About the Execution of Irma.struct for QuasiCertifProtocol-COL-02
| Execution Summary | |||||
| Max Memory Used (MB) |
Time wait (ms) | CPU Usage (ms) | I/O Wait (ms) | Computed Result | Execution Status |
| 426.210 | 49924.00 | 14887.00 | 1176.60 | TFTFTFFTTFTTTTFF | normal |
Execution Chart
We display below the execution chart for this examination (boot time has been removed).
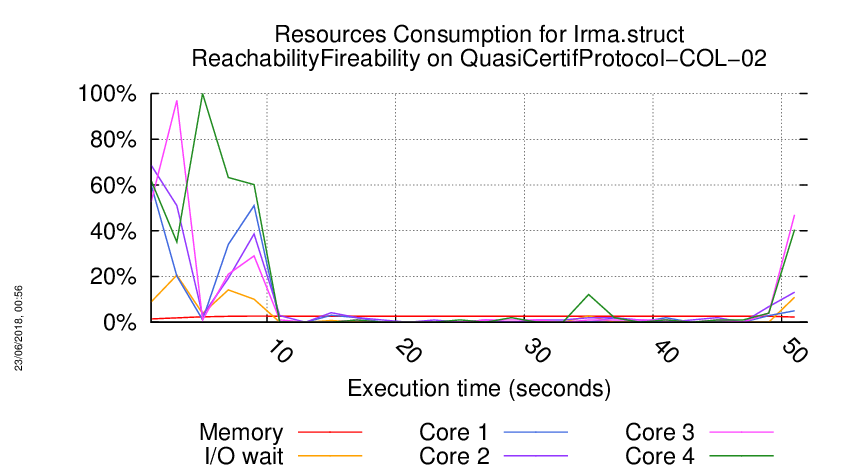
Trace from the execution
Waiting for the VM to be ready (probing ssh)
.........................
/home/mcc/execution
total 204K
-rw-r--r-- 1 mcc users 3.9K May 15 18:54 CTLCardinality.txt
-rw-r--r-- 1 mcc users 22K May 15 18:54 CTLCardinality.xml
-rw-r--r-- 1 mcc users 3.3K May 15 18:54 CTLFireability.txt
-rw-r--r-- 1 mcc users 23K May 15 18:54 CTLFireability.xml
-rw-r--r-- 1 mcc users 4.0K May 15 18:50 GenericPropertiesDefinition.xml
-rw-r--r-- 1 mcc users 6.4K May 15 18:50 GenericPropertiesVerdict.xml
-rw-r--r-- 1 mcc users 2.5K May 26 09:27 LTLCardinality.txt
-rw-r--r-- 1 mcc users 11K May 26 09:27 LTLCardinality.xml
-rw-r--r-- 1 mcc users 2.1K May 26 09:27 LTLFireability.txt
-rw-r--r-- 1 mcc users 9.7K May 26 09:27 LTLFireability.xml
-rw-r--r-- 1 mcc users 3.4K May 15 18:54 ReachabilityCardinality.txt
-rw-r--r-- 1 mcc users 16K May 15 18:54 ReachabilityCardinality.xml
-rw-r--r-- 1 mcc users 117 May 15 18:54 ReachabilityDeadlock.txt
-rw-r--r-- 1 mcc users 355 May 15 18:54 ReachabilityDeadlock.xml
-rw-r--r-- 1 mcc users 2.7K May 15 18:54 ReachabilityFireability.txt
-rw-r--r-- 1 mcc users 14K May 15 18:54 ReachabilityFireability.xml
-rw-r--r-- 1 mcc users 1.8K May 15 18:54 UpperBounds.txt
-rw-r--r-- 1 mcc users 3.8K May 15 18:54 UpperBounds.xml
-rw-r--r-- 1 mcc users 5 May 15 18:50 equiv_pt
-rw-r--r-- 1 mcc users 3 May 15 18:50 instance
-rw-r--r-- 1 mcc users 5 May 15 18:50 iscolored
-rw-r--r-- 1 mcc users 34K May 15 18:50 model.pnml
=====================================================================
Generated by BenchKit 2-3637
Executing tool irma4mcc-structural
Input is QuasiCertifProtocol-COL-02, examination is ReachabilityFireability
Time confinement is 3600 seconds
Memory confinement is 16384 MBytes
Number of cores is 4
Run identifier is r139-qhx2-152673581100014
=====================================================================
--------------------
content from stdout:
=== Data for post analysis generated by BenchKit (invocation template)
The expected result is a vector of booleans
BOOL_VECTOR
here is the order used to build the result vector(from text file)
FORMULA_NAME QuasiCertifProtocol-COL-02-ReachabilityFireability-00
FORMULA_NAME QuasiCertifProtocol-COL-02-ReachabilityFireability-01
FORMULA_NAME QuasiCertifProtocol-COL-02-ReachabilityFireability-02
FORMULA_NAME QuasiCertifProtocol-COL-02-ReachabilityFireability-03
FORMULA_NAME QuasiCertifProtocol-COL-02-ReachabilityFireability-04
FORMULA_NAME QuasiCertifProtocol-COL-02-ReachabilityFireability-05
FORMULA_NAME QuasiCertifProtocol-COL-02-ReachabilityFireability-06
FORMULA_NAME QuasiCertifProtocol-COL-02-ReachabilityFireability-07
FORMULA_NAME QuasiCertifProtocol-COL-02-ReachabilityFireability-08
FORMULA_NAME QuasiCertifProtocol-COL-02-ReachabilityFireability-09
FORMULA_NAME QuasiCertifProtocol-COL-02-ReachabilityFireability-10
FORMULA_NAME QuasiCertifProtocol-COL-02-ReachabilityFireability-11
FORMULA_NAME QuasiCertifProtocol-COL-02-ReachabilityFireability-12
FORMULA_NAME QuasiCertifProtocol-COL-02-ReachabilityFireability-13
FORMULA_NAME QuasiCertifProtocol-COL-02-ReachabilityFireability-14
FORMULA_NAME QuasiCertifProtocol-COL-02-ReachabilityFireability-15
=== Now, execution of the tool begins
BK_START 1527780761288
BK_STOP 1527780811212
--------------------
content from stderr:
Prefix is 75f5f979.
Reading known information in /usr/share/mcc4mcc/75f5f979-known.json.
Reading learned information in /usr/share/mcc4mcc/75f5f979-learned.json.
Reading value translations in /usr/share/mcc4mcc/75f5f979-values.json.
Using directory /home/mcc/execution for input, as it contains a model.pnml file.
Using QuasiCertifProtocol-COL-02 as instance name.
Using QuasiCertifProtocol as model name.
Using algorithm or tool decision-tree.
Model characteristics are: {'Examination': 'ReachabilityFireability', 'Place/Transition': True, 'Colored': True, 'Relative-Time': 1, 'Relative-Memory': 1, 'Ordinary': True, 'Simple Free Choice': False, 'Extended Free Choice': False, 'State Machine': False, 'Marked Graph': False, 'Connected': True, 'Strongly Connected': False, 'Source Place': True, 'Sink Place': True, 'Source Transition': False, 'Sink Transition': False, 'Loop Free': True, 'Conservative': False, 'Sub-Conservative': False, 'Nested Units': False, 'Safe': False, 'Deadlock': True, 'Reversible': False, 'Quasi Live': None, 'Live': False}.
Known tools are: [{'Time': 143, 'Memory': 108.6, 'Tool': 'lola'}, {'Time': 196, 'Memory': 107.94, 'Tool': 'lola'}, {'Time': 632, 'Memory': 100.5, 'Tool': 'gspn'}, {'Time': 2612, 'Memory': 163.93, 'Tool': 'gspn'}, {'Time': 4309, 'Memory': 2228.5, 'Tool': 'marcie'}, {'Time': 4452, 'Memory': 2228.57, 'Tool': 'marcie'}, {'Time': 6638, 'Memory': 350.84, 'Tool': 'itstools'}, {'Time': 6679, 'Memory': 339.33, 'Tool': 'itstools'}].
Learned tools are: [{'Tool': 'lola'}].
Learned tool lola is 1.0x far from the best tool lola.
ReachabilityFireability lola QuasiCertifProtocol-COL-02...
Time: 3600 - MCC
----- Start make prepare stdout -----
----- Start make prepare stderr -----
===========================================================================================
QuasiCertifProtocol-COL-02: translating COL Petri net model.pnml into LoLA format
===========================================================================================
translating COL Petri net complete
checking for too many tokens
===========================================================================================
QuasiCertifProtocol-COL-02: translating COL formula ReachabilityFireability into LoLA format
===========================================================================================
translating formula complete
----- Start make result stdout -----
----- Start make result stderr -----
ReachabilityFireability @ QuasiCertifProtocol-COL-02 @ 3540 seconds
----- Start make result stdout -----
----- Start make result stderr -----
lola: LoLA will run for 3540 seconds at most (--timelimit)
lola: NET
lola: reading net from model.pnml.lola
lola: finished parsing
lola: closed net file model.pnml.lola
lola: 142/65536 symbol table entries, 0 collisions
lola: preprocessing...
lola: finding significant places
lola: 86 places, 56 transitions, 55 significant places
lola: computing forward-conflicting sets
lola: computing back-conflicting sets
lola: 71 transition conflict sets
lola: TASK
lola: reading formula from QuasiCertifProtocol-COL-02-ReachabilityFireability.task
lola: E (F ((FIREABLE(t34) OR FIREABLE(t33) OR FIREABLE(t32)))) : A (G ((FIREABLE(t9) OR (NOT FIREABLE(t50) AND NOT FIREABLE(t49) AND NOT FIREABLE(t48) AND NOT FIREABLE(t40)) OR FIREABLE(t34) OR FIREABLE(t33) OR FIREABLE(t32) OR FIREABLE(t0)))) : E (F ((FIREABLE(t25) OR FIREABLE(t24) OR FIREABLE(t23)))) : A (G ((FIREABLE(t47) OR FIREABLE(t46) OR FIREABLE(t45)))) : A (G ((NOT FIREABLE(t52) OR (NOT FIREABLE(t34) AND NOT FIREABLE(t33) AND NOT FIREABLE(t32) AND ((NOT FIREABLE(t47) AND NOT FIREABLE(t46) AND NOT FIREABLE(t45)) OR NOT FIREABLE(t35)))))) : E (F (((FIREABLE(t5) OR FIREABLE(t4) OR FIREABLE(t3)) AND (FIREABLE(t34) OR FIREABLE(t33) OR FIREABLE(t32) OR (FIREABLE(t22) AND (FIREABLE(t47) OR FIREABLE(t46) OR FIREABLE(t45)) AND FIREABLE(t2) AND FIREABLE(t52)))))) : A (G ((NOT FIREABLE(t39) AND NOT FIREABLE(t38) AND NOT FIREABLE(t37) AND NOT FIREABLE(t39) AND NOT FIREABLE(t38) AND NOT FIREABLE(t37) AND NOT FIREABLE(t28) AND NOT FIREABLE(t27) AND NOT FIREABLE(t26) AND NOT FIREABLE(t0)))) : E (F ((FIREABLE(t55) OR FIREABLE(t54) OR FIREABLE(t53)))) : E (F (((NOT FIREABLE(t47) AND NOT FIREABLE(t46) AND NOT FIREABLE(t45)) OR (FIREABLE(t0) AND FIREABLE(t9))))) : E (F ((NOT FIREABLE(t39) AND NOT FIREABLE(t38) AND NOT FIREABLE(t37) AND (FIREABLE(t34) OR FIREABLE(t33) OR FIREABLE(t32)) AND FIREABLE(t36) AND (FIREABLE(t47) OR FIREABLE(t46) OR FIREABLE(t45) OR (FIREABLE(t51) AND (FIREABLE(t18) OR FIREABLE(t17) OR FIREABLE(t16))))))) : A (G ((FIREABLE(t39) OR FIREABLE(t38) OR FIREABLE(t37) OR FIREABLE(t1) OR FIREABLE(t21) OR FIREABLE(t20) OR FIREABLE(t19) OR FIREABLE(t21) OR FIREABLE(t20) OR FIREABLE(t19) OR FIREABLE(t22) OR FIREABLE(t47) OR FIREABLE(t46) OR FIREABLE(t45) OR FIREABLE(t31) OR FIREABLE(t30) OR FIREABLE(t29) OR (NOT FIREABLE(t55) AND NOT FIREABLE(t54) AND NOT FIREABLE(t53))))) : A (G ((NOT FIREABLE(t36) OR (NOT FIREABLE(t50) AND NOT FIREABLE(t49) AND NOT FIREABLE(t48)) OR FIREABLE(t22) OR (NOT FIREABLE(t18) AND NOT FIREABLE(t17) AND NOT FIREABLE(t16) AND NOT FIREABLE(t12) AND NOT FIREABLE(t11) AND NOT FIREABLE(t10) AND (FIREABLE(t40) OR FIREABLE(t9) OR (NOT FIREABLE(t47) AND NOT FIREABLE(t46) AND NOT FIREABLE(t45))))))) : E (F (FIREABLE(t1))) : E (F ((NOT FIREABLE(t50) AND NOT FIREABLE(t49) AND NOT FIREABLE(t48)))) : A (G ((FIREABLE(t47) OR FIREABLE(t46) OR FIREABLE(t45)))) : E (F ((FIREABLE(t22) AND (FIREABLE(t8) OR FIREABLE(t7) OR FIREABLE(t6)) AND NOT FIREABLE(t28) AND NOT FIREABLE(t27) AND NOT FIREABLE(t26) AND (FIREABLE(t8) OR FIREABLE(t7) OR FIREABLE(t6) OR FIREABLE(t31) OR FIREABLE(t30) OR FIREABLE(t29)) AND (FIREABLE(t50) OR FIREABLE(t49) OR FIREABLE(t48)))))
lola: computing a collection of formulas
lola: RUNNING
lola: subprocess 0 will run for 221 seconds at most (--localtimelimit=-1)
lola: ========================================
lola: ...considering subproblem: E (F ((FIREABLE(t34) OR FIREABLE(t33) OR FIREABLE(t32))))
lola: ========================================
lola: SUBTASK
lola: checking reachability
lola: Planning: workflow for reachability check: stateequation||search (--findpath=off)
lola: STORE
lola: using a bit-perfect encoder (--encoder=bit)
lola: using 220 bytes per marking, with 0 unused bits
lola: using a prefix tree store (--store=prefix)
lola: SEARCH (state space)
lola: state space: using reachability graph (--search=depth)
lola: state space: using reachability preserving stubborn set method with insertion algorithm (--stubborn=tarjan)
lola: RUNNING
lola: state equation: Generated DNF with 6 literals and 3 conjunctive subformulas
lola: SUBRESULT
lola: result: yes
lola: produced by: state space
lola: The predicate is reachable.
lola: 19 markings, 18 edges
lola: state equation: write sara problem file to QuasiCertifProtocol-COL-02-ReachabilityFireability.sara
lola: ========================================
lola: subprocess 1 will run for 236 seconds at most (--localtimelimit=-1)
lola: ========================================
lola: ...considering subproblem: A (G ((FIREABLE(t9) OR (NOT FIREABLE(t50) AND NOT FIREABLE(t49) AND NOT FIREABLE(t48) AND NOT FIREABLE(t40)) OR FIREABLE(t34) OR FIREABLE(t33) OR FIREABLE(t32) OR FIREABLE(t0))))
lola: ========================================
lola: SUBTASK
lola: checking invariance
lola: Planning: workflow for reachability check: stateequation||search (--findpath=off)
lola: STORE
lola: using a bit-perfect encoder (--encoder=bit)
lola: using 220 bytes per marking, with 0 unused bits
lola: using a prefix tree store (--store=prefix)
lola: SEARCH (state space)
lola: state space: using reachability graph (--search=depth)
lola: state space: using reachability preserving stubborn set method with insertion algorithm (--stubborn=tarjan)
lola: RUNNING
lola: SUBRESULT
lola: result: no
lola: produced by: state space
lola: The predicate is not invariant.
lola: 45 markings, 62 edges
lola: ========================================
lola: subprocess 2 will run for 252 seconds at most (--localtimelimit=-1)
lola: ========================================
lola: ...considering subproblem: E (F ((FIREABLE(t25) OR FIREABLE(t24) OR FIREABLE(t23))))
lola: ========================================
lola: SUBTASK
lola: checking reachability
lola: Planning: workflow for reachability check: stateequation||search (--findpath=off)
lola: STORE
lola: using a bit-perfect encoder (--encoder=bit)
lola: using 220 bytes per marking, with 0 unused bits
lola: using a prefix tree store (--store=prefix)
lola: SEARCH (state space)
lola: state space: using reachability graph (--search=depth)
lola: state space: using reachability preserving stubborn set method with insertion algorithm (--stubborn=tarjan)
lola: RUNNING
lola: state equation: Generated DNF with 12 literals and 3 conjunctive subformulas
lola: SUBRESULT
lola: result: yes
lola: produced by: state space
lola: The predicate is reachable.
lola: 27 markings, 26 edges
lola: state equation: write sara problem file to QuasiCertifProtocol-COL-02-ReachabilityFireability-2.sara
lola: ========================================
lola: subprocess 3 will run for 272 seconds at most (--localtimelimit=-1)
lola: ========================================
lola: ...considering subproblem: A (G ((FIREABLE(t47) OR FIREABLE(t46) OR FIREABLE(t45))))
lola: ========================================
lola: SUBTASK
lola: checking invariance
lola: Planning: workflow for reachability check: stateequation||search (--findpath=off)
lola: STORE
lola: using a bit-perfect encoder (--encoder=bit)
lola: using 220 bytes per marking, with 0 unused bits
lola: using a prefix tree store (--store=prefix)
lola: SEARCH (state space)
lola: state space: using reachability graph (--search=depth)
lola: state space: using reachability preserving stubborn set method with insertion algorithm (--stubborn=tarjan)
lola: RUNNING
lola: state equation: Generated DNF with 24 literals and 8 conjunctive subformulas
lola: SUBRESULT
lola: result: no
lola: produced by: state space
lola: The predicate is not invariant.
lola: 0 markings, 0 edges
lola: state equation: write sara problem file to QuasiCertifProtocol-COL-02-ReachabilityFireability-3.sara
lola: ========================================
lola: subprocess 4 will run for 295 seconds at most (--localtimelimit=-1)
lola: ========================================
lola: ...considering subproblem: A (G ((NOT FIREABLE(t52) OR (NOT FIREABLE(t34) AND NOT FIREABLE(t33) AND NOT FIREABLE(t32) AND ((NOT FIREABLE(t47) AND NOT FIREABLE(t46) AND NOT FIREABLE(t45)) OR NOT FIREABLE(t35))))))
lola: ========================================
lola: SUBTASK
lola: checking invariance
lola: Planning: workflow for reachability check: stateequation||search (--findpath=off)
lola: STORE
lola: using a bit-perfect encoder (--encoder=bit)
lola: using 220 bytes per marking, with 0 unused bits
lola: using a prefix tree store (--store=prefix)
lola: SEARCH (state space)
lola: state space: using reachability graph (--search=depth)
lola: state space: using reachability preserving stubborn set method with insertion algorithm (--stubborn=tarjan)
lola: RUNNING
lola: state equation: Generated DNF with 48 literals and 6 conjunctive subformulas
lola: SUBRESULT
lola: result: yes
lola: produced by: state space
lola: The predicate is invariant.
lola: 41 markings, 56 edges
lola: state equation: write sara problem file to QuasiCertifProtocol-COL-02-ReachabilityFireability-4.sara
lola: ========================================
lola: subprocess 5 will run for 321 seconds at most (--localtimelimit=-1)
lola: ========================================
lola: ...considering subproblem: E (F (((FIREABLE(t5) OR FIREABLE(t4) OR FIREABLE(t3)) AND (FIREABLE(t34) OR FIREABLE(t33) OR FIREABLE(t32) OR (FIREABLE(t22) AND (FIREABLE(t47) OR FIREABLE(t46) OR FIREABLE(t45)) AND FIREABLE(t2) AND FIREABLE(t52))))))
lola: ========================================
lola: SUBTASK
lola: checking reachability
lola: Planning: workflow for reachability check: stateequation||search (--findpath=off)
lola: STORE
lola: using a bit-perfect encoder (--encoder=bit)
lola: using 220 bytes per marking, with 0 unused bits
lola: using a prefix tree store (--store=prefix)
lola: SEARCH (state space)
lola: state space: using reachability graph (--search=depth)
lola: state space: using reachability preserving stubborn set method with insertion algorithm (--stubborn=tarjan)
lola: RUNNING
lola: state equation: Generated DNF with 126 literals and 18 conjunctive subformulas
lola: SUBRESULT
lola: result: no
lola: produced by: state space
lola: The predicate is unreachable.
lola: 33 markings, 48 edges
lola: state equation: write sara problem file to QuasiCertifProtocol-COL-02-ReachabilityFireability-5.sara
lola: ========================================
lola: subprocess 6 will run for 354 seconds at most (--localtimelimit=-1)
lola: ========================================
lola: ...considering subproblem: A (G ((NOT FIREABLE(t39) AND NOT FIREABLE(t38) AND NOT FIREABLE(t37) AND NOT FIREABLE(t39) AND NOT FIREABLE(t38) AND NOT FIREABLE(t37) AND NOT FIREABLE(t28) AND NOT FIREABLE(t27) AND NOT FIREABLE(t26) AND NOT FIREABLE(t0))))
lola: ========================================
lola: SUBTASK
lola: checking invariance
lola: Planning: workflow for reachability check: stateequation||search (--findpath=off)
lola: STORE
lola: using a bit-perfect encoder (--encoder=bit)
lola: using 220 bytes per marking, with 0 unused bits
lola: using a prefix tree store (--store=prefix)
lola: SEARCH (state space)
lola: state space: using reachability graph (--search=depth)
lola: state space: using reachability preserving stubborn set method with insertion algorithm (--stubborn=tarjan)
lola: RUNNING
lola: state equation: Generated DNF with 16 literals and 7 conjunctive subformulas
lola: SUBRESULT
lola: result: no
lola: produced by: state space
lola: The predicate is not invariant.
lola: 7 markings, 6 edges
lola: state equation: write sara problem file to QuasiCertifProtocol-COL-02-ReachabilityFireability-6.sara
lola: ========================================
lola: subprocess 7 will run for 393 seconds at most (--localtimelimit=-1)
lola: ========================================
lola: ...considering subproblem: E (F ((FIREABLE(t55) OR FIREABLE(t54) OR FIREABLE(t53))))
lola: ========================================
lola: SUBTASK
lola: checking reachability
lola: Planning: workflow for reachability check: stateequation||search (--findpath=off)
lola: STORE
lola: using a bit-perfect encoder (--encoder=bit)
lola: using 220 bytes per marking, with 0 unused bits
lola: using a prefix tree store (--store=prefix)
lola: SEARCH (state space)
lola: state space: using reachability graph (--search=depth)
lola: state space: using reachability preserving stubborn set method with insertion algorithm (--stubborn=tarjan)
lola: RUNNING
lola: state equation: Generated DNF with 6 literals and 3 conjunctive subformulas
lola: state equation: write sara problem file to QuasiCertifProtocol-COL-02-ReachabilityFireability-7.sara
lola: SUBRESULT
lola: result: yes
lola: produced by: state space
lola: The predicate is reachable.
lola: 22 markings, 21 edges
lola: ========================================
lola: state equation: calling and running sara
lola: subprocess 8 will run for 442 seconds at most (--localtimelimit=-1)
lola: ========================================
lola: ...considering subproblem: E (F (((NOT FIREABLE(t47) AND NOT FIREABLE(t46) AND NOT FIREABLE(t45)) OR (FIREABLE(t0) AND FIREABLE(t9)))))
lola: ========================================
lola: SUBTASK
lola: checking reachability
lola: Planning: workflow for reachability check: stateequation||search (--findpath=off)
lola: STORE
lola: using a bit-perfect encoder (--encoder=bit)
lola: using 220 bytes per marking, with 0 unused bits
lola: using a prefix tree store (--store=prefix)
lola: SEARCH (state space)
lola: state space: using reachability graph (--search=depth)
lola: state space: using reachability preserving stubborn set method with insertion algorithm (--stubborn=tarjan)
lola: RUNNING
lola: SUBRESULT
lola: result: yes
lola: produced by: state space
lola: The predicate is reachable.
lola: 0 markings, 0 edges
lola: state equation: Generated DNF with 26 literals and 9 conjunctive subformulas
lola: ========================================
lola: subprocess 9 will run for 505 seconds at most (--localtimelimit=-1)
lola: ========================================
lola: ...considering subproblem: E (F ((NOT FIREABLE(t39) AND NOT FIREABLE(t38) AND NOT FIREABLE(t37) AND (FIREABLE(t34) OR FIREABLE(t33) OR FIREABLE(t32)) AND FIREABLE(t36) AND (FIREABLE(t47) OR FIREABLE(t46) OR FIREABLE(t45) OR (FIREABLE(t51) AND (FIREABLE(t18) OR FIREABLE(t17) OR FIREABLE(t16)))))))
lola: ========================================
lola: SUBTASK
lola: checking reachability
lola: Planning: workflow for reachability check: stateequation||search (--findpath=off)
lola: STORE
lola: using a bit-perfect encoder (--encoder=bit)
lola: using 220 bytes per marking, with 0 unused bits
lola: using a prefix tree store (--store=prefix)
lola: SEARCH (state space)
lola: state space: using reachability graph (--search=depth)
lola: state space: using reachability preserving stubborn set method with insertion algorithm (--stubborn=tarjan)
lola: RUNNING
sara: try reading problem file QuasiCertifProtocol-COL-02-ReachabilityFireability-7.sara.
lola: SUBRESULT
lola: result: no
lola: produced by: state space
lola: The predicate is unreachable.
lola: 2 markings, 1 edges
lola: state equation: Generated DNF with 180 literals and 18 conjunctive subformulas
lola: ========================================
lola: subprocess 10 will run for 590 seconds at most (--localtimelimit=-1)
lola: ========================================
lola: ...considering subproblem: A (G ((FIREABLE(t39) OR FIREABLE(t38) OR FIREABLE(t37) OR FIREABLE(t1) OR FIREABLE(t21) OR FIREABLE(t20) OR FIREABLE(t19) OR FIREABLE(t21) OR FIREABLE(t20) OR FIREABLE(t19) OR FIREABLE(t22) OR FIREABLE(t47) OR FIREABLE(t46) OR FIREABLE(t45) OR FIREABLE(t31) OR FIREABLE(t30) OR FIREABLE(t29) OR (NOT FIREABLE(t55) AND NOT FIREABLE(t54) AND NOT FIREABLE(t53)))))
lola: ========================================
lola: SUBTASK
lola: checking invariance
lola: Planning: workflow for reachability check: stateequation||search (--findpath=off)
lola: STORE
lola: using a bit-perfect encoder (--encoder=bit)
lola: using 220 bytes per marking, with 0 unused bits
lola: using a prefix tree store (--store=prefix)
lola: SEARCH (state space)
lola: state space: using reachability graph (--search=depth)
lola: state space: using reachability preserving stubborn set method with insertion algorithm (--stubborn=tarjan)
lola: RUNNING
lola: SUBRESULT
lola: result: yes
lola: produced by: state space
lola: The predicate is invariant.
lola: 394 markings, 661 edges
sara: place or transition ordering is non-deterministic
lola: ========================================
lola: subprocess 11 will run for 708 seconds at most (--localtimelimit=-1)
lola: ========================================
lola: ...considering subproblem: A (G ((NOT FIREABLE(t36) OR (NOT FIREABLE(t50) AND NOT FIREABLE(t49) AND NOT FIREABLE(t48)) OR FIREABLE(t22) OR (NOT FIREABLE(t18) AND NOT FIREABLE(t17) AND NOT FIREABLE(t16) AND NOT FIREABLE(t12) AND NOT FIREABLE(t11) AND NOT FIREABLE(t10) AND (FIREABLE(t40) OR FIREABLE(t9) OR (NOT FIREABLE(t47) AND NOT FIREABLE(t46) AND NOT FIREABLE(t45)))))))
lola: ========================================
lola: SUBTASK
lola: checking invariance
lola: Planning: workflow for reachability check: stateequation||search (--findpath=off)
lola: STORE
lola: using a bit-perfect encoder (--encoder=bit)
lola: using 220 bytes per marking, with 0 unused bits
lola: using a prefix tree store (--store=prefix)
lola: SEARCH (state space)
lola: state space: using reachability graph (--search=depth)
lola: state space: using reachability preserving stubborn set method with insertion algorithm (--stubborn=tarjan)
lola: RUNNING
lola: SUBRESULT
lola: result: yes
lola: produced by: state space
lola: The predicate is invariant.
lola: 18 markings, 20 edges
lola: state equation: Generated DNF with 234 literals and 27 conjunctive subformulas
lola: ========================================
lola: subprocess 12 will run for 885 seconds at most (--localtimelimit=-1)
lola: ========================================
lola: ...considering subproblem: E (F (FIREABLE(t1)))
lola: ========================================
lola: SUBTASK
lola: checking reachability
lola: Planning: workflow for reachability check: stateequation||search (--findpath=off)
lola: STORE
lola: using a bit-perfect encoder (--encoder=bit)
lola: using 220 bytes per marking, with 0 unused bits
lola: using a prefix tree store (--store=prefix)
lola: SEARCH (state space)
lola: state space: using reachability graph (--search=depth)
lola: state space: using reachability preserving stubborn set method with insertion algorithm (--stubborn=tarjan)
lola: RUNNING
lola: state equation: Generated DNF with 1 literals and 1 conjunctive subformulas
lola: SUBRESULT
lola: result: yes
lola: produced by: state space
lola: The predicate is reachable.
lola: 11 markings, 10 edges
lola: state equation: write sara problem file to QuasiCertifProtocol-COL-02-ReachabilityFireability-12.sara
lola: ========================================
lola: subprocess 13 will run for 1180 seconds at most (--localtimelimit=-1)
lola: ========================================
lola: ...considering subproblem: E (F ((NOT FIREABLE(t50) AND NOT FIREABLE(t49) AND NOT FIREABLE(t48))))
lola: ========================================
lola: SUBTASK
lola: checking reachability
lola: Planning: workflow for reachability check: stateequation||search (--findpath=off)
lola: STORE
lola: using a bit-perfect encoder (--encoder=bit)
lola: using 220 bytes per marking, with 0 unused bits
lola: using a prefix tree store (--store=prefix)
lola: SEARCH (state space)
lola: state space: using reachability graph (--search=depth)
lola: state space: using reachability preserving stubborn set method with insertion algorithm (--stubborn=tarjan)
lola: RUNNING
lola: SUBRESULT
lola: result: yes
lola: produced by: state space
lola: The predicate is reachable.
lola: 0 markings, 0 edges
lola: state equation: Generated DNF with 192 literals and 64 conjunctive subformulas
lola: ========================================
lola: subprocess 14 will run for 1770 seconds at most (--localtimelimit=-1)
lola: ========================================
lola: ...considering subproblem: A (G ((FIREABLE(t47) OR FIREABLE(t46) OR FIREABLE(t45))))
lola: ========================================
lola: SUBTASK
lola: checking invariance
lola: Planning: workflow for reachability check: stateequation||search (--findpath=off)
lola: STORE
lola: using a bit-perfect encoder (--encoder=bit)
lola: using 220 bytes per marking, with 0 unused bits
lola: using a prefix tree store (--store=prefix)
lola: SEARCH (state space)
lola: state space: using reachability graph (--search=depth)
lola: state space: using reachability preserving stubborn set method with insertion algorithm (--stubborn=tarjan)
lola: RUNNING
lola: state equation: Generated DNF with 24 literals and 8 conjunctive subformulas
lola: SUBRESULT
lola: result: no
lola: produced by: state space
lola: The predicate is not invariant.
lola: 0 markings, 0 edges
lola: state equation: write sara problem file to QuasiCertifProtocol-COL-02-ReachabilityFireability-14.sara
lola: ========================================
lola: subprocess 15 will run for 3540 seconds at most (--localtimelimit=-1)
lola: ========================================
lola: ...considering subproblem: E (F ((FIREABLE(t22) AND (FIREABLE(t8) OR FIREABLE(t7) OR FIREABLE(t6)) AND NOT FIREABLE(t28) AND NOT FIREABLE(t27) AND NOT FIREABLE(t26) AND (FIREABLE(t8) OR FIREABLE(t7) OR FIREABLE(t6) OR FIREABLE(t31) OR FIREABLE(t30) OR FIREABLE(t29)) AND (FIREABLE(t50) OR FIREABLE(t49) OR FIREABLE(t48)))))
lola: ========================================
lola: SUBTASK
lola: checking reachability
lola: Planning: workflow for reachability check: stateequation||search (--findpath=off)
lola: STORE
lola: using a bit-perfect encoder (--encoder=bit)
lola: using 220 bytes per marking, with 0 unused bits
lola: using a prefix tree store (--store=prefix)
lola: SEARCH (state space)
lola: state space: using reachability graph (--search=depth)
lola: state space: using reachability preserving stubborn set method with insertion algorithm (--stubborn=tarjan)
lola: RUNNING
lola: SUBRESULT
lola: result: no
lola: produced by: state space
lola: The predicate is unreachable.
lola: 38 markings, 51 edges
lola: ========================================
lola: RESULT
lola:
SUMMARY: yes no yes no yes no no yes yes no yes yes yes yes no no
FORMULA QuasiCertifProtocol-COL-02-ReachabilityFireability-0 TRUE TECHNIQUES COLLATERAL_PROCESSING EXPLICIT STATE_COMPRESSION STUBBORN_SETS TOPOLOGICAL USE_NUPN
FORMULA QuasiCertifProtocol-COL-02-ReachabilityFireability-1 FALSE TECHNIQUES COLLATERAL_PROCESSING EXPLICIT STATE_COMPRESSION STUBBORN_SETS TOPOLOGICAL USE_NUPN
FORMULA QuasiCertifProtocol-COL-02-ReachabilityFireability-2 TRUE TECHNIQUES COLLATERAL_PROCESSING EXPLICIT STATE_COMPRESSION STUBBORN_SETS TOPOLOGICAL USE_NUPN
FORMULA QuasiCertifProtocol-COL-02-ReachabilityFireability-3 FALSE TECHNIQUES COLLATERAL_PROCESSING EXPLICIT STATE_COMPRESSION STUBBORN_SETS TOPOLOGICAL USE_NUPN
FORMULA QuasiCertifProtocol-COL-02-ReachabilityFireability-4 TRUE TECHNIQUES COLLATERAL_PROCESSING EXPLICIT STATE_COMPRESSION STUBBORN_SETS TOPOLOGICAL USE_NUPN
FORMULA QuasiCertifProtocol-COL-02-ReachabilityFireability-5 FALSE TECHNIQUES COLLATERAL_PROCESSING EXPLICIT STATE_COMPRESSION STUBBORN_SETS TOPOLOGICAL USE_NUPN
FORMULA QuasiCertifProtocol-COL-02-ReachabilityFireability-6 FALSE TECHNIQUES COLLATERAL_PROCESSING EXPLICIT STATE_COMPRESSION STUBBORN_SETS TOPOLOGICAL USE_NUPN
FORMULA QuasiCertifProtocol-COL-02-ReachabilityFireability-7 TRUE TECHNIQUES COLLATERAL_PROCESSING EXPLICIT STATE_COMPRESSION STUBBORN_SETS TOPOLOGICAL USE_NUPN
FORMULA QuasiCertifProtocol-COL-02-ReachabilityFireability-8 TRUE TECHNIQUES COLLATERAL_PROCESSING EXPLICIT STATE_COMPRESSION STUBBORN_SETS TOPOLOGICAL USE_NUPN
FORMULA QuasiCertifProtocol-COL-02-ReachabilityFireability-9 FALSE TECHNIQUES COLLATERAL_PROCESSING EXPLICIT STATE_COMPRESSION STUBBORN_SETS TOPOLOGICAL USE_NUPN
FORMULA QuasiCertifProtocol-COL-02-ReachabilityFireability-10 TRUE TECHNIQUES COLLATERAL_PROCESSING EXPLICIT STATE_COMPRESSION STUBBORN_SETS TOPOLOGICAL USE_NUPN
FORMULA QuasiCertifProtocol-COL-02-ReachabilityFireability-11 TRUE TECHNIQUES COLLATERAL_PROCESSING EXPLICIT STATE_COMPRESSION STUBBORN_SETS TOPOLOGICAL USE_NUPN
FORMULA QuasiCertifProtocol-COL-02-ReachabilityFireability-12 TRUE TECHNIQUES COLLATERAL_PROCESSING EXPLICIT STATE_COMPRESSION STUBBORN_SETS TOPOLOGICAL USE_NUPN
FORMULA QuasiCertifProtocol-COL-02-ReachabilityFireability-13 TRUE TECHNIQUES COLLATERAL_PROCESSING EXPLICIT STATE_COMPRESSION STUBBORN_SETS TOPOLOGICAL USE_NUPN
FORMULA QuasiCertifProtocol-COL-02-ReachabilityFireability-14 FALSE TECHNIQUES COLLATERAL_PROCESSING EXPLICIT STATE_COMPRESSION STUBBORN_SETS TOPOLOGICAL USE_NUPN
FORMULA QuasiCertifProtocol-COL-02-ReachabilityFireability-15 FALSE TECHNIQUES COLLATERAL_PROCESSING EXPLICIT STATE_COMPRESSION STUBBORN_SETS TOPOLOGICAL USE_NUPN
----- Kill lola and sara stdout -----
----- Kill lola and sara stderr -----
----- Finished stderr -----
----- Finished stdout -----
Sequence of Actions to be Executed by the VM
This is useful if one wants to reexecute the tool in the VM from the submitted image disk.
set -x
# this is for BenchKit: configuration of major elements for the test
export BK_INPUT="QuasiCertifProtocol-COL-02"
export BK_EXAMINATION="ReachabilityFireability"
export BK_TOOL="irma4mcc-structural"
export BK_RESULT_DIR="/tmp/BK_RESULTS/OUTPUTS"
export BK_TIME_CONFINEMENT="3600"
export BK_MEMORY_CONFINEMENT="16384"
# this is specific to your benchmark or test
export BIN_DIR="$HOME/BenchKit/bin"
# remove the execution directoty if it exists (to avoid increse of .vmdk images)
if [ -d execution ] ; then
rm -rf execution
fi
tar xzf /home/mcc/BenchKit/INPUTS/QuasiCertifProtocol-COL-02.tgz
mv QuasiCertifProtocol-COL-02 execution
cd execution
pwd
ls -lh
# this is for BenchKit: explicit launching of the test
echo "====================================================================="
echo " Generated by BenchKit 2-3637"
echo " Executing tool irma4mcc-structural"
echo " Input is QuasiCertifProtocol-COL-02, examination is ReachabilityFireability"
echo " Time confinement is $BK_TIME_CONFINEMENT seconds"
echo " Memory confinement is 16384 MBytes"
echo " Number of cores is 4"
echo " Run identifier is r139-qhx2-152673581100014"
echo "====================================================================="
echo
echo "--------------------"
echo "content from stdout:"
echo
echo "=== Data for post analysis generated by BenchKit (invocation template)"
echo
if [ "ReachabilityFireability" = "UpperBounds" ] ; then
echo "The expected result is a vector of positive values"
echo NUM_VECTOR
elif [ "ReachabilityFireability" != "StateSpace" ] ; then
echo "The expected result is a vector of booleans"
echo BOOL_VECTOR
else
echo "no data necessary for post analysis"
fi
echo
if [ -f "ReachabilityFireability.txt" ] ; then
echo "here is the order used to build the result vector(from text file)"
for x in $(grep Property ReachabilityFireability.txt | cut -d ' ' -f 2 | sort -u) ; do
echo "FORMULA_NAME $x"
done
elif [ -f "ReachabilityFireability.xml" ] ; then # for cunf (txt files deleted;-)
echo echo "here is the order used to build the result vector(from xml file)"
for x in $(grep '
echo "FORMULA_NAME $x"
done
fi
echo
echo "=== Now, execution of the tool begins"
echo
echo -n "BK_START "
date -u +%s%3N
echo
timeout -s 9 $BK_TIME_CONFINEMENT bash -c "/home/mcc/BenchKit/BenchKit_head.sh 2> STDERR ; echo ; echo -n \"BK_STOP \" ; date -u +%s%3N"
if [ $? -eq 137 ] ; then
echo
echo "BK_TIME_CONFINEMENT_REACHED"
fi
echo
echo "--------------------"
echo "content from stderr:"
echo
cat STDERR ;

