About the Execution of ITS-Tools for S_QuasiCertifProtocol-COL-02
| Execution Summary | |||||
| Max Memory Used (MB) |
Time wait (ms) | CPU Usage (ms) | I/O Wait (ms) | Computed Result | Execution Status |
| 296.440 | 5815.00 | 10678.00 | 228.20 | FTFTFFFFTTFTFTTT | normal |
Execution Chart
We display below the execution chart for this examination (boot time has been removed).
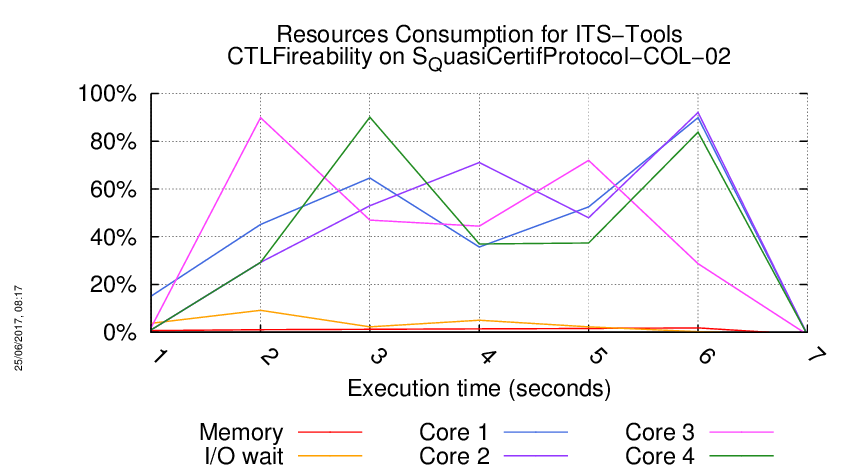
Trace from the execution
Waiting for the VM to be ready (probing ssh)
.................
=====================================================================
Generated by BenchKit 2-3254
Executing tool itstools
Input is S_QuasiCertifProtocol-COL-02, examination is CTLFireability
Time confinement is 3600 seconds
Memory confinement is 16384 MBytes
Number of cores is 4
Run identifier is r140-smll-149479233800193
=====================================================================
--------------------
content from stdout:
=== Data for post analysis generated by BenchKit (invocation template)
The expected result is a vector of booleans
BOOL_VECTOR
here is the order used to build the result vector(from text file)
FORMULA_NAME QuasiCertifProtocol-COL-02-CTLFireability-0
FORMULA_NAME QuasiCertifProtocol-COL-02-CTLFireability-1
FORMULA_NAME QuasiCertifProtocol-COL-02-CTLFireability-10
FORMULA_NAME QuasiCertifProtocol-COL-02-CTLFireability-11
FORMULA_NAME QuasiCertifProtocol-COL-02-CTLFireability-12
FORMULA_NAME QuasiCertifProtocol-COL-02-CTLFireability-13
FORMULA_NAME QuasiCertifProtocol-COL-02-CTLFireability-14
FORMULA_NAME QuasiCertifProtocol-COL-02-CTLFireability-15
FORMULA_NAME QuasiCertifProtocol-COL-02-CTLFireability-2
FORMULA_NAME QuasiCertifProtocol-COL-02-CTLFireability-3
FORMULA_NAME QuasiCertifProtocol-COL-02-CTLFireability-4
FORMULA_NAME QuasiCertifProtocol-COL-02-CTLFireability-5
FORMULA_NAME QuasiCertifProtocol-COL-02-CTLFireability-6
FORMULA_NAME QuasiCertifProtocol-COL-02-CTLFireability-7
FORMULA_NAME QuasiCertifProtocol-COL-02-CTLFireability-8
FORMULA_NAME QuasiCertifProtocol-COL-02-CTLFireability-9
=== Now, execution of the tool begins
BK_START 1496392839425
its-ctl command run as :
/home/mcc/BenchKit/eclipse/plugins/fr.lip6.move.gal.itstools.binaries_1.0.0.201705302212/bin/its-ctl-linux64 --gc-threshold 2000000 --quiet -i /home/mcc/execution/CTLFireability.pnml.gal -t CGAL -ctl /home/mcc/execution/CTLFireability.ctl
No direction supplied, using forward translation only.
Parsed 16 CTL formulae.
Model ,|S| ,Time ,Mem(kb) ,fin. SDD ,fin. DDD ,peak SDD ,peak DDD ,SDD Hom ,SDD cache peak ,DDD Hom ,DDD cachepeak ,SHom cache
reachable,1029,0.081065,6176,793,200,3573,677,199,1668,86,2214,0
Converting to forward existential form...Done !
original formula: (AX(!(((((tsid0.s5_0>=1 * malicious_reservoir.malicious_reservoir[0]>=1) + (tsid1.s5_1>=1 * malicious_reservoir.malicious_reservoir[0]>=1)) + (tsid2.s5_2>=1 * malicious_reservoir.malicious_reservoir[0]>=1)) + (a5.a5[0]>=1 + (((malicious_reservoir.malicious_reservoir[0]>=1 * tsid0.s6_0>=1) + (malicious_reservoir.malicious_reservoir[0]>=1 * tsid1.s6_1>=1)) + (malicious_reservoir.malicious_reservoir[0]>=1 * tsid2.s6_2>=1)))))) * ((!(AF(a4.a4[0]>=1)) + (EF(a4.a4[0]>=1) + (((tsid0.s4_0>=1 + tsid1.s4_1>=1) + tsid2.s4_2>=1) + (Astart.Astart[0]>=1 * (((malicious_reservoir.malicious_reservoir[0]>=1 * tsid0.s2_0>=1) + (malicious_reservoir.malicious_reservoir[0]>=1 * tsid1.s2_1>=1)) + (malicious_reservoir.malicious_reservoir[0]>=1 * tsid2.s2_2>=1)))))) * AF(((((((tsid0.c1_0>=1 * tsidxtsid3.n9_3>=1) * tsidxtsid6.n9_6>=1) * tsidxtsid0.n9_0>=1) + (((tsid1.c1_1>=1 * tsidxtsid4.n9_4>=1) * tsidxtsid7.n9_7>=1) * tsidxtsid1.n9_1>=1)) + (((tsid2.c1_2>=1 * tsidxtsid5.n9_5>=1) * tsidxtsid8.n9_8>=1) * tsidxtsid2.n9_2>=1)) * Astart.Astart[0]>=1))))
=> equivalent forward existential formula: ([(EY(Init) * ((((tsid0.s5_0>=1 * malicious_reservoir.malicious_reservoir[0]>=1) + (tsid1.s5_1>=1 * malicious_reservoir.malicious_reservoir[0]>=1)) + (tsid2.s5_2>=1 * malicious_reservoir.malicious_reservoir[0]>=1)) + (a5.a5[0]>=1 + (((malicious_reservoir.malicious_reservoir[0]>=1 * tsid0.s6_0>=1) + (malicious_reservoir.malicious_reservoir[0]>=1 * tsid1.s6_1>=1)) + (malicious_reservoir.malicious_reservoir[0]>=1 * tsid2.s6_2>=1)))))] = FALSE * ([((Init * !((E(TRUE U a4.a4[0]>=1) + (((tsid0.s4_0>=1 + tsid1.s4_1>=1) + tsid2.s4_2>=1) + (Astart.Astart[0]>=1 * (((malicious_reservoir.malicious_reservoir[0]>=1 * tsid0.s2_0>=1) + (malicious_reservoir.malicious_reservoir[0]>=1 * tsid1.s2_1>=1)) + (malicious_reservoir.malicious_reservoir[0]>=1 * tsid2.s2_2>=1))))))) * !(EG(!(a4.a4[0]>=1))))] = FALSE * [FwdG(Init,!(((((((tsid0.c1_0>=1 * tsidxtsid3.n9_3>=1) * tsidxtsid6.n9_6>=1) * tsidxtsid0.n9_0>=1) + (((tsid1.c1_1>=1 * tsidxtsid4.n9_4>=1) * tsidxtsid7.n9_7>=1) * tsidxtsid1.n9_1>=1)) + (((tsid2.c1_2>=1 * tsidxtsid5.n9_5>=1) * tsidxtsid8.n9_8>=1) * tsidxtsid2.n9_2>=1)) * Astart.Astart[0]>=1)))] = FALSE))
(forward)formula 0,0,0.349203,14040,1,0,18511,3474,1045,16614,433,18581,55810
FORMULA QuasiCertifProtocol-COL-02-CTLFireability-0 FALSE TECHNIQUES DECISION_DIAGRAMS TOPOLOGICAL USE_NUPN
Formula is FALSE !
***************************************
original formula: EG((EG((((tsid0.s2_0>=1 * tsid0.n3_0>=1) + (tsid1.s2_1>=1 * tsid1.n3_1>=1)) + (tsid2.s2_2>=1 * tsid2.n3_2>=1))) + !(EX(a5.a5[0]>=1))))
=> equivalent forward existential formula: [FwdG(Init,(EG((((tsid0.s2_0>=1 * tsid0.n3_0>=1) + (tsid1.s2_1>=1 * tsid1.n3_1>=1)) + (tsid2.s2_2>=1 * tsid2.n3_2>=1))) + !(EX(a5.a5[0]>=1))))] != FALSE
(forward)formula 1,1,0.362228,14376,1,0,19749,3482,1070,17833,435,18878,59535
FORMULA QuasiCertifProtocol-COL-02-CTLFireability-1 TRUE TECHNIQUES DECISION_DIAGRAMS TOPOLOGICAL USE_NUPN
Formula is TRUE !
***************************************
original formula: EG((!(EX(a4.a4[0]>=1)) + EF(((((tsid0.s5_0>=1 * malicious_reservoir.malicious_reservoir[0]>=1) + (tsid1.s5_1>=1 * malicious_reservoir.malicious_reservoir[0]>=1)) + (tsid2.s5_2>=1 * malicious_reservoir.malicious_reservoir[0]>=1)) + a2.a2[0]>=1))))
=> equivalent forward existential formula: [FwdG(Init,(!(EX(a4.a4[0]>=1)) + E(TRUE U ((((tsid0.s5_0>=1 * malicious_reservoir.malicious_reservoir[0]>=1) + (tsid1.s5_1>=1 * malicious_reservoir.malicious_reservoir[0]>=1)) + (tsid2.s5_2>=1 * malicious_reservoir.malicious_reservoir[0]>=1)) + a2.a2[0]>=1))))] != FALSE
(forward)formula 2,1,0.444486,17068,1,0,26660,3564,1191,24074,449,19100,77977
FORMULA QuasiCertifProtocol-COL-02-CTLFireability-2 TRUE TECHNIQUES DECISION_DIAGRAMS TOPOLOGICAL USE_NUPN
Formula is TRUE !
***************************************
original formula: !(A(AF(a2.a2[0]>=1) U ((a2.a2[0]>=1 + (((tsid0.s2_0>=1 * tsid0.n3_0>=1) + (tsid1.s2_1>=1 * tsid1.n3_1>=1)) + (tsid2.s2_2>=1 * tsid2.n3_2>=1))) * !(a2.a2[0]>=1))))
=> equivalent forward existential formula: ([FwdG((FwdU(Init,!(((a2.a2[0]>=1 + (((tsid0.s2_0>=1 * tsid0.n3_0>=1) + (tsid1.s2_1>=1 * tsid1.n3_1>=1)) + (tsid2.s2_2>=1 * tsid2.n3_2>=1))) * !(a2.a2[0]>=1)))) * !(((a2.a2[0]>=1 + (((tsid0.s2_0>=1 * tsid0.n3_0>=1) + (tsid1.s2_1>=1 * tsid1.n3_1>=1)) + (tsid2.s2_2>=1 * tsid2.n3_2>=1))) * !(a2.a2[0]>=1)))),!(a2.a2[0]>=1))] != FALSE + [FwdG(Init,!(((a2.a2[0]>=1 + (((tsid0.s2_0>=1 * tsid0.n3_0>=1) + (tsid1.s2_1>=1 * tsid1.n3_1>=1)) + (tsid2.s2_2>=1 * tsid2.n3_2>=1))) * !(a2.a2[0]>=1))))] != FALSE)
(forward)formula 3,1,0.450887,17328,1,0,26887,3564,1241,24354,450,19100,79056
FORMULA QuasiCertifProtocol-COL-02-CTLFireability-3 TRUE TECHNIQUES DECISION_DIAGRAMS TOPOLOGICAL USE_NUPN
Formula is TRUE !
***************************************
original formula: AF((((tsid2.n2_2>=1 * tsid1.n2_1>=1) * tsid0.n2_0>=1) * a1.a1[0]>=1))
=> equivalent forward existential formula: [FwdG(Init,!((((tsid2.n2_2>=1 * tsid1.n2_1>=1) * tsid0.n2_0>=1) * a1.a1[0]>=1)))] = FALSE
(forward)formula 4,0,0.453814,17464,1,0,26978,3564,1277,24500,450,19100,79692
FORMULA QuasiCertifProtocol-COL-02-CTLFireability-4 FALSE TECHNIQUES DECISION_DIAGRAMS TOPOLOGICAL USE_NUPN
Formula is FALSE !
***************************************
original formula: EX(((((malicious_reservoir.malicious_reservoir[0]>=1 * tsid0.s2_0>=1) + (malicious_reservoir.malicious_reservoir[0]>=1 * tsid1.s2_1>=1)) + (malicious_reservoir.malicious_reservoir[0]>=1 * tsid2.s2_2>=1)) + !(AF(((tsid0.s4_0>=1 + tsid1.s4_1>=1) + tsid2.s4_2>=1)))))
=> equivalent forward existential formula: ([(EY(Init) * (((malicious_reservoir.malicious_reservoir[0]>=1 * tsid0.s2_0>=1) + (malicious_reservoir.malicious_reservoir[0]>=1 * tsid1.s2_1>=1)) + (malicious_reservoir.malicious_reservoir[0]>=1 * tsid2.s2_2>=1)))] != FALSE + [FwdG(EY(Init),!(((tsid0.s4_0>=1 + tsid1.s4_1>=1) + tsid2.s4_2>=1)))] != FALSE)
(forward)formula 5,1,0.46218,17492,1,0,27528,3564,1312,25084,450,19103,81713
FORMULA QuasiCertifProtocol-COL-02-CTLFireability-5 TRUE TECHNIQUES DECISION_DIAGRAMS TOPOLOGICAL USE_NUPN
Formula is TRUE !
***************************************
original formula: AG(EG(EF((((malicious_reservoir.malicious_reservoir[0]>=1 * tsid0.s6_0>=1) + (malicious_reservoir.malicious_reservoir[0]>=1 * tsid1.s6_1>=1)) + (malicious_reservoir.malicious_reservoir[0]>=1 * tsid2.s6_2>=1)))))
=> equivalent forward existential formula: [(FwdU(Init,TRUE) * !(EG(E(TRUE U (((malicious_reservoir.malicious_reservoir[0]>=1 * tsid0.s6_0>=1) + (malicious_reservoir.malicious_reservoir[0]>=1 * tsid1.s6_1>=1)) + (malicious_reservoir.malicious_reservoir[0]>=1 * tsid2.s6_2>=1))))))] = FALSE
(forward)formula 6,0,0.469646,17848,1,0,27671,3564,1331,25258,450,19103,82648
FORMULA QuasiCertifProtocol-COL-02-CTLFireability-6 FALSE TECHNIQUES DECISION_DIAGRAMS TOPOLOGICAL USE_NUPN
Formula is FALSE !
***************************************
original formula: ((!((a3.a3[0]>=1 * AX(((tsid0.s6_0>=1 + tsid1.s6_1>=1) + tsid2.s6_2>=1)))) + (((((malicious_reservoir.malicious_reservoir[0]>=1 * tsid0.s2_0>=1) + (malicious_reservoir.malicious_reservoir[0]>=1 * tsid1.s2_1>=1)) + (malicious_reservoir.malicious_reservoir[0]>=1 * tsid2.s2_2>=1)) + (((a3.a3[0]>=1 * tsid1.n4_1>=1) * tsid2.n4_2>=1) * tsid0.n4_0>=1)) + (a3.a3[0]>=1 * (((tsid0.s2_0>=1 * tsid0.n3_0>=1) + (tsid1.s2_1>=1 * tsid1.n3_1>=1)) + (tsid2.s2_2>=1 * tsid2.n3_2>=1))))) * (!(AF((((((tsidxtsid0.n7_0>=1 * tsidxtsid6.n7_6>=1) * tsidxtsid3.n7_3>=1) * tsid0.Cstart_0>=1) + (((tsidxtsid1.n7_1>=1 * tsidxtsid7.n7_7>=1) * tsidxtsid4.n7_4>=1) * tsid1.Cstart_1>=1)) + (((tsidxtsid2.n7_2>=1 * tsidxtsid8.n7_8>=1) * tsidxtsid5.n7_5>=1) * tsid2.Cstart_2>=1)))) * (!((((tsid0.s2_0>=1 * tsid0.n3_0>=1) + (tsid1.s2_1>=1 * tsid1.n3_1>=1)) + (tsid2.s2_2>=1 * tsid2.n3_2>=1))) + (a4.a4[0]>=1 + (((((tsid0.c1_0>=1 * tsidxtsid3.n9_3>=1) * tsidxtsid6.n9_6>=1) * tsidxtsid0.n9_0>=1) + (((tsid1.c1_1>=1 * tsidxtsid4.n9_4>=1) * tsidxtsid7.n9_7>=1) * tsidxtsid1.n9_1>=1)) + (((tsid2.c1_2>=1 * tsidxtsid5.n9_5>=1) * tsidxtsid8.n9_8>=1) * tsidxtsid2.n9_2>=1))))))
=> equivalent forward existential formula: [FwdG(((Init * (!((a3.a3[0]>=1 * !(EX(!(((tsid0.s6_0>=1 + tsid1.s6_1>=1) + tsid2.s6_2>=1)))))) + (((((malicious_reservoir.malicious_reservoir[0]>=1 * tsid0.s2_0>=1) + (malicious_reservoir.malicious_reservoir[0]>=1 * tsid1.s2_1>=1)) + (malicious_reservoir.malicious_reservoir[0]>=1 * tsid2.s2_2>=1)) + (((a3.a3[0]>=1 * tsid1.n4_1>=1) * tsid2.n4_2>=1) * tsid0.n4_0>=1)) + (a3.a3[0]>=1 * (((tsid0.s2_0>=1 * tsid0.n3_0>=1) + (tsid1.s2_1>=1 * tsid1.n3_1>=1)) + (tsid2.s2_2>=1 * tsid2.n3_2>=1)))))) * (!((((tsid0.s2_0>=1 * tsid0.n3_0>=1) + (tsid1.s2_1>=1 * tsid1.n3_1>=1)) + (tsid2.s2_2>=1 * tsid2.n3_2>=1))) + (a4.a4[0]>=1 + (((((tsid0.c1_0>=1 * tsidxtsid3.n9_3>=1) * tsidxtsid6.n9_6>=1) * tsidxtsid0.n9_0>=1) + (((tsid1.c1_1>=1 * tsidxtsid4.n9_4>=1) * tsidxtsid7.n9_7>=1) * tsidxtsid1.n9_1>=1)) + (((tsid2.c1_2>=1 * tsidxtsid5.n9_5>=1) * tsidxtsid8.n9_8>=1) * tsidxtsid2.n9_2>=1))))),!((((((tsidxtsid0.n7_0>=1 * tsidxtsid6.n7_6>=1) * tsidxtsid3.n7_3>=1) * tsid0.Cstart_0>=1) + (((tsidxtsid1.n7_1>=1 * tsidxtsid7.n7_7>=1) * tsidxtsid4.n7_4>=1) * tsid1.Cstart_1>=1)) + (((tsidxtsid2.n7_2>=1 * tsidxtsid8.n7_8>=1) * tsidxtsid5.n7_5>=1) * tsid2.Cstart_2>=1))))] != FALSE
(forward)formula 7,1,0.518043,18372,1,0,29169,3609,1408,26763,450,19277,87691
FORMULA QuasiCertifProtocol-COL-02-CTLFireability-7 TRUE TECHNIQUES DECISION_DIAGRAMS TOPOLOGICAL USE_NUPN
Formula is TRUE !
***************************************
original formula: !(AF(EG(((((tsid0.s3_0>=1 * tsid0.n5_0>=1) + (tsid1.s3_1>=1 * tsid1.n5_1>=1)) + (tsid2.s3_2>=1 * tsid2.n5_2>=1)) + (((((tsidxtsid0.n7_0>=1 * tsidxtsid6.n7_6>=1) * tsidxtsid3.n7_3>=1) * tsid0.Cstart_0>=1) + (((tsidxtsid1.n7_1>=1 * tsidxtsid7.n7_7>=1) * tsidxtsid4.n7_4>=1) * tsid1.Cstart_1>=1)) + (((tsidxtsid2.n7_2>=1 * tsidxtsid8.n7_8>=1) * tsidxtsid5.n7_5>=1) * tsid2.Cstart_2>=1))))))
=> equivalent forward existential formula: [FwdG(Init,!(EG(((((tsid0.s3_0>=1 * tsid0.n5_0>=1) + (tsid1.s3_1>=1 * tsid1.n5_1>=1)) + (tsid2.s3_2>=1 * tsid2.n5_2>=1)) + (((((tsidxtsid0.n7_0>=1 * tsidxtsid6.n7_6>=1) * tsidxtsid3.n7_3>=1) * tsid0.Cstart_0>=1) + (((tsidxtsid1.n7_1>=1 * tsidxtsid7.n7_7>=1) * tsidxtsid4.n7_4>=1) * tsid1.Cstart_1>=1)) + (((tsidxtsid2.n7_2>=1 * tsidxtsid8.n7_8>=1) * tsidxtsid5.n7_5>=1) * tsid2.Cstart_2>=1))))))] != FALSE
(forward)formula 8,1,0.52838,18712,1,0,29231,3613,1434,26878,452,19289,88393
FORMULA QuasiCertifProtocol-COL-02-CTLFireability-8 TRUE TECHNIQUES DECISION_DIAGRAMS TOPOLOGICAL USE_NUPN
Formula is TRUE !
***************************************
original formula: EG(EF((!((((tsid0.s5_0>=1 * malicious_reservoir.malicious_reservoir[0]>=1) + (tsid1.s5_1>=1 * malicious_reservoir.malicious_reservoir[0]>=1)) + (tsid2.s5_2>=1 * malicious_reservoir.malicious_reservoir[0]>=1))) + ((((malicious_reservoir.malicious_reservoir[0]>=1 * tsid0.s2_0>=1) + (malicious_reservoir.malicious_reservoir[0]>=1 * tsid1.s2_1>=1)) + (malicious_reservoir.malicious_reservoir[0]>=1 * tsid2.s2_2>=1)) * (((((tsid0.s5_0>=1 * tsidxtsid1.n8_1>=1) * tsidxtsid0.n8_0>=1) * tsidxtsid2.n8_2>=1) + (((tsid1.s5_1>=1 * tsidxtsid4.n8_4>=1) * tsidxtsid3.n8_3>=1) * tsidxtsid5.n8_5>=1)) + (((tsid2.s5_2>=1 * tsidxtsid7.n8_7>=1) * tsidxtsid6.n8_6>=1) * tsidxtsid8.n8_8>=1))))))
=> equivalent forward existential formula: [FwdG(Init,E(TRUE U (!((((tsid0.s5_0>=1 * malicious_reservoir.malicious_reservoir[0]>=1) + (tsid1.s5_1>=1 * malicious_reservoir.malicious_reservoir[0]>=1)) + (tsid2.s5_2>=1 * malicious_reservoir.malicious_reservoir[0]>=1))) + ((((malicious_reservoir.malicious_reservoir[0]>=1 * tsid0.s2_0>=1) + (malicious_reservoir.malicious_reservoir[0]>=1 * tsid1.s2_1>=1)) + (malicious_reservoir.malicious_reservoir[0]>=1 * tsid2.s2_2>=1)) * (((((tsid0.s5_0>=1 * tsidxtsid1.n8_1>=1) * tsidxtsid0.n8_0>=1) * tsidxtsid2.n8_2>=1) + (((tsid1.s5_1>=1 * tsidxtsid4.n8_4>=1) * tsidxtsid3.n8_3>=1) * tsidxtsid5.n8_5>=1)) + (((tsid2.s5_2>=1 * tsidxtsid7.n8_7>=1) * tsidxtsid6.n8_6>=1) * tsidxtsid8.n8_8>=1))))))] != FALSE
(forward)formula 9,1,0.558661,18912,1,0,29357,3628,1472,27225,452,19311,91031
FORMULA QuasiCertifProtocol-COL-02-CTLFireability-9 TRUE TECHNIQUES DECISION_DIAGRAMS TOPOLOGICAL USE_NUPN
Formula is TRUE !
***************************************
original formula: AX(AX(AF(Astart.Astart[0]>=1)))
=> equivalent forward existential formula: [FwdG(EY(EY(Init)),!(Astart.Astart[0]>=1))] = FALSE
(forward)formula 10,0,0.566175,19172,1,0,29423,3628,1508,27401,455,19342,92699
FORMULA QuasiCertifProtocol-COL-02-CTLFireability-10 FALSE TECHNIQUES DECISION_DIAGRAMS TOPOLOGICAL USE_NUPN
Formula is FALSE !
***************************************
original formula: AG(((((tsid2.n2_2>=1 * tsid1.n2_1>=1) * tsid0.n2_0>=1) * a1.a1[0]>=1) + !(EG(((tsid0.s6_0>=1 + tsid1.s6_1>=1) + tsid2.s6_2>=1)))))
=> equivalent forward existential formula: [FwdG((FwdU(Init,TRUE) * !((((tsid2.n2_2>=1 * tsid1.n2_1>=1) * tsid0.n2_0>=1) * a1.a1[0]>=1))),((tsid0.s6_0>=1 + tsid1.s6_1>=1) + tsid2.s6_2>=1))] = FALSE
dead was empty
(forward)formula 11,1,0.568873,19180,1,0,29452,3634,1508,27499,455,19348,92795
FORMULA QuasiCertifProtocol-COL-02-CTLFireability-11 TRUE TECHNIQUES DECISION_DIAGRAMS TOPOLOGICAL USE_NUPN
Formula is TRUE !
***************************************
original formula: EF(EG((((tsid0.Sstart_0>=1 * malicious_reservoir.malicious_reservoir[0]>=1) + (tsid1.Sstart_1>=1 * malicious_reservoir.malicious_reservoir[0]>=1)) + (tsid2.Sstart_2>=1 * malicious_reservoir.malicious_reservoir[0]>=1))))
=> equivalent forward existential formula: [FwdG(FwdU(Init,TRUE),(((tsid0.Sstart_0>=1 * malicious_reservoir.malicious_reservoir[0]>=1) + (tsid1.Sstart_1>=1 * malicious_reservoir.malicious_reservoir[0]>=1)) + (tsid2.Sstart_2>=1 * malicious_reservoir.malicious_reservoir[0]>=1)))] != FALSE
dead was empty
(forward)formula 12,0,0.570875,19420,1,0,29456,3634,1524,27512,455,19348,92971
FORMULA QuasiCertifProtocol-COL-02-CTLFireability-12 FALSE TECHNIQUES DECISION_DIAGRAMS TOPOLOGICAL USE_NUPN
Formula is FALSE !
***************************************
original formula: AF((EX((((tsid0.s6_0>=1 + tsid1.s6_1>=1) + tsid2.s6_2>=1) + (((tsid0.c1_0>=1 * malicious_reservoir.malicious_reservoir[0]>=1) + (tsid1.c1_1>=1 * malicious_reservoir.malicious_reservoir[0]>=1)) + (tsid2.c1_2>=1 * malicious_reservoir.malicious_reservoir[0]>=1)))) * (((tsid0.Sstart_0>=1 * malicious_reservoir.malicious_reservoir[0]>=1) + (tsid1.Sstart_1>=1 * malicious_reservoir.malicious_reservoir[0]>=1)) + (tsid2.Sstart_2>=1 * malicious_reservoir.malicious_reservoir[0]>=1))))
=> equivalent forward existential formula: [FwdG(Init,!((EX((((tsid0.s6_0>=1 + tsid1.s6_1>=1) + tsid2.s6_2>=1) + (((tsid0.c1_0>=1 * malicious_reservoir.malicious_reservoir[0]>=1) + (tsid1.c1_1>=1 * malicious_reservoir.malicious_reservoir[0]>=1)) + (tsid2.c1_2>=1 * malicious_reservoir.malicious_reservoir[0]>=1)))) * (((tsid0.Sstart_0>=1 * malicious_reservoir.malicious_reservoir[0]>=1) + (tsid1.Sstart_1>=1 * malicious_reservoir.malicious_reservoir[0]>=1)) + (tsid2.Sstart_2>=1 * malicious_reservoir.malicious_reservoir[0]>=1)))))] = FALSE
(forward)formula 13,0,0.584509,19420,1,0,29996,3634,1539,28048,455,19365,94471
FORMULA QuasiCertifProtocol-COL-02-CTLFireability-13 FALSE TECHNIQUES DECISION_DIAGRAMS TOPOLOGICAL USE_NUPN
Formula is FALSE !
***************************************
original formula: AX((AF((((tsid0.s5_0>=1 * malicious_reservoir.malicious_reservoir[0]>=1) + (tsid1.s5_1>=1 * malicious_reservoir.malicious_reservoir[0]>=1)) + (tsid2.s5_2>=1 * malicious_reservoir.malicious_reservoir[0]>=1))) + a5.a5[0]>=1))
=> equivalent forward existential formula: [FwdG((EY(Init) * !(a5.a5[0]>=1)),!((((tsid0.s5_0>=1 * malicious_reservoir.malicious_reservoir[0]>=1) + (tsid1.s5_1>=1 * malicious_reservoir.malicious_reservoir[0]>=1)) + (tsid2.s5_2>=1 * malicious_reservoir.malicious_reservoir[0]>=1))))] = FALSE
(forward)formula 14,0,0.594437,19444,1,0,30688,3634,1550,28658,455,19435,96126
FORMULA QuasiCertifProtocol-COL-02-CTLFireability-14 FALSE TECHNIQUES DECISION_DIAGRAMS TOPOLOGICAL USE_NUPN
Formula is FALSE !
***************************************
original formula: AG(AF((((((tsid0.c1_0>=1 * tsidxtsid3.n9_3>=1) * tsidxtsid6.n9_6>=1) * tsidxtsid0.n9_0>=1) + (((tsid1.c1_1>=1 * tsidxtsid4.n9_4>=1) * tsidxtsid7.n9_7>=1) * tsidxtsid1.n9_1>=1)) + (((tsid2.c1_2>=1 * tsidxtsid5.n9_5>=1) * tsidxtsid8.n9_8>=1) * tsidxtsid2.n9_2>=1))))
=> equivalent forward existential formula: [FwdG(FwdU(Init,TRUE),!((((((tsid0.c1_0>=1 * tsidxtsid3.n9_3>=1) * tsidxtsid6.n9_6>=1) * tsidxtsid0.n9_0>=1) + (((tsid1.c1_1>=1 * tsidxtsid4.n9_4>=1) * tsidxtsid7.n9_7>=1) * tsidxtsid1.n9_1>=1)) + (((tsid2.c1_2>=1 * tsidxtsid5.n9_5>=1) * tsidxtsid8.n9_8>=1) * tsidxtsid2.n9_2>=1))))] = FALSE
(forward)formula 15,0,0.601422,19636,1,0,30850,3634,1561,28836,455,19435,96925
FORMULA QuasiCertifProtocol-COL-02-CTLFireability-15 FALSE TECHNIQUES DECISION_DIAGRAMS TOPOLOGICAL USE_NUPN
Formula is FALSE !
***************************************
Exit code :0
BK_STOP 1496392845240
--------------------
content from stderr:
+ export BINDIR=/home/mcc/BenchKit/
+ BINDIR=/home/mcc/BenchKit/
++ pwd
+ export MODEL=/home/mcc/execution
+ MODEL=/home/mcc/execution
+ [[ CTLFireability = StateSpace ]]
+ /home/mcc/BenchKit//runeclipse.sh /home/mcc/execution CTLFireability -its -ltsminpath /home/mcc/BenchKit//lts_install_dir/ -smt
+ ulimit -s 65536
+ java -Dosgi.requiredJavaVersion=1.6 -Xss8m -Xms40m -Xmx8192m -Declipse.pde.launch=true -Dfile.encoding=UTF-8 -classpath /home/mcc/BenchKit//eclipse/plugins/org.eclipse.equinox.launcher_1.3.201.v20161025-1711.jar org.eclipse.equinox.launcher.Main -application fr.lip6.move.gal.application.pnmcc -data /home/mcc/BenchKit//workspace -os linux -ws gtk -arch x86_64 -nl en_US -consoleLog -pnfolder /home/mcc/execution -examination CTLFireability -yices2path /home/mcc/BenchKit//yices/bin/yices -its -ltsminpath /home/mcc/BenchKit//lts_install_dir/ -smt
Jun 02, 2017 8:40:41 AM fr.lip6.move.gal.application.MccTranslator transformPNML
INFO: Parsing pnml file : /home/mcc/execution/model.pnml
Jun 02, 2017 8:40:41 AM fr.lip6.move.gal.pnml.togal.PnmlToGalTransformer transform
INFO: Detected file is not PT type :http://www.pnml.org/version-2009/grammar/symmetricnet
Jun 02, 2017 8:40:43 AM fr.lip6.move.gal.pnml.togal.PnmlToGalTransformer transform
INFO: Load time of PNML (colored model parsed with PNMLFW) : 1776 ms
Jun 02, 2017 8:40:43 AM fr.lip6.move.gal.pnml.togal.HLGALTransformer handlePage
INFO: Transformed 30 places.
Jun 02, 2017 8:40:43 AM fr.lip6.move.gal.pnml.togal.HLGALTransformer handlePage
INFO: Computed order using colors.
Jun 02, 2017 8:40:43 AM fr.lip6.move.gal.pnml.togal.HLGALTransformer handlePage
INFO: sort/places :tsidxtsid->n9,n8,n7,
Dot->malicious_reservoir,CstopAbort,SstopAbort,AstopAbort,a5,a4,a3,a2,a1,Astart,AstopOK,
tsid->n6,n5,n4,n3,n2,n1,c1,Cstart,Sstart,s2,s3,s4,s5,s6,SstopOK,CstopOK,
Jun 02, 2017 8:40:43 AM fr.lip6.move.gal.pnml.togal.HLGALTransformer handlePage
INFO: Transformed 26 transitions.
Jun 02, 2017 8:40:43 AM fr.lip6.move.gal.pnml.togal.PnmlToGalTransformer transform
INFO: Computed order based on color domains.
Jun 02, 2017 8:40:43 AM fr.lip6.move.gal.application.MccTranslator applyOrder
INFO: Applying decomposition
Jun 02, 2017 8:40:43 AM fr.lip6.move.gal.instantiate.CompositeBuilder decomposeWithOrder
INFO: Decomposing Gal with order
Jun 02, 2017 8:40:43 AM fr.lip6.move.gal.instantiate.GALRewriter flatten
INFO: Flatten gal took : 69 ms
Jun 02, 2017 8:40:44 AM fr.lip6.move.gal.instantiate.CompositeBuilder rewriteArraysToAllowPartition
INFO: Rewriting arrays n9, n8, n7, n6, n5, n4, n3, n2, n1, c1, Cstart, Sstart, s2, s3, s4, s5, s6, SstopOK, CstopOK to variables to allow decomposition.
Jun 02, 2017 8:40:44 AM fr.lip6.move.gal.instantiate.Instantiator fuseIsomorphicEffects
INFO: Removed a total of 20 redundant transitions.
Jun 02, 2017 8:40:44 AM fr.lip6.move.serialization.SerializationUtil systemToFile
INFO: Time to serialize gal into /home/mcc/execution/CTLFireability.pnml.gal : 14 ms
Jun 02, 2017 8:40:44 AM fr.lip6.move.serialization.SerializationUtil serializePropertiesForITSCTLTools
INFO: Time to serialize properties into /home/mcc/execution/CTLFireability.ctl : 3 ms
Jun 02, 2017 8:40:45 AM fr.lip6.move.gal.itstools.Runner runTool
INFO: Standard error output from running tool CommandLine [args=[/home/mcc/BenchKit/eclipse/plugins/fr.lip6.move.gal.itstools.binaries_1.0.0.201705302212/bin/its-ctl-linux64, --gc-threshold, 2000000, --quiet, -i, /home/mcc/execution/CTLFireability.pnml.gal, -t, CGAL, -ctl, /home/mcc/execution/CTLFireability.ctl], workingDir=/home/mcc/execution]
built 25 ordering constraints for composite.
Reverse transition relation is NOT exact ! Due to transitions malC1, malS6, malS5, malS4, malS3, malS2, malS1, malA5, malA3, malA4, malA2, malA1, Intersection with reachable at each step enabled. (destroyed/reverse/intersect/total) :0/30/12/42
Sequence of Actions to be Executed by the VM
This is useful if one wants to reexecute the tool in the VM from the submitted image disk.
set -x
# this is for BenchKit: configuration of major elements for the test
export BK_INPUT="S_QuasiCertifProtocol-COL-02"
export BK_EXAMINATION="CTLFireability"
export BK_TOOL="itstools"
export BK_RESULT_DIR="/tmp/BK_RESULTS/OUTPUTS"
export BK_TIME_CONFINEMENT="3600"
export BK_MEMORY_CONFINEMENT="16384"
# this is specific to your benchmark or test
export BIN_DIR="$HOME/BenchKit/bin"
# remove the execution directoty if it exists (to avoid increse of .vmdk images)
if [ -d execution ] ; then
rm -rf execution
fi
tar xzf /home/mcc/BenchKit/INPUTS/S_QuasiCertifProtocol-COL-02.tgz
mv S_QuasiCertifProtocol-COL-02 execution
# this is for BenchKit: explicit launching of the test
cd execution
echo "====================================================================="
echo " Generated by BenchKit 2-3254"
echo " Executing tool itstools"
echo " Input is S_QuasiCertifProtocol-COL-02, examination is CTLFireability"
echo " Time confinement is $BK_TIME_CONFINEMENT seconds"
echo " Memory confinement is 16384 MBytes"
echo " Number of cores is 4"
echo " Run identifier is r140-smll-149479233800193"
echo "====================================================================="
echo
echo "--------------------"
echo "content from stdout:"
echo
echo "=== Data for post analysis generated by BenchKit (invocation template)"
echo
if [ "CTLFireability" = "UpperBounds" ] ; then
echo "The expected result is a vector of positive values"
echo NUM_VECTOR
elif [ "CTLFireability" != "StateSpace" ] ; then
echo "The expected result is a vector of booleans"
echo BOOL_VECTOR
else
echo "no data necessary for post analysis"
fi
echo
if [ -f "CTLFireability.txt" ] ; then
echo "here is the order used to build the result vector(from text file)"
for x in $(grep Property CTLFireability.txt | cut -d ' ' -f 2 | sort -u) ; do
echo "FORMULA_NAME $x"
done
elif [ -f "CTLFireability.xml" ] ; then # for cunf (txt files deleted;-)
echo echo "here is the order used to build the result vector(from xml file)"
for x in $(grep '
echo "FORMULA_NAME $x"
done
fi
echo
echo "=== Now, execution of the tool begins"
echo
echo -n "BK_START "
date -u +%s%3N
echo
timeout -s 9 $BK_TIME_CONFINEMENT bash -c "/home/mcc/BenchKit/BenchKit_head.sh 2> STDERR ; echo ; echo -n \"BK_STOP \" ; date -u +%s%3N"
if [ $? -eq 137 ] ; then
echo
echo "BK_TIME_CONFINEMENT_REACHED"
fi
echo
echo "--------------------"
echo "content from stderr:"
echo
cat STDERR ;

