i1.u49.Node4WantsToManageTheBreakDownOfNode8>=1)&&(i6.i1.u11.NoNodeManageTheBreakDownOfNode8>=1))) + ((i7.i2.u83.RequestOfNode8IsSentToRx>=1)&&(i11.u88.RxIsActiveAndNotInTheLeafSet>=1))) + ((i1.u31.Node3IsActive>=1)&&(i3.u18.Node7DontAnswerToAnyNode>=1))) + ((i0.i0.u1.BreakDownReservoir>=1)&&(i1.u31.Node3IsActive>=1))) + ((i1.u39.Node3HasAskedItsLeafSetToRxToReplaceNode8>=1)&&(i11.u88.LeafSetOfRxIsSentToNode3>=1))) + ((!(EG(!((((((i11.u88.Node8HasTheLeafSetOfRxToReplaceNode6>=1)||((i1.u31.Node3IsActive>=1)&&(i5.u50.Node4DontAnswerToAnyNode>=1)))||((i3.u48.Node4HasAskedItsLeafSetToRxToReplaceNode7>=1)&&(i11.u46.LeafSetOfRxIsSentToNode4>=1)))||(u87.Node1HasTheLeafSetOfLxToReplaceNode2>=1))||((i4.u61.Node6IsActive>=1)&&(i3.u18.Node7DontAnswerToAnyNode>=1)))))) * (((((u87.Node3HasTheLeafSetOfLxToReplaceNode4>=1) + E((((((((((i3.u29.Node2ManageTheBreakDownOfNode7>=1)||((i0.i2.u5.Node0HasAskedItsLeafSetToLxToReplaceNode3>=1)&&(u87.LeafSetOfLxIsSentToNode0>=1)))||((i7.i2.u59.Node5DontAnswerToAnyNode>=1)&&(i4.u61.Node6IsActive>=1)))||((i0.i0.u1.BreakDownReservoir>=1)&&(i2.i0.u12.Node1IsActive>=1)))||(u87.LxHasReceivedTheRequestOfNode8>=1))||((i0.i0.u23.NoNodeManageTheBreakDownOfNode1>=1)&&(i0.i0.u33.Node3WantsToManageTheBreakDownOfNode1>=1)))||((i2.i0.u12.Node1IsActive>=1)&&(i5.u50.Node4DontAnswerToAnyNode>=1)))||((i6.i0.u0.Node0IsActive>=1)&&(i3.u18.Node7DontAnswerToAnyNode>=1)))||((i0.i0.u23.Node2HasAskedItsLeafSetToLxToReplaceNode1>=1)&&(u87.LeafSetOfLxIsSentToNode2>=1))) U (((i10.u77.Node8HasAskedItsLeafSetToLxToReplaceNode0>=1)&&(u87.LeafSetOfLxIsSentToNode8>=1))||((i3.u19.Node1HasAskedItsLeafSetToRxToReplaceNode7>=1)&&(i11.u88.LeafSetOfRxIsSentToNode1>=1))))) + ((i7.i2.u21.Node2IsActive>=1)&&(i6.i1.u10.Node8DontAnswerToAnyNode>=1))) + ((i6.i1.u58.Node5HasAskedItsLeafSetToRxToReplaceNode8>=1)&&(i11.u88.LeafSetOfRxIsSentToNode5>=1))) + ((i0.i2.u24.Node3DontAnswerToAnyNode>=1)&&(i9.u70.Node7IsActive>=1)))) * ((((((((i11.u88.Node6HasTheLeafSetOfRxToReplaceNode7>=1)||(i3.u19.Node1ManageTheBreakDownOfNode7>=1))||(i6.i0.u7.Node0ManageTheBreakDownOfNode5>=1))||((i5.u6.NoNodeManageTheBreakDownOfNode4>=1)&&(i5.u82.Node8WantsToManageTheBreakDownOfNode4>=1)))||((i0.i0.u2.Node0WantsToManageTheBreakDownOfNode1>=1)&&(i0.i0.u23.NoNodeManageTheBreakDownOfNode1>=1)))||((i6.i0.u0.Node0IsActive>=1)&&(i3.u18.Node7DontAnswerToAnyNode>=1)))||((i0.i2.u5.NoNodeManageTheBreakDownOfNode3>=1)&&(i0.i2.u44.Node4WantsToManageTheBreakDownOfNode3>=1)))||((i2.i0.u12.Node1IsActive>=1)&&(i3.u18.Node7DontAnswerToAnyNode>=1)))))))) * !(E(TRUE U (((((((((((((((((((((((((((i9.u76.Node7WantsToManageTheBreakDownOfNode8>=1)&&(i6.i1.u11.NoNodeManageTheBreakDownOfNode8>=1))||(i9.u75.Node7ManageTheBreakDownOfNode6>=1))||(i3.u57.Node5ManageTheBreakDownOfNode7>=1))||(i0.i2.u72.Node7ManageTheBreakDownOfNode3>=1))||((i0.i1.u22.Node0DontAnswerToAnyNode>=1)&&(i9.u70.Node7IsActive>=1)))||(u87.Node3HasTheLeafSetOfLxToReplaceNode4>=1))||(i2.i1.u4.Node0ManageTheBreakDownOfNode2>=1))||((i8.u52.Node5IsActive>=1)&&(i6.i1.u10.Node8DontAnswerToAnyNode>=1)))||(i5.u64.Node6ManageTheBreakDownOfNode4>=1))&&((i3.u57.Node5ManageTheBreakDownOfNode7>=1)||((i7.i2.u21.Node2IsActive>=1)&&(i3.u18.Node7DontAnswerToAnyNode>=1))))||(i2.i0.u13.Node1ManageTheBreakDownOfNode2>=1))||(u87.Node6HasTheLeafSetOfLxToReplaceNode1>=1))||(i1.u39.Node3ManageTheBreakDownOfNode8>=1))||(i6.i0.u9.Node0ManageTheBreakDownOfNode7>=1))||(i11.u88.RxHasReceivedTheRequestOfNode1>=1))||((i2.i1.u4.NoNodeManageTheBreakDownOfNode2>=1)&&(i2.i1.u34.Node3WantsToManageTheBreakDownOfNode2>=1)))||((i0.i1.u68.NoNodeManageTheBreakDownOfNode0>=1)&&(i0.i1.u41.Node4WantsToManageTheBreakDownOfNode0>=1)))||(i7.i2.u16.Node1ManageTheBreakDownOfNode5>=1))||((i6.i1.u10.Node0WantsToManageTheBreakDownOfNode8>=1)&&(i6.i1.u11.NoNodeManageTheBreakDownOfNode8>=1)))||((i3.u57.Node5HasAskedItsLeafSetToRxToReplaceNode7>=1)&&(i11.u88.LeafSetOfRxIsSentToNode5>=1)))||((i7.i2.u83.RequestOfNode8IsSentToRx>=1)&&(i11.u88.RxIsActiveAndNotInTheLeafSet>=1)))||((i0.i0.u1.BreakDownReservoir>=1)&&(i6.i0.u0.Node0IsActive>=1)))||(u87.Node4HasTheLeafSetOfLxToReplaceNode3>=1))||((i0.i0.u23.NoNodeManageTheBreakDownOfNode1>=1)&&(i0.i0.u69.Node7WantsToManageTheBreakDownOfNode1>=1)))||(i11.u88.Node1HasTheLeafSetOfRxToReplaceNode6>=1))||(i2.i0.u14.Node1ManageTheBreakDownOfNode3>=1))))),EX(E(((((((((i7.i0.u28.RequestOfNode2IsSentToRx>=1)&&(i11.u88.RxIsActiveAndNotInTheLeafSet>=1))||(i0.i1.u68.Node7ManageTheBreakDownOfNode0>=1))||(i8.u51.Node5ManageTheBreakDownOfNode0>=1))||((i7.i2.u83.RequestOfNode8IsSentToRx>=1)&&(i11.u88.RxIsActiveAndNotInTheLeafSet>=1)))||((i0.i0.u69.RequestOfNode7IsSentToLx>=1)&&(u87.LxIsActiveAndNotInTheLeafSet>=1)))||(i10.u79.Node8ManageTheBreakDownOfNode1>=1))||(i0.i0.u33.Node3ManageTheBreakDownOfNode1>=1)) U ((((((((((i2.i1.u4.NoNodeManageTheBreakDownOfNode2>=1)&&(i4.u62.Node6WantsToManageTheBreakDownOfNode2>=1))||((i7.i0.u56.Node5WantsToManageTheBreakDownOfNode6>=1)&&(i7.i0.u47.NoNodeManageTheBreakDownOfNode6>=1)))||((i0.i0.u1.BreakDownReservoir>=1)&&(i7.i2.u21.Node2IsActive>=1)))||(i11.u88.Node8HasTheLeafSetOfRxToReplaceNode4>=1))||((i0.i2.u5.NoNodeManageTheBreakDownOfNode3>=1)&&(i0.i2.u44.Node4WantsToManageTheBreakDownOfNode3>=1)))||(i1.u37.Node3ManageTheBreakDownOfNode6>=1))||(u87.LxHasReceivedTheRequestOfNode3>=1))||((i0.i1.u22.Node0DontAnswerToAnyNode>=1)&&(i1.u31.Node3IsActive>=1)))||(i11.u88.RxHasReceivedTheRequestOfNode7>=1)))))] != FALSE
dead was empty
(forward)formula 3,0,153.528,2300424,1,0,1.29705e+06,699380,5345,6.14187e+06,1305,2.59804e+07,4854674
FORMULA LeafsetExtension-PT-S08C2-CTLFireability-03 FALSE TECHNIQUES DECISION_DIAGRAMS TOPOLOGICAL USE_NUPN
Formula is FALSE !
***************************************
original formula: E((((((i1.u36.Node3ManageTheBreakDownOfNode5>=1)||(u87.Node0HasTheLeafSetOfLxToReplaceNode2>=1))||(i11.u88.Node0HasTheLeafSetOfRxToReplaceNode6>=1))||((i0.i0.u1.Node1DontAnswerToAnyNode>=1)&&(i7.i1.u40.Node4IsActive>=1)))||((i2.i0.u14.Node1WantsToManageTheBreakDownOfNode3>=1)&&(i0.i2.u5.NoNodeManageTheBreakDownOfNode3>=1))) U (EF((((((((((i5.u6.NoNodeManageTheBreakDownOfNode4<1)||(i5.u55.Node5WantsToManageTheBreakDownOfNode4<1))&&((i1.u31.Node3WantsToManageTheBreakDownOfNode6<1)||(i7.i0.u47.NoNodeManageTheBreakDownOfNode6<1)))&&((i2.i0.u13.Node1WantsToManageTheBreakDownOfNode2<1)||(i2.i1.u4.NoNodeManageTheBreakDownOfNode2<1)))&&(i4.u62.Node6ManageTheBreakDownOfNode2<1))&&((i1.u31.Node3IsActive<1)||(i6.i1.u10.Node8DontAnswerToAnyNode<1)))&&(i11.u88.Node6HasTheLeafSetOfRxToReplaceNode4<1))&&((i10.u79.Node8HasAskedItsLeafSetToLxToReplaceNode1<1)||(u87.LeafSetOfLxIsSentToNode8<1))) + ((((((((((((((i0.i0.u1.Node1DontAnswerToAnyNode>=1)&&(i7.i2.u21.Node2IsActive>=1))||((i7.i2.u21.Node2IsActive>=1)&&(i7.i0.u8.Node6DontAnswerToAnyNode>=1)))||(u87.Node3HasTheLeafSetOfLxToReplaceNode0>=1))||(u87.Node2HasTheLeafSetOfLxToReplaceNode4>=1))||(u87.Node1HasTheLeafSetOfLxToReplaceNode0>=1))||(i11.u88.Node7HasTheLeafSetOfRxToReplaceNode4>=1))||(i0.i0.u69.Node7ManageTheBreakDownOfNode1>=1))||((i7.i2.u16.Node1HasAskedItsLeafSetToRxToReplaceNode5>=1)&&(i11.u88.LeafSetOfRxIsSentToNode1>=1)))||(i1.u37.Node3ManageTheBreakDownOfNode6>=1))||((i7.i2.u83.Node8HasAskedItsLeafSetToRxToReplaceNode5>=1)&&(i11.u86.LeafSetOfRxIsSentToNode8>=1)))||(((i9.u76.Node7ManageTheBreakDownOfNode8<1)&&((i1.u37.RequestOfNode3IsSentToRx<1)||(i11.u88.RxIsActiveAndNotInTheLeafSet<1)))&&((i0.i2.u5.NoNodeManageTheBreakDownOfNode3<1)||(i4.u63.Node6WantsToManageTheBreakDownOfNode3<1)))) * AX(((((((((i8.u53.Node5ManageTheBreakDownOfNode2>=1)||((i2.i0.u15.Node1HasAskedItsLeafSetToLxToReplaceNode4>=1)&&(u87.LeafSetOfLxIsSentToNode1>=1)))||(i0.i1.u41.Node4ManageTheBreakDownOfNode0>=1))||((i3.u48.Node4HasAskedItsLeafSetToRxToReplaceNode7>=1)&&(i11.u46.LeafSetOfRxIsSentToNode4>=1)))||((i5.u35.Node3WantsToManageTheBreakDownOfNode4>=1)&&(i5.u6.NoNodeManageTheBreakDownOfNode4>=1)))||((i0.i0.u2.RequestOfNode0IsSentToLx>=1)&&(u87.LxIsActiveAndNotInTheLeafSet>=1)))||((i0.i2.u72.Node7HasAskedItsLeafSetToLxToReplaceNode3>=1)&&(u87.LeafSetOfLxIsSentToNode7>=1)))||(u87.Node7HasTheLeafSetOfLxToReplaceNode3>=1)))) * EG((((((i3.u29.Node2ManageTheBreakDownOfNode7>=1)||((i1.u39.Node3WantsToManageTheBreakDownOfNode8>=1)&&(i6.i1.u11.NoNodeManageTheBreakDownOfNode8>=1)))||(i11.u88.Node1HasTheLeafSetOfRxToReplaceNode7>=1))||((i7.i1.u45.Node4WantsToManageTheBreakDownOfNode5>=1)&&(i7.i2.u27.NoNodeManageTheBreakDownOfNode5>=1)))||((i5.u55.Node5HasAskedItsLeafSetToRxToReplaceNode4>=1)&&(i11.u88.LeafSetOfRxIsSentToNode5>=1))))))) * AF(((((((((((i0.i2.u5.Node0HasAskedItsLeafSetToLxToReplaceNode3>=1)&&(u87.LeafSetOfLxIsSentToNode0>=1))||((i7.i1.u40.Node4IsActive>=1)&&(i7.i2.u59.Node5DontAnswerToAnyNode>=1)))||((i7.i2.u65.Node6HasAskedItsLeafSetToRxToReplaceNode5>=1)&&(i11.u88.LeafSetOfRxIsSentToNode6>=1)))||((i0.i1.u68.NoNodeManageTheBreakDownOfNode0>=1)&&(i0.i1.u41.Node4WantsToManageTheBreakDownOfNode0>=1)))||((i2.i1.u4.NoNodeManageTheBreakDownOfNode2>=1)&&(i2.i1.u43.Node4WantsToManageTheBreakDownOfNode2>=1)))||((i2.i1.u3.Node2DontAnswerToAnyNode>=1)&&(i8.u52.Node5IsActive>=1))) + A(((((i3.u66.Node6ManageTheBreakDownOfNode7>=1)||(u87.Node2HasTheLeafSetOfLxToReplaceNode0>=1))||((i6.i0.u7.Node0WantsToManageTheBreakDownOfNode5>=1)&&(i7.i2.u27.NoNodeManageTheBreakDownOfNode5>=1)))||(u87.LxHasReceivedTheRequestOfNode0>=1)) U ((((i8.u54.Node5ManageTheBreakDownOfNode3>=1)||((i5.u50.Node4DontAnswerToAnyNode>=1)&&(i10.u78.Node8IsActive>=1)))||(i11.u88.Node0HasTheLeafSetOfRxToReplaceNode5>=1))||(i11.u88.Node0HasTheLeafSetOfRxToReplaceNode6>=1)))) + EG((((((u87.Node0HasTheLeafSetOfLxToReplaceNode4>=1)||((i2.i1.u3.Node2DontAnswerToAnyNode>=1)&&(i7.i1.u40.Node4IsActive>=1)))||((i10.u77.Node8HasAskedItsLeafSetToLxToReplaceNode0>=1)&&(u87.LeafSetOfLxIsSentToNode8>=1)))||((i0.i0.u69.Node7HasAskedItsLeafSetToLxToReplaceNode1>=1)&&(u87.LeafSetOfLxIsSentToNode7>=1)))||(i5.u82.Node8ManageTheBreakDownOfNode4>=1)))) * ((((((i11.u88.RxHasReceivedTheRequestOfNode2<1)&&(i4.u62.Node6ManageTheBreakDownOfNode2<1))&&(i5.u82.Node8ManageTheBreakDownOfNode4<1))&&((i0.i0.u23.Node2HasAskedItsLeafSetToLxToReplaceNode1<1)||(u87.LeafSetOfLxIsSentToNode2<1)))&&(u87.Node6HasTheLeafSetOfLxToReplaceNode3<1)) + !(AF(((((i3.u85.Node8HasAskedItsLeafSetToRxToReplaceNode7>=1)&&(i11.u86.LeafSetOfRxIsSentToNode8>=1))||((i5.u55.RequestOfNode5IsSentToRx>=1)&&(i11.u88.RxIsActiveAndNotInTheLeafSet>=1)))||((i5.u6.Node0HasAskedItsLeafSetToLxToReplaceNode4>=1)&&(u87.LeafSetOfLxIsSentToNode0>=1))))))))))
=> equivalent forward existential formula: [((FwdU(Init,(((((i1.u36.Node3ManageTheBreakDownOfNode5>=1)||(u87.Node0HasTheLeafSetOfLxToReplaceNode2>=1))||(i11.u88.Node0HasTheLeafSetOfRxToReplaceNode6>=1))||((i0.i0.u1.Node1DontAnswerToAnyNode>=1)&&(i7.i1.u40.Node4IsActive>=1)))||((i2.i0.u14.Node1WantsToManageTheBreakDownOfNode3>=1)&&(i0.i2.u5.NoNodeManageTheBreakDownOfNode3>=1)))) * E(TRUE U (((((((((i5.u6.NoNodeManageTheBreakDownOfNode4<1)||(i5.u55.Node5WantsToManageTheBreakDownOfNode4<1))&&((i1.u31.Node3WantsToManageTheBreakDownOfNode6<1)||(i7.i0.u47.NoNodeManageTheBreakDownOfNode6<1)))&&((i2.i0.u13.Node1WantsToManageTheBreakDownOfNode2<1)||(i2.i1.u4.NoNodeManageTheBreakDownOfNode2<1)))&&(i4.u62.Node6ManageTheBreakDownOfNode2<1))&&((i1.u31.Node3IsActive<1)||(i6.i1.u10.Node8DontAnswerToAnyNode<1)))&&(i11.u88.Node6HasTheLeafSetOfRxToReplaceNode4<1))&&((i10.u79.Node8HasAskedItsLeafSetToLxToReplaceNode1<1)||(u87.LeafSetOfLxIsSentToNode8<1))) + ((((((((((((((i0.i0.u1.Node1DontAnswerToAnyNode>=1)&&(i7.i2.u21.Node2IsActive>=1))||((i7.i2.u21.Node2IsActive>=1)&&(i7.i0.u8.Node6DontAnswerToAnyNode>=1)))||(u87.Node3HasTheLeafSetOfLxToReplaceNode0>=1))||(u87.Node2HasTheLeafSetOfLxToReplaceNode4>=1))||(u87.Node1HasTheLeafSetOfLxToReplaceNode0>=1))||(i11.u88.Node7HasTheLeafSetOfRxToReplaceNode4>=1))||(i0.i0.u69.Node7ManageTheBreakDownOfNode1>=1))||((i7.i2.u16.Node1HasAskedItsLeafSetToRxToReplaceNode5>=1)&&(i11.u88.LeafSetOfRxIsSentToNode1>=1)))||(i1.u37.Node3ManageTheBreakDownOfNode6>=1))||((i7.i2.u83.Node8HasAskedItsLeafSetToRxToReplaceNode5>=1)&&(i11.u86.LeafSetOfRxIsSentToNode8>=1)))||(((i9.u76.Node7ManageTheBreakDownOfNode8<1)&&((i1.u37.RequestOfNode3IsSentToRx<1)||(i11.u88.RxIsActiveAndNotInTheLeafSet<1)))&&((i0.i2.u5.NoNodeManageTheBreakDownOfNode3<1)||(i4.u63.Node6WantsToManageTheBreakDownOfNode3<1)))) * !(EX(!(((((((((i8.u53.Node5ManageTheBreakDownOfNode2>=1)||((i2.i0.u15.Node1HasAskedItsLeafSetToLxToReplaceNode4>=1)&&(u87.LeafSetOfLxIsSentToNode1>=1)))||(i0.i1.u41.Node4ManageTheBreakDownOfNode0>=1))||((i3.u48.Node4HasAskedItsLeafSetToRxToReplaceNode7>=1)&&(i11.u46.LeafSetOfRxIsSentToNode4>=1)))||((i5.u35.Node3WantsToManageTheBreakDownOfNode4>=1)&&(i5.u6.NoNodeManageTheBreakDownOfNode4>=1)))||((i0.i0.u2.RequestOfNode0IsSentToLx>=1)&&(u87.LxIsActiveAndNotInTheLeafSet>=1)))||((i0.i2.u72.Node7HasAskedItsLeafSetToLxToReplaceNode3>=1)&&(u87.LeafSetOfLxIsSentToNode7>=1)))||(u87.Node7HasTheLeafSetOfLxToReplaceNode3>=1)))))) * EG((((((i3.u29.Node2ManageTheBreakDownOfNode7>=1)||((i1.u39.Node3WantsToManageTheBreakDownOfNode8>=1)&&(i6.i1.u11.NoNodeManageTheBreakDownOfNode8>=1)))||(i11.u88.Node1HasTheLeafSetOfRxToReplaceNode7>=1))||((i7.i1.u45.Node4WantsToManageTheBreakDownOfNode5>=1)&&(i7.i2.u27.NoNodeManageTheBreakDownOfNode5>=1)))||((i5.u55.Node5HasAskedItsLeafSetToRxToReplaceNode4>=1)&&(i11.u88.LeafSetOfRxIsSentToNode5>=1)))))))) * !(EG(!(((((((((((i0.i2.u5.Node0HasAskedItsLeafSetToLxToReplaceNode3>=1)&&(u87.LeafSetOfLxIsSentToNode0>=1))||((i7.i1.u40.Node4IsActive>=1)&&(i7.i2.u59.Node5DontAnswerToAnyNode>=1)))||((i7.i2.u65.Node6HasAskedItsLeafSetToRxToReplaceNode5>=1)&&(i11.u88.LeafSetOfRxIsSentToNode6>=1)))||((i0.i1.u68.NoNodeManageTheBreakDownOfNode0>=1)&&(i0.i1.u41.Node4WantsToManageTheBreakDownOfNode0>=1)))||((i2.i1.u4.NoNodeManageTheBreakDownOfNode2>=1)&&(i2.i1.u43.Node4WantsToManageTheBreakDownOfNode2>=1)))||((i2.i1.u3.Node2DontAnswerToAnyNode>=1)&&(i8.u52.Node5IsActive>=1))) + !((E(!(((((i8.u54.Node5ManageTheBreakDownOfNode3>=1)||((i5.u50.Node4DontAnswerToAnyNode>=1)&&(i10.u78.Node8IsActive>=1)))||(i11.u88.Node0HasTheLeafSetOfRxToReplaceNode5>=1))||(i11.u88.Node0HasTheLeafSetOfRxToReplaceNode6>=1))) U (!(((((i3.u66.Node6ManageTheBreakDownOfNode7>=1)||(u87.Node2HasTheLeafSetOfLxToReplaceNode0>=1))||((i6.i0.u7.Node0WantsToManageTheBreakDownOfNode5>=1)&&(i7.i2.u27.NoNodeManageTheBreakDownOfNode5>=1)))||(u87.LxHasReceivedTheRequestOfNode0>=1))) * !(((((i8.u54.Node5ManageTheBreakDownOfNode3>=1)||((i5.u50.Node4DontAnswerToAnyNode>=1)&&(i10.u78.Node8IsActive>=1)))||(i11.u88.Node0HasTheLeafSetOfRxToReplaceNode5>=1))||(i11.u88.Node0HasTheLeafSetOfRxToReplaceNode6>=1))))) + EG(!(((((i8.u54.Node5ManageTheBreakDownOfNode3>=1)||((i5.u50.Node4DontAnswerToAnyNode>=1)&&(i10.u78.Node8IsActive>=1)))||(i11.u88.Node0HasTheLeafSetOfRxToReplaceNode5>=1))||(i11.u88.Node0HasTheLeafSetOfRxToReplaceNode6>=1))))))) + EG((((((u87.Node0HasTheLeafSetOfLxToReplaceNode4>=1)||((i2.i1.u3.Node2DontAnswerToAnyNode>=1)&&(i7.i1.u40.Node4IsActive>=1)))||((i10.u77.Node8HasAskedItsLeafSetToLxToReplaceNode0>=1)&&(u87.LeafSetOfLxIsSentToNode8>=1)))||((i0.i0.u69.Node7HasAskedItsLeafSetToLxToReplaceNode1>=1)&&(u87.LeafSetOfLxIsSentToNode7>=1)))||(i5.u82.Node8ManageTheBreakDownOfNode4>=1)))) * ((((((i11.u88.RxHasReceivedTheRequestOfNode2<1)&&(i4.u62.Node6ManageTheBreakDownOfNode2<1))&&(i5.u82.Node8ManageTheBreakDownOfNode4<1))&&((i0.i0.u23.Node2HasAskedItsLeafSetToLxToReplaceNode1<1)||(u87.LeafSetOfLxIsSentToNode2<1)))&&(u87.Node6HasTheLeafSetOfLxToReplaceNode3<1)) + !(!(EG(!(((((i3.u85.Node8HasAskedItsLeafSetToRxToReplaceNode7>=1)&&(i11.u86.LeafSetOfRxIsSentToNode8>=1))||((i5.u55.RequestOfNode5IsSentToRx>=1)&&(i11.u88.RxIsActiveAndNotInTheLeafSet>=1)))||((i5.u6.Node0HasAskedItsLeafSetToLxToReplaceNode4>=1)&&(u87.LeafSetOfLxIsSentToNode0>=1)))))))))))))] != FALSE
(forward)formula 4,0,168.51,2300424,1,0,1.37086e+06,699380,5721,6.14187e+06,1318,2.59804e+07,6057232
FORMULA LeafsetExtension-PT-S08C2-CTLFireability-04 FALSE TECHNIQUES DECISION_DIAGRAMS TOPOLOGICAL USE_NUPN
Formula is FALSE !
***************************************
original formula: AF((A(AX((((((EF(((((((i3.u48.NoNodeManageTheBreakDownOfNode7>=1)&&(i3.u85.Node8WantsToManageTheBreakDownOfNode7>=1))||(i11.u88.Node6HasTheLeafSetOfRxToReplaceNode4>=1))||((i0.i0.u2.RequestOfNode0IsSentToLx>=1)&&(u87.LxIsActiveAndNotInTheLeafSet>=1)))||(u87.Node2HasTheLeafSetOfLxToReplaceNode1>=1))||(i0.i2.u25.Node2ManageTheBreakDownOfNode3>=1))) + (i6.i1.u11.Node0ManageTheBreakDownOfNode8>=1)) + (i11.u88.Node3HasTheLeafSetOfRxToReplaceNode7>=1)) + ((i0.i0.u1.Node1DontAnswerToAnyNode>=1)&&(i4.u61.Node6IsActive>=1))) + (i11.u88.Node5HasTheLeafSetOfRxToReplaceNode8>=1)) + ((i0.i2.u24.Node3DontAnswerToAnyNode>=1)&&(i8.u52.Node5IsActive>=1)))) U (((((((((((((((((i9.u76.Node7WantsToManageTheBreakDownOfNode8<1)||(i6.i1.u11.NoNodeManageTheBreakDownOfNode8<1))&&((i2.i0.u13.Node1HasAskedItsLeafSetToLxToReplaceNode2<1)||(u87.LeafSetOfLxIsSentToNode1<1)))&&((i7.i2.u21.Node2IsActive<1)||(i6.i1.u10.Node8DontAnswerToAnyNode<1)))&&((i2.i1.u4.NoNodeManageTheBreakDownOfNode2<1)||(i4.u62.Node6WantsToManageTheBreakDownOfNode2<1)))&&((i4.u61.Node6HasAskedItsLeafSetToLxToReplaceNode1<1)||(u87.LeafSetOfLxIsSentToNode6<1)))&&(u87.Node1HasTheLeafSetOfLxToReplaceNode0<1))&&((i2.i0.u12.Node1IsActive<1)||(i5.u50.Node4DontAnswerToAnyNode<1)))&&((i6.i1.u10.Node0WantsToManageTheBreakDownOfNode8<1)||(i6.i1.u11.NoNodeManageTheBreakDownOfNode8<1)))&&((i4.u63.Node6HasAskedItsLeafSetToLxToReplaceNode3<1)||(u87.LeafSetOfLxIsSentToNode6<1)))&&((i6.i1.u58.Node5HasAskedItsLeafSetToRxToReplaceNode8<1)||(i11.u88.LeafSetOfRxIsSentToNode5<1)))&&((i5.u82.Node8HasAskedItsLeafSetToRxToReplaceNode4<1)||(i11.u86.LeafSetOfRxIsSentToNode8<1)))&&(i11.u88.Node1HasTheLeafSetOfRxToReplaceNode8<1))&&((i2.i1.u3.Node2DontAnswerToAnyNode<1)||(i10.u78.Node8IsActive<1)))&&(i11.u88.Node2HasTheLeafSetOfRxToReplaceNode8<1)) * EG((((i1.u39.Node3WantsToManageTheBreakDownOfNode8>=1)&&(i6.i1.u11.NoNodeManageTheBreakDownOfNode8>=1))||(u87.Node0HasTheLeafSetOfLxToReplaceNode2>=1)))) + (((((((((((i6.i0.u0.Node0IsActive<1)||(i5.u50.Node4DontAnswerToAnyNode<1))&&(i9.u74.Node7ManageTheBreakDownOfNode5<1))&&((i0.i0.u1.Node1DontAnswerToAnyNode<1)||(i10.u78.Node8IsActive<1)))&&(i10.u79.Node8ManageTheBreakDownOfNode1<1))&&((i3.u66.Node6HasAskedItsLeafSetToRxToReplaceNode7<1)||(i11.u88.LeafSetOfRxIsSentToNode6<1)))&&((i7.i2.u21.Node2WantsToManageTheBreakDownOfNode5<1)||(i7.i2.u27.NoNodeManageTheBreakDownOfNode5<1)))&&((i4.u63.Node6HasAskedItsLeafSetToLxToReplaceNode3<1)||(u87.LeafSetOfLxIsSentToNode6<1)))&&(i6.i1.u67.Node6ManageTheBreakDownOfNode8<1)) + EG(((((i7.i1.u40.Node4IsActive>=1)&&(i7.i2.u59.Node5DontAnswerToAnyNode>=1))||((i2.i0.u14.Node1HasAskedItsLeafSetToLxToReplaceNode3>=1)&&(u87.LeafSetOfLxIsSentToNode1>=1)))||((i7.i2.u59.Node5DontAnswerToAnyNode>=1)&&(i4.u61.Node6IsActive>=1))))) * ((((((((((((i7.i2.u27.NoNodeManageTheBreakDownOfNode5>=1)&&(i7.i2.u65.Node6WantsToManageTheBreakDownOfNode5>=1))||((i6.i1.u30.Node2HasAskedItsLeafSetToRxToReplaceNode8>=1)&&(i11.u88.LeafSetOfRxIsSentToNode2>=1)))||(u87.Node0HasTheLeafSetOfLxToReplaceNode1>=1))||((i3.u48.Node4HasAskedItsLeafSetToRxToReplaceNode7>=1)&&(i11.u46.LeafSetOfRxIsSentToNode4>=1)))||(i0.i1.u32.Node3ManageTheBreakDownOfNode0>=1))||((i0.i2.u24.Node3DontAnswerToAnyNode>=1)&&(i8.u52.Node5IsActive>=1)))||(i7.i1.u45.Node4ManageTheBreakDownOfNode5>=1))||(i0.i0.u23.Node2ManageTheBreakDownOfNode1>=1))||(u87.LxHasReceivedTheRequestOfNode2>=1))||(u87.Node5HasTheLeafSetOfLxToReplaceNode0>=1))||((i7.i2.u21.Node2IsActive>=1)&&(i5.u50.Node4DontAnswerToAnyNode>=1)))))) + EG(((((u87.Node4HasTheLeafSetOfLxToReplaceNode3>=1)||((i0.i0.u1.BreakDownReservoir>=1)&&(i1.u31.Node3IsActive>=1)))||((i6.i0.u0.Node0IsActive>=1)&&(i6.i1.u10.Node8DontAnswerToAnyNode>=1)))||((u87.LxIsActiveAndNotInTheLeafSet>=1)&&(u87.ANodeFromTheLeafSetOfLxIsACtiveInTheLeafSet>=1))))))
=> equivalent forward existential formula: [FwdG(Init,!((!((E(!((((((((((((((((((i9.u76.Node7WantsToManageTheBreakDownOfNode8<1)||(i6.i1.u11.NoNodeManageTheBreakDownOfNode8<1))&&((i2.i0.u13.Node1HasAskedItsLeafSetToLxToReplaceNode2<1)||(u87.LeafSetOfLxIsSentToNode1<1)))&&((i7.i2.u21.Node2IsActive<1)||(i6.i1.u10.Node8DontAnswerToAnyNode<1)))&&((i2.i1.u4.NoNodeManageTheBreakDownOfNode2<1)||(i4.u62.Node6WantsToManageTheBreakDownOfNode2<1)))&&((i4.u61.Node6HasAskedItsLeafSetToLxToReplaceNode1<1)||(u87.LeafSetOfLxIsSentToNode6<1)))&&(u87.Node1HasTheLeafSetOfLxToReplaceNode0<1))&&((i2.i0.u12.Node1IsActive<1)||(i5.u50.Node4DontAnswerToAnyNode<1)))&&((i6.i1.u10.Node0WantsToManageTheBreakDownOfNode8<1)||(i6.i1.u11.NoNodeManageTheBreakDownOfNode8<1)))&&((i4.u63.Node6HasAskedItsLeafSetToLxToReplaceNode3<1)||(u87.LeafSetOfLxIsSentToNode6<1)))&&((i6.i1.u58.Node5HasAskedItsLeafSetToRxToReplaceNode8<1)||(i11.u88.LeafSetOfRxIsSentToNode5<1)))&&((i5.u82.Node8HasAskedItsLeafSetToRxToReplaceNode4<1)||(i11.u86.LeafSetOfRxIsSentToNode8<1)))&&(i11.u88.Node1HasTheLeafSetOfRxToReplaceNode8<1))&&((i2.i1.u3.Node2DontAnswerToAnyNode<1)||(i10.u78.Node8IsActive<1)))&&(i11.u88.Node2HasTheLeafSetOfRxToReplaceNode8<1)) * EG((((i1.u39.Node3WantsToManageTheBreakDownOfNode8>=1)&&(i6.i1.u11.NoNodeManageTheBreakDownOfNode8>=1))||(u87.Node0HasTheLeafSetOfLxToReplaceNode2>=1)))) + (((((((((((i6.i0.u0.Node0IsActive<1)||(i5.u50.Node4DontAnswerToAnyNode<1))&&(i9.u74.Node7ManageTheBreakDownOfNode5<1))&&((i0.i0.u1.Node1DontAnswerToAnyNode<1)||(i10.u78.Node8IsActive<1)))&&(i10.u79.Node8ManageTheBreakDownOfNode1<1))&&((i3.u66.Node6HasAskedItsLeafSetToRxToReplaceNode7<1)||(i11.u88.LeafSetOfRxIsSentToNode6<1)))&&((i7.i2.u21.Node2WantsToManageTheBreakDownOfNode5<1)||(i7.i2.u27.NoNodeManageTheBreakDownOfNode5<1)))&&((i4.u63.Node6HasAskedItsLeafSetToLxToReplaceNode3<1)||(u87.LeafSetOfLxIsSentToNode6<1)))&&(i6.i1.u67.Node6ManageTheBreakDownOfNode8<1)) + EG(((((i7.i1.u40.Node4IsActive>=1)&&(i7.i2.u59.Node5DontAnswerToAnyNode>=1))||((i2.i0.u14.Node1HasAskedItsLeafSetToLxToReplaceNode3>=1)&&(u87.LeafSetOfLxIsSentToNode1>=1)))||((i7.i2.u59.Node5DontAnswerToAnyNode>=1)&&(i4.u61.Node6IsActive>=1))))) * ((((((((((((i7.i2.u27.NoNodeManageTheBreakDownOfNode5>=1)&&(i7.i2.u65.Node6WantsToManageTheBreakDownOfNode5>=1))||((i6.i1.u30.Node2HasAskedItsLeafSetToRxToReplaceNode8>=1)&&(i11.u88.LeafSetOfRxIsSentToNode2>=1)))||(u87.Node0HasTheLeafSetOfLxToReplaceNode1>=1))||((i3.u48.Node4HasAskedItsLeafSetToRxToReplaceNode7>=1)&&(i11.u46.LeafSetOfRxIsSentToNode4>=1)))||(i0.i1.u32.Node3ManageTheBreakDownOfNode0>=1))||((i0.i2.u24.Node3DontAnswerToAnyNode>=1)&&(i8.u52.Node5IsActive>=1)))||(i7.i1.u45.Node4ManageTheBreakDownOfNode5>=1))||(i0.i0.u23.Node2ManageTheBreakDownOfNode1>=1))||(u87.LxHasReceivedTheRequestOfNode2>=1))||(u87.Node5HasTheLeafSetOfLxToReplaceNode0>=1))||((i7.i2.u21.Node2IsActive>=1)&&(i5.u50.Node4DontAnswerToAnyNode>=1)))))) U (!(!(EX(!((((((E(TRUE U ((((((i3.u48.NoNodeManageTheBreakDownOfNode7>=1)&&(i3.u85.Node8WantsToManageTheBreakDownOfNode7>=1))||(i11.u88.Node6HasTheLeafSetOfRxToReplaceNode4>=1))||((i0.i0.u2.RequestOfNode0IsSentToLx>=1)&&(u87.LxIsActiveAndNotInTheLeafSet>=1)))||(u87.Node2HasTheLeafSetOfLxToReplaceNode1>=1))||(i0.i2.u25.Node2ManageTheBreakDownOfNode3>=1))) + (i6.i1.u11.Node0ManageTheBreakDownOfNode8>=1)) + (i11.u88.Node3HasTheLeafSetOfRxToReplaceNode7>=1)) + ((i0.i0.u1.Node1DontAnswerToAnyNode>=1)&&(i4.u61.Node6IsActive>=1))) + (i11.u88.Node5HasTheLeafSetOfRxToReplaceNode8>=1)) + ((i0.i2.u24.Node3DontAnswerToAnyNode>=1)&&(i8.u52.Node5IsActive>=1))))))) * !((((((((((((((((((i9.u76.Node7WantsToManageTheBreakDownOfNode8<1)||(i6.i1.u11.NoNodeManageTheBreakDownOfNode8<1))&&((i2.i0.u13.Node1HasAskedItsLeafSetToLxToReplaceNode2<1)||(u87.LeafSetOfLxIsSentToNode1<1)))&&((i7.i2.u21.Node2IsActive<1)||(i6.i1.u10.Node8DontAnswerToAnyNode<1)))&&((i2.i1.u4.NoNodeManageTheBreakDownOfNode2<1)||(i4.u62.Node6WantsToManageTheBreakDownOfNode2<1)))&&((i4.u61.Node6HasAskedItsLeafSetToLxToReplaceNode1<1)||(u87.LeafSetOfLxIsSentToNode6<1)))&&(u87.Node1HasTheLeafSetOfLxToReplaceNode0<1))&&((i2.i0.u12.Node1IsActive<1)||(i5.u50.Node4DontAnswerToAnyNode<1)))&&((i6.i1.u10.Node0WantsToManageTheBreakDownOfNode8<1)||(i6.i1.u11.NoNodeManageTheBreakDownOfNode8<1)))&&((i4.u63.Node6HasAskedItsLeafSetToLxToReplaceNode3<1)||(u87.LeafSetOfLxIsSentToNode6<1)))&&((i6.i1.u58.Node5HasAskedItsLeafSetToRxToReplaceNode8<1)||(i11.u88.LeafSetOfRxIsSentToNode5<1)))&&((i5.u82.Node8HasAskedItsLeafSetToRxToReplaceNode4<1)||(i11.u86.LeafSetOfRxIsSentToNode8<1)))&&(i11.u88.Node1HasTheLeafSetOfRxToReplaceNode8<1))&&((i2.i1.u3.Node2DontAnswerToAnyNode<1)||(i10.u78.Node8IsActive<1)))&&(i11.u88.Node2HasTheLeafSetOfRxToReplaceNode8<1)) * EG((((i1.u39.Node3WantsToManageTheBreakDownOfNode8>=1)&&(i6.i1.u11.NoNodeManageTheBreakDownOfNode8>=1))||(u87.Node0HasTheLeafSetOfLxToReplaceNode2>=1)))) + (((((((((((i6.i0.u0.Node0IsActive<1)||(i5.u50.Node4DontAnswerToAnyNode<1))&&(i9.u74.Node7ManageTheBreakDownOfNode5<1))&&((i0.i0.u1.Node1DontAnswerToAnyNode<1)||(i10.u78.Node8IsActive<1)))&&(i10.u79.Node8ManageTheBreakDownOfNode1<1))&&((i3.u66.Node6HasAskedItsLeafSetToRxToReplaceNode7<1)||(i11.u88.LeafSetOfRxIsSentToNode6<1)))&&((i7.i2.u21.Node2WantsToManageTheBreakDownOfNode5<1)||(i7.i2.u27.NoNodeManageTheBreakDownOfNode5<1)))&&((i4.u63.Node6HasAskedItsLeafSetToLxToReplaceNode3<1)||(u87.LeafSetOfLxIsSentToNode6<1)))&&(i6.i1.u67.Node6ManageTheBreakDownOfNode8<1)) + EG(((((i7.i1.u40.Node4IsActive>=1)&&(i7.i2.u59.Node5DontAnswerToAnyNode>=1))||((i2.i0.u14.Node1HasAskedItsLeafSetToLxToReplaceNode3>=1)&&(u87.LeafSetOfLxIsSentToNode1>=1)))||((i7.i2.u59.Node5DontAnswerToAnyNode>=1)&&(i4.u61.Node6IsActive>=1))))) * ((((((((((((i7.i2.u27.NoNodeManageTheBreakDownOfNode5>=1)&&(i7.i2.u65.Node6WantsToManageTheBreakDownOfNode5>=1))||((i6.i1.u30.Node2HasAskedItsLeafSetToRxToReplaceNode8>=1)&&(i11.u88.LeafSetOfRxIsSentToNode2>=1)))||(u87.Node0HasTheLeafSetOfLxToReplaceNode1>=1))||((i3.u48.Node4HasAskedItsLeafSetToRxToReplaceNode7>=1)&&(i11.u46.LeafSetOfRxIsSentToNode4>=1)))||(i0.i1.u32.Node3ManageTheBreakDownOfNode0>=1))||((i0.i2.u24.Node3DontAnswerToAnyNode>=1)&&(i8.u52.Node5IsActive>=1)))||(i7.i1.u45.Node4ManageTheBreakDownOfNode5>=1))||(i0.i0.u23.Node2ManageTheBreakDownOfNode1>=1))||(u87.LxHasReceivedTheRequestOfNode2>=1))||(u87.Node5HasTheLeafSetOfLxToReplaceNode0>=1))||((i7.i2.u21.Node2IsActive>=1)&&(i5.u50.Node4DontAnswerToAnyNode>=1)))))))) + EG(!((((((((((((((((((i9.u76.Node7WantsToManageTheBreakDownOfNode8<1)||(i6.i1.u11.NoNodeManageTheBreakDownOfNode8<1))&&((i2.i0.u13.Node1HasAskedItsLeafSetToLxToReplaceNode2<1)||(u87.LeafSetOfLxIsSentToNode1<1)))&&((i7.i2.u21.Node2IsActive<1)||(i6.i1.u10.Node8DontAnswerToAnyNode<1)))&&((i2.i1.u4.NoNodeManageTheBreakDownOfNode2<1)||(i4.u62.Node6WantsToManageTheBreakDownOfNode2<1)))&&((i4.u61.Node6HasAskedItsLeafSetToLxToReplaceNode1<1)||(u87.LeafSetOfLxIsSentToNode6<1)))&&(u87.Node1HasTheLeafSetOfLxToReplaceNode0<1))&&((i2.i0.u12.Node1IsActive<1)||(i5.u50.Node4DontAnswerToAnyNode<1)))&&((i6.i1.u10.Node0WantsToManageTheBreakDownOfNode8<1)||(i6.i1.u11.NoNodeManageTheBreakDownOfNode8<1)))&&((i4.u63.Node6HasAskedItsLeafSetToLxToReplaceNode3<1)||(u87.LeafSetOfLxIsSentToNode6<1)))&&((i6.i1.u58.Node5HasAskedItsLeafSetToRxToReplaceNode8<1)||(i11.u88.LeafSetOfRxIsSentToNode5<1)))&&((i5.u82.Node8HasAskedItsLeafSetToRxToReplaceNode4<1)||(i11.u86.LeafSetOfRxIsSentToNode8<1)))&&(i11.u88.Node1HasTheLeafSetOfRxToReplaceNode8<1))&&((i2.i1.u3.Node2DontAnswerToAnyNode<1)||(i10.u78.Node8IsActive<1)))&&(i11.u88.Node2HasTheLeafSetOfRxToReplaceNode8<1)) * EG((((i1.u39.Node3WantsToManageTheBreakDownOfNode8>=1)&&(i6.i1.u11.NoNodeManageTheBreakDownOfNode8>=1))||(u87.Node0HasTheLeafSetOfLxToReplaceNode2>=1)))) + (((((((((((i6.i0.u0.Node0IsActive<1)||(i5.u50.Node4DontAnswerToAnyNode<1))&&(i9.u74.Node7ManageTheBreakDownOfNode5<1))&&((i0.i0.u1.Node1DontAnswerToAnyNode<1)||(i10.u78.Node8IsActive<1)))&&(i10.u79.Node8ManageTheBreakDownOfNode1<1))&&((i3.u66.Node6HasAskedItsLeafSetToRxToReplaceNode7<1)||(i11.u88.LeafSetOfRxIsSentToNode6<1)))&&((i7.i2.u21.Node2WantsToManageTheBreakDownOfNode5<1)||(i7.i2.u27.NoNodeManageTheBreakDownOfNode5<1)))&&((i4.u63.Node6HasAskedItsLeafSetToLxToReplaceNode3<1)||(u87.LeafSetOfLxIsSentToNode6<1)))&&(i6.i1.u67.Node6ManageTheBreakDownOfNode8<1)) + EG(((((i7.i1.u40.Node4IsActive>=1)&&(i7.i2.u59.Node5DontAnswerToAnyNode>=1))||((i2.i0.u14.Node1HasAskedItsLeafSetToLxToReplaceNode3>=1)&&(u87.LeafSetOfLxIsSentToNode1>=1)))||((i7.i2.u59.Node5DontAnswerToAnyNode>=1)&&(i4.u61.Node6IsActive>=1))))) * ((((((((((((i7.i2.u27.NoNodeManageTheBreakDownOfNode5>=1)&&(i7.i2.u65.Node6WantsToManageTheBreakDownOfNode5>=1))||((i6.i1.u30.Node2HasAskedItsLeafSetToRxToReplaceNode8>=1)&&(i11.u88.LeafSetOfRxIsSentToNode2>=1)))||(u87.Node0HasTheLeafSetOfLxToReplaceNode1>=1))||((i3.u48.Node4HasAskedItsLeafSetToRxToReplaceNode7>=1)&&(i11.u46.LeafSetOfRxIsSentToNode4>=1)))||(i0.i1.u32.Node3ManageTheBreakDownOfNode0>=1))||((i0.i2.u24.Node3DontAnswerToAnyNode>=1)&&(i8.u52.Node5IsActive>=1)))||(i7.i1.u45.Node4ManageTheBreakDownOfNode5>=1))||(i0.i0.u23.Node2ManageTheBreakDownOfNode1>=1))||(u87.LxHasReceivedTheRequestOfNode2>=1))||(u87.Node5HasTheLeafSetOfLxToReplaceNode0>=1))||((i7.i2.u21.Node2IsActive>=1)&&(i5.u50.Node4DontAnswerToAnyNode>=1))))))))) + EG(((((u87.Node4HasTheLeafSetOfLxToReplaceNode3>=1)||((i0.i0.u1.BreakDownReservoir>=1)&&(i1.u31.Node3IsActive>=1)))||((i6.i0.u0.Node0IsActive>=1)&&(i6.i1.u10.Node8DontAnswerToAnyNode>=1)))||((u87.LxIsActiveAndNotInTheLeafSet>=1)&&(u87.ANodeFromTheLeafSetOfLxIsACtiveInTheLeafSet>=1)))))))] = FALSE
(forward)formula 5,0,199.693,2523500,1,0,1.90148e+06,755205,5967,6.65052e+06,1337,2.59804e+07,8447716
FORMULA LeafsetExtension-PT-S08C2-CTLFireability-05 FALSE TECHNIQUES DECISION_DIAGRAMS TOPOLOGICAL USE_NUPN
Formula is FALSE !
***************************************
original formula: (AG(!(AG((((i11.u88.RxHasReceivedTheRequestOfNode0>=1)||((i4.u61.Node6IsActive>=1)&&(i6.i1.u10.Node8DontAnswerToAnyNode>=1)))||(u87.Node6HasTheLeafSetOfLxToReplaceNode3>=1))))) * EF(AX((((((i11.u88.Node8HasTheLeafSetOfRxToReplaceNode6>=1)||((i7.i2.u83.RequestOfNode8IsSentToRx>=1)&&(i11.u88.RxIsActiveAndNotInTheLeafSet>=1)))||((i8.u51.Node5HasAskedItsLeafSetToLxToReplaceNode0>=1)&&(u87.LeafSetOfLxIsSentToNode5>=1)))||((i7.i0.u28.Node2HasAskedItsLeafSetToRxToReplaceNode6>=1)&&(i11.u88.LeafSetOfRxIsSentToNode2>=1)))||((i6.i1.u58.Node5WantsToManageTheBreakDownOfNode8>=1)&&(i6.i1.u11.NoNodeManageTheBreakDownOfNode8>=1))))))
=> equivalent forward existential formula: ([(FwdU(Init,TRUE) * !(E(TRUE U !((((i11.u88.RxHasReceivedTheRequestOfNode0>=1)||((i4.u61.Node6IsActive>=1)&&(i6.i1.u10.Node8DontAnswerToAnyNode>=1)))||(u87.Node6HasTheLeafSetOfLxToReplaceNode3>=1))))))] = FALSE * [(Init * !(E(TRUE U !(EX(!((((((i11.u88.Node8HasTheLeafSetOfRxToReplaceNode6>=1)||((i7.i2.u83.RequestOfNode8IsSentToRx>=1)&&(i11.u88.RxIsActiveAndNotInTheLeafSet>=1)))||((i8.u51.Node5HasAskedItsLeafSetToLxToReplaceNode0>=1)&&(u87.LeafSetOfLxIsSentToNode5>=1)))||((i7.i0.u28.Node2HasAskedItsLeafSetToRxToReplaceNode6>=1)&&(i11.u88.LeafSetOfRxIsSentToNode2>=1)))||((i6.i1.u58.Node5WantsToManageTheBreakDownOfNode8>=1)&&(i6.i1.u11.NoNodeManageTheBreakDownOfNode8>=1)))))))))] = FALSE)
(forward)formula 6,1,226.155,2570356,1,0,1.94845e+06,763399,3734,6.75861e+06,1221,2.59804e+07,748293
FORMULA LeafsetExtension-PT-S08C2-CTLFireability-06 TRUE TECHNIQUES DECISION_DIAGRAMS TOPOLOGICAL USE_NUPN
Formula is TRUE !
***************************************
original formula: AF((!(A(((((((((((((i6.i1.u58.Node5HasAskedItsLeafSetToRxToReplaceNode8>=1)&&(i11.u88.LeafSetOfRxIsSentToNode5>=1))||(u87.Node3HasTheLeafSetOfLxToReplaceNode2>=1))||((i6.i0.u0.Node0IsActive>=1)&&(i5.u50.Node4DontAnswerToAnyNode>=1)))||((i3.u19.Node1WantsToManageTheBreakDownOfNode7>=1)&&(i3.u48.NoNodeManageTheBreakDownOfNode7>=1)))||((i1.u31.Node3IsActive>=1)&&(i6.i1.u10.Node8DontAnswerToAnyNode>=1)))||((i0.i2.u24.Node2WantsToManageTheBreakDownOfNode3>=1)&&(i0.i2.u5.NoNodeManageTheBreakDownOfNode3>=1)))||(i11.u88.Node7HasTheLeafSetOfRxToReplaceNode8>=1))||((i6.i0.u0.Node0IsActive>=1)&&(i3.u18.Node7DontAnswerToAnyNode>=1)))||(u87.Node6HasTheLeafSetOfLxToReplaceNode0>=1))||((i0.i0.u1.BreakDownReservoir>=1)&&(i4.u61.Node6IsActive>=1))) * EF(((((((((((i1.u38.Node3ManageTheBreakDownOfNode7>=1)||((i0.i1.u41.RequestOfNode4IsSentToLx>=1)&&(u87.LxIsActiveAndNotInTheLeafSet>=1)))||((i1.u31.Node3IsActive>=1)&&(i3.u18.Node7DontAnswerToAnyNode>=1)))||(i11.u88.Node4HasTheLeafSetOfRxToReplaceNode7>=1))||(u87.Node7HasTheLeafSetOfLxToReplaceNode2>=1))||((i2.i1.u4.NoNodeManageTheBreakDownOfNode2>=1)&&(i2.i1.u71.Node7WantsToManageTheBreakDownOfNode2>=1)))||(u87.Node8HasTheLeafSetOfLxToReplaceNode1>=1))||((i3.u19.Node1HasAskedItsLeafSetToRxToReplaceNode7>=1)&&(i11.u88.LeafSetOfRxIsSentToNode1>=1)))||(i11.u88.Node3HasTheLeafSetOfRxToReplaceNode5>=1))||((i5.u50.Node4DontAnswerToAnyNode>=1)&&(i8.u52.Node5IsActive>=1))))) U (AF(((((((((((i6.i0.u0.Node0WantsToManageTheBreakDownOfNode3>=1)&&(i0.i2.u5.NoNodeManageTheBreakDownOfNode3>=1))||((i7.i2.u21.Node2IsActive>=1)&&(i7.i0.u8.Node6DontAnswerToAnyNode>=1)))||((i1.u36.Node3WantsToManageTheBreakDownOfNode5>=1)&&(i7.i2.u27.NoNodeManageTheBreakDownOfNode5>=1)))||((i1.u38.Node3HasAskedItsLeafSetToRxToReplaceNode7>=1)&&(i11.u88.LeafSetOfRxIsSentToNode3>=1)))||(i11.u88.Node3HasTheLeafSetOfRxToReplaceNode6>=1))||((i0.i0.u1.Node1DontAnswerToAnyNode>=1)&&(i9.u70.Node7IsActive>=1)))||((i0.i1.u68.NoNodeManageTheBreakDownOfNode0>=1)&&(i0.i1.u41.Node4WantsToManageTheBreakDownOfNode0>=1)))||((i7.i1.u40.Node4IsActive>=1)&&(i6.i1.u10.Node8DontAnswerToAnyNode>=1)))||((i0.i2.u5.NoNodeManageTheBreakDownOfNode3>=1)&&(i0.i2.u44.Node4WantsToManageTheBreakDownOfNode3>=1)))) + A(((((((((((i7.i0.u28.RequestOfNode2IsSentToRx>=1)&&(i11.u88.RxIsActiveAndNotInTheLeafSet>=1))||((i7.i0.u28.Node2WantsToManageTheBreakDownOfNode6>=1)&&(i7.i0.u47.NoNodeManageTheBreakDownOfNode6>=1)))||((i0.i1.u41.RequestOfNode4IsSentToLx>=1)&&(u87.LxIsActiveAndNotInTheLeafSet>=1)))||((i0.i0.u33.Node3HasAskedItsLeafSetToLxToReplaceNode1>=1)&&(u87.LeafSetOfLxIsSentToNode3>=1)))||((i7.i2.u27.Node2HasAskedItsLeafSetToRxToReplaceNode5>=1)&&(i11.u88.LeafSetOfRxIsSentToNode2>=1)))||((i7.i2.u59.Node5DontAnswerToAnyNode>=1)&&(i10.u78.Node8IsActive>=1)))||(i2.i1.u4.Node0ManageTheBreakDownOfNode2>=1))||((i0.i1.u22.Node0DontAnswerToAnyNode>=1)&&(i8.u52.Node5IsActive>=1)))||((i7.i0.u47.Node4HasAskedItsLeafSetToRxToReplaceNode6>=1)&&(i11.u46.LeafSetOfRxIsSentToNode4>=1))) U ((i6.i0.u0.Node0IsActive>=1)&&(i5.u50.Node4DontAnswerToAnyNode>=1)))))) * (A((((i0.i1.u32.Node3ManageTheBreakDownOfNode0>=1)||((i4.u63.Node6HasAskedItsLeafSetToLxToReplaceNode3>=1)&&(u87.LeafSetOfLxIsSentToNode6>=1)))&&((((((((((i3.u48.NoNodeManageTheBreakDownOfNode7>=1)&&(i3.u85.Node8WantsToManageTheBreakDownOfNode7>=1))||((i5.u55.RequestOfNode5IsSentToRx>=1)&&(i11.u88.RxIsActiveAndNotInTheLeafSet>=1)))||((i0.i0.u1.Node1DontAnswerToAnyNode>=1)&&(i4.u61.Node6IsActive>=1)))||(i0.i0.u42.Node4ManageTheBreakDownOfNode1>=1))||((i10.u77.Node8HasAskedItsLeafSetToLxToReplaceNode0>=1)&&(u87.LeafSetOfLxIsSentToNode8>=1)))||((i6.i1.u10.Node0WantsToManageTheBreakDownOfNode8>=1)&&(i6.i1.u11.NoNodeManageTheBreakDownOfNode8>=1)))||((i0.i0.u23.NoNodeManageTheBreakDownOfNode1>=1)&&(i8.u52.Node5WantsToManageTheBreakDownOfNode1>=1)))||(i0.i2.u5.Node0ManageTheBreakDownOfNode3>=1))||(u87.Node8HasTheLeafSetOfLxToReplaceNode0>=1))) U ((((((((((i0.i1.u68.Node7ManageTheBreakDownOfNode0>=1)||(i4.u63.Node6ManageTheBreakDownOfNode3>=1))||((i7.i1.u45.RequestOfNode4IsSentToRx>=1)&&(i11.u88.RxIsActiveAndNotInTheLeafSet>=1)))||((i1.u37.Node3HasAskedItsLeafSetToRxToReplaceNode6>=1)&&(i11.u88.LeafSetOfRxIsSentToNode3>=1)))||((i2.i1.u71.Node7HasAskedItsLeafSetToLxToReplaceNode2>=1)&&(u87.LeafSetOfLxIsSentToNode7>=1)))||(u87.Node0HasTheLeafSetOfLxToReplaceNode1>=1))||(i11.u88.Node8HasTheLeafSetOfRxToReplaceNode4>=1))||((i0.i0.u69.Node7HasAskedItsLeafSetToLxToReplaceNode1>=1)&&(u87.LeafSetOfLxIsSentToNode7>=1)))||((i0.i2.u24.Node3DontAnswerToAnyNode>=1)&&(i4.u61.Node6IsActive>=1)))||((i1.u39.Node3HasAskedItsLeafSetToRxToReplaceNode8>=1)&&(i11.u88.LeafSetOfRxIsSentToNode3>=1)))) + ((((((((i4.u63.Node6ManageTheBreakDownOfNode3<1)&&(u87.Node4HasTheLeafSetOfLxToReplaceNode3<1))&&(i11.u88.Node2HasTheLeafSetOfRxToReplaceNode7<1))&&(i4.u61.Node6ManageTheBreakDownOfNode1<1))&&(i7.i2.u27.Node2ManageTheBreakDownOfNode5<1))&&((i3.u85.Node8HasAskedItsLeafSetToRxToReplaceNode7<1)||(i11.u86.LeafSetOfRxIsSentToNode8<1)))&&((i0.i0.u1.Node1DontAnswerToAnyNode<1)||(i10.u78.Node8IsActive<1)))&&((i0.i2.u24.Node2WantsToManageTheBreakDownOfNode3<1)||(i0.i2.u5.NoNodeManageTheBreakDownOfNode3<1))))))
=> equivalent forward existential formula: [FwdG(Init,!((!(!((E(!((!(EG(!(((((((((((i6.i0.u0.Node0WantsToManageTheBreakDownOfNode3>=1)&&(i0.i2.u5.NoNodeManageTheBreakDownOfNode3>=1))||((i7.i2.u21.Node2IsActive>=1)&&(i7.i0.u8.Node6DontAnswerToAnyNode>=1)))||((i1.u36.Node3WantsToManageTheBreakDownOfNode5>=1)&&(i7.i2.u27.NoNodeManageTheBreakDownOfNode5>=1)))||((i1.u38.Node3HasAskedItsLeafSetToRxToReplaceNode7>=1)&&(i11.u88.LeafSetOfRxIsSentToNode3>=1)))||(i11.u88.Node3HasTheLeafSetOfRxToReplaceNode6>=1))||((i0.i0.u1.Node1DontAnswerToAnyNode>=1)&&(i9.u70.Node7IsActive>=1)))||((i0.i1.u68.NoNodeManageTheBreakDownOfNode0>=1)&&(i0.i1.u41.Node4WantsToManageTheBreakDownOfNode0>=1)))||((i7.i1.u40.Node4IsActive>=1)&&(i6.i1.u10.Node8DontAnswerToAnyNode>=1)))||((i0.i2.u5.NoNodeManageTheBreakDownOfNode3>=1)&&(i0.i2.u44.Node4WantsToManageTheBreakDownOfNode3>=1)))))) + !((E(!(((i6.i0.u0.Node0IsActive>=1)&&(i5.u50.Node4DontAnswerToAnyNode>=1))) U (!(((((((((((i7.i0.u28.RequestOfNode2IsSentToRx>=1)&&(i11.u88.RxIsActiveAndNotInTheLeafSet>=1))||((i7.i0.u28.Node2WantsToManageTheBreakDownOfNode6>=1)&&(i7.i0.u47.NoNodeManageTheBreakDownOfNode6>=1)))||((i0.i1.u41.RequestOfNode4IsSentToLx>=1)&&(u87.LxIsActiveAndNotInTheLeafSet>=1)))||((i0.i0.u33.Node3HasAskedItsLeafSetToLxToReplaceNode1>=1)&&(u87.LeafSetOfLxIsSentToNode3>=1)))||((i7.i2.u27.Node2HasAskedItsLeafSetToRxToReplaceNode5>=1)&&(i11.u88.LeafSetOfRxIsSentToNode2>=1)))||((i7.i2.u59.Node5DontAnswerToAnyNode>=1)&&(i10.u78.Node8IsActive>=1)))||(i2.i1.u4.Node0ManageTheBreakDownOfNode2>=1))||((i0.i1.u22.Node0DontAnswerToAnyNode>=1)&&(i8.u52.Node5IsActive>=1)))||((i7.i0.u47.Node4HasAskedItsLeafSetToRxToReplaceNode6>=1)&&(i11.u46.LeafSetOfRxIsSentToNode4>=1)))) * !(((i6.i0.u0.Node0IsActive>=1)&&(i5.u50.Node4DontAnswerToAnyNode>=1))))) + EG(!(((i6.i0.u0.Node0IsActive>=1)&&(i5.u50.Node4DontAnswerToAnyNode>=1)))))))) U (!(((((((((((((i6.i1.u58.Node5HasAskedItsLeafSetToRxToReplaceNode8>=1)&&(i11.u88.LeafSetOfRxIsSentToNode5>=1))||(u87.Node3HasTheLeafSetOfLxToReplaceNode2>=1))||((i6.i0.u0.Node0IsActive>=1)&&(i5.u50.Node4DontAnswerToAnyNode>=1)))||((i3.u19.Node1WantsToManageTheBreakDownOfNode7>=1)&&(i3.u48.NoNodeManageTheBreakDownOfNode7>=1)))||((i1.u31.Node3IsActive>=1)&&(i6.i1.u10.Node8DontAnswerToAnyNode>=1)))||((i0.i2.u24.Node2WantsToManageTheBreakDownOfNode3>=1)&&(i0.i2.u5.NoNodeManageTheBreakDownOfNode3>=1)))||(i11.u88.Node7HasTheLeafSetOfRxToReplaceNode8>=1))||((i6.i0.u0.Node0IsActive>=1)&&(i3.u18.Node7DontAnswerToAnyNode>=1)))||(u87.Node6HasTheLeafSetOfLxToReplaceNode0>=1))||((i0.i0.u1.BreakDownReservoir>=1)&&(i4.u61.Node6IsActive>=1))) * E(TRUE U ((((((((((i1.u38.Node3ManageTheBreakDownOfNode7>=1)||((i0.i1.u41.RequestOfNode4IsSentToLx>=1)&&(u87.LxIsActiveAndNotInTheLeafSet>=1)))||((i1.u31.Node3IsActive>=1)&&(i3.u18.Node7DontAnswerToAnyNode>=1)))||(i11.u88.Node4HasTheLeafSetOfRxToReplaceNode7>=1))||(u87.Node7HasTheLeafSetOfLxToReplaceNode2>=1))||((i2.i1.u4.NoNodeManageTheBreakDownOfNode2>=1)&&(i2.i1.u71.Node7WantsToManageTheBreakDownOfNode2>=1)))||(u87.Node8HasTheLeafSetOfLxToReplaceNode1>=1))||((i3.u19.Node1HasAskedItsLeafSetToRxToReplaceNode7>=1)&&(i11.u88.LeafSetOfRxIsSentToNode1>=1)))||(i11.u88.Node3HasTheLeafSetOfRxToReplaceNode5>=1))||((i5.u50.Node4DontAnswerToAnyNode>=1)&&(i8.u52.Node5IsActive>=1)))))) * !((!(EG(!(((((((((((i6.i0.u0.Node0WantsToManageTheBreakDownOfNode3>=1)&&(i0.i2.u5.NoNodeManageTheBreakDownOfNode3>=1))||((i7.i2.u21.Node2IsActive>=1)&&(i7.i0.u8.Node6DontAnswerToAnyNode>=1)))||((i1.u36.Node3WantsToManageTheBreakDownOfNode5>=1)&&(i7.i2.u27.NoNodeManageTheBreakDownOfNode5>=1)))||((i1.u38.Node3HasAskedItsLeafSetToRxToReplaceNode7>=1)&&(i11.u88.LeafSetOfRxIsSentToNode3>=1)))||(i11.u88.Node3HasTheLeafSetOfRxToReplaceNode6>=1))||((i0.i0.u1.Node1DontAnswerToAnyNode>=1)&&(i9.u70.Node7IsActive>=1)))||((i0.i1.u68.NoNodeManageTheBreakDownOfNode0>=1)&&(i0.i1.u41.Node4WantsToManageTheBreakDownOfNode0>=1)))||((i7.i1.u40.Node4IsActive>=1)&&(i6.i1.u10.Node8DontAnswerToAnyNode>=1)))||((i0.i2.u5.NoNodeManageTheBreakDownOfNode3>=1)&&(i0.i2.u44.Node4WantsToManageTheBreakDownOfNode3>=1)))))) + !((E(!(((i6.i0.u0.Node0IsActive>=1)&&(i5.u50.Node4DontAnswerToAnyNode>=1))) U (!(((((((((((i7.i0.u28.RequestOfNode2IsSentToRx>=1)&&(i11.u88.RxIsActiveAndNotInTheLeafSet>=1))||((i7.i0.u28.Node2WantsToManageTheBreakDownOfNode6>=1)&&(i7.i0.u47.NoNodeManageTheBreakDownOfNode6>=1)))||((i0.i1.u41.RequestOfNode4IsSentToLx>=1)&&(u87.LxIsActiveAndNotInTheLeafSet>=1)))||((i0.i0.u33.Node3HasAskedItsLeafSetToLxToReplaceNode1>=1)&&(u87.LeafSetOfLxIsSentToNode3>=1)))||((i7.i2.u27.Node2HasAskedItsLeafSetToRxToReplaceNode5>=1)&&(i11.u88.LeafSetOfRxIsSentToNode2>=1)))||((i7.i2.u59.Node5DontAnswerToAnyNode>=1)&&(i10.u78.Node8IsActive>=1)))||(i2.i1.u4.Node0ManageTheBreakDownOfNode2>=1))||((i0.i1.u22.Node0DontAnswerToAnyNode>=1)&&(i8.u52.Node5IsActive>=1)))||((i7.i0.u47.Node4HasAskedItsLeafSetToRxToReplaceNode6>=1)&&(i11.u46.LeafSetOfRxIsSentToNode4>=1)))) * !(((i6.i0.u0.Node0IsActive>=1)&&(i5.u50.Node4DontAnswerToAnyNode>=1))))) + EG(!(((i6.i0.u0.Node0IsActive>=1)&&(i5.u50.Node4DontAnswerToAnyNode>=1)))))))))) + EG(!((!(EG(!(((((((((((i6.i0.u0.Node0WantsToManageTheBreakDownOfNode3>=1)&&(i0.i2.u5.NoNodeManageTheBreakDownOfNode3>=1))||((i7.i2.u21.Node2IsActive>=1)&&(i7.i0.u8.Node6DontAnswerToAnyNode>=1)))||((i1.u36.Node3WantsToManageTheBreakDownOfNode5>=1)&&(i7.i2.u27.NoNodeManageTheBreakDownOfNode5>=1)))||((i1.u38.Node3HasAskedItsLeafSetToRxToReplaceNode7>=1)&&(i11.u88.LeafSetOfRxIsSentToNode3>=1)))||(i11.u88.Node3HasTheLeafSetOfRxToReplaceNode6>=1))||((i0.i0.u1.Node1DontAnswerToAnyNode>=1)&&(i9.u70.Node7IsActive>=1)))||((i0.i1.u68.NoNodeManageTheBreakDownOfNode0>=1)&&(i0.i1.u41.Node4WantsToManageTheBreakDownOfNode0>=1)))||((i7.i1.u40.Node4IsActive>=1)&&(i6.i1.u10.Node8DontAnswerToAnyNode>=1)))||((i0.i2.u5.NoNodeManageTheBreakDownOfNode3>=1)&&(i0.i2.u44.Node4WantsToManageTheBreakDownOfNode3>=1)))))) + !((E(!(((i6.i0.u0.Node0IsActive>=1)&&(i5.u50.Node4DontAnswerToAnyNode>=1))) U (!(((((((((((i7.i0.u28.RequestOfNode2IsSentToRx>=1)&&(i11.u88.RxIsActiveAndNotInTheLeafSet>=1))||((i7.i0.u28.Node2WantsToManageTheBreakDownOfNode6>=1)&&(i7.i0.u47.NoNodeManageTheBreakDownOfNode6>=1)))||((i0.i1.u41.RequestOfNode4IsSentToLx>=1)&&(u87.LxIsActiveAndNotInTheLeafSet>=1)))||((i0.i0.u33.Node3HasAskedItsLeafSetToLxToReplaceNode1>=1)&&(u87.LeafSetOfLxIsSentToNode3>=1)))||((i7.i2.u27.Node2HasAskedItsLeafSetToRxToReplaceNode5>=1)&&(i11.u88.LeafSetOfRxIsSentToNode2>=1)))||((i7.i2.u59.Node5DontAnswerToAnyNode>=1)&&(i10.u78.Node8IsActive>=1)))||(i2.i1.u4.Node0ManageTheBreakDownOfNode2>=1))||((i0.i1.u22.Node0DontAnswerToAnyNode>=1)&&(i8.u52.Node5IsActive>=1)))||((i7.i0.u47.Node4HasAskedItsLeafSetToRxToReplaceNode6>=1)&&(i11.u46.LeafSetOfRxIsSentToNode4>=1)))) * !(((i6.i0.u0.Node0IsActive>=1)&&(i5.u50.Node4DontAnswerToAnyNode>=1))))) + EG(!(((i6.i0.u0.Node0IsActive>=1)&&(i5.u50.Node4DontAnswerToAnyNode>=1)))))))))))) * (!((E(!(((((((((((i0.i1.u68.Node7ManageTheBreakDownOfNode0>=1)||(i4.u63.Node6ManageTheBreakDownOfNode3>=1))||((i7.i1.u45.RequestOfNode4IsSentToRx>=1)&&(i11.u88.RxIsActiveAndNotInTheLeafSet>=1)))||((i1.u37.Node3HasAskedItsLeafSetToRxToReplaceNode6>=1)&&(i11.u88.LeafSetOfRxIsSentToNode3>=1)))||((i2.i1.u71.Node7HasAskedItsLeafSetToLxToReplaceNode2>=1)&&(u87.LeafSetOfLxIsSentToNode7>=1)))||(u87.Node0HasTheLeafSetOfLxToReplaceNode1>=1))||(i11.u88.Node8HasTheLeafSetOfRxToReplaceNode4>=1))||((i0.i0.u69.Node7HasAskedItsLeafSetToLxToReplaceNode1>=1)&&(u87.LeafSetOfLxIsSentToNode7>=1)))||((i0.i2.u24.Node3DontAnswerToAnyNode>=1)&&(i4.u61.Node6IsActive>=1)))||((i1.u39.Node3HasAskedItsLeafSetToRxToReplaceNode8>=1)&&(i11.u88.LeafSetOfRxIsSentToNode3>=1)))) U (!((((i0.i1.u32.Node3ManageTheBreakDownOfNode0>=1)||((i4.u63.Node6HasAskedItsLeafSetToLxToReplaceNode3>=1)&&(u87.LeafSetOfLxIsSentToNode6>=1)))&&((((((((((i3.u48.NoNodeManageTheBreakDownOfNode7>=1)&&(i3.u85.Node8WantsToManageTheBreakDownOfNode7>=1))||((i5.u55.RequestOfNode5IsSentToRx>=1)&&(i11.u88.RxIsActiveAndNotInTheLeafSet>=1)))||((i0.i0.u1.Node1DontAnswerToAnyNode>=1)&&(i4.u61.Node6IsActive>=1)))||(i0.i0.u42.Node4ManageTheBreakDownOfNode1>=1))||((i10.u77.Node8HasAskedItsLeafSetToLxToReplaceNode0>=1)&&(u87.LeafSetOfLxIsSentToNode8>=1)))||((i6.i1.u10.Node0WantsToManageTheBreakDownOfNode8>=1)&&(i6.i1.u11.NoNodeManageTheBreakDownOfNode8>=1)))||((i0.i0.u23.NoNodeManageTheBreakDownOfNode1>=1)&&(i8.u52.Node5WantsToManageTheBreakDownOfNode1>=1)))||(i0.i2.u5.Node0ManageTheBreakDownOfNode3>=1))||(u87.Node8HasTheLeafSetOfLxToReplaceNode0>=1)))) * !(((((((((((i0.i1.u68.Node7ManageTheBreakDownOfNode0>=1)||(i4.u63.Node6ManageTheBreakDownOfNode3>=1))||((i7.i1.u45.RequestOfNode4IsSentToRx>=1)&&(i11.u88.RxIsActiveAndNotInTheLeafSet>=1)))||((i1.u37.Node3HasAskedItsLeafSetToRxToReplaceNode6>=1)&&(i11.u88.LeafSetOfRxIsSentToNode3>=1)))||((i2.i1.u71.Node7HasAskedItsLeafSetToLxToReplaceNode2>=1)&&(u87.LeafSetOfLxIsSentToNode7>=1)))||(u87.Node0HasTheLeafSetOfLxToReplaceNode1>=1))||(i11.u88.Node8HasTheLeafSetOfRxToReplaceNode4>=1))||((i0.i0.u69.Node7HasAskedItsLeafSetToLxToReplaceNode1>=1)&&(u87.LeafSetOfLxIsSentToNode7>=1)))||((i0.i2.u24.Node3DontAnswerToAnyNode>=1)&&(i4.u61.Node6IsActive>=1)))||((i1.u39.Node3HasAskedItsLeafSetToRxToReplaceNode8>=1)&&(i11.u88.LeafSetOfRxIsSentToNode3>=1)))))) + EG(!(((((((((((i0.i1.u68.Node7ManageTheBreakDownOfNode0>=1)||(i4.u63.Node6ManageTheBreakDownOfNode3>=1))||((i7.i1.u45.RequestOfNode4IsSentToRx>=1)&&(i11.u88.RxIsActiveAndNotInTheLeafSet>=1)))||((i1.u37.Node3HasAskedItsLeafSetToRxToReplaceNode6>=1)&&(i11.u88.LeafSetOfRxIsSentToNode3>=1)))||((i2.i1.u71.Node7HasAskedItsLeafSetToLxToReplaceNode2>=1)&&(u87.LeafSetOfLxIsSentToNode7>=1)))||(u87.Node0HasTheLeafSetOfLxToReplaceNode1>=1))||(i11.u88.Node8HasTheLeafSetOfRxToReplaceNode4>=1))||((i0.i0.u69.Node7HasAskedItsLeafSetToLxToReplaceNode1>=1)&&(u87.LeafSetOfLxIsSentToNode7>=1)))||((i0.i2.u24.Node3DontAnswerToAnyNode>=1)&&(i4.u61.Node6IsActive>=1)))||((i1.u39.Node3HasAskedItsLeafSetToRxToReplaceNode8>=1)&&(i11.u88.LeafSetOfRxIsSentToNode3>=1))))))) + ((((((((i4.u63.Node6ManageTheBreakDownOfNode3<1)&&(u87.Node4HasTheLeafSetOfLxToReplaceNode3<1))&&(i11.u88.Node2HasTheLeafSetOfRxToReplaceNode7<1))&&(i4.u61.Node6ManageTheBreakDownOfNode1<1))&&(i7.i2.u27.Node2ManageTheBreakDownOfNode5<1))&&((i3.u85.Node8HasAskedItsLeafSetToRxToReplaceNode7<1)||(i11.u86.LeafSetOfRxIsSentToNode8<1)))&&((i0.i0.u1.Node1DontAnswerToAnyNode<1)||(i10.u78.Node8IsActive<1)))&&((i0.i2.u24.Node2WantsToManageTheBreakDownOfNode3<1)||(i0.i2.u5.NoNodeManageTheBreakDownOfNode3<1)))))))] = FALSE
dead was empty
(forward)formula 7,1,253.831,2570356,1,0,1.94845e+06,763399,4384,6.75861e+06,1242,2.59804e+07,3682104
FORMULA LeafsetExtension-PT-S08C2-CTLFireability-07 TRUE TECHNIQUES DECISION_DIAGRAMS TOPOLOGICAL USE_NUPN
Formula is TRUE !
***************************************
original formula: A((((((((((i5.u64.Node6ManageTheBreakDownOfNode4>=1)||((i0.i0.u1.Node1DontAnswerToAnyNode>=1)&&(i7.i2.u21.Node2IsActive>=1)))||((i1.u36.Node3WantsToManageTheBreakDownOfNode5>=1)&&(i7.i2.u27.NoNodeManageTheBreakDownOfNode5>=1)))||((i4.u61.Node6HasAskedItsLeafSetToLxToReplaceNode1>=1)&&(u87.LeafSetOfLxIsSentToNode6>=1)))||((i7.i2.u65.Node6HasAskedItsLeafSetToRxToReplaceNode5>=1)&&(i11.u88.LeafSetOfRxIsSentToNode6>=1)))||((i2.i0.u12.Node1IsActive>=1)&&(i5.u50.Node4DontAnswerToAnyNode>=1)))||((i0.i1.u22.Node0DontAnswerToAnyNode>=1)&&(i1.u31.Node3IsActive>=1)))||((i0.i1.u22.Node0DontAnswerToAnyNode>=1)&&(i7.i2.u21.Node2IsActive>=1))) * (((((((i0.i1.u32.Node3ManageTheBreakDownOfNode0>=1)||(i0.i0.u42.Node4ManageTheBreakDownOfNode1>=1))||(i7.i2.u16.Node1ManageTheBreakDownOfNode5>=1))||((i0.i0.u1.BreakDownReservoir>=1)&&(i8.u52.Node5IsActive>=1)))||((i0.i1.u22.Node0DontAnswerToAnyNode>=1)&&(i2.i0.u12.Node1IsActive>=1)))||((i0.i1.u68.Node7HasAskedItsLeafSetToLxToReplaceNode0>=1)&&(u87.LeafSetOfLxIsSentToNode7>=1))) + (!(AX(((((i7.i0.u56.Node5ManageTheBreakDownOfNode6<1)&&((i2.i1.u4.NoNodeManageTheBreakDownOfNode2<1)||(i2.i1.u71.Node7WantsToManageTheBreakDownOfNode2<1)))&&((i6.i1.u67.Node6WantsToManageTheBreakDownOfNode8<1)||(i6.i1.u11.NoNodeManageTheBreakDownOfNode8<1)))&&((i0.i2.u5.NoNodeManageTheBreakDownOfNode3<1)||(i0.i2.u72.Node7WantsToManageTheBreakDownOfNode3<1))))) * (!(A(((((((i8.u53.Node5ManageTheBreakDownOfNode2>=1)||(u87.Node4HasTheLeafSetOfLxToReplaceNode3>=1))||((i3.u48.NoNodeManageTheBreakDownOfNode7>=1)&&(i3.u85.Node8WantsToManageTheBreakDownOfNode7>=1)))||((i0.i0.u1.BreakDownReservoir>=1)&&(i2.i0.u12.Node1IsActive>=1)))||((i3.u18.Node7DontAnswerToAnyNode>=1)&&(i10.u78.Node8IsActive>=1)))||((i0.i2.u24.Node3DontAnswerToAnyNode>=1)&&(i9.u70.Node7IsActive>=1))) U ((i8.u53.Node5ManageTheBreakDownOfNode2>=1)||((i0.i1.u68.NoNodeManageTheBreakDownOfNode0>=1)&&(i0.i1.u32.Node3WantsToManageTheBreakDownOfNode0>=1))))) + ((((((i5.u35.Node3ManageTheBreakDownOfNode4<1)&&(i10.u80.Node8ManageTheBreakDownOfNode2<1))&&((i1.u31.Node3IsActive<1)||(i3.u18.Node7DontAnswerToAnyNode<1)))&&((i6.i0.u0.Node0IsActive<1)||(i6.i1.u10.Node8DontAnswerToAnyNode<1)))&&((i7.i0.u8.Node0WantsToManageTheBreakDownOfNode6<1)||(i7.i0.u47.NoNodeManageTheBreakDownOfNode6<1)))&&((i0.i1.u22.Node0DontAnswerToAnyNode<1)||(i2.i0.u12.Node1IsActive<1))))))) U !(AG(AF(((((((i0.i2.u5.Node0HasAskedItsLeafSetToLxToReplaceNode3>=1)&&(u87.LeafSetOfLxIsSentToNode0>=1))||((i2.i1.u43.Node4HasAskedItsLeafSetToLxToReplaceNode2>=1)&&(u87.LeafSetOfLxIsSentToNode4>=1)))||((i2.i1.u3.Node2DontAnswerToAnyNode>=1)&&(i10.u78.Node8IsActive>=1)))||((i0.i0.u1.BreakDownReservoir>=1)&&(i4.u61.Node6IsActive>=1)))||((i4.u63.Node6HasAskedItsLeafSetToLxToReplaceNode3>=1)&&(u87.LeafSetOfLxIsSentToNode6>=1)))))))
=> equivalent forward existential formula: [((Init * !(EG(!(!(!(E(TRUE U !(!(EG(!(((((((i0.i2.u5.Node0HasAskedItsLeafSetToLxToReplaceNode3>=1)&&(u87.LeafSetOfLxIsSentToNode0>=1))||((i2.i1.u43.Node4HasAskedItsLeafSetToLxToReplaceNode2>=1)&&(u87.LeafSetOfLxIsSentToNode4>=1)))||((i2.i1.u3.Node2DontAnswerToAnyNode>=1)&&(i10.u78.Node8IsActive>=1)))||((i0.i0.u1.BreakDownReservoir>=1)&&(i4.u61.Node6IsActive>=1)))||((i4.u63.Node6HasAskedItsLeafSetToLxToReplaceNode3>=1)&&(u87.LeafSetOfLxIsSentToNode6>=1)))))))))))))) * !(E(!(!(!(E(TRUE U !(!(EG(!(((((((i0.i2.u5.Node0HasAskedItsLeafSetToLxToReplaceNode3>=1)&&(u87.LeafSetOfLxIsSentToNode0>=1))||((i2.i1.u43.Node4HasAskedItsLeafSetToLxToReplaceNode2>=1)&&(u87.LeafSetOfLxIsSentToNode4>=1)))||((i2.i1.u3.Node2DontAnswerToAnyNode>=1)&&(i10.u78.Node8IsActive>=1)))||((i0.i0.u1.BreakDownReservoir>=1)&&(i4.u61.Node6IsActive>=1)))||((i4.u63.Node6HasAskedItsLeafSetToLxToReplaceNode3>=1)&&(u87.LeafSetOfLxIsSentToNode6>=1))))))))))) U (!((((((((((i5.u64.Node6ManageTheBreakDownOfNode4>=1)||((i0.i0.u1.Node1DontAnswerToAnyNode>=1)&&(i7.i2.u21.Node2IsActive>=1)))||((i1.u36.Node3WantsToManageTheBreakDownOfNode5>=1)&&(i7.i2.u27.NoNodeManageTheBreakDownOfNode5>=1)))||((i4.u61.Node6HasAskedItsLeafSetToLxToReplaceNode1>=1)&&(u87.LeafSetOfLxIsSentToNode6>=1)))||((i7.i2.u65.Node6HasAskedItsLeafSetToRxToReplaceNode5>=1)&&(i11.u88.LeafSetOfRxIsSentToNode6>=1)))||((i2.i0.u12.Node1IsActive>=1)&&(i5.u50.Node4DontAnswerToAnyNode>=1)))||((i0.i1.u22.Node0DontAnswerToAnyNode>=1)&&(i1.u31.Node3IsActive>=1)))||((i0.i1.u22.Node0DontAnswerToAnyNode>=1)&&(i7.i2.u21.Node2IsActive>=1))) * (((((((i0.i1.u32.Node3ManageTheBreakDownOfNode0>=1)||(i0.i0.u42.Node4ManageTheBreakDownOfNode1>=1))||(i7.i2.u16.Node1ManageTheBreakDownOfNode5>=1))||((i0.i0.u1.BreakDownReservoir>=1)&&(i8.u52.Node5IsActive>=1)))||((i0.i1.u22.Node0DontAnswerToAnyNode>=1)&&(i2.i0.u12.Node1IsActive>=1)))||((i0.i1.u68.Node7HasAskedItsLeafSetToLxToReplaceNode0>=1)&&(u87.LeafSetOfLxIsSentToNode7>=1))) + (!(!(EX(!(((((i7.i0.u56.Node5ManageTheBreakDownOfNode6<1)&&((i2.i1.u4.NoNodeManageTheBreakDownOfNode2<1)||(i2.i1.u71.Node7WantsToManageTheBreakDownOfNode2<1)))&&((i6.i1.u67.Node6WantsToManageTheBreakDownOfNode8<1)||(i6.i1.u11.NoNodeManageTheBreakDownOfNode8<1)))&&((i0.i2.u5.NoNodeManageTheBreakDownOfNode3<1)||(i0.i2.u72.Node7WantsToManageTheBreakDownOfNode3<1))))))) * (!(!((E(!(((i8.u53.Node5ManageTheBreakDownOfNode2>=1)||((i0.i1.u68.NoNodeManageTheBreakDownOfNode0>=1)&&(i0.i1.u32.Node3WantsToManageTheBreakDownOfNode0>=1)))) U (!(((((((i8.u53.Node5ManageTheBreakDownOfNode2>=1)||(u87.Node4HasTheLeafSetOfLxToReplaceNode3>=1))||((i3.u48.NoNodeManageTheBreakDownOfNode7>=1)&&(i3.u85.Node8WantsToManageTheBreakDownOfNode7>=1)))||((i0.i0.u1.BreakDownReservoir>=1)&&(i2.i0.u12.Node1IsActive>=1)))||((i3.u18.Node7DontAnswerToAnyNode>=1)&&(i10.u78.Node8IsActive>=1)))||((i0.i2.u24.Node3DontAnswerToAnyNode>=1)&&(i9.u70.Node7IsActive>=1)))) * !(((i8.u53.Node5ManageTheBreakDownOfNode2>=1)||((i0.i1.u68.NoNodeManageTheBreakDownOfNode0>=1)&&(i0.i1.u32.Node3WantsToManageTheBreakDownOfNode0>=1)))))) + EG(!(((i8.u53.Node5ManageTheBreakDownOfNode2>=1)||((i0.i1.u68.NoNodeManageTheBreakDownOfNode0>=1)&&(i0.i1.u32.Node3WantsToManageTheBreakDownOfNode0>=1)))))))) + ((((((i5.u35.Node3ManageTheBreakDownOfNode4<1)&&(i10.u80.Node8ManageTheBreakDownOfNode2<1))&&((i1.u31.Node3IsActive<1)||(i3.u18.Node7DontAnswerToAnyNode<1)))&&((i6.i0.u0.Node0IsActive<1)||(i6.i1.u10.Node8DontAnswerToAnyNode<1)))&&((i7.i0.u8.Node0WantsToManageTheBreakDownOfNode6<1)||(i7.i0.u47.NoNodeManageTheBreakDownOfNode6<1)))&&((i0.i1.u22.Node0DontAnswerToAnyNode<1)||(i2.i0.u12.Node1IsActive<1)))))))) * !(!(!(E(TRUE U !(!(EG(!(((((((i0.i2.u5.Node0HasAskedItsLeafSetToLxToReplaceNode3>=1)&&(u87.LeafSetOfLxIsSentToNode0>=1))||((i2.i1.u43.Node4HasAskedItsLeafSetToLxToReplaceNode2>=1)&&(u87.LeafSetOfLxIsSentToNode4>=1)))||((i2.i1.u3.Node2DontAnswerToAnyNode>=1)&&(i10.u78.Node8IsActive>=1)))||((i0.i0.u1.BreakDownReservoir>=1)&&(i4.u61.Node6IsActive>=1)))||((i4.u63.Node6HasAskedItsLeafSetToLxToReplaceNode3>=1)&&(u87.LeafSetOfLxIsSentToNode6>=1)))))))))))))))] != FALSE
(forward)formula 8,1,257.229,2570356,1,0,1.94845e+06,763399,4529,6.75861e+06,1243,2.59804e+07,4093638
FORMULA LeafsetExtension-PT-S08C2-CTLFireability-08 TRUE TECHNIQUES DECISION_DIAGRAMS TOPOLOGICAL USE_NUPN
Formula is TRUE !
***************************************
original formula: EX(((A((((((((u87.Node8HasTheLeafSetOfLxToReplaceNode2<1)&&((i0.i0.u23.NoNodeManageTheBreakDownOfNode1<1)||(i0.i0.u69.Node7WantsToManageTheBreakDownOfNode1<1)))&&(u87.Node5HasTheLeafSetOfLxToReplaceNode0<1))&&((i7.i2.u83.Node8HasAskedItsLeafSetToRxToReplaceNode5<1)||(i11.u86.LeafSetOfRxIsSentToNode8<1)))&&(i1.u37.Node3ManageTheBreakDownOfNode6<1))&&(i2.i0.u14.Node1ManageTheBreakDownOfNode3<1)) + !(EF(((((i8.u52.Node5HasAskedItsLeafSetToLxToReplaceNode1>=1)&&(u87.LeafSetOfLxIsSentToNode5>=1))||((i0.i0.u1.BreakDownReservoir>=1)&&(i8.u52.Node5IsActive>=1)))||(i2.i1.u34.Node3ManageTheBreakDownOfNode2>=1))))) U E(AG((((((((((i7.i2.u21.Node2IsActive>=1)&&(i7.i2.u59.Node5DontAnswerToAnyNode>=1))||((i1.u38.Node3HasAskedItsLeafSetToRxToReplaceNode7>=1)&&(i11.u88.LeafSetOfRxIsSentToNode3>=1)))||(i6.i1.u20.Node1ManageTheBreakDownOfNode8>=1))||((i0.i0.u23.NoNodeManageTheBreakDownOfNode1>=1)&&(i0.i0.u1.Node2WantsToManageTheBreakDownOfNode1>=1)))||(i7.i2.u16.Node1ManageTheBreakDownOfNode5>=1))||((i5.u26.Node2WantsToManageTheBreakDownOfNode4>=1)&&(i5.u6.NoNodeManageTheBreakDownOfNode4>=1)))||(i8.u52.Node5ManageTheBreakDownOfNode1>=1))||((i8.u52.Node5IsActive>=1)&&(i7.i0.u8.Node6DontAnswerToAnyNode>=1)))) U ((((EG((((((((((((i3.u57.Node5HasAskedItsLeafSetToRxToReplaceNode7>=1)&&(i11.u88.LeafSetOfRxIsSentToNode5>=1))||(i11.u88.Node8HasTheLeafSetOfRxToReplaceNode6>=1))||(i0.i2.u72.Node7ManageTheBreakDownOfNode3>=1))||(i5.u6.Node0ManageTheBreakDownOfNode4>=1))||((i2.i0.u15.Node1HasAskedItsLeafSetToLxToReplaceNode4>=1)&&(u87.LeafSetOfLxIsSentToNode1>=1)))||(i0.i1.u22.Node2ManageTheBreakDownOfNode0>=1))||(i7.i0.u17.Node1ManageTheBreakDownOfNode6>=1))||((i3.u29.Node2HasAskedItsLeafSetToRxToReplaceNode7>=1)&&(i11.u88.LeafSetOfRxIsSentToNode2>=1)))||(i7.i0.u8.Node0ManageTheBreakDownOfNode6>=1))||(u87.Node7HasTheLeafSetOfLxToReplaceNode3>=1))) * ((i0.i0.u1.Node1DontAnswerToAnyNode<1)||(i8.u52.Node5IsActive<1))) * (i2.i1.u71.Node7ManageTheBreakDownOfNode2<1)) * (i4.u62.Node6ManageTheBreakDownOfNode2<1)) * ((i6.i1.u67.Node6WantsToManageTheBreakDownOfNode8<1)||(i6.i1.u11.NoNodeManageTheBreakDownOfNode8<1))))) + (i0.i1.u32.Node3ManageTheBreakDownOfNode0>=1)) + (i11.u88.Node0HasTheLeafSetOfRxToReplaceNode6>=1)))
=> equivalent forward existential formula: (([((EY(Init) * !(EG(!(E(!(E(TRUE U !((((((((((i7.i2.u21.Node2IsActive>=1)&&(i7.i2.u59.Node5DontAnswerToAnyNode>=1))||((i1.u38.Node3HasAskedItsLeafSetToRxToReplaceNode7>=1)&&(i11.u88.LeafSetOfRxIsSentToNode3>=1)))||(i6.i1.u20.Node1ManageTheBreakDownOfNode8>=1))||((i0.i0.u23.NoNodeManageTheBreakDownOfNode1>=1)&&(i0.i0.u1.Node2WantsToManageTheBreakDownOfNode1>=1)))||(i7.i2.u16.Node1ManageTheBreakDownOfNode5>=1))||((i5.u26.Node2WantsToManageTheBreakDownOfNode4>=1)&&(i5.u6.NoNodeManageTheBreakDownOfNode4>=1)))||(i8.u52.Node5ManageTheBreakDownOfNode1>=1))||((i8.u52.Node5IsActive>=1)&&(i7.i0.u8.Node6DontAnswerToAnyNode>=1)))))) U ((((EG((((((((((((i3.u57.Node5HasAskedItsLeafSetToRxToReplaceNode7>=1)&&(i11.u88.LeafSetOfRxIsSentToNode5>=1))||(i11.u88.Node8HasTheLeafSetOfRxToReplaceNode6>=1))||(i0.i2.u72.Node7ManageTheBreakDownOfNode3>=1))||(i5.u6.Node0ManageTheBreakDownOfNode4>=1))||((i2.i0.u15.Node1HasAskedItsLeafSetToLxToReplaceNode4>=1)&&(u87.LeafSetOfLxIsSentToNode1>=1)))||(i0.i1.u22.Node2ManageTheBreakDownOfNode0>=1))||(i7.i0.u17.Node1ManageTheBreakDownOfNode6>=1))||((i3.u29.Node2HasAskedItsLeafSetToRxToReplaceNode7>=1)&&(i11.u88.LeafSetOfRxIsSentToNode2>=1)))||(i7.i0.u8.Node0ManageTheBreakDownOfNode6>=1))||(u87.Node7HasTheLeafSetOfLxToReplaceNode3>=1))) * ((i0.i0.u1.Node1DontAnswerToAnyNode<1)||(i8.u52.Node5IsActive<1))) * (i2.i1.u71.Node7ManageTheBreakDownOfNode2<1)) * (i4.u62.Node6ManageTheBreakDownOfNode2<1)) * ((i6.i1.u67.Node6WantsToManageTheBreakDownOfNode8<1)||(i6.i1.u11.NoNodeManageTheBreakDownOfNode8<1)))))))) * !(E(!(E(!(E(TRUE U !((((((((((i7.i2.u21.Node2IsActive>=1)&&(i7.i2.u59.Node5DontAnswerToAnyNode>=1))||((i1.u38.Node3HasAskedItsLeafSetToRxToReplaceNode7>=1)&&(i11.u88.LeafSetOfRxIsSentToNode3>=1)))||(i6.i1.u20.Node1ManageTheBreakDownOfNode8>=1))||((i0.i0.u23.NoNodeManageTheBreakDownOfNode1>=1)&&(i0.i0.u1.Node2WantsToManageTheBreakDownOfNode1>=1)))||(i7.i2.u16.Node1ManageTheBreakDownOfNode5>=1))||((i5.u26.Node2WantsToManageTheBreakDownOfNode4>=1)&&(i5.u6.NoNodeManageTheBreakDownOfNode4>=1)))||(i8.u52.Node5ManageTheBreakDownOfNode1>=1))||((i8.u52.Node5IsActive>=1)&&(i7.i0.u8.Node6DontAnswerToAnyNode>=1)))))) U ((((EG((((((((((((i3.u57.Node5HasAskedItsLeafSetToRxToReplaceNode7>=1)&&(i11.u88.LeafSetOfRxIsSentToNode5>=1))||(i11.u88.Node8HasTheLeafSetOfRxToReplaceNode6>=1))||(i0.i2.u72.Node7ManageTheBreakDownOfNode3>=1))||(i5.u6.Node0ManageTheBreakDownOfNode4>=1))||((i2.i0.u15.Node1HasAskedItsLeafSetToLxToReplaceNode4>=1)&&(u87.LeafSetOfLxIsSentToNode1>=1)))||(i0.i1.u22.Node2ManageTheBreakDownOfNode0>=1))||(i7.i0.u17.Node1ManageTheBreakDownOfNode6>=1))||((i3.u29.Node2HasAskedItsLeafSetToRxToReplaceNode7>=1)&&(i11.u88.LeafSetOfRxIsSentToNode2>=1)))||(i7.i0.u8.Node0ManageTheBreakDownOfNode6>=1))||(u87.Node7HasTheLeafSetOfLxToReplaceNode3>=1))) * ((i0.i0.u1.Node1DontAnswerToAnyNode<1)||(i8.u52.Node5IsActive<1))) * (i2.i1.u71.Node7ManageTheBreakDownOfNode2<1)) * (i4.u62.Node6ManageTheBreakDownOfNode2<1)) * ((i6.i1.u67.Node6WantsToManageTheBreakDownOfNode8<1)||(i6.i1.u11.NoNodeManageTheBreakDownOfNode8<1))))) U (!((((((((u87.Node8HasTheLeafSetOfLxToReplaceNode2<1)&&((i0.i0.u23.NoNodeManageTheBreakDownOfNode1<1)||(i0.i0.u69.Node7WantsToManageTheBreakDownOfNode1<1)))&&(u87.Node5HasTheLeafSetOfLxToReplaceNode0<1))&&((i7.i2.u83.Node8HasAskedItsLeafSetToRxToReplaceNode5<1)||(i11.u86.LeafSetOfRxIsSentToNode8<1)))&&(i1.u37.Node3ManageTheBreakDownOfNode6<1))&&(i2.i0.u14.Node1ManageTheBreakDownOfNode3<1)) + !(E(TRUE U ((((i8.u52.Node5HasAskedItsLeafSetToLxToReplaceNode1>=1)&&(u87.LeafSetOfLxIsSentToNode5>=1))||((i0.i0.u1.BreakDownReservoir>=1)&&(i8.u52.Node5IsActive>=1)))||(i2.i1.u34.Node3ManageTheBreakDownOfNode2>=1)))))) * !(E(!(E(TRUE U !((((((((((i7.i2.u21.Node2IsActive>=1)&&(i7.i2.u59.Node5DontAnswerToAnyNode>=1))||((i1.u38.Node3HasAskedItsLeafSetToRxToReplaceNode7>=1)&&(i11.u88.LeafSetOfRxIsSentToNode3>=1)))||(i6.i1.u20.Node1ManageTheBreakDownOfNode8>=1))||((i0.i0.u23.NoNodeManageTheBreakDownOfNode1>=1)&&(i0.i0.u1.Node2WantsToManageTheBreakDownOfNode1>=1)))||(i7.i2.u16.Node1ManageTheBreakDownOfNode5>=1))||((i5.u26.Node2WantsToManageTheBreakDownOfNode4>=1)&&(i5.u6.NoNodeManageTheBreakDownOfNode4>=1)))||(i8.u52.Node5ManageTheBreakDownOfNode1>=1))||((i8.u52.Node5IsActive>=1)&&(i7.i0.u8.Node6DontAnswerToAnyNode>=1)))))) U ((((EG((((((((((((i3.u57.Node5HasAskedItsLeafSetToRxToReplaceNode7>=1)&&(i11.u88.LeafSetOfRxIsSentToNode5>=1))||(i11.u88.Node8HasTheLeafSetOfRxToReplaceNode6>=1))||(i0.i2.u72.Node7ManageTheBreakDownOfNode3>=1))||(i5.u6.Node0ManageTheBreakDownOfNode4>=1))||((i2.i0.u15.Node1HasAskedItsLeafSetToLxToReplaceNode4>=1)&&(u87.LeafSetOfLxIsSentToNode1>=1)))||(i0.i1.u22.Node2ManageTheBreakDownOfNode0>=1))||(i7.i0.u17.Node1ManageTheBreakDownOfNode6>=1))||((i3.u29.Node2HasAskedItsLeafSetToRxToReplaceNode7>=1)&&(i11.u88.LeafSetOfRxIsSentToNode2>=1)))||(i7.i0.u8.Node0ManageTheBreakDownOfNode6>=1))||(u87.Node7HasTheLeafSetOfLxToReplaceNode3>=1))) * ((i0.i0.u1.Node1DontAnswerToAnyNode<1)||(i8.u52.Node5IsActive<1))) * (i2.i1.u71.Node7ManageTheBreakDownOfNode2<1)) * (i4.u62.Node6ManageTheBreakDownOfNode2<1)) * ((i6.i1.u67.Node6WantsToManageTheBreakDownOfNode8<1)||(i6.i1.u11.NoNodeManageTheBreakDownOfNode8<1)))))))))] != FALSE + [(EY(Init) * (i0.i1.u32.Node3ManageTheBreakDownOfNode0>=1))] != FALSE) + [(EY(Init) * (i11.u88.Node0HasTheLeafSetOfRxToReplaceNode6>=1))] != FALSE)
(forward)formula 9,0,259.861,2570356,1,0,1.94845e+06,763399,5126,6.75861e+06,1295,2.59804e+07,4589747
FORMULA LeafsetExtension-PT-S08C2-CTLFireability-09 FALSE TECHNIQUES DECISION_DIAGRAMS TOPOLOGICAL USE_NUPN
Formula is FALSE !
***************************************
original formula: A((AG(A(((i0.i1.u68.NoNodeManageTheBreakDownOfNode0>=1)&&(i8.u51.Node5WantsToManageTheBreakDownOfNode0>=1)) U ((((((((((u87.Node1HasTheLeafSetOfLxToReplaceNode3<1)&&(((i0.i0.u1.BreakDownReservoir<1)||(i7.i1.u40.Node4IsActive<1))||(i5.u50.Node4isTheNodeMaster<1)))&&((i2.i0.u13.Node1WantsToManageTheBreakDownOfNode2<1)||(i2.i1.u4.NoNodeManageTheBreakDownOfNode2<1)))&&(i4.u62.Node6ManageTheBreakDownOfNode2<1))&&(i11.u88.Node7HasTheLeafSetOfRxToReplaceNode5<1))&&((i7.i2.u16.Node1WantsToManageTheBreakDownOfNode5<1)||(i7.i2.u27.NoNodeManageTheBreakDownOfNode5<1)))&&((i4.u61.Node6IsActive<1)||(i6.i1.u10.Node8DontAnswerToAnyNode<1)))&&((i2.i1.u3.Node2DontAnswerToAnyNode<1)||(i8.u52.Node5IsActive<1)))&&((i7.i1.u40.Node4IsActive<1)||(i6.i1.u10.Node8DontAnswerToAnyNode<1)))||((i1.u38.Node3ManageTheBreakDownOfNode7>=1)&&(u87.Node8HasTheLeafSetOfLxToReplaceNode1>=1))))) + AG(((((((((((i5.u6.NoNodeManageTheBreakDownOfNode4<1)||(i5.u64.Node6WantsToManageTheBreakDownOfNode4<1))&&((i7.i1.u40.Node4IsActive<1)||(i7.i2.u59.Node5DontAnswerToAnyNode<1)))&&(i4.u60.Node6ManageTheBreakDownOfNode0<1))&&((i0.i0.u23.NoNodeManageTheBreakDownOfNode1<1)||(i0.i0.u69.Node7WantsToManageTheBreakDownOfNode1<1)))&&((i0.i2.u24.Node3DontAnswerToAnyNode<1)||(i8.u52.Node5IsActive<1)))&&(u87.Node7HasTheLeafSetOfLxToReplaceNode1<1))&&(i0.i2.u25.Node2ManageTheBreakDownOfNode3<1))&&((i5.u35.Node3HasAskedItsLeafSetToLxToReplaceNode4<1)||(u87.LeafSetOfLxIsSentToNode3<1))) * !(AX(((((u87.Node0HasTheLeafSetOfLxToReplaceNode3>=1)||((i2.i0.u12.Node1IsActive>=1)&&(i5.u50.Node4DontAnswerToAnyNode>=1)))||(i0.i0.u33.Node3ManageTheBreakDownOfNode1>=1))||(u87.Node5HasTheLeafSetOfLxToReplaceNode0>=1))))))) U EG(E(!(AF((((((((i11.u88.Node1HasTheLeafSetOfRxToReplaceNode7>=1)||((i0.i2.u25.Node2HasAskedItsLeafSetToLxToReplaceNode3>=1)&&(u87.LeafSetOfLxIsSentToNode2>=1)))||(u87.Node3HasTheLeafSetOfLxToReplaceNode1>=1))||(u87.Node5HasTheLeafSetOfLxToReplaceNode1>=1))||(i9.u76.Node7ManageTheBreakDownOfNode8>=1))||((i7.i0.u17.Node1HasAskedItsLeafSetToRxToReplaceNode6>=1)&&(i11.u88.LeafSetOfRxIsSentToNode1>=1)))||(i7.i0.u28.Node2ManageTheBreakDownOfNode6>=1)))) U AX((i5.u50.RightNodeHasDetectedBreakDownOfMaster>=1)))))
=> equivalent forward existential formula: [((Init * !(EG(!(EG(E(!(!(EG(!((((((((i11.u88.Node1HasTheLeafSetOfRxToReplaceNode7>=1)||((i0.i2.u25.Node2HasAskedItsLeafSetToLxToReplaceNode3>=1)&&(u87.LeafSetOfLxIsSentToNode2>=1)))||(u87.Node3HasTheLeafSetOfLxToReplaceNode1>=1))||(u87.Node5HasTheLeafSetOfLxToReplaceNode1>=1))||(i9.u76.Node7ManageTheBreakDownOfNode8>=1))||((i7.i0.u17.Node1HasAskedItsLeafSetToRxToReplaceNode6>=1)&&(i11.u88.LeafSetOfRxIsSentToNode1>=1)))||(i7.i0.u28.Node2ManageTheBreakDownOfNode6>=1)))))) U !(EX(!((i5.u50.RightNodeHasDetectedBreakDownOfMaster>=1)))))))))) * !(E(!(EG(E(!(!(EG(!((((((((i11.u88.Node1HasTheLeafSetOfRxToReplaceNode7>=1)||((i0.i2.u25.Node2HasAskedItsLeafSetToLxToReplaceNode3>=1)&&(u87.LeafSetOfLxIsSentToNode2>=1)))||(u87.Node3HasTheLeafSetOfLxToReplaceNode1>=1))||(u87.Node5HasTheLeafSetOfLxToReplaceNode1>=1))||(i9.u76.Node7ManageTheBreakDownOfNode8>=1))||((i7.i0.u17.Node1HasAskedItsLeafSetToRxToReplaceNode6>=1)&&(i11.u88.LeafSetOfRxIsSentToNode1>=1)))||(i7.i0.u28.Node2ManageTheBreakDownOfNode6>=1)))))) U !(EX(!((i5.u50.RightNodeHasDetectedBreakDownOfMaster>=1))))))) U (!((!(E(TRUE U !(!((E(!(((((((((((u87.Node1HasTheLeafSetOfLxToReplaceNode3<1)&&(((i0.i0.u1.BreakDownReservoir<1)||(i7.i1.u40.Node4IsActive<1))||(i5.u50.Node4isTheNodeMaster<1)))&&((i2.i0.u13.Node1WantsToManageTheBreakDownOfNode2<1)||(i2.i1.u4.NoNodeManageTheBreakDownOfNode2<1)))&&(i4.u62.Node6ManageTheBreakDownOfNode2<1))&&(i11.u88.Node7HasTheLeafSetOfRxToReplaceNode5<1))&&((i7.i2.u16.Node1WantsToManageTheBreakDownOfNode5<1)||(i7.i2.u27.NoNodeManageTheBreakDownOfNode5<1)))&&((i4.u61.Node6IsActive<1)||(i6.i1.u10.Node8DontAnswerToAnyNode<1)))&&((i2.i1.u3.Node2DontAnswerToAnyNode<1)||(i8.u52.Node5IsActive<1)))&&((i7.i1.u40.Node4IsActive<1)||(i6.i1.u10.Node8DontAnswerToAnyNode<1)))||((i1.u38.Node3ManageTheBreakDownOfNode7>=1)&&(u87.Node8HasTheLeafSetOfLxToReplaceNode1>=1)))) U (!(((i0.i1.u68.NoNodeManageTheBreakDownOfNode0>=1)&&(i8.u51.Node5WantsToManageTheBreakDownOfNode0>=1))) * !(((((((((((u87.Node1HasTheLeafSetOfLxToReplaceNode3<1)&&(((i0.i0.u1.BreakDownReservoir<1)||(i7.i1.u40.Node4IsActive<1))||(i5.u50.Node4isTheNodeMaster<1)))&&((i2.i0.u13.Node1WantsToManageTheBreakDownOfNode2<1)||(i2.i1.u4.NoNodeManageTheBreakDownOfNode2<1)))&&(i4.u62.Node6ManageTheBreakDownOfNode2<1))&&(i11.u88.Node7HasTheLeafSetOfRxToReplaceNode5<1))&&((i7.i2.u16.Node1WantsToManageTheBreakDownOfNode5<1)||(i7.i2.u27.NoNodeManageTheBreakDownOfNode5<1)))&&((i4.u61.Node6IsActive<1)||(i6.i1.u10.Node8DontAnswerToAnyNode<1)))&&((i2.i1.u3.Node2DontAnswerToAnyNode<1)||(i8.u52.Node5IsActive<1)))&&((i7.i1.u40.Node4IsActive<1)||(i6.i1.u10.Node8DontAnswerToAnyNode<1)))||((i1.u38.Node3ManageTheBreakDownOfNode7>=1)&&(u87.Node8HasTheLeafSetOfLxToReplaceNode1>=1)))))) + EG(!(((((((((((u87.Node1HasTheLeafSetOfLxToReplaceNode3<1)&&(((i0.i0.u1.BreakDownReservoir<1)||(i7.i1.u40.Node4IsActive<1))||(i5.u50.Node4isTheNodeMaster<1)))&&((i2.i0.u13.Node1WantsToManageTheBreakDownOfNode2<1)||(i2.i1.u4.NoNodeManageTheBreakDownOfNode2<1)))&&(i4.u62.Node6ManageTheBreakDownOfNode2<1))&&(i11.u88.Node7HasTheLeafSetOfRxToReplaceNode5<1))&&((i7.i2.u16.Node1WantsToManageTheBreakDownOfNode5<1)||(i7.i2.u27.NoNodeManageTheBreakDownOfNode5<1)))&&((i4.u61.Node6IsActive<1)||(i6.i1.u10.Node8DontAnswerToAnyNode<1)))&&((i2.i1.u3.Node2DontAnswerToAnyNode<1)||(i8.u52.Node5IsActive<1)))&&((i7.i1.u40.Node4IsActive<1)||(i6.i1.u10.Node8DontAnswerToAnyNode<1)))||((i1.u38.Node3ManageTheBreakDownOfNode7>=1)&&(u87.Node8HasTheLeafSetOfLxToReplaceNode1>=1)))))))))) + !(E(TRUE U !(((((((((((i5.u6.NoNodeManageTheBreakDownOfNode4<1)||(i5.u64.Node6WantsToManageTheBreakDownOfNode4<1))&&((i7.i1.u40.Node4IsActive<1)||(i7.i2.u59.Node5DontAnswerToAnyNode<1)))&&(i4.u60.Node6ManageTheBreakDownOfNode0<1))&&((i0.i0.u23.NoNodeManageTheBreakDownOfNode1<1)||(i0.i0.u69.Node7WantsToManageTheBreakDownOfNode1<1)))&&((i0.i2.u24.Node3DontAnswerToAnyNode<1)||(i8.u52.Node5IsActive<1)))&&(u87.Node7HasTheLeafSetOfLxToReplaceNode1<1))&&(i0.i2.u25.Node2ManageTheBreakDownOfNode3<1))&&((i5.u35.Node3HasAskedItsLeafSetToLxToReplaceNode4<1)||(u87.LeafSetOfLxIsSentToNode3<1))) * !(!(EX(!(((((u87.Node0HasTheLeafSetOfLxToReplaceNode3>=1)||((i2.i0.u12.Node1IsActive>=1)&&(i5.u50.Node4DontAnswerToAnyNode>=1)))||(i0.i0.u33.Node3ManageTheBreakDownOfNode1>=1))||(u87.Node5HasTheLeafSetOfLxToReplaceNode0>=1)))))))))))) * !(EG(E(!(!(EG(!((((((((i11.u88.Node1HasTheLeafSetOfRxToReplaceNode7>=1)||((i0.i2.u25.Node2HasAskedItsLeafSetToLxToReplaceNode3>=1)&&(u87.LeafSetOfLxIsSentToNode2>=1)))||(u87.Node3HasTheLeafSetOfLxToReplaceNode1>=1))||(u87.Node5HasTheLeafSetOfLxToReplaceNode1>=1))||(i9.u76.Node7ManageTheBreakDownOfNode8>=1))||((i7.i0.u17.Node1HasAskedItsLeafSetToRxToReplaceNode6>=1)&&(i11.u88.LeafSetOfRxIsSentToNode1>=1)))||(i7.i0.u28.Node2ManageTheBreakDownOfNode6>=1)))))) U !(EX(!((i5.u50.RightNodeHasDetectedBreakDownOfMaster>=1)))))))))))] != FALSE
(forward)formula 10,1,273.826,2570356,1,0,1.94845e+06,763399,5353,6.75861e+06,1301,2.59804e+07,5915170
FORMULA LeafsetExtension-PT-S08C2-CTLFireability-10 TRUE TECHNIQUES DECISION_DIAGRAMS TOPOLOGICAL USE_NUPN
Formula is TRUE !
***************************************
original formula: EF(!(EX(EF(EG((((((i3.u85.Node8HasAskedItsLeafSetToRxToReplaceNode7>=1)&&(i11.u86.LeafSetOfRxIsSentToNode8>=1))||((i1.u31.Node3IsActive>=1)&&(i7.i0.u8.Node6DontAnswerToAnyNode>=1)))||((i0.i0.u23.NoNodeManageTheBreakDownOfNode1>=1)&&(i0.i0.u42.Node4WantsToManageTheBreakDownOfNode1>=1)))||((i6.i1.u67.Node6HasAskedItsLeafSetToRxToReplaceNode8>=1)&&(i11.u88.LeafSetOfRxIsSentToNode6>=1))))))))
=> equivalent forward existential formula: [(FwdU(Init,TRUE) * !(EX(E(TRUE U EG((((((i3.u85.Node8HasAskedItsLeafSetToRxToReplaceNode7>=1)&&(i11.u86.LeafSetOfRxIsSentToNode8>=1))||((i1.u31.Node3IsActive>=1)&&(i7.i0.u8.Node6DontAnswerToAnyNode>=1)))||((i0.i0.u23.NoNodeManageTheBreakDownOfNode1>=1)&&(i0.i0.u42.Node4WantsToManageTheBreakDownOfNode1>=1)))||((i6.i1.u67.Node6HasAskedItsLeafSetToRxToReplaceNode8>=1)&&(i11.u88.LeafSetOfRxIsSentToNode6>=1))))))))] != FALSE
(forward)formula 11,1,273.85,2570356,1,0,1.94845e+06,763399,5393,6.75861e+06,1301,2.59804e+07,5933527
FORMULA LeafsetExtension-PT-S08C2-CTLFireability-11 TRUE TECHNIQUES DECISION_DIAGRAMS TOPOLOGICAL USE_NUPN
Formula is TRUE !
***************************************
original formula: AF(E(EX((E((((((i11.u88.Node5HasTheLeafSetOfRxToReplaceNode7>=1)||((i4.u62.Node6HasAskedItsLeafSetToLxToReplaceNode2>=1)&&(u87.LeafSetOfLxIsSentToNode6>=1)))||(i0.i0.u42.Node4ManageTheBreakDownOfNode1>=1))||(i2.i1.u34.Node3ManageTheBreakDownOfNode2>=1))||((i8.u51.RequestOfNode5IsSentToLx>=1)&&(u87.LxIsActiveAndNotInTheLeafSet>=1))) U ((((((((i7.i0.u8.Node6DontAnswerToAnyNode>=1)&&(i10.u78.Node8IsActive>=1))||(i0.i1.u68.Node7ManageTheBreakDownOfNode0>=1))||(i11.u88.Node7HasTheLeafSetOfRxToReplaceNode6>=1))||(i11.u88.Node5HasTheLeafSetOfRxToReplaceNode7>=1))||((i7.i0.u47.NoNodeManageTheBreakDownOfNode6>=1)&&(i9.u75.Node7WantsToManageTheBreakDownOfNode6>=1)))||((i0.i1.u68.NoNodeManageTheBreakDownOfNode0>=1)&&(i0.i1.u41.Node4WantsToManageTheBreakDownOfNode0>=1)))||((i3.u66.Node6HasAskedItsLeafSetToRxToReplaceNode7>=1)&&(i11.u88.LeafSetOfRxIsSentToNode6>=1)))) * E((((i3.u66.Node6ManageTheBreakDownOfNode7>=1)||(i5.u35.Node3ManageTheBreakDownOfNode4>=1))||(u87.Node5HasTheLeafSetOfLxToReplaceNode0>=1)) U (((((((((((i7.i1.u49.Node4HasAskedItsLeafSetToRxToReplaceNode8>=1)&&(i11.u46.LeafSetOfRxIsSentToNode4>=1))||((i4.u62.Node6HasAskedItsLeafSetToLxToReplaceNode2>=1)&&(u87.LeafSetOfLxIsSentToNode6>=1)))||((i0.i1.u68.NoNodeManageTheBreakDownOfNode0>=1)&&(i8.u51.Node5WantsToManageTheBreakDownOfNode0>=1)))||(i11.u88.Node3HasTheLeafSetOfRxToReplaceNode5>=1))||((i7.i2.u27.NoNodeManageTheBreakDownOfNode5>=1)&&(i7.i2.u65.Node6WantsToManageTheBreakDownOfNode5>=1)))||((i7.i1.u40.Node4IsActive>=1)&&(i6.i1.u10.Node8DontAnswerToAnyNode>=1)))||((i8.u52.Node5IsActive>=1)&&(i3.u18.Node7DontAnswerToAnyNode>=1)))||(u87.Node4HasTheLeafSetOfLxToReplaceNode1>=1))||(i5.u55.Node5ManageTheBreakDownOfNode4>=1))||(i2.i0.u14.Node1ManageTheBreakDownOfNode3>=1))))) U EX(((((i9.u76.Node7ManageTheBreakDownOfNode8>=1)||((i3.u57.Node5HasAskedItsLeafSetToRxToReplaceNode7>=1)&&(i11.u88.LeafSetOfRxIsSentToNode5>=1)))||((i6.i0.u0.Node0WantsToManageTheBreakDownOfNode3>=1)&&(i0.i2.u5.NoNodeManageTheBreakDownOfNode3>=1)))||((i3.u66.Node6HasAskedItsLeafSetToRxToReplaceNode7>=1)&&(i11.u88.LeafSetOfRxIsSentToNode6>=1))))))
=> equivalent forward existential formula: [FwdG(Init,!(E(EX((E((((((i11.u88.Node5HasTheLeafSetOfRxToReplaceNode7>=1)||((i4.u62.Node6HasAskedItsLeafSetToLxToReplaceNode2>=1)&&(u87.LeafSetOfLxIsSentToNode6>=1)))||(i0.i0.u42.Node4ManageTheBreakDownOfNode1>=1))||(i2.i1.u34.Node3ManageTheBreakDownOfNode2>=1))||((i8.u51.RequestOfNode5IsSentToLx>=1)&&(u87.LxIsActiveAndNotInTheLeafSet>=1))) U ((((((((i7.i0.u8.Node6DontAnswerToAnyNode>=1)&&(i10.u78.Node8IsActive>=1))||(i0.i1.u68.Node7ManageTheBreakDownOfNode0>=1))||(i11.u88.Node7HasTheLeafSetOfRxToReplaceNode6>=1))||(i11.u88.Node5HasTheLeafSetOfRxToReplaceNode7>=1))||((i7.i0.u47.NoNodeManageTheBreakDownOfNode6>=1)&&(i9.u75.Node7WantsToManageTheBreakDownOfNode6>=1)))||((i0.i1.u68.NoNodeManageTheBreakDownOfNode0>=1)&&(i0.i1.u41.Node4WantsToManageTheBreakDownOfNode0>=1)))||((i3.u66.Node6HasAskedItsLeafSetToRxToReplaceNode7>=1)&&(i11.u88.LeafSetOfRxIsSentToNode6>=1)))) * E((((i3.u66.Node6ManageTheBreakDownOfNode7>=1)||(i5.u35.Node3ManageTheBreakDownOfNode4>=1))||(u87.Node5HasTheLeafSetOfLxToReplaceNode0>=1)) U (((((((((((i7.i1.u49.Node4HasAskedItsLeafSetToRxToReplaceNode8>=1)&&(i11.u46.LeafSetOfRxIsSentToNode4>=1))||((i4.u62.Node6HasAskedItsLeafSetToLxToReplaceNode2>=1)&&(u87.LeafSetOfLxIsSentToNode6>=1)))||((i0.i1.u68.NoNodeManageTheBreakDownOfNode0>=1)&&(i8.u51.Node5WantsToManageTheBreakDownOfNode0>=1)))||(i11.u88.Node3HasTheLeafSetOfRxToReplaceNode5>=1))||((i7.i2.u27.NoNodeManageTheBreakDownOfNode5>=1)&&(i7.i2.u65.Node6WantsToManageTheBreakDownOfNode5>=1)))||((i7.i1.u40.Node4IsActive>=1)&&(i6.i1.u10.Node8DontAnswerToAnyNode>=1)))||((i8.u52.Node5IsActive>=1)&&(i3.u18.Node7DontAnswerToAnyNode>=1)))||(u87.Node4HasTheLeafSetOfLxToReplaceNode1>=1))||(i5.u55.Node5ManageTheBreakDownOfNode4>=1))||(i2.i0.u14.Node1ManageTheBreakDownOfNode3>=1))))) U EX(((((i9.u76.Node7ManageTheBreakDownOfNode8>=1)||((i3.u57.Node5HasAskedItsLeafSetToRxToReplaceNode7>=1)&&(i11.u88.LeafSetOfRxIsSentToNode5>=1)))||((i6.i0.u0.Node0WantsToManageTheBreakDownOfNode3>=1)&&(i0.i2.u5.NoNodeManageTheBreakDownOfNode3>=1)))||((i3.u66.Node6HasAskedItsLeafSetToRxToReplaceNode7>=1)&&(i11.u88.LeafSetOfRxIsSentToNode6>=1)))))))] = FALSE
(forward)formula 12,0,288.103,2570356,1,0,1.94845e+06,763399,5555,6.75861e+06,1310,2.59804e+07,7502425
FORMULA LeafsetExtension-PT-S08C2-CTLFireability-12 FALSE TECHNIQUES DECISION_DIAGRAMS TOPOLOGICAL USE_NUPN
Formula is FALSE !
***************************************
original formula: A(EG(((AF(((((((((((((((((i11.u46.RxHasReceivedTheRequestOfNode4>=1)||(u87.Node1HasTheLeafSetOfLxToReplaceNode4>=1))||((i1.u31.Node3IsActive>=1)&&(i3.u18.Node7DontAnswerToAnyNode>=1)))||(i11.u88.Node3HasTheLeafSetOfRxToReplaceNode7>=1))||((i0.i1.u68.NoNodeManageTheBreakDownOfNode0>=1)&&(i0.i1.u41.Node4WantsToManageTheBreakDownOfNode0>=1)))||((i0.i0.u69.Node7HasAskedItsLeafSetToLxToReplaceNode1>=1)&&(u87.LeafSetOfLxIsSentToNode7>=1)))||((i2.i0.u12.Node1HasAskedItsLeafSetToLxToReplaceNode0>=1)&&(u87.LeafSetOfLxIsSentToNode1>=1)))||((i3.u85.Node8HasAskedItsLeafSetToRxToReplaceNode7>=1)&&(i11.u86.LeafSetOfRxIsSentToNode8>=1)))||((i7.i0.u8.Node6DontAnswerToAnyNode>=1)&&(i9.u70.Node7IsActive>=1)))||((i6.i0.u0.Node0IsActive>=1)&&(i5.u50.Node4DontAnswerToAnyNode>=1)))||((i0.i1.u68.NoNodeManageTheBreakDownOfNode0>=1)&&(i0.i1.u22.Node2WantsToManageTheBreakDownOfNode0>=1)))||(i11.u88.Node7HasTheLeafSetOfRxToReplaceNode8>=1))||((i10.u79.Node8HasAskedItsLeafSetToLxToReplaceNode1>=1)&&(u87.LeafSetOfLxIsSentToNode8>=1)))||((i0.i2.u72.Node7HasAskedItsLeafSetToLxToReplaceNode3>=1)&&(u87.LeafSetOfLxIsSentToNode7>=1)))||(i11.u88.Node1HasTheLeafSetOfRxToReplaceNode5>=1))||(u87.Node6HasTheLeafSetOfLxToReplaceNode0>=1))) + E(((((i11.u88.Node0HasTheLeafSetOfRxToReplaceNode7<1)&&(i2.i0.u13.Node1ManageTheBreakDownOfNode2<1))&&(i0.i0.u23.Node2ManageTheBreakDownOfNode1<1))&&((i7.i1.u40.Node4IsActive<1)||(i6.i1.u10.Node8DontAnswerToAnyNode<1))) U EX((((((i9.u76.Node7WantsToManageTheBreakDownOfNode8>=1)&&(i6.i1.u11.NoNodeManageTheBreakDownOfNode8>=1))||((i3.u29.Node2HasAskedItsLeafSetToRxToReplaceNode7>=1)&&(i11.u88.LeafSetOfRxIsSentToNode2>=1)))||((i7.i0.u17.Node1HasAskedItsLeafSetToRxToReplaceNode6>=1)&&(i11.u88.LeafSetOfRxIsSentToNode1>=1)))||((i4.u63.Node6HasAskedItsLeafSetToLxToReplaceNode3>=1)&&(u87.LeafSetOfLxIsSentToNode6>=1)))))) + ((AX((((((((((i6.i0.u9.Node0HasAskedItsLeafSetToRxToReplaceNode7>=1)&&(i11.u88.LeafSetOfRxIsSentToNode0>=1))||((i2.i0.u15.Node1HasAskedItsLeafSetToLxToReplaceNode4>=1)&&(u87.LeafSetOfLxIsSentToNode1>=1)))||(u87.Node8HasTheLeafSetOfLxToReplaceNode2>=1))||((i0.i0.u1.BreakDownReservoir>=1)&&(i1.u31.Node3IsActive>=1)))||((i4.u61.Node6HasAskedItsLeafSetToLxToReplaceNode1>=1)&&(u87.LeafSetOfLxIsSentToNode6>=1)))||((i2.i1.u4.NoNodeManageTheBreakDownOfNode2>=1)&&(i2.i1.u43.Node4WantsToManageTheBreakDownOfNode2>=1)))||(u87.Node7HasTheLeafSetOfLxToReplaceNode3>=1))||(i1.u37.Node3ManageTheBreakDownOfNode6>=1))) + AF((u87.Node8HasTheLeafSetOfLxToReplaceNode3>=1))) * (EG((((i3.u48.Node4HasAskedItsLeafSetToRxToReplaceNode7>=1)&&(i11.u46.LeafSetOfRxIsSentToNode4>=1))||((i6.i1.u11.Node0HasAskedItsLeafSetToRxToReplaceNode8>=1)&&(i11.u88.LeafSetOfRxIsSentToNode0>=1)))) + (A((u87.Node6HasTheLeafSetOfLxToReplaceNode0>=1) U (((((((((i7.i0.u28.Node2WantsToManageTheBreakDownOfNode6>=1)&&(i7.i0.u47.NoNodeManageTheBreakDownOfNode6>=1))||((i5.u82.Node8HasAskedItsLeafSetToRxToReplaceNode4>=1)&&(i11.u86.LeafSetOfRxIsSentToNode8>=1)))||((i0.i1.u41.RequestOfNode4IsSentToLx>=1)&&(u87.LxIsActiveAndNotInTheLeafSet>=1)))||(i0.i2.u44.Node4ManageTheBreakDownOfNode3>=1))||(u87.LxHasReceivedTheRequestOfNode2>=1))||(i0.i2.u25.Node2ManageTheBreakDownOfNode3>=1))||((i7.i2.u21.Node2IsActive>=1)&&(i0.i2.u24.Node3DontAnswerToAnyNode>=1)))||(u87.LxHasReceivedTheRequestOfNode0>=1))) * EF(((((((((i9.u76.Node7WantsToManageTheBreakDownOfNode8>=1)&&(i6.i1.u11.NoNodeManageTheBreakDownOfNode8>=1))||((i4.u62.Node6HasAskedItsLeafSetToLxToReplaceNode2>=1)&&(u87.LeafSetOfLxIsSentToNode6>=1)))||((i5.u55.RequestOfNode5IsSentToRx>=1)&&(i11.u88.RxIsActiveAndNotInTheLeafSet>=1)))||((i0.i0.u23.NoNodeManageTheBreakDownOfNode1>=1)&&(i10.u78.Node8WantsToManageTheBreakDownOfNode1>=1)))||((i5.u50.Node4DontAnswerToAnyNode>=1)&&(i9.u70.Node7IsActive>=1)))||((i3.u18.Node7DontAnswerToAnyNode>=1)&&(i10.u78.Node8IsActive>=1)))||(u87.Node5HasTheLeafSetOfLxToReplaceNode0>=1)))))))) U !(A((EG((i11.u86.RxHasReceivedTheRequestOfNode8<1)) + !(A((((((i5.u6.NoNodeManageTheBreakDownOfNode4>=1)&&(i5.u82.Node8WantsToManageTheBreakDownOfNode4>=1))||((i8.u51.Node5HasAskedItsLeafSetToLxToReplaceNode0>=1)&&(u87.LeafSetOfLxIsSentToNode5>=1)))||((i2.i1.u4.NoNodeManageTheBreakDownOfNode2>=1)&&(i4.u62.Node6WantsToManageTheBreakDownOfNode2>=1)))||(u87.Node7HasTheLeafSetOfLxToReplaceNode3>=1)) U ((((((((((i3.u29.Node2WantsToManageTheBreakDownOfNode7>=1)&&(i3.u48.NoNodeManageTheBreakDownOfNode7>=1))||((i7.i0.u8.Node6DontAnswerToAnyNode>=1)&&(i10.u78.Node8IsActive>=1)))||(i11.u88.Node6HasTheLeafSetOfRxToReplaceNode7>=1))||((i3.u48.NoNodeManageTheBreakDownOfNode7>=1)&&(i3.u85.Node8WantsToManageTheBreakDownOfNode7>=1)))||(i11.u88.Node2HasTheLeafSetOfRxToReplaceNode5>=1))||(i11.u88.Node3HasTheLeafSetOfRxToReplaceNode5>=1))||((i0.i2.u5.NoNodeManageTheBreakDownOfNode3>=1)&&(i8.u54.Node5WantsToManageTheBreakDownOfNode3>=1)))||(i11.u88.RxHasReceivedTheRequestOfNode5>=1))||((i2.i0.u12.Node1IsActive>=1)&&(i7.i2.u59.Node5DontAnswerToAnyNode>=1)))))) U ((((i5.u55.Node5HasAskedItsLeafSetToRxToReplaceNode4>=1)&&(i11.u88.LeafSetOfRxIsSentToNode5>=1))||((i0.i0.u23.NoNodeManageTheBreakDownOfNode1>=1)&&(i10.u78.Node8WantsToManageTheBreakDownOfNode1>=1)))||((i6.i1.u58.Node5WantsToManageTheBreakDownOfNode8>=1)&&(i6.i1.u11.NoNodeManageTheBreakDownOfNode8>=1))))))
=> equivalent forward existential formula: [((Init * !(EG(!(!(!((E(!(((((i5.u55.Node5HasAskedItsLeafSetToRxToReplaceNode4>=1)&&(i11.u88.LeafSetOfRxIsSentToNode5>=1))||((i0.i0.u23.NoNodeManageTheBreakDownOfNode1>=1)&&(i10.u78.Node8WantsToManageTheBreakDownOfNode1>=1)))||((i6.i1.u58.Node5WantsToManageTheBreakDownOfNode8>=1)&&(i6.i1.u11.NoNodeManageTheBreakDownOfNode8>=1)))) U (!((EG((i11.u86.RxHasReceivedTheRequestOfNode8<1)) + !(!((E(!(((((((((((i3.u29.Node2WantsToManageTheBreakDownOfNode7>=1)&&(i3.u48.NoNodeManageTheBreakDownOfNode7>=1))||((i7.i0.u8.Node6DontAnswerToAnyNode>=1)&&(i10.u78.Node8IsActive>=1)))||(i11.u88.Node6HasTheLeafSetOfRxToReplaceNode7>=1))||((i3.u48.NoNodeManageTheBreakDownOfNode7>=1)&&(i3.u85.Node8WantsToManageTheBreakDownOfNode7>=1)))||(i11.u88.Node2HasTheLeafSetOfRxToReplaceNode5>=1))||(i11.u88.Node3HasTheLeafSetOfRxToReplaceNode5>=1))||((i0.i2.u5.NoNodeManageTheBreakDownOfNode3>=1)&&(i8.u54.Node5WantsToManageTheBreakDownOfNode3>=1)))||(i11.u88.RxHasReceivedTheRequestOfNode5>=1))||((i2.i0.u12.Node1IsActive>=1)&&(i7.i2.u59.Node5DontAnswerToAnyNode>=1)))) U (!((((((i5.u6.NoNodeManageTheBreakDownOfNode4>=1)&&(i5.u82.Node8WantsToManageTheBreakDownOfNode4>=1))||((i8.u51.Node5HasAskedItsLeafSetToLxToReplaceNode0>=1)&&(u87.LeafSetOfLxIsSentToNode5>=1)))||((i2.i1.u4.NoNodeManageTheBreakDownOfNode2>=1)&&(i4.u62.Node6WantsToManageTheBreakDownOfNode2>=1)))||(u87.Node7HasTheLeafSetOfLxToReplaceNode3>=1))) * !(((((((((((i3.u29.Node2WantsToManageTheBreakDownOfNode7>=1)&&(i3.u48.NoNodeManageTheBreakDownOfNode7>=1))||((i7.i0.u8.Node6DontAnswerToAnyNode>=1)&&(i10.u78.Node8IsActive>=1)))||(i11.u88.Node6HasTheLeafSetOfRxToReplaceNode7>=1))||((i3.u48.NoNodeManageTheBreakDownOfNode7>=1)&&(i3.u85.Node8WantsToManageTheBreakDownOfNode7>=1)))||(i11.u88.Node2HasTheLeafSetOfRxToReplaceNode5>=1))||(i11.u88.Node3HasTheLeafSetOfRxToReplaceNode5>=1))||((i0.i2.u5.NoNodeManageTheBreakDownOfNode3>=1)&&(i8.u54.Node5WantsToManageTheBreakDownOfNode3>=1)))||(i11.u88.RxHasReceivedTheRequestOfNode5>=1))||((i2.i0.u12.Node1IsActive>=1)&&(i7.i2.u59.Node5DontAnswerToAnyNode>=1)))))) + EG(!(((((((((((i3.u29.Node2WantsToManageTheBreakDownOfNode7>=1)&&(i3.u48.NoNodeManageTheBreakDownOfNode7>=1))||((i7.i0.u8.Node6DontAnswerToAnyNode>=1)&&(i10.u78.Node8IsActive>=1)))||(i11.u88.Node6HasTheLeafSetOfRxToReplaceNode7>=1))||((i3.u48.NoNodeManageTheBreakDownOfNode7>=1)&&(i3.u85.Node8WantsToManageTheBreakDownOfNode7>=1)))||(i11.u88.Node2HasTheLeafSetOfRxToReplaceNode5>=1))||(i11.u88.Node3HasTheLeafSetOfRxToReplaceNode5>=1))||((i0.i2.u5.NoNodeManageTheBreakDownOfNode3>=1)&&(i8.u54.Node5WantsToManageTheBreakDownOfNode3>=1)))||(i11.u88.RxHasReceivedTheRequestOfNode5>=1))||((i2.i0.u12.Node1IsActive>=1)&&(i7.i2.u59.Node5DontAnswerToAnyNode>=1)))))))))) * !(((((i5.u55.Node5HasAskedItsLeafSetToRxToReplaceNode4>=1)&&(i11.u88.LeafSetOfRxIsSentToNode5>=1))||((i0.i0.u23.NoNodeManageTheBreakDownOfNode1>=1)&&(i10.u78.Node8WantsToManageTheBreakDownOfNode1>=1)))||((i6.i1.u58.Node5WantsToManageTheBreakDownOfNode8>=1)&&(i6.i1.u11.NoNodeManageTheBreakDownOfNode8>=1)))))) + EG(!(((((i5.u55.Node5HasAskedItsLeafSetToRxToReplaceNode4>=1)&&(i11.u88.LeafSetOfRxIsSentToNode5>=1))||((i0.i0.u23.NoNodeManageTheBreakDownOfNode1>=1)&&(i10.u78.Node8WantsToManageTheBreakDownOfNode1>=1)))||((i6.i1.u58.Node5WantsToManageTheBreakDownOfNode8>=1)&&(i6.i1.u11.NoNodeManageTheBreakDownOfNode8>=1)))))))))))) * !(E(!(!(!((E(!(((((i5.u55.Node5HasAskedItsLeafSetToRxToReplaceNode4>=1)&&(i11.u88.LeafSetOfRxIsSentToNode5>=1))||((i0.i0.u23.NoNodeManageTheBreakDownOfNode1>=1)&&(i10.u78.Node8WantsToManageTheBreakDownOfNode1>=1)))||((i6.i1.u58.Node5WantsToManageTheBreakDownOfNode8>=1)&&(i6.i1.u11.NoNodeManageTheBreakDownOfNode8>=1)))) U (!((EG((i11.u86.RxHasReceivedTheRequestOfNode8<1)) + !(!((E(!(((((((((((i3.u29.Node2WantsToManageTheBreakDownOfNode7>=1)&&(i3.u48.NoNodeManageTheBreakDownOfNode7>=1))||((i7.i0.u8.Node6DontAnswerToAnyNode>=1)&&(i10.u78.Node8IsActive>=1)))||(i11.u88.Node6HasTheLeafSetOfRxToReplaceNode7>=1))||((i3.u48.NoNodeManageTheBreakDownOfNode7>=1)&&(i3.u85.Node8WantsToManageTheBreakDownOfNode7>=1)))||(i11.u88.Node2HasTheLeafSetOfRxToReplaceNode5>=1))||(i11.u88.Node3HasTheLeafSetOfRxToReplaceNode5>=1))||((i0.i2.u5.NoNodeManageTheBreakDownOfNode3>=1)&&(i8.u54.Node5WantsToManageTheBreakDownOfNode3>=1)))||(i11.u88.RxHasReceivedTheRequestOfNode5>=1))||((i2.i0.u12.Node1IsActive>=1)&&(i7.i2.u59.Node5DontAnswerToAnyNode>=1)))) U (!((((((i5.u6.NoNodeManageTheBreakDownOfNode4>=1)&&(i5.u82.Node8WantsToManageTheBreakDownOfNode4>=1))||((i8.u51.Node5HasAskedItsLeafSetToLxToReplaceNode0>=1)&&(u87.LeafSetOfLxIsSentToNode5>=1)))||((i2.i1.u4.NoNodeManageTheBreakDownOfNode2>=1)&&(i4.u62.Node6WantsToManageTheBreakDownOfNode2>=1)))||(u87.Node7HasTheLeafSetOfLxToReplaceNode3>=1))) * !(((((((((((i3.u29.Node2WantsToManageTheBreakDownOfNode7>=1)&&(i3.u48.NoNodeManageTheBreakDownOfNode7>=1))||((i7.i0.u8.Node6DontAnswerToAnyNode>=1)&&(i10.u78.Node8IsActive>=1)))||(i11.u88.Node6HasTheLeafSetOfRxToReplaceNode7>=1))||((i3.u48.NoNodeManageTheBreakDownOfNode7>=1)&&(i3.u85.Node8WantsToManageTheBreakDownOfNode7>=1)))||(i11.u88.Node2HasTheLeafSetOfRxToReplaceNode5>=1))||(i11.u88.Node3HasTheLeafSetOfRxToReplaceNode5>=1))||((i0.i2.u5.NoNodeManageTheBreakDownOfNode3>=1)&&(i8.u54.Node5WantsToManageTheBreakDownOfNode3>=1)))||(i11.u88.RxHasReceivedTheRequestOfNode5>=1))||((i2.i0.u12.Node1IsActive>=1)&&(i7.i2.u59.Node5DontAnswerToAnyNode>=1)))))) + EG(!(((((((((((i3.u29.Node2WantsToManageTheBreakDownOfNode7>=1)&&(i3.u48.NoNodeManageTheBreakDownOfNode7>=1))||((i7.i0.u8.Node6DontAnswerToAnyNode>=1)&&(i10.u78.Node8IsActive>=1)))||(i11.u88.Node6HasTheLeafSetOfRxToReplaceNode7>=1))||((i3.u48.NoNodeManageTheBreakDownOfNode7>=1)&&(i3.u85.Node8WantsToManageTheBreakDownOfNode7>=1)))||(i11.u88.Node2HasTheLeafSetOfRxToReplaceNode5>=1))||(i11.u88.Node3HasTheLeafSetOfRxToReplaceNode5>=1))||((i0.i2.u5.NoNodeManageTheBreakDownOfNode3>=1)&&(i8.u54.Node5WantsToManageTheBreakDownOfNode3>=1)))||(i11.u88.RxHasReceivedTheRequestOfNode5>=1))||((i2.i0.u12.Node1IsActive>=1)&&(i7.i2.u59.Node5DontAnswerToAnyNode>=1)))))))))) * !(((((i5.u55.Node5HasAskedItsLeafSetToRxToReplaceNode4>=1)&&(i11.u88.LeafSetOfRxIsSentToNode5>=1))||((i0.i0.u23.NoNodeManageTheBreakDownOfNode1>=1)&&(i10.u78.Node8WantsToManageTheBreakDownOfNode1>=1)))||((i6.i1.u58.Node5WantsToManageTheBreakDownOfNode8>=1)&&(i6.i1.u11.NoNodeManageTheBreakDownOfNode8>=1)))))) + EG(!(((((i5.u55.Node5HasAskedItsLeafSetToRxToReplaceNode4>=1)&&(i11.u88.LeafSetOfRxIsSentToNode5>=1))||((i0.i0.u23.NoNodeManageTheBreakDownOfNode1>=1)&&(i10.u78.Node8WantsToManageTheBreakDownOfNode1>=1)))||((i6.i1.u58.Node5WantsToManageTheBreakDownOfNode8>=1)&&(i6.i1.u11.NoNodeManageTheBreakDownOfNode8>=1))))))))) U (!(EG(((!(EG(!(((((((((((((((((i11.u46.RxHasReceivedTheRequestOfNode4>=1)||(u87.Node1HasTheLeafSetOfLxToReplaceNode4>=1))||((i1.u31.Node3IsActive>=1)&&(i3.u18.Node7DontAnswerToAnyNode>=1)))||(i11.u88.Node3HasTheLeafSetOfRxToReplaceNode7>=1))||((i0.i1.u68.NoNodeManageTheBreakDownOfNode0>=1)&&(i0.i1.u41.Node4WantsToManageTheBreakDownOfNode0>=1)))||((i0.i0.u69.Node7HasAskedItsLeafSetToLxToReplaceNode1>=1)&&(u87.LeafSetOfLxIsSentToNode7>=1)))||((i2.i0.u12.Node1HasAskedItsLeafSetToLxToReplaceNode0>=1)&&(u87.LeafSetOfLxIsSentToNode1>=1)))||((i3.u85.Node8HasAskedItsLeafSetToRxToReplaceNode7>=1)&&(i11.u86.LeafSetOfRxIsSentToNode8>=1)))||((i7.i0.u8.Node6DontAnswerToAnyNode>=1)&&(i9.u70.Node7IsActive>=1)))||((i6.i0.u0.Node0IsActive>=1)&&(i5.u50.Node4DontAnswerToAnyNode>=1)))||((i0.i1.u68.NoNodeManageTheBreakDownOfNode0>=1)&&(i0.i1.u22.Node2WantsToManageTheBreakDownOfNode0>=1)))||(i11.u88.Node7HasTheLeafSetOfRxToReplaceNode8>=1))||((i10.u79.Node8HasAskedItsLeafSetToLxToReplaceNode1>=1)&&(u87.LeafSetOfLxIsSentToNode8>=1)))||((i0.i2.u72.Node7HasAskedItsLeafSetToLxToReplaceNode3>=1)&&(u87.LeafSetOfLxIsSentToNode7>=1)))||(i11.u88.Node1HasTheLeafSetOfRxToReplaceNode5>=1))||(u87.Node6HasTheLeafSetOfLxToReplaceNode0>=1))))) + E(((((i11.u88.Node0HasTheLeafSetOfRxToReplaceNode7<1)&&(i2.i0.u13.Node1ManageTheBreakDownOfNode2<1))&&(i0.i0.u23.Node2ManageTheBreakDownOfNode1<1))&&((i7.i1.u40.Node4IsActive<1)||(i6.i1.u10.Node8DontAnswerToAnyNode<1))) U EX((((((i9.u76.Node7WantsToManageTheBreakDownOfNode8>=1)&&(i6.i1.u11.NoNodeManageTheBreakDownOfNode8>=1))||((i3.u29.Node2HasAskedItsLeafSetToRxToReplaceNode7>=1)&&(i11.u88.LeafSetOfRxIsSentToNode2>=1)))||((i7.i0.u17.Node1HasAskedItsLeafSetToRxToReplaceNode6>=1)&&(i11.u88.LeafSetOfRxIsSentToNode1>=1)))||((i4.u63.Node6HasAskedItsLeafSetToLxToReplaceNode3>=1)&&(u87.LeafSetOfLxIsSentToNode6>=1)))))) + ((!(EX(!((((((((((i6.i0.u9.Node0HasAskedItsLeafSetToRxToReplaceNode7>=1)&&(i11.u88.LeafSetOfRxIsSentToNode0>=1))||((i2.i0.u15.Node1HasAskedItsLeafSetToLxToReplaceNode4>=1)&&(u87.LeafSetOfLxIsSentToNode1>=1)))||(u87.Node8HasTheLeafSetOfLxToReplaceNode2>=1))||((i0.i0.u1.BreakDownReservoir>=1)&&(i1.u31.Node3IsActive>=1)))||((i4.u61.Node6HasAskedItsLeafSetToLxToReplaceNode1>=1)&&(u87.LeafSetOfLxIsSentToNode6>=1)))||((i2.i1.u4.NoNodeManageTheBreakDownOfNode2>=1)&&(i2.i1.u43.Node4WantsToManageTheBreakDownOfNode2>=1)))||(u87.Node7HasTheLeafSetOfLxToReplaceNode3>=1))||(i1.u37.Node3ManageTheBreakDownOfNode6>=1))))) + !(EG(!((u87.Node8HasTheLeafSetOfLxToReplaceNode3>=1))))) * (EG((((i3.u48.Node4HasAskedItsLeafSetToRxToReplaceNode7>=1)&&(i11.u46.LeafSetOfRxIsSentToNode4>=1))||((i6.i1.u11.Node0HasAskedItsLeafSetToRxToReplaceNode8>=1)&&(i11.u88.LeafSetOfRxIsSentToNode0>=1)))) + (!((E(!((((((((((i7.i0.u28.Node2WantsToManageTheBreakDownOfNode6>=1)&&(i7.i0.u47.NoNodeManageTheBreakDownOfNode6>=1))||((i5.u82.Node8HasAskedItsLeafSetToRxToReplaceNode4>=1)&&(i11.u86.LeafSetOfRxIsSentToNode8>=1)))||((i0.i1.u41.RequestOfNode4IsSentToLx>=1)&&(u87.LxIsActiveAndNotInTheLeafSet>=1)))||(i0.i2.u44.Node4ManageTheBreakDownOfNode3>=1))||(u87.LxHasReceivedTheRequestOfNode2>=1))||(i0.i2.u25.Node2ManageTheBreakDownOfNode3>=1))||((i7.i2.u21.Node2IsActive>=1)&&(i0.i2.u24.Node3DontAnswerToAnyNode>=1)))||(u87.LxHasReceivedTheRequestOfNode0>=1))) U (!((u87.Node6HasTheLeafSetOfLxToReplaceNode0>=1)) * !((((((((((i7.i0.u28.Node2WantsToManageTheBreakDownOfNode6>=1)&&(i7.i0.u47.NoNodeManageTheBreakDownOfNode6>=1))||((i5.u82.Node8HasAskedItsLeafSetToRxToReplaceNode4>=1)&&(i11.u86.LeafSetOfRxIsSentToNode8>=1)))||((i0.i1.u41.RequestOfNode4IsSentToLx>=1)&&(u87.LxIsActiveAndNotInTheLeafSet>=1)))||(i0.i2.u44.Node4ManageTheBreakDownOfNode3>=1))||(u87.LxHasReceivedTheRequestOfNode2>=1))||(i0.i2.u25.Node2ManageTheBreakDownOfNode3>=1))||((i7.i2.u21.Node2IsActive>=1)&&(i0.i2.u24.Node3DontAnswerToAnyNode>=1)))||(u87.LxHasReceivedTheRequestOfNode0>=1))))) + EG(!((((((((((i7.i0.u28.Node2WantsToManageTheBreakDownOfNode6>=1)&&(i7.i0.u47.NoNodeManageTheBreakDownOfNode6>=1))||((i5.u82.Node8HasAskedItsLeafSetToRxToReplaceNode4>=1)&&(i11.u86.LeafSetOfRxIsSentToNode8>=1)))||((i0.i1.u41.RequestOfNode4IsSentToLx>=1)&&(u87.LxIsActiveAndNotInTheLeafSet>=1)))||(i0.i2.u44.Node4ManageTheBreakDownOfNode3>=1))||(u87.LxHasReceivedTheRequestOfNode2>=1))||(i0.i2.u25.Node2ManageTheBreakDownOfNode3>=1))||((i7.i2.u21.Node2IsActive>=1)&&(i0.i2.u24.Node3DontAnswerToAnyNode>=1)))||(u87.LxHasReceivedTheRequestOfNode0>=1)))))) * E(TRUE U ((((((((i9.u76.Node7WantsToManageTheBreakDownOfNode8>=1)&&(i6.i1.u11.NoNodeManageTheBreakDownOfNode8>=1))||((i4.u62.Node6HasAskedItsLeafSetToLxToReplaceNode2>=1)&&(u87.LeafSetOfLxIsSentToNode6>=1)))||((i5.u55.RequestOfNode5IsSentToRx>=1)&&(i11.u88.RxIsActiveAndNotInTheLeafSet>=1)))||((i0.i0.u23.NoNodeManageTheBreakDownOfNode1>=1)&&(i10.u78.Node8WantsToManageTheBreakDownOfNode1>=1)))||((i5.u50.Node4DontAnswerToAnyNode>=1)&&(i9.u70.Node7IsActive>=1)))||((i3.u18.Node7DontAnswerToAnyNode>=1)&&(i10.u78.Node8IsActive>=1)))||(u87.Node5HasTheLeafSetOfLxToReplaceNode0>=1))))))))) * !(!(!((E(!(((((i5.u55.Node5HasAskedItsLeafSetToRxToReplaceNode4>=1)&&(i11.u88.LeafSetOfRxIsSentToNode5>=1))||((i0.i0.u23.NoNodeManageTheBreakDownOfNode1>=1)&&(i10.u78.Node8WantsToManageTheBreakDownOfNode1>=1)))||((i6.i1.u58.Node5WantsToManageTheBreakDownOfNode8>=1)&&(i6.i1.u11.NoNodeManageTheBreakDownOfNode8>=1)))) U (!((EG((i11.u86.RxHasReceivedTheRequestOfNode8<1)) + !(!((E(!(((((((((((i3.u29.Node2WantsToManageTheBreakDownOfNode7>=1)&&(i3.u48.NoNodeManageTheBreakDownOfNode7>=1))||((i7.i0.u8.Node6DontAnswerToAnyNode>=1)&&(i10.u78.Node8IsActive>=1)))||(i11.u88.Node6HasTheLeafSetOfRxToReplaceNode7>=1))||((i3.u48.NoNodeManageTheBreakDownOfNode7>=1)&&(i3.u85.Node8WantsToManageTheBreakDownOfNode7>=1)))||(i11.u88.Node2HasTheLeafSetOfRxToReplaceNode5>=1))||(i11.u88.Node3HasTheLeafSetOfRxToReplaceNode5>=1))||((i0.i2.u5.NoNodeManageTheBreakDownOfNode3>=1)&&(i8.u54.Node5WantsToManageTheBreakDownOfNode3>=1)))||(i11.u88.RxHasReceivedTheRequestOfNode5>=1))||((i2.i0.u12.Node1IsActive>=1)&&(i7.i2.u59.Node5DontAnswerToAnyNode>=1)))) U (!((((((i5.u6.NoNodeManageTheBreakDownOfNode4>=1)&&(i5.u82.Node8WantsToManageTheBreakDownOfNode4>=1))||((i8.u51.Node5HasAskedItsLeafSetToLxToReplaceNode0>=1)&&(u87.LeafSetOfLxIsSentToNode5>=1)))||((i2.i1.u4.NoNodeManageTheBreakDownOfNode2>=1)&&(i4.u62.Node6WantsToManageTheBreakDownOfNode2>=1)))||(u87.Node7HasTheLeafSetOfLxToReplaceNode3>=1))) * !(((((((((((i3.u29.Node2WantsToManageTheBreakDownOfNode7>=1)&&(i3.u48.NoNodeManageTheBreakDownOfNode7>=1))||((i7.i0.u8.Node6DontAnswerToAnyNode>=1)&&(i10.u78.Node8IsActive>=1)))||(i11.u88.Node6HasTheLeafSetOfRxToReplaceNode7>=1))||((i3.u48.NoNodeManageTheBreakDownOfNode7>=1)&&(i3.u85.Node8WantsToManageTheBreakDownOfNode7>=1)))||(i11.u88.Node2HasTheLeafSetOfRxToReplaceNode5>=1))||(i11.u88.Node3HasTheLeafSetOfRxToReplaceNode5>=1))||((i0.i2.u5.NoNodeManageTheBreakDownOfNode3>=1)&&(i8.u54.Node5WantsToManageTheBreakDownOfNode3>=1)))||(i11.u88.RxHasReceivedTheRequestOfNode5>=1))||((i2.i0.u12.Node1IsActive>=1)&&(i7.i2.u59.Node5DontAnswerToAnyNode>=1)))))) + EG(!(((((((((((i3.u29.Node2WantsToManageTheBreakDownOfNode7>=1)&&(i3.u48.NoNodeManageTheBreakDownOfNode7>=1))||((i7.i0.u8.Node6DontAnswerToAnyNode>=1)&&(i10.u78.Node8IsActive>=1)))||(i11.u88.Node6HasTheLeafSetOfRxToReplaceNode7>=1))||((i3.u48.NoNodeManageTheBreakDownOfNode7>=1)&&(i3.u85.Node8WantsToManageTheBreakDownOfNode7>=1)))||(i11.u88.Node2HasTheLeafSetOfRxToReplaceNode5>=1))||(i11.u88.Node3HasTheLeafSetOfRxToReplaceNode5>=1))||((i0.i2.u5.NoNodeManageTheBreakDownOfNode3>=1)&&(i8.u54.Node5WantsToManageTheBreakDownOfNode3>=1)))||(i11.u88.RxHasReceivedTheRequestOfNode5>=1))||((i2.i0.u12.Node1IsActive>=1)&&(i7.i2.u59.Node5DontAnswerToAnyNode>=1)))))))))) * !(((((i5.u55.Node5HasAskedItsLeafSetToRxToReplaceNode4>=1)&&(i11.u88.LeafSetOfRxIsSentToNode5>=1))||((i0.i0.u23.NoNodeManageTheBreakDownOfNode1>=1)&&(i10.u78.Node8WantsToManageTheBreakDownOfNode1>=1)))||((i6.i1.u58.Node5WantsToManageTheBreakDownOfNode8>=1)&&(i6.i1.u11.NoNodeManageTheBreakDownOfNode8>=1)))))) + EG(!(((((i5.u55.Node5HasAskedItsLeafSetToRxToReplaceNode4>=1)&&(i11.u88.LeafSetOfRxIsSentToNode5>=1))||((i0.i0.u23.NoNodeManageTheBreakDownOfNode1>=1)&&(i10.u78.Node8WantsToManageTheBreakDownOfNode1>=1)))||((i6.i1.u58.Node5WantsToManageTheBreakDownOfNode8>=1)&&(i6.i1.u11.NoNodeManageTheBreakDownOfNode8>=1)))))))))))))] != FALSE
(forward)formula 13,1,319.19,2725852,1,0,2.26695e+06,816419,6034,6.92074e+06,1324,2.59804e+07,10108379
FORMULA LeafsetExtension-PT-S08C2-CTLFireability-14 TRUE TECHNIQUES DECISION_DIAGRAMS TOPOLOGICAL USE_NUPN
Formula is TRUE !
***************************************
original formula: !(EF(EG(AX((AG((((((((((i7.i1.u40.Node4WantsToManageTheBreakDownOfNode6>=1)&&(i7.i0.u47.NoNodeManageTheBreakDownOfNode6>=1))||((i7.i0.u47.NoNodeManageTheBreakDownOfNode6>=1)&&(i9.u75.Node7WantsToManageTheBreakDownOfNode6>=1)))||((i0.i2.u44.Node4HasAskedItsLeafSetToLxToReplaceNode3>=1)&&(u87.LeafSetOfLxIsSentToNode4>=1)))||(u87.Node0HasTheLeafSetOfLxToReplaceNode1>=1))||((i2.i0.u12.Node1IsActive>=1)&&(i2.i1.u3.Node2DontAnswerToAnyNode>=1)))||(u87.Node3HasTheLeafSetOfLxToReplaceNode1>=1))||((i5.u26.Node2WantsToManageTheBreakDownOfNode4>=1)&&(i5.u6.NoNodeManageTheBreakDownOfNode4>=1)))||(i11.u88.RxHasReceivedTheRequestOfNode7>=1))) * A((((i5.u35.Node3ManageTheBreakDownOfNode4>=1)||((i0.i0.u2.Node0HasAskedItsLeafSetToLxToReplaceNode1>=1)&&(u87.LeafSetOfLxIsSentToNode0>=1)))||(i5.u64.Node6ManageTheBreakDownOfNode4>=1)) U ((((((((((i7.i1.u49.Node4HasAskedItsLeafSetToRxToReplaceNode8>=1)&&(i11.u46.LeafSetOfRxIsSentToNode4>=1))||(i11.u88.Node7HasTheLeafSetOfRxToReplaceNode6>=1))||(i8.u51.Node5ManageTheBreakDownOfNode0>=1))||(i4.u60.Node6ManageTheBreakDownOfNode0>=1))||(u87.Node5HasTheLeafSetOfLxToReplaceNode3>=1))||(i6.i1.u11.Node0ManageTheBreakDownOfNode8>=1))||(i11.u88.Node3HasTheLeafSetOfRxToReplaceNode7>=1))||((i4.u61.Node6IsActive>=1)&&(i6.i1.u10.Node8DontAnswerToAnyNode>=1)))||((i0.i2.u24.Node3DontAnswerToAnyNode>=1)&&(i7.i1.u40.Node4IsActive>=1)))))))))
=> equivalent forward existential formula: [FwdG(FwdU(Init,TRUE),!(EX(!((!(E(TRUE U !((((((((((i7.i1.u40.Node4WantsToManageTheBreakDownOfNode6>=1)&&(i7.i0.u47.NoNodeManageTheBreakDownOfNode6>=1))||((i7.i0.u47.NoNodeManageTheBreakDownOfNode6>=1)&&(i9.u75.Node7WantsToManageTheBreakDownOfNode6>=1)))||((i0.i2.u44.Node4HasAskedItsLeafSetToLxToReplaceNode3>=1)&&(u87.LeafSetOfLxIsSentToNode4>=1)))||(u87.Node0HasTheLeafSetOfLxToReplaceNode1>=1))||((i2.i0.u12.Node1IsActive>=1)&&(i2.i1.u3.Node2DontAnswerToAnyNode>=1)))||(u87.Node3HasTheLeafSetOfLxToReplaceNode1>=1))||((i5.u26.Node2WantsToManageTheBreakDownOfNode4>=1)&&(i5.u6.NoNodeManageTheBreakDownOfNode4>=1)))||(i11.u88.RxHasReceivedTheRequestOfNode7>=1))))) * !((E(!(((((((((((i7.i1.u49.Node4HasAskedItsLeafSetToRxToReplaceNode8>=1)&&(i11.u46.LeafSetOfRxIsSentToNode4>=1))||(i11.u88.Node7HasTheLeafSetOfRxToReplaceNode6>=1))||(i8.u51.Node5ManageTheBreakDownOfNode0>=1))||(i4.u60.Node6ManageTheBreakDownOfNode0>=1))||(u87.Node5HasTheLeafSetOfLxToReplaceNode3>=1))||(i6.i1.u11.Node0ManageTheBreakDownOfNode8>=1))||(i11.u88.Node3HasTheLeafSetOfRxToReplaceNode7>=1))||((i4.u61.Node6IsActive>=1)&&(i6.i1.u10.Node8DontAnswerToAnyNode>=1)))||((i0.i2.u24.Node3DontAnswerToAnyNode>=1)&&(i7.i1.u40.Node4IsActive>=1)))) U (!((((i5.u35.Node3ManageTheBreakDownOfNode4>=1)||((i0.i0.u2.Node0HasAskedItsLeafSetToLxToReplaceNode1>=1)&&(u87.LeafSetOfLxIsSentToNode0>=1)))||(i5.u64.Node6ManageTheBreakDownOfNode4>=1))) * !(((((((((((i7.i1.u49.Node4HasAskedItsLeafSetToRxToReplaceNode8>=1)&&(i11.u46.LeafSetOfRxIsSentToNode4>=1))||(i11.u88.Node7HasTheLeafSetOfRxToReplaceNode6>=1))||(i8.u51.Node5ManageTheBreakDownOfNode0>=1))||(i4.u60.Node6ManageTheBreakDownOfNode0>=1))||(u87.Node5HasTheLeafSetOfLxToReplaceNode3>=1))||(i6.i1.u11.Node0ManageTheBreakDownOfNode8>=1))||(i11.u88.Node3HasTheLeafSetOfRxToReplaceNode7>=1))||((i4.u61.Node6IsActive>=1)&&(i6.i1.u10.Node8DontAnswerToAnyNode>=1)))||((i0.i2.u24.Node3DontAnswerToAnyNode>=1)&&(i7.i1.u40.Node4IsActive>=1)))))) + EG(!(((((((((((i7.i1.u49.Node4HasAskedItsLeafSetToRxToReplaceNode8>=1)&&(i11.u46.LeafSetOfRxIsSentToNode4>=1))||(i11.u88.Node7HasTheLeafSetOfRxToReplaceNode6>=1))||(i8.u51.Node5ManageTheBreakDownOfNode0>=1))||(i4.u60.Node6ManageTheBreakDownOfNode0>=1))||(u87.Node5HasTheLeafSetOfLxToReplaceNode3>=1))||(i6.i1.u11.Node0ManageTheBreakDownOfNode8>=1))||(i11.u88.Node3HasTheLeafSetOfRxToReplaceNode7>=1))||((i4.u61.Node6IsActive>=1)&&(i6.i1.u10.Node8DontAnswerToAnyNode>=1)))||((i0.i2.u24.Node3DontAnswerToAnyNode>=1)&&(i7.i1.u40.Node4IsActive>=1))))))))))))] = FALSE
(forward)formula 14,0,352.571,2884516,1,0,2.42454e+06,849129,4238,7.26213e+06,1283,2.59804e+07,1065463
FORMULA LeafsetExtension-PT-S08C2-CTLFireability-15 FALSE TECHNIQUES DECISION_DIAGRAMS TOPOLOGICAL USE_NUPN
Formula is FALSE !
***************************************
BK_STOP 1621299512730
--------------------
content from stderr:
+ export BINDIR=/home/mcc/BenchKit/bin//../
+ BINDIR=/home/mcc/BenchKit/bin//../
++ pwd
+ export MODEL=/home/mcc/execution
+ MODEL=/home/mcc/execution
+ [[ CTLFireability = StateSpace ]]
+ /home/mcc/BenchKit/bin//..//runeclipse.sh /home/mcc/execution CTLFireability -its -ltsmin -greatspnpath /home/mcc/BenchKit/bin//..//greatspn/ -order META -manyOrder -smt -timeout 3600
+ ulimit -s 65536
+ [[ -z '' ]]
+ export LTSMIN_MEM_SIZE=8589934592
+ LTSMIN_MEM_SIZE=8589934592
++ cut -d . -f 9
++ ls /home/mcc/BenchKit/bin//..//itstools/plugins/fr.lip6.move.gal.application.pnmcc_1.0.0.202104292328.jar
+ VERSION=0
+ echo 'Running Version 0'
+ /home/mcc/BenchKit/bin//..//itstools/its-tools -data /home/mcc/execution/workspace -pnfolder /home/mcc/execution -examination CTLFireability -spotpath /home/mcc/BenchKit/bin//..//ltlfilt -z3path /home/mcc/BenchKit/bin//..//z3/bin/z3 -yices2path /home/mcc/BenchKit/bin//..//yices/bin/yices -its -ltsmin -greatspnpath /home/mcc/BenchKit/bin//..//greatspn/ -order META -manyOrder -smt -timeout 3600 -vmargs -Dosgi.locking=none -Declipse.stateSaveDelayInterval=-1 -Dosgi.configuration.area=/tmp/.eclipse -Xss128m -Xms40m -Xmx16000m
Sequence of Actions to be Executed by the VM
This is useful if one wants to reexecute the tool in the VM from the submitted image disk.
set -x
# this is for BenchKit: configuration of major elements for the test
export BK_INPUT="LeafsetExtension-PT-S08C2"
export BK_EXAMINATION="CTLFireability"
export BK_TOOL="itstools"
export BK_RESULT_DIR="/tmp/BK_RESULTS/OUTPUTS"
export BK_TIME_CONFINEMENT="3600"
export BK_MEMORY_CONFINEMENT="16384"
export BK_BIN_PATH="/home/mcc/BenchKit/bin/"
# this is specific to your benchmark or test
export BIN_DIR="$HOME/BenchKit/bin"
# remove the execution directoty if it exists (to avoid increse of .vmdk images)
if [ -d execution ] ; then
rm -rf execution
fi
# this is for BenchKit: explicit launching of the test
echo "====================================================================="
echo " Generated by BenchKit 2-4028"
echo " Executing tool itstools"
echo " Input is LeafsetExtension-PT-S08C2, examination is CTLFireability"
echo " Time confinement is $BK_TIME_CONFINEMENT seconds"
echo " Memory confinement is 16384 MBytes"
echo " Number of cores is 4"
echo " Run identifier is r292-tall-162124156500474"
echo "====================================================================="
echo
echo "--------------------"
echo "preparation of the directory to be used:"
tar xzf /home/mcc/BenchKit/INPUTS/LeafsetExtension-PT-S08C2.tgz
mv LeafsetExtension-PT-S08C2 execution
cd execution
if [ "CTLFireability" = "ReachabilityDeadlock" ] || [ "CTLFireability" = "UpperBounds" ] || [ "CTLFireability" = "QuasiLiveness" ] || [ "CTLFireability" = "StableMarking" ] || [ "CTLFireability" = "Liveness" ] || [ "CTLFireability" = "OneSafe" ] || [ "CTLFireability" = "StateSpace" ]; then
rm -f GenericPropertiesVerdict.xml
fi
pwd
ls -lh
echo
echo "--------------------"
echo "content from stdout:"
echo
echo "=== Data for post analysis generated by BenchKit (invocation template)"
echo
if [ "CTLFireability" = "UpperBounds" ] ; then
echo "The expected result is a vector of positive values"
echo NUM_VECTOR
elif [ "CTLFireability" != "StateSpace" ] ; then
echo "The expected result is a vector of booleans"
echo BOOL_VECTOR
else
echo "no data necessary for post analysis"
fi
echo
if [ -f "CTLFireability.txt" ] ; then
echo "here is the order used to build the result vector(from text file)"
for x in $(grep Property CTLFireability.txt | cut -d ' ' -f 2 | sort -u) ; do
echo "FORMULA_NAME $x"
done
elif [ -f "CTLFireability.xml" ] ; then # for cunf (txt files deleted;-)
echo echo "here is the order used to build the result vector(from xml file)"
for x in $(grep '
echo "FORMULA_NAME $x"
done
elif [ "CTLFireability" = "ReachabilityDeadlock" ] || [ "CTLFireability" = "QuasiLiveness" ] || [ "CTLFireability" = "StableMarking" ] || [ "CTLFireability" = "Liveness" ] || [ "CTLFireability" = "OneSafe" ] ; then
echo "FORMULA_NAME CTLFireability"
fi
echo
echo "=== Now, execution of the tool begins"
echo
echo -n "BK_START "
date -u +%s%3N
echo
timeout -s 9 $BK_TIME_CONFINEMENT bash -c "/home/mcc/BenchKit/BenchKit_head.sh 2> STDERR ; echo ; echo -n \"BK_STOP \" ; date -u +%s%3N"
if [ $? -eq 137 ] ; then
echo
echo "BK_TIME_CONFINEMENT_REACHED"
fi
echo
echo "--------------------"
echo "content from stderr:"
echo
cat STDERR ;

