About the Execution of ITS-Tools for QuasiCertifProtocol-PT-06
| Execution Summary | |||||
| Max Memory Used (MB) |
Time wait (ms) | CPU Usage (ms) | I/O Wait (ms) | Computed Result | Execution Status |
| 15741.640 | 838250.00 | 856487.00 | 1327.00 | TFFTFFFTTFTTFFTT | normal |
Execution Chart
We display below the execution chart for this examination (boot time has been removed).
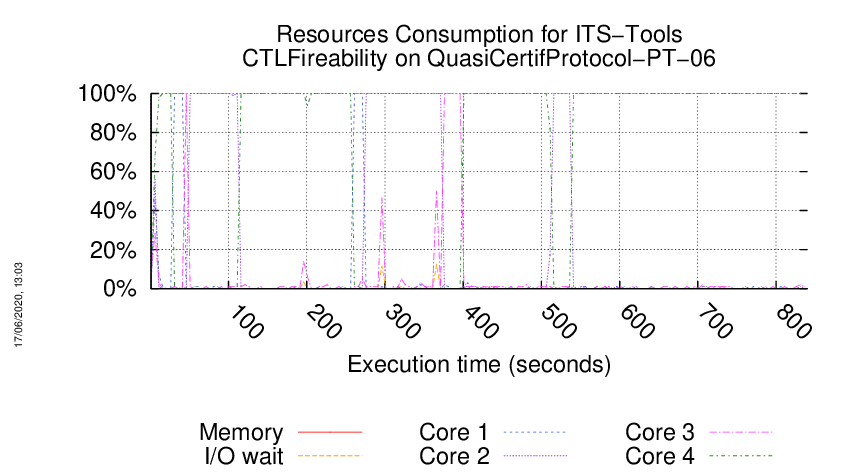
Trace from the execution
Formatting '/mnt/tpsp/fkordon/mcc2020-input.r126-tajo-158961390900788.qcow2', fmt=qcow2 size=4294967296 backing_file='/mnt/tpsp/fkordon/mcc2020-input.qcow2' encryption=off cluster_size=65536 lazy_refcounts=off
Waiting for the VM to be ready (probing ssh)
.........................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................
=====================================================================
Generated by BenchKit 2-4028
Executing tool itstools
Input is QuasiCertifProtocol-PT-06, examination is CTLFireability
Time confinement is 3600 seconds
Memory confinement is 16384 MBytes
Number of cores is 4
Run identifier is r126-tajo-158961390900788
=====================================================================
--------------------
preparation of the directory to be used:
/home/mcc/execution
total 372K
-rw-r--r-- 1 mcc users 5.8K Apr 12 06:55 CTLCardinality.txt
-rw-r--r-- 1 mcc users 27K Apr 12 06:55 CTLCardinality.xml
-rw-r--r-- 1 mcc users 3.2K Apr 11 07:55 CTLFireability.txt
-rw-r--r-- 1 mcc users 16K Apr 11 07:55 CTLFireability.xml
-rw-r--r-- 1 mcc users 4.0K Mar 24 05:37 GenericPropertiesDefinition.xml
-rw-r--r-- 1 mcc users 6.4K Mar 24 05:37 GenericPropertiesVerdict.xml
-rw-r--r-- 1 mcc users 5.8K Apr 14 12:47 LTLCardinality.txt
-rw-r--r-- 1 mcc users 33K Apr 28 14:02 LTLCardinality.xml
-rw-r--r-- 1 mcc users 3.1K Apr 14 12:47 LTLFireability.txt
-rw-r--r-- 1 mcc users 19K Apr 28 14:02 LTLFireability.xml
-rw-r--r-- 1 mcc users 6.0K Apr 10 13:51 ReachabilityCardinality.txt
-rw-r--r-- 1 mcc users 26K Apr 10 13:51 ReachabilityCardinality.xml
-rw-r--r-- 1 mcc users 3.5K Apr 9 20:24 ReachabilityFireability.txt
-rw-r--r-- 1 mcc users 15K Apr 9 20:24 ReachabilityFireability.xml
-rw-r--r-- 1 mcc users 2.6K Apr 10 22:24 UpperBounds.txt
-rw-r--r-- 1 mcc users 6.3K Apr 10 22:24 UpperBounds.xml
-rw-r--r-- 1 mcc users 5 Mar 24 05:37 equiv_col
-rw-r--r-- 1 mcc users 3 Mar 24 05:37 instance
-rw-r--r-- 1 mcc users 6 Mar 24 05:37 iscolored
-rw-r--r-- 1 mcc users 153K Mar 24 05:37 model.pnml
--------------------
content from stdout:
=== Data for post analysis generated by BenchKit (invocation template)
The expected result is a vector of booleans
BOOL_VECTOR
here is the order used to build the result vector(from text file)
FORMULA_NAME QuasiCertifProtocol-PT-06-CTLFireability-00
FORMULA_NAME QuasiCertifProtocol-PT-06-CTLFireability-01
FORMULA_NAME QuasiCertifProtocol-PT-06-CTLFireability-02
FORMULA_NAME QuasiCertifProtocol-PT-06-CTLFireability-03
FORMULA_NAME QuasiCertifProtocol-PT-06-CTLFireability-04
FORMULA_NAME QuasiCertifProtocol-PT-06-CTLFireability-05
FORMULA_NAME QuasiCertifProtocol-PT-06-CTLFireability-06
FORMULA_NAME QuasiCertifProtocol-PT-06-CTLFireability-07
FORMULA_NAME QuasiCertifProtocol-PT-06-CTLFireability-08
FORMULA_NAME QuasiCertifProtocol-PT-06-CTLFireability-09
FORMULA_NAME QuasiCertifProtocol-PT-06-CTLFireability-10
FORMULA_NAME QuasiCertifProtocol-PT-06-CTLFireability-11
FORMULA_NAME QuasiCertifProtocol-PT-06-CTLFireability-12
FORMULA_NAME QuasiCertifProtocol-PT-06-CTLFireability-13
FORMULA_NAME QuasiCertifProtocol-PT-06-CTLFireability-14
FORMULA_NAME QuasiCertifProtocol-PT-06-CTLFireability-15
=== Now, execution of the tool begins
BK_START 1589858024075
[2020-05-19 03:13:45] [INFO ] Running its-tools with arguments : [-pnfolder, /home/mcc/execution, -examination, CTLFireability, -z3path, /home/mcc/BenchKit//z3/bin/z3, -yices2path, /home/mcc/BenchKit//yices/bin/yices, -its, -ltsminpath, /home/mcc/BenchKit//lts_install_dir/, -greatspnpath, /home/mcc/BenchKit//greatspn/, -order, META, -manyOrder, -smt, -timeout, 3600]
[2020-05-19 03:13:45] [INFO ] Parsing pnml file : /home/mcc/execution/model.pnml
[2020-05-19 03:13:45] [INFO ] Load time of PNML (sax parser for PT used): 51 ms
[2020-05-19 03:13:45] [INFO ] Transformed 270 places.
[2020-05-19 03:13:45] [INFO ] Transformed 116 transitions.
[2020-05-19 03:13:45] [INFO ] Parsed PT model containing 270 places and 116 transitions in 86 ms.
Parsed 16 properties from file /home/mcc/execution/CTLFireability.xml in 16 ms.
Incomplete random walk after 100000 steps, including 9831 resets, run finished after 372 ms. (steps per millisecond=268 ) properties seen :[1, 0, 0, 0, 0, 0, 1, 0, 1, 0, 1, 1, 1, 1, 1, 1, 1, 1, 0, 0, 1, 0, 0, 0, 0, 0, 0, 0, 1, 1, 0, 0, 1, 0]
// Phase 1: matrix 116 rows 270 cols
[2020-05-19 03:13:46] [INFO ] Computed 155 place invariants in 12 ms
[2020-05-19 03:13:46] [INFO ] [Real]Absence check using 3 positive place invariants in 20 ms returned sat
[2020-05-19 03:13:46] [INFO ] [Real]Absence check using 3 positive and 152 generalized place invariants in 54 ms returned sat
[2020-05-19 03:13:46] [INFO ] [Real]Adding state equation constraints to refine reachable states.
[2020-05-19 03:13:46] [INFO ] [Real]Absence check using state equation in 200 ms returned sat
[2020-05-19 03:13:46] [INFO ] Computed and/alt/rep : 108/283/108 causal constraints in 11 ms.
[2020-05-19 03:13:46] [INFO ] Added : 18 causal constraints over 4 iterations in 79 ms. Result :sat
[2020-05-19 03:13:46] [INFO ] [Real]Absence check using 3 positive place invariants in 10 ms returned sat
[2020-05-19 03:13:46] [INFO ] [Real]Absence check using 3 positive and 152 generalized place invariants in 44 ms returned sat
[2020-05-19 03:13:46] [INFO ] [Real]Adding state equation constraints to refine reachable states.
[2020-05-19 03:13:47] [INFO ] [Real]Absence check using state equation in 170 ms returned unsat
[2020-05-19 03:13:47] [INFO ] [Real]Absence check using 3 positive place invariants in 4 ms returned sat
[2020-05-19 03:13:47] [INFO ] [Real]Absence check using 3 positive and 152 generalized place invariants in 43 ms returned sat
[2020-05-19 03:13:47] [INFO ] [Real]Adding state equation constraints to refine reachable states.
[2020-05-19 03:13:47] [INFO ] [Real]Absence check using state equation in 155 ms returned sat
[2020-05-19 03:13:47] [INFO ] Computed and/alt/rep : 108/283/108 causal constraints in 9 ms.
[2020-05-19 03:13:47] [INFO ] Added : 21 causal constraints over 5 iterations in 66 ms. Result :sat
[2020-05-19 03:13:47] [INFO ] [Real]Absence check using 3 positive place invariants in 5 ms returned sat
[2020-05-19 03:13:47] [INFO ] [Real]Absence check using 3 positive and 152 generalized place invariants in 43 ms returned sat
[2020-05-19 03:13:47] [INFO ] [Real]Adding state equation constraints to refine reachable states.
[2020-05-19 03:13:47] [INFO ] [Real]Absence check using state equation in 158 ms returned sat
[2020-05-19 03:13:47] [INFO ] Computed and/alt/rep : 108/283/108 causal constraints in 9 ms.
[2020-05-19 03:13:47] [INFO ] Added : 43 causal constraints over 9 iterations in 94 ms. Result :sat
[2020-05-19 03:13:47] [INFO ] [Real]Absence check using 3 positive place invariants in 4 ms returned sat
[2020-05-19 03:13:47] [INFO ] [Real]Absence check using 3 positive and 152 generalized place invariants in 66 ms returned sat
[2020-05-19 03:13:47] [INFO ] [Real]Adding state equation constraints to refine reachable states.
[2020-05-19 03:13:48] [INFO ] [Real]Absence check using state equation in 199 ms returned sat
[2020-05-19 03:13:48] [INFO ] Computed and/alt/rep : 108/283/108 causal constraints in 8 ms.
[2020-05-19 03:13:48] [INFO ] Added : 25 causal constraints over 5 iterations in 65 ms. Result :sat
[2020-05-19 03:13:48] [INFO ] [Real]Absence check using 3 positive place invariants in 5 ms returned sat
[2020-05-19 03:13:48] [INFO ] [Real]Absence check using 3 positive and 152 generalized place invariants in 49 ms returned sat
[2020-05-19 03:13:48] [INFO ] [Real]Adding state equation constraints to refine reachable states.
[2020-05-19 03:13:48] [INFO ] [Real]Absence check using state equation in 197 ms returned sat
[2020-05-19 03:13:48] [INFO ] Computed and/alt/rep : 108/283/108 causal constraints in 6 ms.
[2020-05-19 03:13:48] [INFO ] Added : 25 causal constraints over 5 iterations in 58 ms. Result :sat
[2020-05-19 03:13:48] [INFO ] [Real]Absence check using 3 positive place invariants in 4 ms returned sat
[2020-05-19 03:13:48] [INFO ] [Real]Absence check using 3 positive and 152 generalized place invariants in 42 ms returned sat
[2020-05-19 03:13:48] [INFO ] [Real]Adding state equation constraints to refine reachable states.
[2020-05-19 03:13:48] [INFO ] [Real]Absence check using state equation in 170 ms returned sat
[2020-05-19 03:13:48] [INFO ] Computed and/alt/rep : 108/283/108 causal constraints in 6 ms.
[2020-05-19 03:13:48] [INFO ] Added : 21 causal constraints over 5 iterations in 62 ms. Result :sat
[2020-05-19 03:13:48] [INFO ] [Real]Absence check using 3 positive place invariants in 4 ms returned sat
[2020-05-19 03:13:48] [INFO ] [Real]Absence check using 3 positive and 152 generalized place invariants in 43 ms returned sat
[2020-05-19 03:13:48] [INFO ] [Real]Adding state equation constraints to refine reachable states.
[2020-05-19 03:13:49] [INFO ] [Real]Absence check using state equation in 169 ms returned sat
[2020-05-19 03:13:49] [INFO ] Computed and/alt/rep : 108/283/108 causal constraints in 6 ms.
[2020-05-19 03:13:49] [INFO ] Added : 50 causal constraints over 10 iterations in 100 ms. Result :sat
[2020-05-19 03:13:49] [INFO ] [Real]Absence check using 3 positive place invariants in 8 ms returned sat
[2020-05-19 03:13:49] [INFO ] [Real]Absence check using 3 positive and 152 generalized place invariants in 66 ms returned sat
[2020-05-19 03:13:49] [INFO ] [Real]Adding state equation constraints to refine reachable states.
[2020-05-19 03:13:49] [INFO ] [Real]Absence check using state equation in 199 ms returned sat
[2020-05-19 03:13:49] [INFO ] Computed and/alt/rep : 108/283/108 causal constraints in 9 ms.
[2020-05-19 03:13:49] [INFO ] Added : 27 causal constraints over 6 iterations in 84 ms. Result :sat
[2020-05-19 03:13:49] [INFO ] [Real]Absence check using 3 positive place invariants in 4 ms returned sat
[2020-05-19 03:13:49] [INFO ] [Real]Absence check using 3 positive and 152 generalized place invariants in 38 ms returned sat
[2020-05-19 03:13:49] [INFO ] [Real]Adding state equation constraints to refine reachable states.
[2020-05-19 03:13:49] [INFO ] [Real]Absence check using state equation in 147 ms returned sat
[2020-05-19 03:13:49] [INFO ] Computed and/alt/rep : 108/283/108 causal constraints in 5 ms.
[2020-05-19 03:13:49] [INFO ] Added : 17 causal constraints over 4 iterations in 48 ms. Result :sat
[2020-05-19 03:13:49] [INFO ] [Real]Absence check using 3 positive place invariants in 8 ms returned sat
[2020-05-19 03:13:50] [INFO ] [Real]Absence check using 3 positive and 152 generalized place invariants in 69 ms returned sat
[2020-05-19 03:13:50] [INFO ] [Real]Adding state equation constraints to refine reachable states.
[2020-05-19 03:13:50] [INFO ] [Real]Absence check using state equation in 158 ms returned sat
[2020-05-19 03:13:50] [INFO ] Computed and/alt/rep : 108/283/108 causal constraints in 7 ms.
[2020-05-19 03:13:50] [INFO ] Added : 20 causal constraints over 4 iterations in 114 ms. Result :sat
[2020-05-19 03:13:50] [INFO ] [Real]Absence check using 3 positive place invariants in 4 ms returned sat
[2020-05-19 03:13:50] [INFO ] [Real]Absence check using 3 positive and 152 generalized place invariants in 39 ms returned sat
[2020-05-19 03:13:50] [INFO ] [Real]Adding state equation constraints to refine reachable states.
[2020-05-19 03:13:50] [INFO ] [Real]Absence check using state equation in 144 ms returned sat
[2020-05-19 03:13:50] [INFO ] Computed and/alt/rep : 108/283/108 causal constraints in 6 ms.
[2020-05-19 03:13:50] [INFO ] Added : 47 causal constraints over 10 iterations in 133 ms. Result :sat
[2020-05-19 03:13:50] [INFO ] [Real]Absence check using 3 positive place invariants in 4 ms returned sat
[2020-05-19 03:13:50] [INFO ] [Real]Absence check using 3 positive and 152 generalized place invariants in 37 ms returned sat
[2020-05-19 03:13:50] [INFO ] [Real]Adding state equation constraints to refine reachable states.
[2020-05-19 03:13:50] [INFO ] [Real]Absence check using state equation in 141 ms returned sat
[2020-05-19 03:13:50] [INFO ] Computed and/alt/rep : 108/283/108 causal constraints in 6 ms.
[2020-05-19 03:13:51] [INFO ] Added : 49 causal constraints over 10 iterations in 117 ms. Result :sat
[2020-05-19 03:13:51] [INFO ] [Real]Absence check using 3 positive place invariants in 4 ms returned sat
[2020-05-19 03:13:51] [INFO ] [Real]Absence check using 3 positive and 152 generalized place invariants in 34 ms returned sat
[2020-05-19 03:13:51] [INFO ] [Real]Adding state equation constraints to refine reachable states.
[2020-05-19 03:13:51] [INFO ] [Real]Absence check using state equation in 140 ms returned sat
[2020-05-19 03:13:51] [INFO ] Computed and/alt/rep : 108/283/108 causal constraints in 19 ms.
[2020-05-19 03:13:51] [INFO ] Added : 26 causal constraints over 6 iterations in 66 ms. Result :sat
[2020-05-19 03:13:51] [INFO ] [Real]Absence check using 3 positive place invariants in 3 ms returned sat
[2020-05-19 03:13:51] [INFO ] [Real]Absence check using 3 positive and 152 generalized place invariants in 35 ms returned sat
[2020-05-19 03:13:51] [INFO ] [Real]Adding state equation constraints to refine reachable states.
[2020-05-19 03:13:51] [INFO ] [Real]Absence check using state equation in 140 ms returned sat
[2020-05-19 03:13:51] [INFO ] Computed and/alt/rep : 108/283/108 causal constraints in 8 ms.
[2020-05-19 03:13:51] [INFO ] Added : 49 causal constraints over 10 iterations in 90 ms. Result :sat
[2020-05-19 03:13:51] [INFO ] [Real]Absence check using 3 positive place invariants in 3 ms returned sat
[2020-05-19 03:13:51] [INFO ] [Real]Absence check using 3 positive and 152 generalized place invariants in 35 ms returned sat
[2020-05-19 03:13:51] [INFO ] [Real]Adding state equation constraints to refine reachable states.
[2020-05-19 03:13:51] [INFO ] [Real]Absence check using state equation in 140 ms returned sat
[2020-05-19 03:13:51] [INFO ] Computed and/alt/rep : 108/283/108 causal constraints in 6 ms.
[2020-05-19 03:13:51] [INFO ] Added : 12 causal constraints over 3 iterations in 46 ms. Result :sat
[2020-05-19 03:13:51] [INFO ] [Real]Absence check using 3 positive place invariants in 4 ms returned sat
[2020-05-19 03:13:52] [INFO ] [Real]Absence check using 3 positive and 152 generalized place invariants in 38 ms returned sat
[2020-05-19 03:13:52] [INFO ] [Real]Adding state equation constraints to refine reachable states.
[2020-05-19 03:13:52] [INFO ] [Real]Absence check using state equation in 149 ms returned sat
[2020-05-19 03:13:52] [INFO ] Computed and/alt/rep : 108/283/108 causal constraints in 7 ms.
[2020-05-19 03:13:52] [INFO ] Added : 27 causal constraints over 6 iterations in 59 ms. Result :sat
[2020-05-19 03:13:52] [INFO ] [Real]Absence check using 3 positive place invariants in 3 ms returned sat
[2020-05-19 03:13:52] [INFO ] [Real]Absence check using 3 positive and 152 generalized place invariants in 31 ms returned unsat
[2020-05-19 03:13:52] [INFO ] [Real]Absence check using 3 positive place invariants in 6 ms returned sat
[2020-05-19 03:13:52] [INFO ] [Real]Absence check using 3 positive and 152 generalized place invariants in 35 ms returned sat
[2020-05-19 03:13:52] [INFO ] [Real]Adding state equation constraints to refine reachable states.
[2020-05-19 03:13:52] [INFO ] [Real]Absence check using state equation in 123 ms returned unsat
Successfully simplified 3 atomic propositions for a total of 3 simplifications.
[2020-05-19 03:13:52] [INFO ] Flatten gal took : 44 ms
[2020-05-19 03:13:52] [INFO ] Flatten gal took : 15 ms
[2020-05-19 03:13:52] [INFO ] Applying decomposition
[2020-05-19 03:13:52] [INFO ] Flatten gal took : 14 ms
Converted graph to binary with : CommandLine [args=[/home/mcc/BenchKit/itstools/plugins/fr.lip6.move.gal.louvain.binaries_1.0.0.202005100927/bin/convert-linux64, -i, /tmp/graph7335545750046744977.txt, -o, /tmp/graph7335545750046744977.bin, -w, /tmp/graph7335545750046744977.weights], workingDir=null]
Built communities with : CommandLine [args=[/home/mcc/BenchKit/itstools/plugins/fr.lip6.move.gal.louvain.binaries_1.0.0.202005100927/bin/louvain-linux64, /tmp/graph7335545750046744977.bin, -l, -1, -v, -w, /tmp/graph7335545750046744977.weights, -q, 0, -e, 0.001], workingDir=null]
[2020-05-19 03:13:52] [INFO ] Decomposing Gal with order
[2020-05-19 03:13:52] [INFO ] Rewriting arrays to variables to allow decomposition.
[2020-05-19 03:13:52] [INFO ] Removed a total of 50 redundant transitions.
[2020-05-19 03:13:52] [INFO ] Flatten gal took : 57 ms
[2020-05-19 03:13:52] [INFO ] Fuse similar labels procedure discarded/fused a total of 50 labels/synchronizations in 20 ms.
[2020-05-19 03:13:52] [INFO ] Time to serialize gal into /home/mcc/execution/CTLFireability.pnml.gal : 7 ms
[2020-05-19 03:13:52] [INFO ] Time to serialize properties into /home/mcc/execution/CTLFireability.ctl : 2 ms
Invoking ITS tools like this :CommandLine [args=[/home/mcc/BenchKit/itstools/plugins/fr.lip6.move.gal.itstools.binaries_1.0.0.202005100927/bin/its-ctl-linux64, --gc-threshold, 2000000, --quiet, -i, /home/mcc/execution/CTLFireability.pnml.gal, -t, CGAL, -ctl, /home/mcc/execution/CTLFireability.ctl], workingDir=/home/mcc/execution]
its-ctl command run as :
/home/mcc/BenchKit/itstools/plugins/fr.lip6.move.gal.itstools.binaries_1.0.0.202005100927/bin/its-ctl-linux64 --gc-threshold 2000000 --quiet -i /home/mcc/execution/CTLFireability.pnml.gal -t CGAL -ctl /home/mcc/execution/CTLFireability.ctl
No direction supplied, using forward translation only.
Parsed 16 CTL formulae.
built 13 ordering constraints for composite.
built 71 ordering constraints for composite.
built 18 ordering constraints for composite.
built 18 ordering constraints for composite.
built 18 ordering constraints for composite.
built 18 ordering constraints for composite.
built 18 ordering constraints for composite.
built 18 ordering constraints for composite.
built 18 ordering constraints for composite.
built 17 ordering constraints for composite.
built 13 ordering constraints for composite.
built 7 ordering constraints for composite.
built 17 ordering constraints for composite.
built 13 ordering constraints for composite.
built 7 ordering constraints for composite.
built 19 ordering constraints for composite.
built 17 ordering constraints for composite.
built 7 ordering constraints for composite.
built 13 ordering constraints for composite.
built 17 ordering constraints for composite.
built 7 ordering constraints for composite.
built 13 ordering constraints for composite.
built 28 ordering constraints for composite.
built 15 ordering constraints for composite.
Model ,|S| ,Time ,Mem(kb) ,fin. SDD ,fin. DDD ,peak SDD ,peak DDD ,SDD Hom ,SDD cache peak ,DDD Hom ,DDD cachepeak ,SHom cache
reachable,2.27196e+06,76.2919,886120,29169,5252,784638,168641,633,5.04485e+06,108,5.72153e+06,0
Converting to forward existential form...Done !
original formula: !(AF((i8.u12.a2>=1)))
=> equivalent forward existential formula: [FwdG(Init,!((i8.u12.a2>=1)))] != FALSE
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
Using saturation style SCC detection
(forward)formula 0,1,192.857,1364020,1,0,1.57966e+06,180120,2400,6.75559e+06,726,6.94133e+06,2016728
FORMULA QuasiCertifProtocol-PT-06-CTLFireability-00 TRUE TECHNIQUES DECISION_DIAGRAMS TOPOLOGICAL USE_NUPN
Formula is TRUE !
***************************************
original formula: (EG(AF((i8.u12.a4>=1))) * AX((((((((((((((((i9.u39.s4_6<1)&&(i5.u7.s4_0<1))&&(i6.i1.u8.s4_2<1))&&(i3.i0.u9.s4_1<1))&&(i8.u30.s4_4<1))&&(i4.i0.u10.s4_3<1))&&(i7.i1.u11.s4_5<1))||((u5.malicious_reservoir>=1)&&(u5.s5_5>=1)))||((u5.malicious_reservoir>=1)&&(u5.s5_2>=1)))||((u5.malicious_reservoir>=1)&&(u5.s5_4>=1)))||((u5.malicious_reservoir>=1)&&(u5.s5_1>=1)))||((u5.malicious_reservoir>=1)&&(u5.s5_3>=1)))||((u5.malicious_reservoir>=1)&&(u5.s5_0>=1)))||((u5.malicious_reservoir>=1)&&(u5.s5_6>=1)))||((((((((i8.u12.a5>=1)&&(i3.i0.u34.n6_1>=1))&&(i6.i1.u32.n6_2>=1))&&(i5.u40.n6_0>=1))&&(i7.i1.u31.n6_5>=1))&&(i9.u39.n6_6>=1))&&(i4.i0.u33.n6_3>=1))&&(i8.u41.n6_4>=1)))))
=> equivalent forward existential formula: ([(Init * !(EG(!(EG(!((i8.u12.a4>=1)))))))] = FALSE * [(EY(Init) * !((((((((((((((((i9.u39.s4_6<1)&&(i5.u7.s4_0<1))&&(i6.i1.u8.s4_2<1))&&(i3.i0.u9.s4_1<1))&&(i8.u30.s4_4<1))&&(i4.i0.u10.s4_3<1))&&(i7.i1.u11.s4_5<1))||((u5.malicious_reservoir>=1)&&(u5.s5_5>=1)))||((u5.malicious_reservoir>=1)&&(u5.s5_2>=1)))||((u5.malicious_reservoir>=1)&&(u5.s5_4>=1)))||((u5.malicious_reservoir>=1)&&(u5.s5_1>=1)))||((u5.malicious_reservoir>=1)&&(u5.s5_3>=1)))||((u5.malicious_reservoir>=1)&&(u5.s5_0>=1)))||((u5.malicious_reservoir>=1)&&(u5.s5_6>=1)))||((((((((i8.u12.a5>=1)&&(i3.i0.u34.n6_1>=1))&&(i6.i1.u32.n6_2>=1))&&(i5.u40.n6_0>=1))&&(i7.i1.u31.n6_5>=1))&&(i9.u39.n6_6>=1))&&(i4.i0.u33.n6_3>=1))&&(i8.u41.n6_4>=1)))))] = FALSE)
Reverse transition relation is NOT exact ! Due to transitions malC1_6, malS6_3, malS2_3, malS1_4, malS4_1, malS4_2, malS4_6, malS3_0, malS1_5, u5.malS5_0, u5.malS2_6, u5.malS5_1, u5.malS5_2, u5.malS5_3, u5.malS5_4, u5.malS5_5, u5.malS5_6, u5.malS1_6, i8.u12.malA1, i8.u12.malA4, i8.u12.malA2, i8.u12.malA5, i8.u12.malA3, Intersection with reachable at each step enabled. (destroyed/reverse/intersect/total) :0/62/23/85
(forward)formula 1,0,235.887,1784836,1,0,1.80564e+06,254795,3414,9.51083e+06,878,1.04681e+07,2647658
FORMULA QuasiCertifProtocol-PT-06-CTLFireability-01 FALSE TECHNIQUES DECISION_DIAGRAMS TOPOLOGICAL USE_NUPN
Formula is FALSE !
***************************************
original formula: AG(EF(((((((((((((((u5.s5_5>=1)&&(i1.i3.u4.n8_5_1>=1))&&(i1.i3.u4.n8_5_0>=1))&&(i1.i3.u4.n8_5_4>=1))&&(i1.i3.u4.n8_5_3>=1))&&(i1.i3.u4.n8_5_2>=1))&&(i1.i3.u4.n8_5_6>=1))&&(i1.i3.u4.n8_5_5>=1))||((((((((u5.s5_0>=1)&&(i1.i0.u1.n8_0_0>=1))&&(i1.i0.u1.n8_0_2>=1))&&(i1.i0.u1.n8_0_1>=1))&&(i1.i0.u1.n8_0_4>=1))&&(i1.i0.u1.n8_0_3>=1))&&(i1.i0.u1.n8_0_6>=1))&&(i1.i0.u1.n8_0_5>=1)))||((((((((u5.s5_6>=1)&&(i1.i4.u6.n8_6_1>=1))&&(i1.i4.u6.n8_6_0>=1))&&(i1.i4.u6.n8_6_4>=1))&&(i1.i4.u6.n8_6_3>=1))&&(i1.i4.u6.n8_6_2>=1))&&(i1.i4.u6.n8_6_6>=1))&&(i1.i4.u6.n8_6_5>=1)))||((((((((u5.s5_1>=1)&&(i1.i1.u2.n8_1_0>=1))&&(i1.i1.u2.n8_1_2>=1))&&(i1.i1.u2.n8_1_1>=1))&&(i1.i1.u2.n8_1_4>=1))&&(i1.i1.u2.n8_1_3>=1))&&(i1.i1.u2.n8_1_6>=1))&&(i1.i1.u2.n8_1_5>=1)))||((((((((u5.s5_2>=1)&&(i1.i6.u42.n8_2_0>=1))&&(i1.i6.u42.n8_2_2>=1))&&(i1.i6.u42.n8_2_1>=1))&&(i1.i6.u42.n8_2_4>=1))&&(i1.i6.u42.n8_2_3>=1))&&(i1.i6.u42.n8_2_6>=1))&&(i1.i6.u42.n8_2_5>=1)))||((((((((u5.s5_4>=1)&&(i1.i5.u43.n8_4_1>=1))&&(i1.i5.u43.n8_4_2>=1))&&(i1.i5.u43.n8_4_0>=1))&&(i1.i5.u43.n8_4_4>=1))&&(i1.i5.u43.n8_4_3>=1))&&(i1.i5.u43.n8_4_6>=1))&&(i1.i5.u43.n8_4_5>=1)))||((((((((u5.s5_3>=1)&&(i1.i2.u3.n8_3_2>=1))&&(i1.i2.u3.n8_3_0>=1))&&(i1.i2.u3.n8_3_1>=1))&&(i1.i2.u3.n8_3_4>=1))&&(i1.i2.u3.n8_3_3>=1))&&(i1.i2.u3.n8_3_6>=1))&&(i1.i2.u3.n8_3_5>=1)))))
=> equivalent forward existential formula: [(FwdU(Init,TRUE) * !(E(TRUE U ((((((((((((((u5.s5_5>=1)&&(i1.i3.u4.n8_5_1>=1))&&(i1.i3.u4.n8_5_0>=1))&&(i1.i3.u4.n8_5_4>=1))&&(i1.i3.u4.n8_5_3>=1))&&(i1.i3.u4.n8_5_2>=1))&&(i1.i3.u4.n8_5_6>=1))&&(i1.i3.u4.n8_5_5>=1))||((((((((u5.s5_0>=1)&&(i1.i0.u1.n8_0_0>=1))&&(i1.i0.u1.n8_0_2>=1))&&(i1.i0.u1.n8_0_1>=1))&&(i1.i0.u1.n8_0_4>=1))&&(i1.i0.u1.n8_0_3>=1))&&(i1.i0.u1.n8_0_6>=1))&&(i1.i0.u1.n8_0_5>=1)))||((((((((u5.s5_6>=1)&&(i1.i4.u6.n8_6_1>=1))&&(i1.i4.u6.n8_6_0>=1))&&(i1.i4.u6.n8_6_4>=1))&&(i1.i4.u6.n8_6_3>=1))&&(i1.i4.u6.n8_6_2>=1))&&(i1.i4.u6.n8_6_6>=1))&&(i1.i4.u6.n8_6_5>=1)))||((((((((u5.s5_1>=1)&&(i1.i1.u2.n8_1_0>=1))&&(i1.i1.u2.n8_1_2>=1))&&(i1.i1.u2.n8_1_1>=1))&&(i1.i1.u2.n8_1_4>=1))&&(i1.i1.u2.n8_1_3>=1))&&(i1.i1.u2.n8_1_6>=1))&&(i1.i1.u2.n8_1_5>=1)))||((((((((u5.s5_2>=1)&&(i1.i6.u42.n8_2_0>=1))&&(i1.i6.u42.n8_2_2>=1))&&(i1.i6.u42.n8_2_1>=1))&&(i1.i6.u42.n8_2_4>=1))&&(i1.i6.u42.n8_2_3>=1))&&(i1.i6.u42.n8_2_6>=1))&&(i1.i6.u42.n8_2_5>=1)))||((((((((u5.s5_4>=1)&&(i1.i5.u43.n8_4_1>=1))&&(i1.i5.u43.n8_4_2>=1))&&(i1.i5.u43.n8_4_0>=1))&&(i1.i5.u43.n8_4_4>=1))&&(i1.i5.u43.n8_4_3>=1))&&(i1.i5.u43.n8_4_6>=1))&&(i1.i5.u43.n8_4_5>=1)))||((((((((u5.s5_3>=1)&&(i1.i2.u3.n8_3_2>=1))&&(i1.i2.u3.n8_3_0>=1))&&(i1.i2.u3.n8_3_1>=1))&&(i1.i2.u3.n8_3_4>=1))&&(i1.i2.u3.n8_3_3>=1))&&(i1.i2.u3.n8_3_6>=1))&&(i1.i2.u3.n8_3_5>=1))))))] = FALSE
(forward)formula 2,0,246.778,1797244,1,0,1.82211e+06,260928,4000,9.52063e+06,970,1.04825e+07,2740218
FORMULA QuasiCertifProtocol-PT-06-CTLFireability-02 FALSE TECHNIQUES DECISION_DIAGRAMS TOPOLOGICAL USE_NUPN
Formula is FALSE !
***************************************
original formula: AF(AX(EF((i8.u12.a5>=1))))
=> equivalent forward existential formula: [FwdG(Init,!(!(EX(!(E(TRUE U (i8.u12.a5>=1)))))))] = FALSE
dead was empty
(forward)formula 3,1,251.854,1800148,1,0,1.8299e+06,261009,4006,9.52744e+06,970,1.04829e+07,2758746
FORMULA QuasiCertifProtocol-PT-06-CTLFireability-03 TRUE TECHNIQUES DECISION_DIAGRAMS TOPOLOGICAL USE_NUPN
Formula is TRUE !
***************************************
original formula: !(AG(((EG(((((((((u5.malicious_reservoir>=1)&&(i8.u27.Sstart_4>=1))||((u5.malicious_reservoir>=1)&&(u5.Sstart_6>=1)))||((u5.malicious_reservoir>=1)&&(i7.i0.u26.Sstart_5>=1)))||((u5.malicious_reservoir>=1)&&(i5.u20.Sstart_0>=1)))||((u5.malicious_reservoir>=1)&&(i4.i1.u29.Sstart_3>=1)))||((u5.malicious_reservoir>=1)&&(i3.i1.u21.Sstart_1>=1)))||((u5.malicious_reservoir>=1)&&(i6.i0.u28.Sstart_2>=1)))) + (i8.u12.a5<1)) + ((((((((u5.malicious_reservoir<1)||(i3.i1.u21.s2_1<1))&&((u5.malicious_reservoir<1)||(i6.i0.u28.s2_2<1)))&&((u5.malicious_reservoir<1)||(i8.u27.s2_4<1)))&&((u5.malicious_reservoir<1)||(i7.i0.u26.s2_5<1)))&&((u5.malicious_reservoir<1)||(i5.u20.s2_0<1)))&&((u5.malicious_reservoir<1)||(i4.i1.u29.s2_3<1)))&&((u5.malicious_reservoir<1)||(u5.s2_6<1))))))
=> equivalent forward existential formula: [(((FwdU(Init,TRUE) * !(((((((((u5.malicious_reservoir<1)||(i3.i1.u21.s2_1<1))&&((u5.malicious_reservoir<1)||(i6.i0.u28.s2_2<1)))&&((u5.malicious_reservoir<1)||(i8.u27.s2_4<1)))&&((u5.malicious_reservoir<1)||(i7.i0.u26.s2_5<1)))&&((u5.malicious_reservoir<1)||(i5.u20.s2_0<1)))&&((u5.malicious_reservoir<1)||(i4.i1.u29.s2_3<1)))&&((u5.malicious_reservoir<1)||(u5.s2_6<1))))) * !((i8.u12.a5<1))) * !(EG(((((((((u5.malicious_reservoir>=1)&&(i8.u27.Sstart_4>=1))||((u5.malicious_reservoir>=1)&&(u5.Sstart_6>=1)))||((u5.malicious_reservoir>=1)&&(i7.i0.u26.Sstart_5>=1)))||((u5.malicious_reservoir>=1)&&(i5.u20.Sstart_0>=1)))||((u5.malicious_reservoir>=1)&&(i4.i1.u29.Sstart_3>=1)))||((u5.malicious_reservoir>=1)&&(i3.i1.u21.Sstart_1>=1)))||((u5.malicious_reservoir>=1)&&(i6.i0.u28.Sstart_2>=1))))))] != FALSE
(forward)formula 4,0,254.773,1805164,1,0,1.832e+06,261635,4104,9.53196e+06,972,1.04844e+07,2799805
FORMULA QuasiCertifProtocol-PT-06-CTLFireability-04 FALSE TECHNIQUES DECISION_DIAGRAMS TOPOLOGICAL USE_NUPN
Formula is FALSE !
***************************************
original formula: AF(((((((((i4.i1.u22.s3_3>=1)&&(i4.i0.u33.n5_3>=1))||((i6.i0.u36.s3_2>=1)&&(i6.i1.u32.n5_2>=1)))||((i8.u35.s3_4>=1)&&(i8.u41.n5_4>=1)))||((i7.i0.u38.s3_5>=1)&&(i7.i1.u31.n5_5>=1)))||((i9.u39.s3_6>=1)&&(i9.u39.n5_6>=1)))||((i3.i1.u23.s3_1>=1)&&(i3.i0.u34.n5_1>=1)))||((i5.u24.s3_0>=1)&&(i5.u40.n5_0>=1))))
=> equivalent forward existential formula: [FwdG(Init,!(((((((((i4.i1.u22.s3_3>=1)&&(i4.i0.u33.n5_3>=1))||((i6.i0.u36.s3_2>=1)&&(i6.i1.u32.n5_2>=1)))||((i8.u35.s3_4>=1)&&(i8.u41.n5_4>=1)))||((i7.i0.u38.s3_5>=1)&&(i7.i1.u31.n5_5>=1)))||((i9.u39.s3_6>=1)&&(i9.u39.n5_6>=1)))||((i3.i1.u23.s3_1>=1)&&(i3.i0.u34.n5_1>=1)))||((i5.u24.s3_0>=1)&&(i5.u40.n5_0>=1)))))] = FALSE
(forward)formula 5,0,254.857,1807804,1,0,1.83635e+06,261635,4184,9.53529e+06,973,1.04844e+07,2822402
FORMULA QuasiCertifProtocol-PT-06-CTLFireability-05 FALSE TECHNIQUES DECISION_DIAGRAMS TOPOLOGICAL USE_NUPN
Formula is FALSE !
***************************************
original formula: !(E(EF(((((((((u5.malicious_reservoir>=1)&&(i8.u27.Sstart_4>=1))||((u5.malicious_reservoir>=1)&&(u5.Sstart_6>=1)))||((u5.malicious_reservoir>=1)&&(i7.i0.u26.Sstart_5>=1)))||((u5.malicious_reservoir>=1)&&(i5.u20.Sstart_0>=1)))||((u5.malicious_reservoir>=1)&&(i4.i1.u29.Sstart_3>=1)))||((u5.malicious_reservoir>=1)&&(i3.i1.u21.Sstart_1>=1)))||((u5.malicious_reservoir>=1)&&(i6.i0.u28.Sstart_2>=1)))) U ((((((((i8.u12.a1>=1)&&(i8.u25.n2_6>=1))&&(i7.i0.u26.n2_5>=1))&&(i8.u27.n2_4>=1))&&(i4.i1.u29.n2_3>=1))&&(i6.i0.u28.n2_2>=1))&&(i3.i1.u21.n2_1>=1))&&(i5.u20.n2_0>=1))))
=> equivalent forward existential formula: [(FwdU(Init,E(TRUE U ((((((((u5.malicious_reservoir>=1)&&(i8.u27.Sstart_4>=1))||((u5.malicious_reservoir>=1)&&(u5.Sstart_6>=1)))||((u5.malicious_reservoir>=1)&&(i7.i0.u26.Sstart_5>=1)))||((u5.malicious_reservoir>=1)&&(i5.u20.Sstart_0>=1)))||((u5.malicious_reservoir>=1)&&(i4.i1.u29.Sstart_3>=1)))||((u5.malicious_reservoir>=1)&&(i3.i1.u21.Sstart_1>=1)))||((u5.malicious_reservoir>=1)&&(i6.i0.u28.Sstart_2>=1))))) * ((((((((i8.u12.a1>=1)&&(i8.u25.n2_6>=1))&&(i7.i0.u26.n2_5>=1))&&(i8.u27.n2_4>=1))&&(i4.i1.u29.n2_3>=1))&&(i6.i0.u28.n2_2>=1))&&(i3.i1.u21.n2_1>=1))&&(i5.u20.n2_0>=1)))] = FALSE
(forward)formula 6,0,254.904,1808860,1,0,1.83987e+06,261691,4219,9.54016e+06,973,1.04848e+07,2829815
FORMULA QuasiCertifProtocol-PT-06-CTLFireability-06 FALSE TECHNIQUES DECISION_DIAGRAMS TOPOLOGICAL USE_NUPN
Formula is FALSE !
***************************************
original formula: !(A(AF((((((((i1.i4.u6.s6_6>=1)||(i1.i0.u1.s6_0>=1))||(i1.i1.u2.s6_1>=1))||(i1.i6.u42.s6_2>=1))||(i1.i2.u3.s6_3>=1))||(i1.i3.u4.s6_5>=1))||(i1.i5.u43.s6_4>=1))) U (((((((i1.i4.u6.s6_6>=1)||(i1.i0.u1.s6_0>=1))||(i1.i1.u2.s6_1>=1))||(i1.i6.u42.s6_2>=1))||(i1.i2.u3.s6_3>=1))||(i1.i3.u4.s6_5>=1))||(i1.i5.u43.s6_4>=1))))
=> equivalent forward existential formula: ([FwdG((FwdU(Init,!((((((((i1.i4.u6.s6_6>=1)||(i1.i0.u1.s6_0>=1))||(i1.i1.u2.s6_1>=1))||(i1.i6.u42.s6_2>=1))||(i1.i2.u3.s6_3>=1))||(i1.i3.u4.s6_5>=1))||(i1.i5.u43.s6_4>=1)))) * !((((((((i1.i4.u6.s6_6>=1)||(i1.i0.u1.s6_0>=1))||(i1.i1.u2.s6_1>=1))||(i1.i6.u42.s6_2>=1))||(i1.i2.u3.s6_3>=1))||(i1.i3.u4.s6_5>=1))||(i1.i5.u43.s6_4>=1)))),!((((((((i1.i4.u6.s6_6>=1)||(i1.i0.u1.s6_0>=1))||(i1.i1.u2.s6_1>=1))||(i1.i6.u42.s6_2>=1))||(i1.i2.u3.s6_3>=1))||(i1.i3.u4.s6_5>=1))||(i1.i5.u43.s6_4>=1))))] != FALSE + [FwdG(Init,!((((((((i1.i4.u6.s6_6>=1)||(i1.i0.u1.s6_0>=1))||(i1.i1.u2.s6_1>=1))||(i1.i6.u42.s6_2>=1))||(i1.i2.u3.s6_3>=1))||(i1.i3.u4.s6_5>=1))||(i1.i5.u43.s6_4>=1))))] != FALSE)
(forward)formula 7,1,259.496,1826256,1,0,1.85342e+06,266167,4346,9.56304e+06,978,1.05143e+07,2966002
FORMULA QuasiCertifProtocol-PT-06-CTLFireability-07 TRUE TECHNIQUES DECISION_DIAGRAMS TOPOLOGICAL USE_NUPN
Formula is TRUE !
***************************************
original formula: EF(((u5.malicious_reservoir>=1)&&(u5.s5_4>=1)))
=> equivalent forward existential formula: [(FwdU(Init,TRUE) * ((u5.malicious_reservoir>=1)&&(u5.s5_4>=1)))] != FALSE
(forward)formula 8,1,260.518,1826784,1,0,1.85344e+06,266167,4346,9.5649e+06,978,1.05143e+07,2970083
FORMULA QuasiCertifProtocol-PT-06-CTLFireability-08 TRUE TECHNIQUES DECISION_DIAGRAMS TOPOLOGICAL USE_NUPN
Formula is TRUE !
***************************************
original formula: AF((((u5.malicious_reservoir>=1)&&(i3.i1.u23.s3_1>=1)) * AF((((u5.malicious_reservoir>=1)&&(i1.i4.u6.s6_6>=1))||((i7.i0.u38.s3_5>=1)&&(i7.i1.u31.n5_5>=1))))))
=> equivalent forward existential formula: [FwdG(Init,!((((u5.malicious_reservoir>=1)&&(i3.i1.u23.s3_1>=1)) * !(EG(!((((u5.malicious_reservoir>=1)&&(i1.i4.u6.s6_6>=1))||((i7.i0.u38.s3_5>=1)&&(i7.i1.u31.n5_5>=1)))))))))] = FALSE
(forward)formula 9,0,363.136,2117712,1,0,2.29815e+06,290049,4382,1.02919e+07,978,1.10683e+07,3852399
FORMULA QuasiCertifProtocol-PT-06-CTLFireability-09 FALSE TECHNIQUES DECISION_DIAGRAMS TOPOLOGICAL USE_NUPN
Formula is FALSE !
***************************************
original formula: EG((((((((((((u5.s5_3<1)||(i1.i2.u3.n8_3_2<1))||(i1.i2.u3.n8_3_0<1))||(i1.i2.u3.n8_3_1<1))||(i1.i2.u3.n8_3_4<1))||(i1.i2.u3.n8_3_3<1))||(i1.i2.u3.n8_3_6<1))||(i1.i2.u3.n8_3_5<1))||(u5.malicious_reservoir<1))||(u0.c1_4<1))||(((u5.malicious_reservoir<1)||(u5.s5_1<1))&&((((((((u5.s5_2<1)||(i1.i6.u42.n8_2_0<1))||(i1.i6.u42.n8_2_2<1))||(i1.i6.u42.n8_2_1<1))||(i1.i6.u42.n8_2_4<1))||(i1.i6.u42.n8_2_3<1))||(i1.i6.u42.n8_2_6<1))||(i1.i6.u42.n8_2_5<1)))))
=> equivalent forward existential formula: [FwdG(Init,(((((((((((u5.s5_3<1)||(i1.i2.u3.n8_3_2<1))||(i1.i2.u3.n8_3_0<1))||(i1.i2.u3.n8_3_1<1))||(i1.i2.u3.n8_3_4<1))||(i1.i2.u3.n8_3_3<1))||(i1.i2.u3.n8_3_6<1))||(i1.i2.u3.n8_3_5<1))||(u5.malicious_reservoir<1))||(u0.c1_4<1))||(((u5.malicious_reservoir<1)||(u5.s5_1<1))&&((((((((u5.s5_2<1)||(i1.i6.u42.n8_2_0<1))||(i1.i6.u42.n8_2_2<1))||(i1.i6.u42.n8_2_1<1))||(i1.i6.u42.n8_2_4<1))||(i1.i6.u42.n8_2_3<1))||(i1.i6.u42.n8_2_6<1))||(i1.i6.u42.n8_2_5<1)))))] != FALSE
(forward)formula 10,1,469.176,2492592,1,0,2.93532e+06,314988,4521,1.13829e+07,1001,1.15607e+07,4555496
FORMULA QuasiCertifProtocol-PT-06-CTLFireability-10 TRUE TECHNIQUES DECISION_DIAGRAMS TOPOLOGICAL USE_NUPN
Formula is TRUE !
***************************************
original formula: !(AF((EX(((((((((u5.s5_1>=1)&&(i1.i1.u2.n8_1_0>=1))&&(i1.i1.u2.n8_1_2>=1))&&(i1.i1.u2.n8_1_1>=1))&&(i1.i1.u2.n8_1_4>=1))&&(i1.i1.u2.n8_1_3>=1))&&(i1.i1.u2.n8_1_6>=1))&&(i1.i1.u2.n8_1_5>=1))) * ((u5.malicious_reservoir<1)||(i6.i0.u36.s3_2<1)))))
=> equivalent forward existential formula: [FwdG(Init,!((EX(((((((((u5.s5_1>=1)&&(i1.i1.u2.n8_1_0>=1))&&(i1.i1.u2.n8_1_2>=1))&&(i1.i1.u2.n8_1_1>=1))&&(i1.i1.u2.n8_1_4>=1))&&(i1.i1.u2.n8_1_3>=1))&&(i1.i1.u2.n8_1_6>=1))&&(i1.i1.u2.n8_1_5>=1))) * ((u5.malicious_reservoir<1)||(i6.i0.u36.s3_2<1)))))] != FALSE
(forward)formula 11,1,500.575,2499720,1,0,2.9425e+06,316473,1445,1.14122e+07,338,1.15857e+07,620316
FORMULA QuasiCertifProtocol-PT-06-CTLFireability-11 TRUE TECHNIQUES DECISION_DIAGRAMS TOPOLOGICAL USE_NUPN
Formula is TRUE !
***************************************
original formula: A(((u5.malicious_reservoir>=1)&&(i6.i0.u28.s2_2>=1)) U (AF(((u5.malicious_reservoir>=1)&&(i1.i4.u6.s6_6>=1))) + ((i3.i1.u21.s2_1>=1)&&(i3.i1.u23.n3_1>=1))))
=> equivalent forward existential formula: [((Init * !(EG(!((!(EG(!(((u5.malicious_reservoir>=1)&&(i1.i4.u6.s6_6>=1))))) + ((i3.i1.u21.s2_1>=1)&&(i3.i1.u23.n3_1>=1))))))) * !(E(!((!(EG(!(((u5.malicious_reservoir>=1)&&(i1.i4.u6.s6_6>=1))))) + ((i3.i1.u21.s2_1>=1)&&(i3.i1.u23.n3_1>=1)))) U (!(((u5.malicious_reservoir>=1)&&(i6.i0.u28.s2_2>=1))) * !((!(EG(!(((u5.malicious_reservoir>=1)&&(i1.i4.u6.s6_6>=1))))) + ((i3.i1.u21.s2_1>=1)&&(i3.i1.u23.n3_1>=1))))))))] != FALSE
(forward)formula 12,0,624.714,2499720,1,0,2.9425e+06,316473,1900,1.14122e+07,442,1.15857e+07,2206944
FORMULA QuasiCertifProtocol-PT-06-CTLFireability-12 FALSE TECHNIQUES DECISION_DIAGRAMS TOPOLOGICAL USE_NUPN
Formula is FALSE !
***************************************
original formula: AF(((EG((i8.u12.a2>=1)) * (u5.s2_6>=1)) * (i9.u37.n3_6>=1)))
=> equivalent forward existential formula: [FwdG(Init,!(((EG((i8.u12.a2>=1)) * (u5.s2_6>=1)) * (i9.u37.n3_6>=1))))] = FALSE
(forward)formula 13,0,663.251,2499720,1,0,2.9425e+06,316473,2238,1.14122e+07,464,1.15857e+07,2746749
FORMULA QuasiCertifProtocol-PT-06-CTLFireability-13 FALSE TECHNIQUES DECISION_DIAGRAMS TOPOLOGICAL USE_NUPN
Formula is FALSE !
***************************************
original formula: AF(EX(AX(((u5.malicious_reservoir>=1)&&(i9.u39.s4_6>=1)))))
=> equivalent forward existential formula: [FwdG(Init,!(EX(!(EX(!(((u5.malicious_reservoir>=1)&&(i9.u39.s4_6>=1))))))))] = FALSE
(forward)formula 14,1,828.022,2499720,1,0,2.9425e+06,316473,2247,1.14122e+07,464,1.20129e+07,3039477
FORMULA QuasiCertifProtocol-PT-06-CTLFireability-14 TRUE TECHNIQUES DECISION_DIAGRAMS TOPOLOGICAL USE_NUPN
Formula is TRUE !
***************************************
original formula: EF(((((((i9.u39.s3_6>=1)&&(i9.u39.n5_6>=1))&&(i5.u20.s2_0>=1))&&(i5.u24.n3_0>=1))||((((((((i6.i1.u8.n7_2_0>=1)&&(i3.i0.u9.n7_1_0>=1))&&(i5.u7.n7_0_0>=1))&&(i9.u39.n7_6_0>=1))&&(i7.i1.u11.n7_5_0>=1))&&(i8.u30.n7_4_0>=1))&&(i4.i0.u10.n7_3_0>=1))&&(i1.i6.u42.Cstart_0>=1)))||((i4.i1.u29.s2_3>=1)&&(i4.i1.u22.n3_3>=1))))
=> equivalent forward existential formula: [(FwdU(Init,TRUE) * ((((((i9.u39.s3_6>=1)&&(i9.u39.n5_6>=1))&&(i5.u20.s2_0>=1))&&(i5.u24.n3_0>=1))||((((((((i6.i1.u8.n7_2_0>=1)&&(i3.i0.u9.n7_1_0>=1))&&(i5.u7.n7_0_0>=1))&&(i9.u39.n7_6_0>=1))&&(i7.i1.u11.n7_5_0>=1))&&(i8.u30.n7_4_0>=1))&&(i4.i0.u10.n7_3_0>=1))&&(i1.i6.u42.Cstart_0>=1)))||((i4.i1.u29.s2_3>=1)&&(i4.i1.u22.n3_3>=1))))] != FALSE
(forward)formula 15,1,828.069,2499720,1,0,2.9425e+06,316473,2315,1.14122e+07,466,1.20129e+07,3048446
FORMULA QuasiCertifProtocol-PT-06-CTLFireability-15 TRUE TECHNIQUES DECISION_DIAGRAMS TOPOLOGICAL USE_NUPN
Formula is TRUE !
***************************************
BK_STOP 1589858862325
--------------------
content from stderr:
+ export BINDIR=/home/mcc/BenchKit/
+ BINDIR=/home/mcc/BenchKit/
++ pwd
+ export MODEL=/home/mcc/execution
+ MODEL=/home/mcc/execution
+ [[ CTLFireability = StateSpace ]]
+ /home/mcc/BenchKit//runeclipse.sh /home/mcc/execution CTLFireability -its -ltsminpath /home/mcc/BenchKit//lts_install_dir/ -greatspnpath /home/mcc/BenchKit//greatspn/ -order META -manyOrder -smt -timeout 3600
+ ulimit -s 65536
+ [[ -z '' ]]
+ export LTSMIN_MEM_SIZE=8589934592
+ LTSMIN_MEM_SIZE=8589934592
+ /home/mcc/BenchKit//itstools/its-tools -data /home/mcc/execution/workspace -pnfolder /home/mcc/execution -examination CTLFireability -z3path /home/mcc/BenchKit//z3/bin/z3 -yices2path /home/mcc/BenchKit//yices/bin/yices -its -ltsminpath /home/mcc/BenchKit//lts_install_dir/ -greatspnpath /home/mcc/BenchKit//greatspn/ -order META -manyOrder -smt -timeout 3600 -vmargs -Dosgi.locking=none -Declipse.stateSaveDelayInterval=-1 -Dosgi.configuration.area=/tmp/.eclipse -Xss128m -Xms40m -Xmx16000m -Dfile.encoding=UTF-8 -Dosgi.requiredJavaVersion=1.6
Sequence of Actions to be Executed by the VM
This is useful if one wants to reexecute the tool in the VM from the submitted image disk.
set -x
# this is for BenchKit: configuration of major elements for the test
export BK_INPUT="QuasiCertifProtocol-PT-06"
export BK_EXAMINATION="CTLFireability"
export BK_TOOL="itstools"
export BK_RESULT_DIR="/tmp/BK_RESULTS/OUTPUTS"
export BK_TIME_CONFINEMENT="3600"
export BK_MEMORY_CONFINEMENT="16384"
# this is specific to your benchmark or test
export BIN_DIR="$HOME/BenchKit/bin"
# remove the execution directoty if it exists (to avoid increse of .vmdk images)
if [ -d execution ] ; then
rm -rf execution
fi
# this is for BenchKit: explicit launching of the test
echo "====================================================================="
echo " Generated by BenchKit 2-4028"
echo " Executing tool itstools"
echo " Input is QuasiCertifProtocol-PT-06, examination is CTLFireability"
echo " Time confinement is $BK_TIME_CONFINEMENT seconds"
echo " Memory confinement is 16384 MBytes"
echo " Number of cores is 4"
echo " Run identifier is r126-tajo-158961390900788"
echo "====================================================================="
echo
echo "--------------------"
echo "preparation of the directory to be used:"
tar xzf /home/mcc/BenchKit/INPUTS/QuasiCertifProtocol-PT-06.tgz
mv QuasiCertifProtocol-PT-06 execution
cd execution
if [ "CTLFireability" = "ReachabilityDeadlock" ] || [ "CTLFireability" = "UpperBounds" ] || [ "CTLFireability" = "QuasiLiveness" ] || [ "CTLFireability" = "StableMarking" ] || [ "CTLFireability" = "Liveness" ] || [ "CTLFireability" = "OneSafe" ] || [ "CTLFireability" = "StateSpace" ]; then
rm -f GenericPropertiesVerdict.xml
fi
pwd
ls -lh
echo
echo "--------------------"
echo "content from stdout:"
echo
echo "=== Data for post analysis generated by BenchKit (invocation template)"
echo
if [ "CTLFireability" = "UpperBounds" ] ; then
echo "The expected result is a vector of positive values"
echo NUM_VECTOR
elif [ "CTLFireability" != "StateSpace" ] ; then
echo "The expected result is a vector of booleans"
echo BOOL_VECTOR
else
echo "no data necessary for post analysis"
fi
echo
if [ -f "CTLFireability.txt" ] ; then
echo "here is the order used to build the result vector(from text file)"
for x in $(grep Property CTLFireability.txt | cut -d ' ' -f 2 | sort -u) ; do
echo "FORMULA_NAME $x"
done
elif [ -f "CTLFireability.xml" ] ; then # for cunf (txt files deleted;-)
echo echo "here is the order used to build the result vector(from xml file)"
for x in $(grep '
echo "FORMULA_NAME $x"
done
elif [ "CTLFireability" = "ReachabilityDeadlock" ] || [ "CTLFireability" = "QuasiLiveness" ] || [ "CTLFireability" = "StableMarking" ] || [ "CTLFireability" = "Liveness" ] || [ "CTLFireability" = "OneSafe" ] ; then
echo "FORMULA_NAME CTLFireability"
fi
echo
echo "=== Now, execution of the tool begins"
echo
echo -n "BK_START "
date -u +%s%3N
echo
timeout -s 9 $BK_TIME_CONFINEMENT bash -c "/home/mcc/BenchKit/BenchKit_head.sh 2> STDERR ; echo ; echo -n \"BK_STOP \" ; date -u +%s%3N"
if [ $? -eq 137 ] ; then
echo
echo "BK_TIME_CONFINEMENT_REACHED"
fi
echo
echo "--------------------"
echo "content from stderr:"
echo
cat STDERR ;

