About the Execution of ITS-Tools for QuasiCertifProtocol-COL-02
| Execution Summary | |||||
| Max Memory Used (MB) |
Time wait (ms) | CPU Usage (ms) | I/O Wait (ms) | Computed Result | Execution Status |
| 15756.230 | 36958.00 | 17988.00 | 2004.60 | FFFFFFFFFFFFFFFF | normal |
Execution Chart
We display below the execution chart for this examination (boot time has been removed).
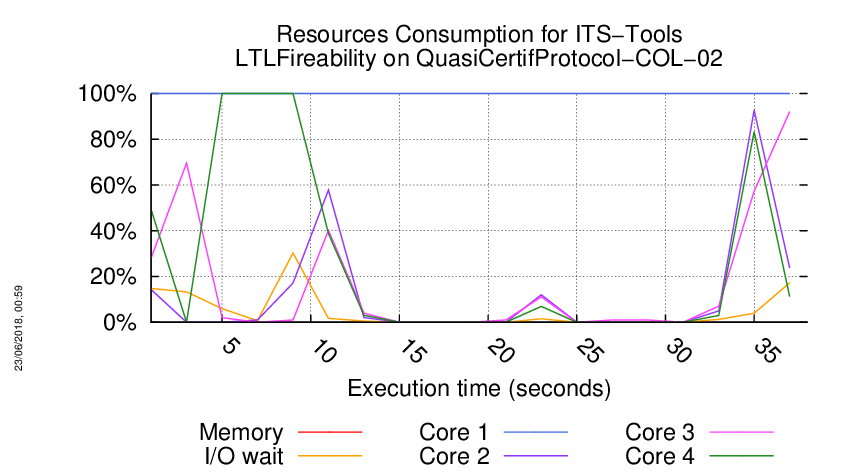
Trace from the execution
Waiting for the VM to be ready (probing ssh)
.........................
/home/mcc/execution
total 204K
-rw-r--r-- 1 mcc users 3.9K May 15 18:54 CTLCardinality.txt
-rw-r--r-- 1 mcc users 22K May 15 18:54 CTLCardinality.xml
-rw-r--r-- 1 mcc users 3.3K May 15 18:54 CTLFireability.txt
-rw-r--r-- 1 mcc users 23K May 15 18:54 CTLFireability.xml
-rw-r--r-- 1 mcc users 4.0K May 15 18:50 GenericPropertiesDefinition.xml
-rw-r--r-- 1 mcc users 6.4K May 15 18:50 GenericPropertiesVerdict.xml
-rw-r--r-- 1 mcc users 2.5K May 26 09:27 LTLCardinality.txt
-rw-r--r-- 1 mcc users 11K May 26 09:27 LTLCardinality.xml
-rw-r--r-- 1 mcc users 2.1K May 26 09:27 LTLFireability.txt
-rw-r--r-- 1 mcc users 9.7K May 26 09:27 LTLFireability.xml
-rw-r--r-- 1 mcc users 3.4K May 15 18:54 ReachabilityCardinality.txt
-rw-r--r-- 1 mcc users 16K May 15 18:54 ReachabilityCardinality.xml
-rw-r--r-- 1 mcc users 117 May 15 18:54 ReachabilityDeadlock.txt
-rw-r--r-- 1 mcc users 355 May 15 18:54 ReachabilityDeadlock.xml
-rw-r--r-- 1 mcc users 2.7K May 15 18:54 ReachabilityFireability.txt
-rw-r--r-- 1 mcc users 14K May 15 18:54 ReachabilityFireability.xml
-rw-r--r-- 1 mcc users 1.8K May 15 18:54 UpperBounds.txt
-rw-r--r-- 1 mcc users 3.8K May 15 18:54 UpperBounds.xml
-rw-r--r-- 1 mcc users 5 May 15 18:50 equiv_pt
-rw-r--r-- 1 mcc users 3 May 15 18:50 instance
-rw-r--r-- 1 mcc users 5 May 15 18:50 iscolored
-rw-r--r-- 1 mcc users 34K May 15 18:50 model.pnml
=====================================================================
Generated by BenchKit 2-3637
Executing tool itstools
Input is QuasiCertifProtocol-COL-02, examination is LTLFireability
Time confinement is 3600 seconds
Memory confinement is 16384 MBytes
Number of cores is 4
Run identifier is r188-qhx2-152732140200042
=====================================================================
--------------------
content from stdout:
=== Data for post analysis generated by BenchKit (invocation template)
The expected result is a vector of booleans
BOOL_VECTOR
here is the order used to build the result vector(from text file)
FORMULA_NAME QuasiCertifProtocol-COL-02-LTLFireability-00
FORMULA_NAME QuasiCertifProtocol-COL-02-LTLFireability-01
FORMULA_NAME QuasiCertifProtocol-COL-02-LTLFireability-02
FORMULA_NAME QuasiCertifProtocol-COL-02-LTLFireability-03
FORMULA_NAME QuasiCertifProtocol-COL-02-LTLFireability-04
FORMULA_NAME QuasiCertifProtocol-COL-02-LTLFireability-05
FORMULA_NAME QuasiCertifProtocol-COL-02-LTLFireability-06
FORMULA_NAME QuasiCertifProtocol-COL-02-LTLFireability-07
FORMULA_NAME QuasiCertifProtocol-COL-02-LTLFireability-08
FORMULA_NAME QuasiCertifProtocol-COL-02-LTLFireability-09
FORMULA_NAME QuasiCertifProtocol-COL-02-LTLFireability-10
FORMULA_NAME QuasiCertifProtocol-COL-02-LTLFireability-11
FORMULA_NAME QuasiCertifProtocol-COL-02-LTLFireability-12
FORMULA_NAME QuasiCertifProtocol-COL-02-LTLFireability-13
FORMULA_NAME QuasiCertifProtocol-COL-02-LTLFireability-14
FORMULA_NAME QuasiCertifProtocol-COL-02-LTLFireability-15
=== Now, execution of the tool begins
BK_START 1528280786854
10:26:59.248 [main] ERROR PNML validation - The rng grammar file can't be accessed : www.pnml.org
10:26:59.252 [main] ERROR import - Grammar file errors have been raised, the validation can't be done, process will continue without Grammar validation
Using solver Z3 to compute partial order matrices.
Built C files in :
/home/mcc/execution
Invoking ITS tools like this :CommandLine [args=[/home/mcc/BenchKit/itstools/plugins/fr.lip6.move.gal.itstools.binaries_1.0.0.201805151631/bin/its-ltl-linux64, --gc-threshold, 2000000, -i, /home/mcc/execution/LTLFireability.pnml.gal, -t, CGAL, -LTL, /home/mcc/execution/LTLFireability.ltl, -c, -stutter-deadlock], workingDir=/home/mcc/execution]
its-ltl command run as :
/home/mcc/BenchKit/itstools/plugins/fr.lip6.move.gal.itstools.binaries_1.0.0.201805151631/bin/its-ltl-linux64 --gc-threshold 2000000 -i /home/mcc/execution/LTLFireability.pnml.gal -t CGAL -LTL /home/mcc/execution/LTLFireability.ltl -c -stutter-deadlock
Read 16 LTL properties
Checking formula 0 : !(((F(F(F("(Astart.Astart_0>=1)"))))U((X("(Astart.Astart_0>=1)"))U(G("(a4.a4_0>=1)")))))
Formula 0 simplified : !(F"(Astart.Astart_0>=1)" U (X"(Astart.Astart_0>=1)" U G"(a4.a4_0>=1)"))
built 25 ordering constraints for composite.
Presburger conditions satisfied. Using coverability to approximate state space in K-Induction.
// Phase 1: matrix 56 rows 86 cols
Reverse transition relation is NOT exact ! Due to transitions malC1, malS6, malS5, malS4, malS3, malS2, malS1, malA5, malA3, malA4, malA2, malA1, Intersection with reachable at each step enabled. (destroyed/reverse/intersect/total) :0/30/12/42
invariant :tsidxtsid7:n8_7 + -1'tsidxtsid8:n8_8 + tsid1:Cstart_1 + -1'tsid2:Cstart_2 = 0
invariant :tsidxtsid5:n9_5 + -1'tsid1:SstopOK_1 + tsid2:CstopOK_2 = 0
invariant :tsidxtsid7:n7_7 + -1'tsidxtsid8:n7_8 + -1'tsid1:Cstart_1 + tsid2:Cstart_2 = 0
invariant :tsidxtsid3:n7_3 + -1'tsidxtsid5:n7_5 + -1'tsid0:Cstart_0 + tsid2:Cstart_2 = 0
invariant :tsidxtsid8:n9_8 + -1'tsid2:SstopOK_2 + tsid2:CstopOK_2 = 0
invariant :tsidxtsid4:n7_4 + -1'tsidxtsid5:n7_5 + -1'tsid1:Cstart_1 + tsid2:Cstart_2 = 0
invariant :tsidxtsid6:n9_6 + tsid0:CstopOK_0 + -1'tsid2:SstopOK_2 = 0
invariant :CstopAbort:CstopAbort_0 + tsid0:c1_0 + tsid0:Cstart_0 + tsid0:CstopOK_0 + tsid1:c1_1 + tsid1:Cstart_1 + tsid1:CstopOK_1 + tsid2:c1_2 + tsid2:Cstart_2 + tsid2:CstopOK_2 = 3
invariant :tsidxtsid4:n9_4 + -1'tsid1:SstopOK_1 + tsid1:CstopOK_1 = 0
invariant :tsid1:n2_1 + tsid1:n1_1 + -1'tsid2:n2_2 + -1'tsid2:n1_2 = 0
invariant :tsidxtsid7:n9_7 + tsid1:CstopOK_1 + -1'tsid2:SstopOK_2 = 0
invariant :tsidxtsid6:n7_6 + -1'tsidxtsid8:n7_8 + -1'tsid0:Cstart_0 + tsid2:Cstart_2 = 0
invariant :tsidxtsid2:n9_2 + -1'tsid0:SstopOK_0 + tsid2:CstopOK_2 = 0
invariant :tsidxtsid3:n8_3 + -1'tsidxtsid5:n8_5 + tsid0:Cstart_0 + -1'tsid2:Cstart_2 = 0
invariant :SstopAbort:SstopAbort_0 + tsid0:Sstart_0 + tsid0:s2_0 + tsid0:s3_0 + tsid0:s4_0 + tsid0:s5_0 + tsid0:s6_0 + tsid0:SstopOK_0 + tsid1:Sstart_1 + tsid1:s2_1 + tsid1:s3_1 + tsid1:s4_1 + tsid1:s5_1 + tsid1:s6_1 + tsid1:SstopOK_1 + tsid2:Sstart_2 + tsid2:s2_2 + tsid2:s3_2 + tsid2:s4_2 + tsid2:s5_2 + tsid2:s6_2 + tsid2:SstopOK_2 = 3
invariant :tsid0:n6_0 + tsid0:n5_0 + -1'tsid2:n6_2 + -1'tsid2:n5_2 = 0
invariant :tsid0:n2_0 + tsid0:n1_0 + -1'tsid2:n2_2 + -1'tsid2:n1_2 = 0
invariant :tsidxtsid0:n9_0 + -1'tsid0:SstopOK_0 + tsid0:CstopOK_0 = 0
invariant :tsid1:n4_1 + tsid1:n3_1 + -1'tsid2:n4_2 + -1'tsid2:n3_2 = 0
invariant :tsidxtsid1:n8_1 + -1'tsidxtsid2:n8_2 + tsid1:Cstart_1 + -1'tsid2:Cstart_2 = 0
Computing Next relation with stutter on 47 deadlock states
invariant :tsidxtsid0:n8_0 + -1'tsidxtsid2:n8_2 + tsid0:Cstart_0 + -1'tsid2:Cstart_2 = 0
invariant :tsidxtsid0:n7_0 + -1'tsidxtsid2:n7_2 + -1'tsid0:Cstart_0 + tsid2:Cstart_2 = 0
invariant :tsidxtsid1:n9_1 + -1'tsid0:SstopOK_0 + tsid1:CstopOK_1 = 0
invariant :tsidxtsid6:n8_6 + -1'tsidxtsid8:n8_8 + tsid0:Cstart_0 + -1'tsid2:Cstart_2 = 0
invariant :tsidxtsid1:n7_1 + -1'tsidxtsid2:n7_2 + -1'tsid1:Cstart_1 + tsid2:Cstart_2 = 0
invariant :malicious_reservoir:malicious_reservoir_0 + -1'tsid0:c1_0 + -1'tsid0:Cstart_0 + -1'tsid0:Sstart_0 + -1'tsid0:s2_0 + -1'tsid0:s3_0 + -1'tsid0:s4_0 + -1'tsid0:s5_0 + -1'tsid0:s6_0 + -1'tsid0:SstopOK_0 + -1'tsid0:CstopOK_0 + -1'tsid1:c1_1 + -1'tsid1:Cstart_1 + -1'tsid1:Sstart_1 + -1'tsid1:s2_1 + -1'tsid1:s3_1 + -1'tsid1:s4_1 + -1'tsid1:s5_1 + -1'tsid1:s6_1 + -1'tsid1:SstopOK_1 + -1'tsid1:CstopOK_1 + -1'tsid2:c1_2 + -1'tsid2:Cstart_2 + -1'tsid2:Sstart_2 + -1'tsid2:s2_2 + -1'tsid2:s3_2 + -1'tsid2:s4_2 + -1'tsid2:s5_2 + -1'tsid2:s6_2 + -1'tsid2:SstopOK_2 + -1'tsid2:CstopOK_2 = -5
invariant :tsid1:n6_1 + tsid1:n5_1 + -1'tsid2:n6_2 + -1'tsid2:n5_2 = 0
invariant :tsidxtsid4:n8_4 + -1'tsidxtsid5:n8_5 + tsid1:Cstart_1 + -1'tsid2:Cstart_2 = 0
invariant :tsidxtsid3:n9_3 + tsid0:CstopOK_0 + -1'tsid1:SstopOK_1 = 0
invariant :AstopAbort:AstopAbort_0 + a5:a5_0 + a4:a4_0 + a3:a3_0 + a2:a2_0 + a1:a1_0 + Astart:Astart_0 + AstopOK:AstopOK_0 = 1
invariant :tsid0:n4_0 + tsid0:n3_0 + -1'tsid2:n4_2 + -1'tsid2:n3_2 = 0
30 unique states visited
30 strongly connected components in search stack
30 transitions explored
30 items max in DFS search stack
51 ticks for the emptiness check
Model ,|S| ,Time ,Mem(kb) ,fin. SDD ,fin. DDD ,peak SDD ,peak DDD ,SDD Hom ,SDD cache peak ,DDD Hom ,DDD cachepeak ,SHom cache
STATS,0,0.636428,27756,1,0,19770,3425,1033,20759,436,19034,67417
an accepting run exists (use option '-e' to print it)
Formula 0 is FALSE accepting run found.
FORMULA QuasiCertifProtocol-COL-02-LTLFireability-00 FALSE TECHNIQUES DECISION_DIAGRAMS TOPOLOGICAL USE_NUPN
Checking formula 1 : !(("(a2.a2_0>=1)"))
Formula 1 simplified : !"(a2.a2_0>=1)"
Computing Next relation with stutter on 47 deadlock states
3 unique states visited
3 strongly connected components in search stack
3 transitions explored
3 items max in DFS search stack
0 ticks for the emptiness check
Model ,|S| ,Time ,Mem(kb) ,fin. SDD ,fin. DDD ,peak SDD ,peak DDD ,SDD Hom ,SDD cache peak ,DDD Hom ,DDD cachepeak ,SHom cache
STATS,0,0.642796,27756,1,0,19885,3425,1038,21084,436,19034,67739
an accepting run exists (use option '-e' to print it)
Formula 1 is FALSE accepting run found.
FORMULA QuasiCertifProtocol-COL-02-LTLFireability-01 FALSE TECHNIQUES DECISION_DIAGRAMS TOPOLOGICAL USE_NUPN
Checking formula 2 : !((G(G(("((((tsid0.Sstart_0>=1)&&(malicious_reservoir.malicious_reservoir_0>=1))||((tsid1.Sstart_1>=1)&&(malicious_reservoir.malicious_reservoir_0>=1)))||((tsid2.Sstart_2>=1)&&(malicious_reservoir.malicious_reservoir_0>=1)))")U(X("(a4.a4_0>=1)"))))))
Formula 2 simplified : !G("((((tsid0.Sstart_0>=1)&&(malicious_reservoir.malicious_reservoir_0>=1))||((tsid1.Sstart_1>=1)&&(malicious_reservoir.malicious_reservoir_0>=1)))||((tsid2.Sstart_2>=1)&&(malicious_reservoir.malicious_reservoir_0>=1)))" U X"(a4.a4_0>=1)")
Computing Next relation with stutter on 47 deadlock states
34 unique states visited
34 strongly connected components in search stack
35 transitions explored
34 items max in DFS search stack
2 ticks for the emptiness check
Model ,|S| ,Time ,Mem(kb) ,fin. SDD ,fin. DDD ,peak SDD ,peak DDD ,SDD Hom ,SDD cache peak ,DDD Hom ,DDD cachepeak ,SHom cache
STATS,0,0.660864,28160,1,0,20070,3425,1057,21343,436,19044,69267
an accepting run exists (use option '-e' to print it)
Formula 2 is FALSE accepting run found.
FORMULA QuasiCertifProtocol-COL-02-LTLFireability-02 FALSE TECHNIQUES DECISION_DIAGRAMS TOPOLOGICAL USE_NUPN
Checking formula 3 : !(("(a2.a2_0>=1)"))
Formula 3 simplified : !"(a2.a2_0>=1)"
Computing Next relation with stutter on 47 deadlock states
3 unique states visited
3 strongly connected components in search stack
3 transitions explored
3 items max in DFS search stack
0 ticks for the emptiness check
Model ,|S| ,Time ,Mem(kb) ,fin. SDD ,fin. DDD ,peak SDD ,peak DDD ,SDD Hom ,SDD cache peak ,DDD Hom ,DDD cachepeak ,SHom cache
STATS,0,0.662547,28160,1,0,20070,3425,1057,21343,436,19044,69267
an accepting run exists (use option '-e' to print it)
Formula 3 is FALSE accepting run found.
FORMULA QuasiCertifProtocol-COL-02-LTLFireability-03 FALSE TECHNIQUES DECISION_DIAGRAMS TOPOLOGICAL USE_NUPN
Checking formula 4 : !(((G(G(X("(a4.a4_0>=1)"))))U(G(F(X("(((tsid0.s6_0>=1)||(tsid1.s6_1>=1))||(tsid2.s6_2>=1))"))))))
Formula 4 simplified : !(GX"(a4.a4_0>=1)" U GFX"(((tsid0.s6_0>=1)||(tsid1.s6_1>=1))||(tsid2.s6_2>=1))")
Computing Next relation with stutter on 47 deadlock states
33 unique states visited
33 strongly connected components in search stack
34 transitions explored
33 items max in DFS search stack
0 ticks for the emptiness check
Model ,|S| ,Time ,Mem(kb) ,fin. SDD ,fin. DDD ,peak SDD ,peak DDD ,SDD Hom ,SDD cache peak ,DDD Hom ,DDD cachepeak ,SHom cache
STATS,0,0.670785,28660,1,0,20070,3425,1082,21343,436,19044,69490
an accepting run exists (use option '-e' to print it)
Formula 4 is FALSE accepting run found.
FORMULA QuasiCertifProtocol-COL-02-LTLFireability-04 FALSE TECHNIQUES DECISION_DIAGRAMS TOPOLOGICAL USE_NUPN
Checking formula 5 : !((F(F((F("((((tsid0.s5_0>=1)&&(malicious_reservoir.malicious_reservoir_0>=1))||((tsid1.s5_1>=1)&&(malicious_reservoir.malicious_reservoir_0>=1)))||((tsid2.s5_2>=1)&&(malicious_reservoir.malicious_reservoir_0>=1)))"))U(X("(a5.a5_0>=1)"))))))
Formula 5 simplified : !F(F"((((tsid0.s5_0>=1)&&(malicious_reservoir.malicious_reservoir_0>=1))||((tsid1.s5_1>=1)&&(malicious_reservoir.malicious_reservoir_0>=1)))||((tsid2.s5_2>=1)&&(malicious_reservoir.malicious_reservoir_0>=1)))" U X"(a5.a5_0>=1)")
Computing Next relation with stutter on 47 deadlock states
3 unique states visited
3 strongly connected components in search stack
3 transitions explored
3 items max in DFS search stack
1 ticks for the emptiness check
Model ,|S| ,Time ,Mem(kb) ,fin. SDD ,fin. DDD ,peak SDD ,peak DDD ,SDD Hom ,SDD cache peak ,DDD Hom ,DDD cachepeak ,SHom cache
STATS,0,0.686111,28660,1,0,20873,3425,1109,22207,436,19044,72090
an accepting run exists (use option '-e' to print it)
Formula 5 is FALSE accepting run found.
FORMULA QuasiCertifProtocol-COL-02-LTLFireability-05 FALSE TECHNIQUES DECISION_DIAGRAMS TOPOLOGICAL USE_NUPN
Checking formula 6 : !((F("((((a1.a1_0>=1)&&(tsid1.n2_1>=1))&&(tsid0.n2_0>=1))&&(tsid2.n2_2>=1))")))
Formula 6 simplified : !F"((((a1.a1_0>=1)&&(tsid1.n2_1>=1))&&(tsid0.n2_0>=1))&&(tsid2.n2_2>=1))"
Computing Next relation with stutter on 47 deadlock states
2 unique states visited
2 strongly connected components in search stack
2 transitions explored
2 items max in DFS search stack
2 ticks for the emptiness check
Model ,|S| ,Time ,Mem(kb) ,fin. SDD ,fin. DDD ,peak SDD ,peak DDD ,SDD Hom ,SDD cache peak ,DDD Hom ,DDD cachepeak ,SHom cache
STATS,0,0.704921,28908,1,0,21686,3435,1148,22984,436,19140,75093
an accepting run exists (use option '-e' to print it)
Formula 6 is FALSE accepting run found.
FORMULA QuasiCertifProtocol-COL-02-LTLFireability-06 FALSE TECHNIQUES DECISION_DIAGRAMS TOPOLOGICAL USE_NUPN
Checking formula 7 : !((G(G("((((malicious_reservoir.malicious_reservoir_0>=1)&&(tsid0.s4_0>=1))||((malicious_reservoir.malicious_reservoir_0>=1)&&(tsid1.s4_1>=1)))||((malicious_reservoir.malicious_reservoir_0>=1)&&(tsid2.s4_2>=1)))"))))
Formula 7 simplified : !G"((((malicious_reservoir.malicious_reservoir_0>=1)&&(tsid0.s4_0>=1))||((malicious_reservoir.malicious_reservoir_0>=1)&&(tsid1.s4_1>=1)))||((malicious_reservoir.malicious_reservoir_0>=1)&&(tsid2.s4_2>=1)))"
Computing Next relation with stutter on 47 deadlock states
3 unique states visited
3 strongly connected components in search stack
3 transitions explored
3 items max in DFS search stack
1 ticks for the emptiness check
Model ,|S| ,Time ,Mem(kb) ,fin. SDD ,fin. DDD ,peak SDD ,peak DDD ,SDD Hom ,SDD cache peak ,DDD Hom ,DDD cachepeak ,SHom cache
STATS,0,0.71035,29172,1,0,21686,3435,1176,22984,436,19140,75124
an accepting run exists (use option '-e' to print it)
Formula 7 is FALSE accepting run found.
FORMULA QuasiCertifProtocol-COL-02-LTLFireability-07 FALSE TECHNIQUES DECISION_DIAGRAMS TOPOLOGICAL USE_NUPN
Checking formula 8 : !((X(X((F("(a4.a4_0>=1)"))U("((((tsid0.s5_0>=1)&&(malicious_reservoir.malicious_reservoir_0>=1))||((tsid1.s5_1>=1)&&(malicious_reservoir.malicious_reservoir_0>=1)))||((tsid2.s5_2>=1)&&(malicious_reservoir.malicious_reservoir_0>=1)))")))))
Formula 8 simplified : !XX(F"(a4.a4_0>=1)" U "((((tsid0.s5_0>=1)&&(malicious_reservoir.malicious_reservoir_0>=1))||((tsid1.s5_1>=1)&&(malicious_reservoir.malicious_reservoir_0>=1)))||((tsid2.s5_2>=1)&&(malicious_reservoir.malicious_reservoir_0>=1)))")
Computing Next relation with stutter on 47 deadlock states
19 unique states visited
19 strongly connected components in search stack
19 transitions explored
19 items max in DFS search stack
19 ticks for the emptiness check
Model ,|S| ,Time ,Mem(kb) ,fin. SDD ,fin. DDD ,peak SDD ,peak DDD ,SDD Hom ,SDD cache peak ,DDD Hom ,DDD cachepeak ,SHom cache
STATS,0,0.90172,31000,1,0,26644,3436,1213,29660,436,19221,89520
an accepting run exists (use option '-e' to print it)
Formula 8 is FALSE accepting run found.
FORMULA QuasiCertifProtocol-COL-02-LTLFireability-08 FALSE TECHNIQUES DECISION_DIAGRAMS TOPOLOGICAL USE_NUPN
Checking formula 9 : !(((G(("((((tsid0.s3_0>=1)&&(malicious_reservoir.malicious_reservoir_0>=1))||((tsid1.s3_1>=1)&&(malicious_reservoir.malicious_reservoir_0>=1)))||((tsid2.s3_2>=1)&&(malicious_reservoir.malicious_reservoir_0>=1)))")U("((((((tsidxtsid2.n8_2>=1)&&(tsidxtsid0.n8_0>=1))&&(tsidxtsid1.n8_1>=1))&&(tsid0.s5_0>=1))||((((tsidxtsid5.n8_5>=1)&&(tsidxtsid3.n8_3>=1))&&(tsidxtsid4.n8_4>=1))&&(tsid1.s5_1>=1)))||((((tsidxtsid8.n8_8>=1)&&(tsidxtsid6.n8_6>=1))&&(tsidxtsid7.n8_7>=1))&&(tsid2.s5_2>=1)))")))U((G("((((tsid0.s2_0>=1)&&(tsid0.n3_0>=1))||((tsid1.s2_1>=1)&&(tsid1.n3_1>=1)))||((tsid2.s2_2>=1)&&(tsid2.n3_2>=1)))"))U("((((malicious_reservoir.malicious_reservoir_0>=1)&&(tsid0.s2_0>=1))||((malicious_reservoir.malicious_reservoir_0>=1)&&(tsid1.s2_1>=1)))||((malicious_reservoir.malicious_reservoir_0>=1)&&(tsid2.s2_2>=1)))"))))
Formula 9 simplified : !(G("((((tsid0.s3_0>=1)&&(malicious_reservoir.malicious_reservoir_0>=1))||((tsid1.s3_1>=1)&&(malicious_reservoir.malicious_reservoir_0>=1)))||((tsid2.s3_2>=1)&&(malicious_reservoir.malicious_reservoir_0>=1)))" U "((((((tsidxtsid2.n8_2>=1)&&(tsidxtsid0.n8_0>=1))&&(tsidxtsid1.n8_1>=1))&&(tsid0.s5_0>=1))||((((tsidxtsid5.n8_5>=1)&&(tsidxtsid3.n8_3>=1))&&(tsidxtsid4.n8_4>=1))&&(tsid1.s5_1>=1)))||((((tsidxtsid8.n8_8>=1)&&(tsidxtsid6.n8_6>=1))&&(tsidxtsid7.n8_7>=1))&&(tsid2.s5_2>=1)))") U (G"((((tsid0.s2_0>=1)&&(tsid0.n3_0>=1))||((tsid1.s2_1>=1)&&(tsid1.n3_1>=1)))||((tsid2.s2_2>=1)&&(tsid2.n3_2>=1)))" U "((((malicious_reservoir.malicious_reservoir_0>=1)&&(tsid0.s2_0>=1))||((malicious_reservoir.malicious_reservoir_0>=1)&&(tsid1.s2_1>=1)))||((malicious_reservoir.malicious_reservoir_0>=1)&&(tsid2.s2_2>=1)))"))
Computing Next relation with stutter on 47 deadlock states
3 unique states visited
3 strongly connected components in search stack
3 transitions explored
3 items max in DFS search stack
2 ticks for the emptiness check
Model ,|S| ,Time ,Mem(kb) ,fin. SDD ,fin. DDD ,peak SDD ,peak DDD ,SDD Hom ,SDD cache peak ,DDD Hom ,DDD cachepeak ,SHom cache
STATS,0,0.938549,32228,1,0,26644,3436,1353,29660,438,19221,89661
an accepting run exists (use option '-e' to print it)
Formula 9 is FALSE accepting run found.
FORMULA QuasiCertifProtocol-COL-02-LTLFireability-09 FALSE TECHNIQUES DECISION_DIAGRAMS TOPOLOGICAL USE_NUPN
Checking formula 10 : !((F(X(X("((((tsid0.c1_0>=1)&&(malicious_reservoir.malicious_reservoir_0>=1))||((tsid1.c1_1>=1)&&(malicious_reservoir.malicious_reservoir_0>=1)))||((tsid2.c1_2>=1)&&(malicious_reservoir.malicious_reservoir_0>=1)))")))))
Formula 10 simplified : !FXX"((((tsid0.c1_0>=1)&&(malicious_reservoir.malicious_reservoir_0>=1))||((tsid1.c1_1>=1)&&(malicious_reservoir.malicious_reservoir_0>=1)))||((tsid2.c1_2>=1)&&(malicious_reservoir.malicious_reservoir_0>=1)))"
Computing Next relation with stutter on 47 deadlock states
4 unique states visited
4 strongly connected components in search stack
4 transitions explored
4 items max in DFS search stack
6 ticks for the emptiness check
Model ,|S| ,Time ,Mem(kb) ,fin. SDD ,fin. DDD ,peak SDD ,peak DDD ,SDD Hom ,SDD cache peak ,DDD Hom ,DDD cachepeak ,SHom cache
STATS,0,1.0106,34076,1,0,31788,3436,1383,33892,438,19221,102593
an accepting run exists (use option '-e' to print it)
Formula 10 is FALSE accepting run found.
FORMULA QuasiCertifProtocol-COL-02-LTLFireability-10 FALSE TECHNIQUES DECISION_DIAGRAMS TOPOLOGICAL USE_NUPN
Checking formula 11 : !((X((X(X("((((malicious_reservoir.malicious_reservoir_0>=1)&&(tsid0.s6_0>=1))||((malicious_reservoir.malicious_reservoir_0>=1)&&(tsid1.s6_1>=1)))||((malicious_reservoir.malicious_reservoir_0>=1)&&(tsid2.s6_2>=1)))")))U(G(G("((((tsid0.s3_0>=1)&&(malicious_reservoir.malicious_reservoir_0>=1))||((tsid1.s3_1>=1)&&(malicious_reservoir.malicious_reservoir_0>=1)))||((tsid2.s3_2>=1)&&(malicious_reservoir.malicious_reservoir_0>=1)))"))))))
Formula 11 simplified : !X(XX"((((malicious_reservoir.malicious_reservoir_0>=1)&&(tsid0.s6_0>=1))||((malicious_reservoir.malicious_reservoir_0>=1)&&(tsid1.s6_1>=1)))||((malicious_reservoir.malicious_reservoir_0>=1)&&(tsid2.s6_2>=1)))" U G"((((tsid0.s3_0>=1)&&(malicious_reservoir.malicious_reservoir_0>=1))||((tsid1.s3_1>=1)&&(malicious_reservoir.malicious_reservoir_0>=1)))||((tsid2.s3_2>=1)&&(malicious_reservoir.malicious_reservoir_0>=1)))")
Computing Next relation with stutter on 47 deadlock states
24 unique states visited
24 strongly connected components in search stack
24 transitions explored
24 items max in DFS search stack
6 ticks for the emptiness check
Model ,|S| ,Time ,Mem(kb) ,fin. SDD ,fin. DDD ,peak SDD ,peak DDD ,SDD Hom ,SDD cache peak ,DDD Hom ,DDD cachepeak ,SHom cache
STATS,0,1.0759,35128,1,0,33645,3441,1394,36433,438,19356,109142
an accepting run exists (use option '-e' to print it)
Formula 11 is FALSE accepting run found.
FORMULA QuasiCertifProtocol-COL-02-LTLFireability-11 FALSE TECHNIQUES DECISION_DIAGRAMS TOPOLOGICAL USE_NUPN
Checking formula 12 : !((X("(a3.a3_0>=1)")))
Formula 12 simplified : !X"(a3.a3_0>=1)"
Computing Next relation with stutter on 47 deadlock states
4 unique states visited
4 strongly connected components in search stack
4 transitions explored
4 items max in DFS search stack
0 ticks for the emptiness check
Model ,|S| ,Time ,Mem(kb) ,fin. SDD ,fin. DDD ,peak SDD ,peak DDD ,SDD Hom ,SDD cache peak ,DDD Hom ,DDD cachepeak ,SHom cache
STATS,0,1.07901,35128,1,0,33645,3441,1397,36433,438,19356,109157
an accepting run exists (use option '-e' to print it)
Formula 12 is FALSE accepting run found.
FORMULA QuasiCertifProtocol-COL-02-LTLFireability-12 FALSE TECHNIQUES DECISION_DIAGRAMS TOPOLOGICAL USE_NUPN
Checking formula 13 : !((G("(a3.a3_0>=1)")))
Formula 13 simplified : !G"(a3.a3_0>=1)"
Computing Next relation with stutter on 47 deadlock states
3 unique states visited
3 strongly connected components in search stack
3 transitions explored
3 items max in DFS search stack
1 ticks for the emptiness check
Model ,|S| ,Time ,Mem(kb) ,fin. SDD ,fin. DDD ,peak SDD ,peak DDD ,SDD Hom ,SDD cache peak ,DDD Hom ,DDD cachepeak ,SHom cache
STATS,0,1.0822,35392,1,0,33645,3441,1410,36433,438,19356,109177
an accepting run exists (use option '-e' to print it)
Formula 13 is FALSE accepting run found.
FORMULA QuasiCertifProtocol-COL-02-LTLFireability-13 FALSE TECHNIQUES DECISION_DIAGRAMS TOPOLOGICAL USE_NUPN
Checking formula 14 : !(((G(X(G("(((tsid0.s6_0>=1)||(tsid1.s6_1>=1))||(tsid2.s6_2>=1))"))))U(G("((((tsid0.Sstart_0>=1)&&(malicious_reservoir.malicious_reservoir_0>=1))||((tsid1.Sstart_1>=1)&&(malicious_reservoir.malicious_reservoir_0>=1)))||((tsid2.Sstart_2>=1)&&(malicious_reservoir.malicious_reservoir_0>=1)))"))))
Formula 14 simplified : !(GXG"(((tsid0.s6_0>=1)||(tsid1.s6_1>=1))||(tsid2.s6_2>=1))" U G"((((tsid0.Sstart_0>=1)&&(malicious_reservoir.malicious_reservoir_0>=1))||((tsid1.Sstart_1>=1)&&(malicious_reservoir.malicious_reservoir_0>=1)))||((tsid2.Sstart_2>=1)&&(malicious_reservoir.malicious_reservoir_0>=1)))")
Computing Next relation with stutter on 47 deadlock states
27 unique states visited
27 strongly connected components in search stack
27 transitions explored
27 items max in DFS search stack
2 ticks for the emptiness check
Model ,|S| ,Time ,Mem(kb) ,fin. SDD ,fin. DDD ,peak SDD ,peak DDD ,SDD Hom ,SDD cache peak ,DDD Hom ,DDD cachepeak ,SHom cache
STATS,0,1.10702,35392,1,0,34122,3441,1432,37241,438,19372,110961
an accepting run exists (use option '-e' to print it)
Formula 14 is FALSE accepting run found.
FORMULA QuasiCertifProtocol-COL-02-LTLFireability-14 FALSE TECHNIQUES DECISION_DIAGRAMS TOPOLOGICAL USE_NUPN
Checking formula 15 : !((F(X((X("(((tsid0.s4_0>=1)||(tsid1.s4_1>=1))||(tsid2.s4_2>=1))"))U(X("((((((tsidxtsid0.n9_0>=1)&&(tsidxtsid3.n9_3>=1))&&(tsidxtsid6.n9_6>=1))&&(tsid0.c1_0>=1))||((((tsidxtsid1.n9_1>=1)&&(tsidxtsid4.n9_4>=1))&&(tsidxtsid7.n9_7>=1))&&(tsid1.c1_1>=1)))||((((tsidxtsid2.n9_2>=1)&&(tsidxtsid5.n9_5>=1))&&(tsidxtsid8.n9_8>=1))&&(tsid2.c1_2>=1)))"))))))
Formula 15 simplified : !FX(X"(((tsid0.s4_0>=1)||(tsid1.s4_1>=1))||(tsid2.s4_2>=1))" U X"((((((tsidxtsid0.n9_0>=1)&&(tsidxtsid3.n9_3>=1))&&(tsidxtsid6.n9_6>=1))&&(tsid0.c1_0>=1))||((((tsidxtsid1.n9_1>=1)&&(tsidxtsid4.n9_4>=1))&&(tsidxtsid7.n9_7>=1))&&(tsid1.c1_1>=1)))||((((tsidxtsid2.n9_2>=1)&&(tsidxtsid5.n9_5>=1))&&(tsidxtsid8.n9_8>=1))&&(tsid2.c1_2>=1)))")
Computing Next relation with stutter on 47 deadlock states
4 unique states visited
4 strongly connected components in search stack
4 transitions explored
4 items max in DFS search stack
8 ticks for the emptiness check
Model ,|S| ,Time ,Mem(kb) ,fin. SDD ,fin. DDD ,peak SDD ,peak DDD ,SDD Hom ,SDD cache peak ,DDD Hom ,DDD cachepeak ,SHom cache
STATS,0,1.18791,37504,1,0,39153,3441,1481,41237,438,19372,130022
an accepting run exists (use option '-e' to print it)
Formula 15 is FALSE accepting run found.
FORMULA QuasiCertifProtocol-COL-02-LTLFireability-15 FALSE TECHNIQUES DECISION_DIAGRAMS TOPOLOGICAL USE_NUPN
Running compilation step : CommandLine [args=[gcc, -c, -I/home/mcc/BenchKit//lts_install_dir//include, -I., -std=c99, -fPIC, -O3, model.c], workingDir=/home/mcc/execution]
WARNING : LTS min runner thread was asked to interrupt. Dying gracefully.
BK_STOP 1528280823812
--------------------
content from stderr:
+ export BINDIR=/home/mcc/BenchKit/
+ BINDIR=/home/mcc/BenchKit/
++ pwd
+ export MODEL=/home/mcc/execution
+ MODEL=/home/mcc/execution
+ /home/mcc/BenchKit//runeclipse.sh /home/mcc/execution LTLFireability -its -ltsminpath /home/mcc/BenchKit//lts_install_dir/ -smt
+ ulimit -s 65536
+ [[ -z '' ]]
+ export LTSMIN_MEM_SIZE=8589934592
+ LTSMIN_MEM_SIZE=8589934592
+ /home/mcc/BenchKit//itstools/its-tools -consoleLog -data /home/mcc/execution/workspace -pnfolder /home/mcc/execution -examination LTLFireability -z3path /home/mcc/BenchKit//z3/bin/z3 -yices2path /home/mcc/BenchKit//yices/bin/yices -its -ltsminpath /home/mcc/BenchKit//lts_install_dir/ -smt -vmargs -Dosgi.locking=none -Declipse.stateSaveDelayInterval=-1 -Dosgi.configuration.area=/tmp/.eclipse -Xss8m -Xms40m -Xmx8192m -Dfile.encoding=UTF-8 -Dosgi.requiredJavaVersion=1.6
Jun 06, 2018 10:26:38 AM fr.lip6.move.gal.application.Application start
INFO: Running its-tools with arguments : [-pnfolder, /home/mcc/execution, -examination, LTLFireability, -z3path, /home/mcc/BenchKit//z3/bin/z3, -yices2path, /home/mcc/BenchKit//yices/bin/yices, -its, -ltsminpath, /home/mcc/BenchKit//lts_install_dir/, -smt]
Jun 06, 2018 10:26:38 AM fr.lip6.move.gal.application.MccTranslator transformPNML
INFO: Parsing pnml file : /home/mcc/execution/model.pnml
Jun 06, 2018 10:26:38 AM fr.lip6.move.gal.pnml.togal.PnmlToGalTransformer transform
INFO: Detected file is not PT type :http://www.pnml.org/version-2009/grammar/symmetricnet
Jun 06, 2018 10:26:59 AM fr.lip6.move.gal.pnml.togal.PnmlToGalTransformer transform
INFO: Load time of PNML (colored model parsed with PNMLFW) : 21292 ms
Jun 06, 2018 10:26:59 AM fr.lip6.move.gal.pnml.togal.HLGALTransformer handlePage
INFO: Transformed 30 places.
Jun 06, 2018 10:26:59 AM fr.lip6.move.gal.pnml.togal.HLGALTransformer handlePage
INFO: Computed order using colors.
Jun 06, 2018 10:26:59 AM fr.lip6.move.gal.pnml.togal.HLGALTransformer handlePage
INFO: sort/places :tsidxtsid->n9,n8,n7,
Dot->malicious_reservoir,CstopAbort,SstopAbort,AstopAbort,a5,a4,a3,a2,a1,Astart,AstopOK,
tsid->n6,n5,n4,n3,n2,n1,c1,Cstart,Sstart,s2,s3,s4,s5,s6,SstopOK,CstopOK,
Jun 06, 2018 10:26:59 AM fr.lip6.move.gal.pnml.togal.HLGALTransformer handlePage
INFO: Transformed 26 transitions.
Jun 06, 2018 10:26:59 AM fr.lip6.move.gal.pnml.togal.PnmlToGalTransformer transform
INFO: Computed order based on color domains.
Jun 06, 2018 10:26:59 AM fr.lip6.move.serialization.SerializationUtil systemToFile
INFO: Time to serialize gal into /home/mcc/execution/model.pnml.img.gal : 11 ms
Jun 06, 2018 10:27:00 AM fr.lip6.move.gal.application.MccTranslator applyOrder
INFO: Applying decomposition
Jun 06, 2018 10:27:00 AM fr.lip6.move.gal.instantiate.CompositeBuilder decomposeWithOrder
INFO: Decomposing Gal with order
Jun 06, 2018 10:27:00 AM fr.lip6.move.gal.instantiate.GALRewriter flatten
INFO: Flatten gal took : 85 ms
Jun 06, 2018 10:27:00 AM fr.lip6.move.gal.instantiate.CompositeBuilder rewriteArraysToAllowPartition
INFO: Rewriting arrays n9, n8, n7, n6, n5, n4, n3, n2, n1, c1, Cstart, Sstart, s2, s3, s4, s5, s6, SstopOK, CstopOK to variables to allow decomposition.
Jun 06, 2018 10:27:00 AM fr.lip6.move.gal.instantiate.Instantiator fuseIsomorphicEffects
INFO: Removed a total of 20 redundant transitions.
Jun 06, 2018 10:27:01 AM fr.lip6.move.serialization.SerializationUtil systemToFile
INFO: Time to serialize gal into /home/mcc/execution/LTLFireability.pnml.gal : 9 ms
Jun 06, 2018 10:27:01 AM fr.lip6.move.serialization.SerializationUtil serializePropertiesForITSLTLTools
INFO: Time to serialize properties into /home/mcc/execution/LTLFireability.ltl : 2 ms
Jun 06, 2018 10:27:01 AM fr.lip6.move.gal.semantics.DeterministicNextBuilder getDeterministicNext
INFO: Input system was not deterministic with 42 transitions. Expanding to a total of 63 deterministic transitions.
Jun 06, 2018 10:27:01 AM fr.lip6.move.gal.semantics.DeterministicNextBuilder getDeterministicNext
INFO: Determinization took 5 ms.
Jun 06, 2018 10:27:01 AM fr.lip6.move.gal.gal2smt.bmc.KInductionSolver computeAndDeclareInvariants
INFO: Computed 31 place invariants in 40 ms
Jun 06, 2018 10:27:02 AM fr.lip6.move.gal.gal2smt.bmc.KInductionSolver init
INFO: Proved 86 variables to be positive in 372 ms
Jun 06, 2018 10:27:02 AM fr.lip6.move.gal.gal2smt.bmc.NecessaryEnablingsolver computeAblingMatrix
INFO: Computing symmetric may disable matrix : 56 transitions.
Jun 06, 2018 10:27:02 AM fr.lip6.move.gal.gal2smt.bmc.NecessaryEnablingsolver printStats
INFO: Computation of disable matrix completed :0/56 took 0 ms. Total solver calls (SAT/UNSAT): 0(0/0)
Jun 06, 2018 10:27:02 AM fr.lip6.move.gal.gal2smt.bmc.NecessaryEnablingsolver printStats
INFO: Computation of Complete disable matrix. took 3 ms. Total solver calls (SAT/UNSAT): 0(0/0)
Jun 06, 2018 10:27:02 AM fr.lip6.move.gal.gal2smt.bmc.NecessaryEnablingsolver computeAblingMatrix
INFO: Computing symmetric may enable matrix : 56 transitions.
Jun 06, 2018 10:27:02 AM fr.lip6.move.gal.gal2smt.bmc.NecessaryEnablingsolver printStats
INFO: Computation of Complete enable matrix. took 2 ms. Total solver calls (SAT/UNSAT): 0(0/0)
Skipping mayMatrices nes/nds Could not set logic :(error "Error writing to Z3 solver: java.io.IOException: Broken pipe")
java.lang.RuntimeException: Could not set logic :(error "Error writing to Z3 solver: java.io.IOException: Broken pipe")
at fr.lip6.move.gal.gal2smt.bmc.NecessaryEnablingsolver.buildSolver(NecessaryEnablingsolver.java:104)
at fr.lip6.move.gal.gal2smt.bmc.NecessaryEnablingsolver.computeAblingForPredicate(NecessaryEnablingsolver.java:660)
at fr.lip6.move.gal.gal2pins.Gal2PinsTransformerNext.printLabels(Gal2PinsTransformerNext.java:502)
at fr.lip6.move.gal.gal2pins.Gal2PinsTransformerNext.printDependencyMatrix(Gal2PinsTransformerNext.java:209)
at fr.lip6.move.gal.gal2pins.Gal2PinsTransformerNext.buildBodyFile(Gal2PinsTransformerNext.java:85)
at fr.lip6.move.gal.gal2pins.Gal2PinsTransformerNext.transform(Gal2PinsTransformerNext.java:830)
at fr.lip6.move.gal.application.LTSminRunner$1.run(LTSminRunner.java:71)
at java.lang.Thread.run(Thread.java:748)
Jun 06, 2018 10:27:02 AM fr.lip6.move.gal.gal2pins.Gal2PinsTransformerNext transform
INFO: Built C files in 1462ms conformant to PINS in folder :/home/mcc/execution
Sequence of Actions to be Executed by the VM
This is useful if one wants to reexecute the tool in the VM from the submitted image disk.
set -x
# this is for BenchKit: configuration of major elements for the test
export BK_INPUT="QuasiCertifProtocol-COL-02"
export BK_EXAMINATION="LTLFireability"
export BK_TOOL="itstools"
export BK_RESULT_DIR="/tmp/BK_RESULTS/OUTPUTS"
export BK_TIME_CONFINEMENT="3600"
export BK_MEMORY_CONFINEMENT="16384"
# this is specific to your benchmark or test
export BIN_DIR="$HOME/BenchKit/bin"
# remove the execution directoty if it exists (to avoid increse of .vmdk images)
if [ -d execution ] ; then
rm -rf execution
fi
tar xzf /home/mcc/BenchKit/INPUTS/QuasiCertifProtocol-COL-02.tgz
mv QuasiCertifProtocol-COL-02 execution
cd execution
pwd
ls -lh
# this is for BenchKit: explicit launching of the test
echo "====================================================================="
echo " Generated by BenchKit 2-3637"
echo " Executing tool itstools"
echo " Input is QuasiCertifProtocol-COL-02, examination is LTLFireability"
echo " Time confinement is $BK_TIME_CONFINEMENT seconds"
echo " Memory confinement is 16384 MBytes"
echo " Number of cores is 4"
echo " Run identifier is r188-qhx2-152732140200042"
echo "====================================================================="
echo
echo "--------------------"
echo "content from stdout:"
echo
echo "=== Data for post analysis generated by BenchKit (invocation template)"
echo
if [ "LTLFireability" = "UpperBounds" ] ; then
echo "The expected result is a vector of positive values"
echo NUM_VECTOR
elif [ "LTLFireability" != "StateSpace" ] ; then
echo "The expected result is a vector of booleans"
echo BOOL_VECTOR
else
echo "no data necessary for post analysis"
fi
echo
if [ -f "LTLFireability.txt" ] ; then
echo "here is the order used to build the result vector(from text file)"
for x in $(grep Property LTLFireability.txt | cut -d ' ' -f 2 | sort -u) ; do
echo "FORMULA_NAME $x"
done
elif [ -f "LTLFireability.xml" ] ; then # for cunf (txt files deleted;-)
echo echo "here is the order used to build the result vector(from xml file)"
for x in $(grep '
echo "FORMULA_NAME $x"
done
fi
echo
echo "=== Now, execution of the tool begins"
echo
echo -n "BK_START "
date -u +%s%3N
echo
timeout -s 9 $BK_TIME_CONFINEMENT bash -c "/home/mcc/BenchKit/BenchKit_head.sh 2> STDERR ; echo ; echo -n \"BK_STOP \" ; date -u +%s%3N"
if [ $? -eq 137 ] ; then
echo
echo "BK_TIME_CONFINEMENT_REACHED"
fi
echo
echo "--------------------"
echo "content from stderr:"
echo
cat STDERR ;

