About the Execution of ITS-Tools for ShieldIIPs-PT-001A
| Execution Summary | |||||
| Max Memory Used (MB) |
Time wait (ms) | CPU Usage (ms) | I/O Wait (ms) | Computed Result | Execution Status |
| 15742.950 | 3831.00 | 9835.00 | 48.00 | FFFFFFFFTTTTFFFF | normal |
Execution Chart
We display below the execution chart for this examination (boot time has been removed).
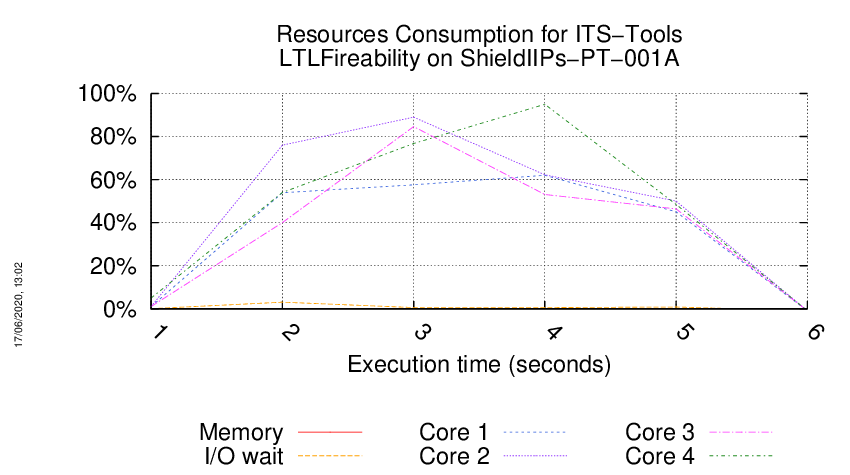
Trace from the execution
Formatting '/mnt/tpsp/fkordon/mcc2020-input.r210-tajo-159033475100042.qcow2', fmt=qcow2 size=4294967296 backing_file='/mnt/tpsp/fkordon/mcc2020-input.qcow2' encryption=off cluster_size=65536 lazy_refcounts=off
Waiting for the VM to be ready (probing ssh)
.......................................................................................................................
=====================================================================
Generated by BenchKit 2-4028
Executing tool itstools
Input is ShieldIIPs-PT-001A, examination is LTLFireability
Time confinement is 3600 seconds
Memory confinement is 16384 MBytes
Number of cores is 4
Run identifier is r210-tajo-159033475100042
=====================================================================
--------------------
preparation of the directory to be used:
/home/mcc/execution
total 172K
-rw-r--r-- 1 mcc users 2.9K May 14 00:30 CTLCardinality.txt
-rw-r--r-- 1 mcc users 16K May 14 00:30 CTLCardinality.xml
-rw-r--r-- 1 mcc users 2.3K May 13 17:43 CTLFireability.txt
-rw-r--r-- 1 mcc users 16K May 13 17:43 CTLFireability.xml
-rw-r--r-- 1 mcc users 3.1K May 14 10:01 LTLCardinality.txt
-rw-r--r-- 1 mcc users 23K May 14 10:01 LTLCardinality.xml
-rw-r--r-- 1 mcc users 1.8K May 14 10:01 LTLFireability.txt
-rw-r--r-- 1 mcc users 15K May 14 10:01 LTLFireability.xml
-rw-r--r-- 1 mcc users 1 May 12 20:42 NewModel
-rw-r--r-- 1 mcc users 3.1K May 13 13:08 ReachabilityCardinality.txt
-rw-r--r-- 1 mcc users 16K May 13 13:08 ReachabilityCardinality.xml
-rw-r--r-- 1 mcc users 3.0K May 13 07:37 ReachabilityFireability.txt
-rw-r--r-- 1 mcc users 22K May 13 07:37 ReachabilityFireability.xml
-rw-r--r-- 1 mcc users 1.6K May 13 16:53 UpperBounds.txt
-rw-r--r-- 1 mcc users 3.7K May 13 16:53 UpperBounds.xml
-rw-r--r-- 1 mcc users 6 May 12 20:42 equiv_col
-rw-r--r-- 1 mcc users 5 May 12 20:42 instance
-rw-r--r-- 1 mcc users 6 May 12 20:42 iscolored
-rw-r--r-- 1 mcc users 9.0K May 12 20:42 model.pnml
--------------------
content from stdout:
=== Data for post analysis generated by BenchKit (invocation template)
The expected result is a vector of booleans
BOOL_VECTOR
here is the order used to build the result vector(from text file)
FORMULA_NAME ShieldIIPs-PT-001A-00
FORMULA_NAME ShieldIIPs-PT-001A-01
FORMULA_NAME ShieldIIPs-PT-001A-02
FORMULA_NAME ShieldIIPs-PT-001A-03
FORMULA_NAME ShieldIIPs-PT-001A-04
FORMULA_NAME ShieldIIPs-PT-001A-05
FORMULA_NAME ShieldIIPs-PT-001A-06
FORMULA_NAME ShieldIIPs-PT-001A-07
FORMULA_NAME ShieldIIPs-PT-001A-08
FORMULA_NAME ShieldIIPs-PT-001A-09
FORMULA_NAME ShieldIIPs-PT-001A-10
FORMULA_NAME ShieldIIPs-PT-001A-11
FORMULA_NAME ShieldIIPs-PT-001A-12
FORMULA_NAME ShieldIIPs-PT-001A-13
FORMULA_NAME ShieldIIPs-PT-001A-14
FORMULA_NAME ShieldIIPs-PT-001A-15
=== Now, execution of the tool begins
BK_START 1590561056969
[2020-05-27 06:30:58] [INFO ] Running its-tools with arguments : [-pnfolder, /home/mcc/execution, -examination, LTLFireability, -z3path, /home/mcc/BenchKit//z3/bin/z3, -yices2path, /home/mcc/BenchKit//yices/bin/yices, -its, -ltsminpath, /home/mcc/BenchKit//lts_install_dir/, -greatspnpath, /home/mcc/BenchKit//greatspn/, -order, META, -manyOrder, -smt, -timeout, 3600]
[2020-05-27 06:30:58] [INFO ] Parsing pnml file : /home/mcc/execution/model.pnml
[2020-05-27 06:30:58] [INFO ] Load time of PNML (sax parser for PT used): 25 ms
[2020-05-27 06:30:58] [INFO ] Transformed 28 places.
[2020-05-27 06:30:58] [INFO ] Transformed 27 transitions.
[2020-05-27 06:30:58] [INFO ] Found NUPN structural information;
[2020-05-27 06:30:58] [INFO ] Parsed PT model containing 28 places and 27 transitions in 59 ms.
Parsed 16 properties from file /home/mcc/execution/LTLFireability.xml in 14 ms.
Working with output stream class java.io.PrintStream
Finished random walk after 112 steps, including 0 resets, run visited all 29 properties in 4 ms. (steps per millisecond=28 )
[2020-05-27 06:30:58] [INFO ] Initial state reduction rules for CTL removed 2 formulas.
[2020-05-27 06:30:58] [INFO ] Flatten gal took : 26 ms
FORMULA ShieldIIPs-PT-001A-11 TRUE TECHNIQUES TOPOLOGICAL INITIAL_STATE
FORMULA ShieldIIPs-PT-001A-10 TRUE TECHNIQUES TOPOLOGICAL INITIAL_STATE
[2020-05-27 06:30:58] [INFO ] Flatten gal took : 10 ms
Using solver Z3 to compute partial order matrices.
Built C files in :
/home/mcc/execution
[2020-05-27 06:30:58] [INFO ] Applying decomposition
[2020-05-27 06:30:58] [INFO ] Flatten gal took : 13 ms
Converted graph to binary with : CommandLine [args=[/home/mcc/BenchKit/itstools/plugins/fr.lip6.move.gal.louvain.binaries_1.0.0.202005100927/bin/convert-linux64, -i, /tmp/graph5265616746921240628.txt, -o, /tmp/graph5265616746921240628.bin, -w, /tmp/graph5265616746921240628.weights], workingDir=null]
Built communities with : CommandLine [args=[/home/mcc/BenchKit/itstools/plugins/fr.lip6.move.gal.louvain.binaries_1.0.0.202005100927/bin/louvain-linux64, /tmp/graph5265616746921240628.bin, -l, -1, -v, -w, /tmp/graph5265616746921240628.weights, -q, 0, -e, 0.001], workingDir=null]
[2020-05-27 06:30:58] [INFO ] Input system was already deterministic with 27 transitions.
[2020-05-27 06:30:58] [INFO ] Decomposing Gal with order
[2020-05-27 06:30:58] [INFO ] Rewriting arrays to variables to allow decomposition.
[2020-05-27 06:30:58] [INFO ] Removed a total of 16 redundant transitions.
Presburger conditions satisfied. Using coverability to approximate state space in K-Induction.
// Phase 1: matrix 27 rows 28 cols
[2020-05-27 06:30:58] [INFO ] Computed 10 place invariants in 6 ms
inv : p0 + p24 + p25 + p26 + p27 = 1
inv : p0 + p5 + p6 + p7 = 1
inv : p0 + p3 + p4 = 1
inv : p0 + p14 + p15 + p16 + p17 = 1
inv : p0 + p20 + p21 + p22 + p23 = 1
inv : p0 + p12 + p13 = 1
inv : p0 + p1 + p2 = 1
inv : p0 + p18 + p19 = 1
inv : p0 + p10 + p11 = 1
inv : p0 + p5 + p8 + p9 = 1
Total of 10 invariants.
[2020-05-27 06:30:58] [INFO ] Computed 10 place invariants in 8 ms
[2020-05-27 06:30:58] [INFO ] Flatten gal took : 40 ms
[2020-05-27 06:30:58] [INFO ] Fuse similar labels procedure discarded/fused a total of 16 labels/synchronizations in 3 ms.
[2020-05-27 06:30:59] [INFO ] Time to serialize gal into /home/mcc/execution/LTLFireability.pnml.gal : 6 ms
[2020-05-27 06:30:59] [INFO ] Time to serialize properties into /home/mcc/execution/LTLFireability.ltl : 1 ms
Invoking ITS tools like this :CommandLine [args=[/home/mcc/BenchKit/itstools/plugins/fr.lip6.move.gal.itstools.binaries_1.0.0.202005100927/bin/its-ltl-linux64, --gc-threshold, 2000000, -i, /home/mcc/execution/LTLFireability.pnml.gal, -t, CGAL, -LTL, /home/mcc/execution/LTLFireability.ltl, -c, -stutter-deadlock], workingDir=/home/mcc/execution]
its-ltl command run as :
/home/mcc/BenchKit/itstools/plugins/fr.lip6.move.gal.itstools.binaries_1.0.0.202005100927/bin/its-ltl-linux64 --gc-threshold 2000000 -i /home/mcc/execution/LTLFireability.pnml.gal -t CGAL -LTL /home/mcc/execution/LTLFireability.ltl -c -stutter-deadlock
Read 14 LTL properties
Checking formula 0 : !(((F("((i1.u2.p6==1)&&(i1.u6.p16==1))"))&&((F(X(G("((i4.u8.p22!=1)&&(((i2.u4.p11!=1)||(i1.u6.p15!=1))||(u9.p27!=1)))"))))||(X("(((i2.u4.p11==1)&&(i1.u6.p15==1))&&(u9.p27==1))")))))
Formula 0 simplified : !(F"((i1.u2.p6==1)&&(i1.u6.p16==1))" & (FXG"((i4.u8.p22!=1)&&(((i2.u4.p11!=1)||(i1.u6.p15!=1))||(u9.p27!=1)))" | X"(((i2.u4.p11==1)&&(i1.u6.p15==1))&&(u9.p27==1))"))
[2020-05-27 06:30:59] [INFO ] Proved 28 variables to be positive in 108 ms
[2020-05-27 06:30:59] [INFO ] Computing symmetric may disable matrix : 27 transitions.
[2020-05-27 06:30:59] [INFO ] Computation of disable matrix completed :0/27 took 0 ms. Total solver calls (SAT/UNSAT): 0(0/0)
[2020-05-27 06:30:59] [INFO ] Computation of Complete disable matrix. took 1 ms. Total solver calls (SAT/UNSAT): 0(0/0)
[2020-05-27 06:30:59] [INFO ] Computing symmetric may enable matrix : 27 transitions.
[2020-05-27 06:30:59] [INFO ] Computation of Complete enable matrix. took 0 ms. Total solver calls (SAT/UNSAT): 0(0/0)
built 7 ordering constraints for composite.
built 5 ordering constraints for composite.
built 6 ordering constraints for composite.
built 6 ordering constraints for composite.
built 5 ordering constraints for composite.
Reverse transition relation is NOT exact ! Due to transitions t0, t19, t21, u9.t5, u9.t6, i1.u6.t1, i1.u6.t2, i1.u6.t9, i4.t12, i4.u8.t3, i4.u8.t4, Intersection with reachable at each step enabled. (destroyed/reverse/intersect/total) :0/8/11/19
Computing Next relation with stutter on 1 deadlock states
3 unique states visited
3 strongly connected components in search stack
3 transitions explored
3 items max in DFS search stack
7 ticks for the emptiness check
Model ,|S| ,Time ,Mem(kb) ,fin. SDD ,fin. DDD ,peak SDD ,peak DDD ,SDD Hom ,SDD cache peak ,DDD Hom ,DDD cachepeak ,SHom cache
STATS,0,0.085653,19644,1,0,6790,156,381,8949,125,387,9516
an accepting run exists (use option '-e' to print it)
Formula 0 is FALSE accepting run found.
FORMULA ShieldIIPs-PT-001A-00 FALSE TECHNIQUES DECISION_DIAGRAMS TOPOLOGICAL USE_NUPN
Checking formula 1 : !((G(F("((i4.u3.p8==1)&&(i4.u8.p22==1))"))))
Formula 1 simplified : !GF"((i4.u3.p8==1)&&(i4.u8.p22==1))"
Computing Next relation with stutter on 1 deadlock states
8 unique states visited
8 strongly connected components in search stack
9 transitions explored
8 items max in DFS search stack
2 ticks for the emptiness check
Model ,|S| ,Time ,Mem(kb) ,fin. SDD ,fin. DDD ,peak SDD ,peak DDD ,SDD Hom ,SDD cache peak ,DDD Hom ,DDD cachepeak ,SHom cache
STATS,0,0.107192,20692,1,0,9094,158,447,12124,127,445,13554
an accepting run exists (use option '-e' to print it)
Formula 1 is FALSE accepting run found.
FORMULA ShieldIIPs-PT-001A-01 FALSE TECHNIQUES DECISION_DIAGRAMS TOPOLOGICAL USE_NUPN
Checking formula 2 : !(((((F(G("(((u5.p13!=1)||(i4.u8.p23!=1))||(u9.p27!=1))")))U(G("((i1.u2.p6==1)&&(i1.u6.p17==1))")))U("(((i1.u2.p6==1)&&(i1.u6.p17==1))||((i0.u1.p4==1)&&(i0.u7.p19==1)))"))&&(F("((i0.u1.p4==1)&&(i0.u7.p19==1))"))))
Formula 2 simplified : !(((FG"(((u5.p13!=1)||(i4.u8.p23!=1))||(u9.p27!=1))" U G"((i1.u2.p6==1)&&(i1.u6.p17==1))") U "(((i1.u2.p6==1)&&(i1.u6.p17==1))||((i0.u1.p4==1)&&(i0.u7.p19==1)))") & F"((i0.u1.p4==1)&&(i0.u7.p19==1))")
Computing Next relation with stutter on 1 deadlock states
3 unique states visited
3 strongly connected components in search stack
3 transitions explored
3 items max in DFS search stack
16 ticks for the emptiness check
Model ,|S| ,Time ,Mem(kb) ,fin. SDD ,fin. DDD ,peak SDD ,peak DDD ,SDD Hom ,SDD cache peak ,DDD Hom ,DDD cachepeak ,SHom cache
STATS,0,0.279815,30160,1,0,28975,159,505,31646,130,475,34640
an accepting run exists (use option '-e' to print it)
Formula 2 is FALSE accepting run found.
FORMULA ShieldIIPs-PT-001A-02 FALSE TECHNIQUES DECISION_DIAGRAMS TOPOLOGICAL USE_NUPN
Checking formula 3 : !((G(F(X(F(G(((F("((i2.u0.p1==1)&&(i4.u8.p20==1))"))&&("(i4.u3.p8==1)"))&&("(i4.u8.p22==1)"))))))))
Formula 3 simplified : !GFXFG("(i4.u3.p8==1)" & "(i4.u8.p22==1)" & F"((i2.u0.p1==1)&&(i4.u8.p20==1))")
Computing Next relation with stutter on 1 deadlock states
7 unique states visited
7 strongly connected components in search stack
8 transitions explored
7 items max in DFS search stack
1 ticks for the emptiness check
Model ,|S| ,Time ,Mem(kb) ,fin. SDD ,fin. DDD ,peak SDD ,peak DDD ,SDD Hom ,SDD cache peak ,DDD Hom ,DDD cachepeak ,SHom cache
STATS,0,0.285033,30640,1,0,29319,159,530,32219,132,480,35538
an accepting run exists (use option '-e' to print it)
Formula 3 is FALSE accepting run found.
FORMULA ShieldIIPs-PT-001A-03 FALSE TECHNIQUES DECISION_DIAGRAMS TOPOLOGICAL USE_NUPN
Checking formula 4 : !((F(!(F(X(((F("((i4.u3.p8==1)&&(i4.u8.p22==1))"))||("(i1.u6.p16==1)"))&&("(i1.u6.p16==1)")))))))
Formula 4 simplified : !F!FX("(i1.u6.p16==1)" & ("(i1.u6.p16==1)" | F"((i4.u3.p8==1)&&(i4.u8.p22==1))"))
Computing Next relation with stutter on 1 deadlock states
7 unique states visited
6 strongly connected components in search stack
8 transitions explored
7 items max in DFS search stack
0 ticks for the emptiness check
Model ,|S| ,Time ,Mem(kb) ,fin. SDD ,fin. DDD ,peak SDD ,peak DDD ,SDD Hom ,SDD cache peak ,DDD Hom ,DDD cachepeak ,SHom cache
STATS,0,0.291381,30640,1,0,30042,159,539,33152,132,484,36767
an accepting run exists (use option '-e' to print it)
Formula 4 is FALSE accepting run found.
FORMULA ShieldIIPs-PT-001A-04 FALSE TECHNIQUES DECISION_DIAGRAMS TOPOLOGICAL USE_NUPN
Checking formula 5 : !((!(F(X("(i4.u8.p22==1)")))))
Formula 5 simplified : FX"(i4.u8.p22==1)"
Computing Next relation with stutter on 1 deadlock states
4 unique states visited
4 strongly connected components in search stack
4 transitions explored
4 items max in DFS search stack
1 ticks for the emptiness check
Model ,|S| ,Time ,Mem(kb) ,fin. SDD ,fin. DDD ,peak SDD ,peak DDD ,SDD Hom ,SDD cache peak ,DDD Hom ,DDD cachepeak ,SHom cache
STATS,0,0.294689,30904,1,0,30307,159,550,33486,132,484,37357
an accepting run exists (use option '-e' to print it)
Formula 5 is FALSE accepting run found.
FORMULA ShieldIIPs-PT-001A-05 FALSE TECHNIQUES DECISION_DIAGRAMS TOPOLOGICAL USE_NUPN
Checking formula 6 : !(((F("(((i2.u4.p11==1)&&(i1.u6.p17==1))&&(u9.p26==1))"))U("(((i2.u4.p11==1)&&(i1.u6.p17==1))&&(u9.p26==1))")))
Formula 6 simplified : !(F"(((i2.u4.p11==1)&&(i1.u6.p17==1))&&(u9.p26==1))" U "(((i2.u4.p11==1)&&(i1.u6.p17==1))&&(u9.p26==1))")
Computing Next relation with stutter on 1 deadlock states
2 unique states visited
2 strongly connected components in search stack
2 transitions explored
2 items max in DFS search stack
6 ticks for the emptiness check
Model ,|S| ,Time ,Mem(kb) ,fin. SDD ,fin. DDD ,peak SDD ,peak DDD ,SDD Hom ,SDD cache peak ,DDD Hom ,DDD cachepeak ,SHom cache
STATS,0,0.361461,34600,1,0,39104,159,574,41830,132,484,48579
an accepting run exists (use option '-e' to print it)
Formula 6 is FALSE accepting run found.
FORMULA ShieldIIPs-PT-001A-06 FALSE TECHNIQUES DECISION_DIAGRAMS TOPOLOGICAL USE_NUPN
Checking formula 7 : !(((G(!(X("(((i2.u4.p11==1)&&(i1.u6.p17==1))&&(u9.p26==1))"))))||(F("(u9.p25==1)"))))
Formula 7 simplified : !(G!X"(((i2.u4.p11==1)&&(i1.u6.p17==1))&&(u9.p26==1))" | F"(u9.p25==1)")
Computing Next relation with stutter on 1 deadlock states
4 unique states visited
4 strongly connected components in search stack
4 transitions explored
4 items max in DFS search stack
5 ticks for the emptiness check
Model ,|S| ,Time ,Mem(kb) ,fin. SDD ,fin. DDD ,peak SDD ,peak DDD ,SDD Hom ,SDD cache peak ,DDD Hom ,DDD cachepeak ,SHom cache
STATS,0,0.410648,36708,1,0,44523,159,615,47123,134,485,56094
an accepting run exists (use option '-e' to print it)
Formula 7 is FALSE accepting run found.
FORMULA ShieldIIPs-PT-001A-07 FALSE TECHNIQUES DECISION_DIAGRAMS TOPOLOGICAL USE_NUPN
Checking formula 8 : !((X((G((!(G((((G("(i1.u6.p14==1)"))&&("(i2.u0.p2==1)"))&&("(i2.u4.p10==1)"))&&("(i1.u6.p14==1)"))))||(F("(i1.u6.p14==1)"))))U("((i2.u0.p2==1)&&(i2.u4.p10==1))"))))
Formula 8 simplified : !X(G(!G("(i1.u6.p14==1)" & "(i2.u0.p2==1)" & "(i2.u4.p10==1)" & G"(i1.u6.p14==1)") | F"(i1.u6.p14==1)") U "((i2.u0.p2==1)&&(i2.u4.p10==1))")
Computing Next relation with stutter on 1 deadlock states
2 unique states visited
0 strongly connected components in search stack
1 transitions explored
2 items max in DFS search stack
0 ticks for the emptiness check
Model ,|S| ,Time ,Mem(kb) ,fin. SDD ,fin. DDD ,peak SDD ,peak DDD ,SDD Hom ,SDD cache peak ,DDD Hom ,DDD cachepeak ,SHom cache
STATS,0,0.412878,36972,1,0,44776,159,643,47277,134,485,56765
no accepting run found
Formula 8 is TRUE no accepting run found.
FORMULA ShieldIIPs-PT-001A-08 TRUE TECHNIQUES DECISION_DIAGRAMS TOPOLOGICAL USE_NUPN
Checking formula 9 : !(((G(X(G("(((i2.u4.p11==1)&&(i1.u6.p15==1))&&(u9.p26==1))"))))||(!(X("((i2.u0.p1==1)&&(i4.u8.p20==1))")))))
Formula 9 simplified : !(GXG"(((i2.u4.p11==1)&&(i1.u6.p15==1))&&(u9.p26==1))" | !X"((i2.u0.p1==1)&&(i4.u8.p20==1))")
Computing Next relation with stutter on 1 deadlock states
2 unique states visited
0 strongly connected components in search stack
1 transitions explored
2 items max in DFS search stack
0 ticks for the emptiness check
Model ,|S| ,Time ,Mem(kb) ,fin. SDD ,fin. DDD ,peak SDD ,peak DDD ,SDD Hom ,SDD cache peak ,DDD Hom ,DDD cachepeak ,SHom cache
STATS,0,0.413742,37236,1,0,44776,159,674,47277,134,485,56781
no accepting run found
Formula 9 is TRUE no accepting run found.
FORMULA ShieldIIPs-PT-001A-09 TRUE TECHNIQUES DECISION_DIAGRAMS TOPOLOGICAL USE_NUPN
Checking formula 10 : !((X(G(F((F("(u9.p25==1)"))||((!(F("(u9.p26==1)")))&&(!(X(X("(((u5.p13==1)&&(i4.u8.p23==1))&&(u9.p25==1))"))))))))))
Formula 10 simplified : !XGF(F"(u9.p25==1)" | (!F"(u9.p26==1)" & !XX"(((u5.p13==1)&&(i4.u8.p23==1))&&(u9.p25==1))"))
Computing Next relation with stutter on 1 deadlock states
44 unique states visited
33 strongly connected components in search stack
45 transitions explored
44 items max in DFS search stack
17 ticks for the emptiness check
Model ,|S| ,Time ,Mem(kb) ,fin. SDD ,fin. DDD ,peak SDD ,peak DDD ,SDD Hom ,SDD cache peak ,DDD Hom ,DDD cachepeak ,SHom cache
STATS,0,0.58113,42492,1,0,58238,159,699,61665,138,493,78127
an accepting run exists (use option '-e' to print it)
Formula 10 is FALSE accepting run found.
FORMULA ShieldIIPs-PT-001A-12 FALSE TECHNIQUES DECISION_DIAGRAMS TOPOLOGICAL USE_NUPN
Checking formula 11 : !((X(X(!(F(X((!((X(G("(i1.u6.p15==1)")))U("((i0.u1.p3==1)&&(u9.p24==1))")))&&("((i0.u1.p3!=1)||(u9.p24!=1))"))))))))
Formula 11 simplified : !XX!FX("((i0.u1.p3!=1)||(u9.p24!=1))" & !(XG"(i1.u6.p15==1)" U "((i0.u1.p3==1)&&(u9.p24==1))"))
Computing Next relation with stutter on 1 deadlock states
35 unique states visited
35 strongly connected components in search stack
36 transitions explored
35 items max in DFS search stack
6 ticks for the emptiness check
Model ,|S| ,Time ,Mem(kb) ,fin. SDD ,fin. DDD ,peak SDD ,peak DDD ,SDD Hom ,SDD cache peak ,DDD Hom ,DDD cachepeak ,SHom cache
STATS,0,0.638934,45652,1,0,66426,159,723,69564,138,502,88585
an accepting run exists (use option '-e' to print it)
Formula 11 is FALSE accepting run found.
FORMULA ShieldIIPs-PT-001A-13 FALSE TECHNIQUES DECISION_DIAGRAMS TOPOLOGICAL USE_NUPN
Checking formula 12 : !((G((X(!(F(!((F("(((u5.p13==1)&&(i4.u8.p21==1))&&(u9.p27==1))"))U("(i1.u6.p15!=1)"))))))&&(!(F("(((u5.p13==1)&&(i4.u8.p21==1))&&(u9.p27==1))"))))))
Formula 12 simplified : !G(X!F!(F"(((u5.p13==1)&&(i4.u8.p21==1))&&(u9.p27==1))" U "(i1.u6.p15!=1)") & !F"(((u5.p13==1)&&(i4.u8.p21==1))&&(u9.p27==1))")
Computing Next relation with stutter on 1 deadlock states
8 unique states visited
8 strongly connected components in search stack
9 transitions explored
8 items max in DFS search stack
13 ticks for the emptiness check
Model ,|S| ,Time ,Mem(kb) ,fin. SDD ,fin. DDD ,peak SDD ,peak DDD ,SDD Hom ,SDD cache peak ,DDD Hom ,DDD cachepeak ,SHom cache
STATS,0,0.768548,52244,1,0,81539,159,761,83215,138,506,106525
an accepting run exists (use option '-e' to print it)
Formula 12 is FALSE accepting run found.
FORMULA ShieldIIPs-PT-001A-14 FALSE TECHNIQUES DECISION_DIAGRAMS TOPOLOGICAL USE_NUPN
Checking formula 13 : !(((!(F(X("(((i2.u4.p11==1)&&(i1.u6.p15==1))&&(u9.p26==1))"))))&&((F("((i4.u3.p8!=1)||(i4.u8.p23!=1))"))U(F(("(((i2.u4.p11==1)&&(i1.u6.p15==1))&&(u9.p26==1))")U("((i4.u3.p8==1)&&(i4.u8.p23==1))"))))))
Formula 13 simplified : !(!FX"(((i2.u4.p11==1)&&(i1.u6.p15==1))&&(u9.p26==1))" & (F"((i4.u3.p8!=1)||(i4.u8.p23!=1))" U F("(((i2.u4.p11==1)&&(i1.u6.p15==1))&&(u9.p26==1))" U "((i4.u3.p8==1)&&(i4.u8.p23==1))")))
Computing Next relation with stutter on 1 deadlock states
6 unique states visited
6 strongly connected components in search stack
7 transitions explored
6 items max in DFS search stack
12 ticks for the emptiness check
Model ,|S| ,Time ,Mem(kb) ,fin. SDD ,fin. DDD ,peak SDD ,peak DDD ,SDD Hom ,SDD cache peak ,DDD Hom ,DDD cachepeak ,SHom cache
STATS,0,0.889505,58580,1,0,97063,159,803,96544,138,507,126151
an accepting run exists (use option '-e' to print it)
Formula 13 is FALSE accepting run found.
FORMULA ShieldIIPs-PT-001A-15 FALSE TECHNIQUES DECISION_DIAGRAMS TOPOLOGICAL USE_NUPN
[2020-05-27 06:31:00] [INFO ] Computing symmetric co enabling matrix : 27 transitions.
[2020-05-27 06:31:00] [INFO ] Computation of Finished co-enabling matrix. took 337 ms. Total solver calls (SAT/UNSAT): 161(18/143)
Skipping mayMatrices nes/nds SMT solver raised an error on invariants :(error "Failed to assert expression: java.io.IOException: Stream closed (invariants (select s 2))")
java.lang.RuntimeException: SMT solver raised an error on invariants :(error "Failed to assert expression: java.io.IOException: Stream closed (invariants (select s 2))")
at fr.lip6.move.gal.gal2smt.bmc.KInductionSolver.addKnownInvariants(KInductionSolver.java:460)
at fr.lip6.move.gal.gal2smt.bmc.NecessaryEnablingsolver.computeDoNotAccord(NecessaryEnablingsolver.java:574)
at fr.lip6.move.gal.gal2pins.Gal2PinsTransformerNext.printLabels(Gal2PinsTransformerNext.java:538)
at fr.lip6.move.gal.gal2pins.Gal2PinsTransformerNext.printDependencyMatrix(Gal2PinsTransformerNext.java:209)
at fr.lip6.move.gal.gal2pins.Gal2PinsTransformerNext.buildBodyFile(Gal2PinsTransformerNext.java:85)
at fr.lip6.move.gal.gal2pins.Gal2PinsTransformerNext.transform(Gal2PinsTransformerNext.java:831)
at fr.lip6.move.gal.application.LTSminRunner$1.run(LTSminRunner.java:73)
at java.base/java.lang.Thread.run(Thread.java:834)
[2020-05-27 06:31:00] [INFO ] Built C files in 1741ms conformant to PINS in folder :/home/mcc/execution
Running compilation step : CommandLine [args=[gcc, -c, -I/home/mcc/BenchKit//lts_install_dir//include, -I., -std=c99, -fPIC, -O2, model.c], workingDir=/home/mcc/execution]
WARNING : LTS min runner thread was asked to interrupt. Dying gracefully.
BK_STOP 1590561060800
--------------------
content from stderr:
+ export BINDIR=/home/mcc/BenchKit/
+ BINDIR=/home/mcc/BenchKit/
++ pwd
+ export MODEL=/home/mcc/execution
+ MODEL=/home/mcc/execution
+ [[ LTLFireability = StateSpace ]]
+ /home/mcc/BenchKit//runeclipse.sh /home/mcc/execution LTLFireability -its -ltsminpath /home/mcc/BenchKit//lts_install_dir/ -greatspnpath /home/mcc/BenchKit//greatspn/ -order META -manyOrder -smt -timeout 3600
+ ulimit -s 65536
+ [[ -z '' ]]
+ export LTSMIN_MEM_SIZE=8589934592
+ LTSMIN_MEM_SIZE=8589934592
+ /home/mcc/BenchKit//itstools/its-tools -data /home/mcc/execution/workspace -pnfolder /home/mcc/execution -examination LTLFireability -z3path /home/mcc/BenchKit//z3/bin/z3 -yices2path /home/mcc/BenchKit//yices/bin/yices -its -ltsminpath /home/mcc/BenchKit//lts_install_dir/ -greatspnpath /home/mcc/BenchKit//greatspn/ -order META -manyOrder -smt -timeout 3600 -vmargs -Dosgi.locking=none -Declipse.stateSaveDelayInterval=-1 -Dosgi.configuration.area=/tmp/.eclipse -Xss128m -Xms40m -Xmx16000m -Dfile.encoding=UTF-8 -Dosgi.requiredJavaVersion=1.6
Sequence of Actions to be Executed by the VM
This is useful if one wants to reexecute the tool in the VM from the submitted image disk.
set -x
# this is for BenchKit: configuration of major elements for the test
export BK_INPUT="ShieldIIPs-PT-001A"
export BK_EXAMINATION="LTLFireability"
export BK_TOOL="itstools"
export BK_RESULT_DIR="/tmp/BK_RESULTS/OUTPUTS"
export BK_TIME_CONFINEMENT="3600"
export BK_MEMORY_CONFINEMENT="16384"
# this is specific to your benchmark or test
export BIN_DIR="$HOME/BenchKit/bin"
# remove the execution directoty if it exists (to avoid increse of .vmdk images)
if [ -d execution ] ; then
rm -rf execution
fi
# this is for BenchKit: explicit launching of the test
echo "====================================================================="
echo " Generated by BenchKit 2-4028"
echo " Executing tool itstools"
echo " Input is ShieldIIPs-PT-001A, examination is LTLFireability"
echo " Time confinement is $BK_TIME_CONFINEMENT seconds"
echo " Memory confinement is 16384 MBytes"
echo " Number of cores is 4"
echo " Run identifier is r210-tajo-159033475100042"
echo "====================================================================="
echo
echo "--------------------"
echo "preparation of the directory to be used:"
tar xzf /home/mcc/BenchKit/INPUTS/ShieldIIPs-PT-001A.tgz
mv ShieldIIPs-PT-001A execution
cd execution
if [ "LTLFireability" = "ReachabilityDeadlock" ] || [ "LTLFireability" = "UpperBounds" ] || [ "LTLFireability" = "QuasiLiveness" ] || [ "LTLFireability" = "StableMarking" ] || [ "LTLFireability" = "Liveness" ] || [ "LTLFireability" = "OneSafe" ] || [ "LTLFireability" = "StateSpace" ]; then
rm -f GenericPropertiesVerdict.xml
fi
pwd
ls -lh
echo
echo "--------------------"
echo "content from stdout:"
echo
echo "=== Data for post analysis generated by BenchKit (invocation template)"
echo
if [ "LTLFireability" = "UpperBounds" ] ; then
echo "The expected result is a vector of positive values"
echo NUM_VECTOR
elif [ "LTLFireability" != "StateSpace" ] ; then
echo "The expected result is a vector of booleans"
echo BOOL_VECTOR
else
echo "no data necessary for post analysis"
fi
echo
if [ -f "LTLFireability.txt" ] ; then
echo "here is the order used to build the result vector(from text file)"
for x in $(grep Property LTLFireability.txt | cut -d ' ' -f 2 | sort -u) ; do
echo "FORMULA_NAME $x"
done
elif [ -f "LTLFireability.xml" ] ; then # for cunf (txt files deleted;-)
echo echo "here is the order used to build the result vector(from xml file)"
for x in $(grep '
echo "FORMULA_NAME $x"
done
elif [ "LTLFireability" = "ReachabilityDeadlock" ] || [ "LTLFireability" = "QuasiLiveness" ] || [ "LTLFireability" = "StableMarking" ] || [ "LTLFireability" = "Liveness" ] || [ "LTLFireability" = "OneSafe" ] ; then
echo "FORMULA_NAME LTLFireability"
fi
echo
echo "=== Now, execution of the tool begins"
echo
echo -n "BK_START "
date -u +%s%3N
echo
timeout -s 9 $BK_TIME_CONFINEMENT bash -c "/home/mcc/BenchKit/BenchKit_head.sh 2> STDERR ; echo ; echo -n \"BK_STOP \" ; date -u +%s%3N"
if [ $? -eq 137 ] ; then
echo
echo "BK_TIME_CONFINEMENT_REACHED"
fi
echo
echo "--------------------"
echo "content from stderr:"
echo
cat STDERR ;

