About the Execution of LoLa for QuasiCertifProtocol-PT-18
| Execution Summary | |||||
| Max Memory Used (MB) |
Time wait (ms) | CPU Usage (ms) | I/O Wait (ms) | Computed Result | Execution Status |
| 5088.180 | 798444.00 | 1587799.00 | 2356.00 | F??FFFFFTTFTFFTF | normal |
Execution Chart
We display below the execution chart for this examination (boot time has been removed).
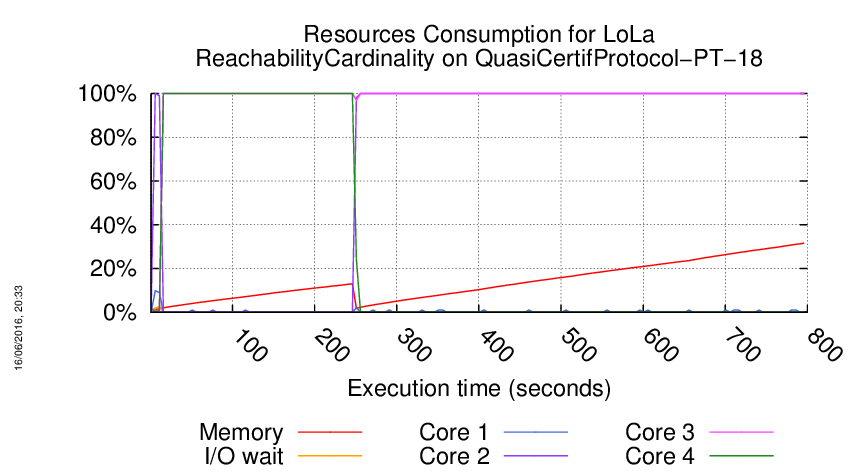
Trace from the execution
Waiting for the VM to be ready (probing ssh)
...............................................................
=====================================================================
Generated by BenchKit 2-2979
Executing tool lola
Input is QuasiCertifProtocol-PT-18, examination is ReachabilityCardinality
Time confinement is 3600 seconds
Memory confinement is 16384 MBytes
Number of cores is 4
Run identifier is r098kn-smll-146369140300106
=====================================================================
--------------------
content from stdout:
=== Data for post analysis generated by BenchKit (invocation template)
The expected result is a vector of booleans
BOOL_VECTOR
here is the order used to build the result vector(from text file)
FORMULA_NAME QuasiCertifProtocol-COL-18-ReachabilityCardinality-0
FORMULA_NAME QuasiCertifProtocol-COL-18-ReachabilityCardinality-1
FORMULA_NAME QuasiCertifProtocol-COL-18-ReachabilityCardinality-10
FORMULA_NAME QuasiCertifProtocol-COL-18-ReachabilityCardinality-11
FORMULA_NAME QuasiCertifProtocol-COL-18-ReachabilityCardinality-12
FORMULA_NAME QuasiCertifProtocol-COL-18-ReachabilityCardinality-13
FORMULA_NAME QuasiCertifProtocol-COL-18-ReachabilityCardinality-14
FORMULA_NAME QuasiCertifProtocol-COL-18-ReachabilityCardinality-15
FORMULA_NAME QuasiCertifProtocol-COL-18-ReachabilityCardinality-2
FORMULA_NAME QuasiCertifProtocol-COL-18-ReachabilityCardinality-3
FORMULA_NAME QuasiCertifProtocol-COL-18-ReachabilityCardinality-4
FORMULA_NAME QuasiCertifProtocol-COL-18-ReachabilityCardinality-5
FORMULA_NAME QuasiCertifProtocol-COL-18-ReachabilityCardinality-6
FORMULA_NAME QuasiCertifProtocol-COL-18-ReachabilityCardinality-7
FORMULA_NAME QuasiCertifProtocol-COL-18-ReachabilityCardinality-8
FORMULA_NAME QuasiCertifProtocol-COL-18-ReachabilityCardinality-9
=== Now, execution of the tool begins
BK_START 1463704525929
bkconf 3600
make: Nothing to be done for 'prepare'.
in benchkit_head lolaszeit 3540
ReachabilityCardinality @ QuasiCertifProtocol-PT-18
FORMULA QuasiCertifProtocol-COL-18-ReachabilityCardinality-0 FALSE TECHNIQUES PARALLEL_PROCESSING EXPLICIT SAT_SMT STATE_COMPRESSION STUBBORN_SETS TOPOLOGICAL
FORMULA QuasiCertifProtocol-COL-18-ReachabilityCardinality-1 CANNOT_COMPUTE
FORMULA QuasiCertifProtocol-COL-18-ReachabilityCardinality-2 TRUE TECHNIQUES PARALLEL_PROCESSING EXPLICIT SAT_SMT STATE_COMPRESSION STUBBORN_SETS TOPOLOGICAL
FORMULA QuasiCertifProtocol-COL-18-ReachabilityCardinality-3 TRUE TECHNIQUES PARALLEL_PROCESSING EXPLICIT SAT_SMT STATE_COMPRESSION STUBBORN_SETS TOPOLOGICAL
FORMULA QuasiCertifProtocol-COL-18-ReachabilityCardinality-4 FALSE TECHNIQUES PARALLEL_PROCESSING EXPLICIT SAT_SMT STATE_COMPRESSION STUBBORN_SETS TOPOLOGICAL
FORMULA QuasiCertifProtocol-COL-18-ReachabilityCardinality-5 TRUE TECHNIQUES PARALLEL_PROCESSING EXPLICIT SAT_SMT STATE_COMPRESSION STUBBORN_SETS TOPOLOGICAL
FORMULA QuasiCertifProtocol-COL-18-ReachabilityCardinality-6 FALSE TECHNIQUES PARALLEL_PROCESSING EXPLICIT SAT_SMT STATE_COMPRESSION STUBBORN_SETS TOPOLOGICAL
FORMULA QuasiCertifProtocol-COL-18-ReachabilityCardinality-7 FALSE TECHNIQUES PARALLEL_PROCESSING EXPLICIT SAT_SMT STATE_COMPRESSION STUBBORN_SETS TOPOLOGICAL
FORMULA QuasiCertifProtocol-COL-18-ReachabilityCardinality-8 TRUE TECHNIQUES PARALLEL_PROCESSING EXPLICIT SAT_SMT STATE_COMPRESSION STUBBORN_SETS TOPOLOGICAL
FORMULA QuasiCertifProtocol-COL-18-ReachabilityCardinality-9 FALSE TECHNIQUES PARALLEL_PROCESSING EXPLICIT SAT_SMT STATE_COMPRESSION STUBBORN_SETS TOPOLOGICAL
FORMULA QuasiCertifProtocol-COL-18-ReachabilityCardinality-10 CANNOT_COMPUTE
FORMULA QuasiCertifProtocol-COL-18-ReachabilityCardinality-11 FALSE TECHNIQUES PARALLEL_PROCESSING EXPLICIT SAT_SMT STATE_COMPRESSION STUBBORN_SETS TOPOLOGICAL
FORMULA QuasiCertifProtocol-COL-18-ReachabilityCardinality-12 FALSE TECHNIQUES PARALLEL_PROCESSING EXPLICIT SAT_SMT STATE_COMPRESSION STUBBORN_SETS TOPOLOGICAL
FORMULA QuasiCertifProtocol-COL-18-ReachabilityCardinality-13 FALSE TECHNIQUES PARALLEL_PROCESSING EXPLICIT SAT_SMT STATE_COMPRESSION STUBBORN_SETS TOPOLOGICAL
FORMULA QuasiCertifProtocol-COL-18-ReachabilityCardinality-14 FALSE TECHNIQUES PARALLEL_PROCESSING EXPLICIT SAT_SMT STATE_COMPRESSION STUBBORN_SETS TOPOLOGICAL
FORMULA QuasiCertifProtocol-COL-18-ReachabilityCardinality-15 FALSE TECHNIQUES PARALLEL_PROCESSING EXPLICIT SAT_SMT STATE_COMPRESSION STUBBORN_SETS TOPOLOGICAL
lola: LoLA will run for 3540 seconds at most (--timelimit)
lola: NET
lola: reading net from model.pnml.lola
lola: finished parsing
lola: closed net file model.pnml.lola
lola: 1694/65536 symbol table entries, 0 collisions
lola: preprocessing...
lola: finding significant places
lola: 1398 places, 296 transitions, 295 significant places
lola: computing forward-conflicting sets
lola: computing back-conflicting sets
lola: 391 transition conflict sets
lola: TASK
lola: reading formula from QuasiCertifProtocol-COL-18-ReachabilityCardinality.task
lola: read: AG ((((3 <= n5_18 + n5_16 + n5_17 + n5_14 + n5_15 + n5_12 + n5_13 + n5_10 + n5_11 + n5_8 + n5_9 + n5_6 + n5_7 + n5_4 + n5_5 + n5_2 + n5_3 + n5_1 + n5_0 OR 3 <= n1_4 + n1_5 + n1_2 + n1_3 + n1_0 + n1_1 + n1_12 + n1_13 + n1_10 + n1_11 + n1_8 + n1_9 + n1_6 + n1_7 + n1_16 + n1_17 + n1_14 + n1_15 + n1_18) OR !(1 <= SstopAbort)) OR !((Astart <= SstopOK_17 + SstopOK_16 + SstopOK_18 + SstopOK_13 + SstopOK_... (shortened)
lola: formula length: 45759
lola: computing a collection of formulas
lola: RUNNING
lola: subprocess 0 will run for 220 seconds at most (--localtimelimit=0)
lola: ========================================
lola: ...considering subproblem: AG ((-n5_9 + -n5_8 + -n5_7 + -n5_6 + -n5_5 + -n5_4 + -n5_3 + -n5_2 + -n5_1 + -n5_0 + -n5_18 + -n5_17 + -n5_16 + -n5_15 + -n5_14 + -n5_13 + -n5_12 + -n5_11 + -n5_10 <= -3 OR (-n1_18 + -n1_17 + -n1_16 + -n1_15 + -n1_14 + -n1_13 + -n1_12 + -n1_11 + -n1_10 + -n1_0 + -n1_1 + -n1_2 + -n1_3 + -n1_4 + -n1_5 + -n1_6 + -n1_7 + -n1_8 + -n1_9 <= -3 OR (-SstopAbort > -1 OR (Astart + -SstopOK_7 + -SstopOK_6 + -... (shortened)
lola: ========================================
lola: SUBTASK
lola: checking invariance
lola: Planning: workflow for reachability check: stateequation||search (--findpath=off)
lola: STORE
lola: using a bit-perfect encoder (--encoder=bit)
lola: using 1180 bytes per marking, with 0 unused bits
lola: using a prefix tree store (--store=prefix)
lola: SEARCH
lola: using reachability graph (--search=depth)
lola: using reachability preserving stubborn set method with insertion algorithm (--stubborn=tarjan)
lola: RUNNING
lola: Transformation into DNF: expect 5 literals
lola: write sara problem file to QuasiCertifProtocol-COL-18-ReachabilityCardinality.sara
lola: calling and running sara
sara: try reading problem file QuasiCertifProtocol-COL-18-ReachabilityCardinality.sara.
sara: place or transition ordering is non-deterministic
lola: sara:solution produced
lola: SUBRESULT
lola: result: no
lola: The predicate is not invariant.
lola: ========================================
lola: subprocess 1 will run for 235 seconds at most (--localtimelimit=0)
lola: ========================================
lola: ...considering subproblem: EF ((-n1_18 + -n1_17 + -n1_16 + -n1_15 + -n1_14 + -n1_13 + -n1_12 + -n1_11 + -n1_10 + AstopOK + -n1_0 + -n1_1 + -n1_2 + -n1_3 + -n1_4 + -n1_5 + -n1_6 + -n1_7 + -n1_8 + -n1_9 > 0 AND (-n8_10_9 + -n8_10_8 + -n8_10_7 + -n8_10_6 + -n8_10_5 + -n8_10_4 + -n8_10_3 + -n8_10_2 + -n8_10_1 + -n8_10_0 + -n8_14_11 + -n8_14_12 + -n8_14_13 + -n8_14_14 + -n8_14_15 + -n8_14_16 + -n8_14_17 + -n8_14_18 + -n8_0_18 + ... (shortened)
lola: ========================================
lola: SUBTASK
lola: checking reachability
lola: Planning: workflow for reachability check: stateequation||search (--findpath=off)
lola: STORE
lola: using a bit-perfect encoder (--encoder=bit)
lola: using 1180 bytes per marking, with 0 unused bits
lola: using a prefix tree store (--store=prefix)
lola: SEARCH
lola: using reachability graph (--search=depth)
lola: using reachability preserving stubborn set method with insertion algorithm (--stubborn=tarjan)
lola: RUNNING
lola: Transformation into DNF: expect 3 literals
lola: write sara problem file to QuasiCertifProtocol-COL-18-ReachabilityCardinality.sara
lola: calling and running sara
sara: try reading problem file QuasiCertifProtocol-COL-18-ReachabilityCardinality.sara.
sara: place or transition ordering is non-deterministic
lola: local time limit reached - aborting
lola: Child process aborted or communication problem between parent and child process
lola: subprocess 2 will run for 235 seconds at most (--localtimelimit=0)
lola: ========================================
lola: ...considering subproblem: EF (-AstopOK <= -1)
lola: ========================================
lola: SUBTASK
lola: checking reachability
lola: Planning: workflow for reachability check: stateequation||search (--findpath=off)
lola: STORE
lola: using a bit-perfect encoder (--encoder=bit)
lola: using 1180 bytes per marking, with 0 unused bits
lola: using a prefix tree store (--store=prefix)
lola: SEARCH
lola: using reachability graph (--search=depth)
lola: using reachability preserving stubborn set method with insertion algorithm (--stubborn=tarjan)
lola: RUNNING
lola: Transformation into DNF: expect 1 literals
lola: write sara problem file to QuasiCertifProtocol-COL-18-ReachabilityCardinality-2.sara
lola: SUBRESULT
lola: result: yes
lola: The predicate is reachable.
lola: ========================================
lola: subprocess 3 will run for 253 seconds at most (--localtimelimit=0)
lola: ========================================
lola: ...considering subproblem: AG ((-n1_18 + -n1_17 + -n1_16 + -n1_15 + -n1_14 + -n1_13 + -n1_12 + -n1_11 + -n1_10 + -n1_0 + -n1_1 + -n1_2 + -n1_3 + -n1_4 + -n1_5 + -n1_6 + -n1_7 + -n1_8 + -n1_9 <= -1 OR (-SstopAbort + a5 <= 0 OR (-s2_10 + -s2_11 + -s2_12 + -s2_13 + -s2_14 + -s2_15 + -s2_16 + -s2_17 + -s2_18 + -s2_0 + -s2_1 + -s2_2 + -s2_3 + -s2_4 + -s2_5 + -s2_6 + -s2_7 + -s2_8 + -s2_9 <= -3 OR (-s2_10 + -s2_11 + -s2_12 + -s2_... (shortened)
lola: ========================================
lola: SUBTASK
lola: checking invariance
lola: Planning: workflow for reachability check: stateequation||search (--findpath=off)
lola: STORE
lola: using a bit-perfect encoder (--encoder=bit)
lola: using 1180 bytes per marking, with 0 unused bits
lola: using a prefix tree store (--store=prefix)
lola: SEARCH
lola: using reachability graph (--search=depth)
lola: using reachability preserving stubborn set method with insertion algorithm (--stubborn=tarjan)
lola: RUNNING
lola: Transformation into DNF: expect 6 literals
lola: write sara problem file to QuasiCertifProtocol-COL-18-ReachabilityCardinality-3.sara
lola: calling and running sara
sara: try reading problem file QuasiCertifProtocol-COL-18-ReachabilityCardinality-3.sara.
sara: place or transition ordering is non-deterministic
lola: sara:solution impossible
lola: SUBRESULT
lola: result: yes
lola: The predicate is invariant.
lola: ========================================
lola: subprocess 4 will run for 274 seconds at most (--localtimelimit=0)
lola: ========================================
lola: ...considering subproblem: AG ((-s2_10 + -s2_11 + -s2_12 + -s2_13 + -s2_14 + -s2_15 + -s2_16 + -s2_17 + -s2_18 + s6_10 + s6_11 + s6_12 + s6_13 + s6_14 + s6_15 + s6_16 + s6_17 + s6_18 + s6_9 + s6_8 + s6_7 + s6_6 + s6_5 + s6_4 + s6_3 + s6_2 + s6_1 + s6_0 + -s2_0 + -s2_1 + -s2_2 + -s2_3 + -s2_4 + -s2_5 + -s2_6 + -s2_7 + -s2_8 + -s2_9 <= 0 OR (-Sstart_18 + -Sstart_17 + -Sstart_16 + -Sstart_15 + -Sstart_14 + -Sstart_13 + -Sstart... (shortened)
lola: ========================================
lola: SUBTASK
lola: checking invariance
lola: Planning: workflow for reachability check: stateequation||search (--findpath=off)
lola: STORE
lola: using a bit-perfect encoder (--encoder=bit)
lola: using 1180 bytes per marking, with 0 unused bits
lola: using a prefix tree store (--store=prefix)
lola: SEARCH
lola: using reachability graph (--search=depth)
lola: using reachability preserving stubborn set method with insertion algorithm (--stubborn=tarjan)
lola: RUNNING
lola: Transformation into DNF: expect 4 literals
lola: write sara problem file to QuasiCertifProtocol-COL-18-ReachabilityCardinality-4.sara
lola: calling and running sara
sara: try reading problem file QuasiCertifProtocol-COL-18-ReachabilityCardinality-4.sara.
sara: place or transition ordering is non-deterministic
lola: sara:solution produced
lola: SUBRESULT
lola: result: no
lola: The predicate is not invariant.
lola: ========================================
lola: subprocess 5 will run for 299 seconds at most (--localtimelimit=0)
lola: ========================================
lola: ...considering subproblem: EF ((-n4_9 + -n4_8 + -n4_7 + -n4_6 + -n4_5 + -n4_4 + -n4_3 + -n4_2 + -n4_1 + -n4_0 + -n4_18 + -n4_17 + -n4_16 + -n4_15 + -n4_14 + -n4_13 + -n4_12 + -n4_11 + -n4_10 <= -1 OR -n3_18 + -n3_17 + -n3_16 + -n3_15 + -n3_14 + -n3_13 + -n3_12 + -n3_11 + -n3_10 + -n3_0 + -n3_1 + -n3_2 + -n3_3 + -n3_4 + -n3_5 + Sstart_18 + Sstart_17 + Sstart_16 + Sstart_15 + Sstart_14 + Sstart_13 + Sstart_12 + Sstart_11 + Ss... (shortened)
lola: ========================================
lola: SUBTASK
lola: checking reachability
lola: Planning: workflow for reachability check: stateequation||search (--findpath=off)
lola: STORE
lola: using a bit-perfect encoder (--encoder=bit)
lola: using 1180 bytes per marking, with 0 unused bits
lola: using a prefix tree store (--store=prefix)
lola: SEARCH
lola: using reachability graph (--search=depth)
lola: using reachability preserving stubborn set method with insertion algorithm (--stubborn=tarjan)
lola: RUNNING
lola: Transformation into DNF: expect 2 literals
lola: SUBRESULT
lola: result: yes
lola: The predicate is reachable.
lola: ========================================
lola: subprocess 6 will run for 329 seconds at most (--localtimelimit=0)
lola: ========================================
lola: ...considering subproblem: EF (((-AstopAbort <= -2 OR (-n7_5_9 + -n7_5_8 + -n7_5_7 + -n7_5_6 + -n7_5_5 + -n7_5_4 + -n7_5_3 + -n7_5_2 + -n7_5_1 + -n7_5_0 + -n7_6_1 + -n7_16_9 + -n7_16_8 + -n7_16_7 + -n7_16_6 + -n7_16_5 + -n7_16_4 + -n7_16_3 + -n7_16_2 + -n7_16_1 + -n7_16_0 + -n7_9_18 + -n7_9_17 + -n7_9_16 + -n7_9_15 + -n7_9_14 + -n7_9_13 + -n7_9_12 + -n7_9_11 + -n7_9_10 + -n7_15_18 + -n7_15_17 + -n7_15_16 + -n7_15_15 + -n7_1... (shortened)
lola: ========================================
lola: SUBTASK
lola: checking reachability
lola: Planning: workflow for reachability check: stateequation||search (--findpath=off)
lola: STORE
lola: using a bit-perfect encoder (--encoder=bit)
lola: using 1180 bytes per marking, with 0 unused bits
lola: using a prefix tree store (--store=prefix)
lola: SEARCH
lola: using reachability graph (--search=depth)
lola: using reachability preserving stubborn set method with insertion algorithm (--stubborn=tarjan)
lola: RUNNING
lola: Transformation into DNF: expect 5 literals
lola: write sara problem file to QuasiCertifProtocol-COL-18-ReachabilityCardinality-6.sara
lola: calling and running sara
sara: try reading problem file QuasiCertifProtocol-COL-18-ReachabilityCardinality-6.sara.
sara: place or transition ordering is non-deterministic
lola: sara:solution impossible
lola: SUBRESULT
lola: result: no
lola: The predicate is unreachable.
lola: ========================================
lola: subprocess 7 will run for 365 seconds at most (--localtimelimit=0)
lola: ========================================
lola: ...considering subproblem: AG (((-Cstart_9 + -Cstart_8 + -Cstart_7 + -Cstart_6 + -Cstart_5 + -Cstart_4 + -Cstart_3 + -Cstart_2 + -Cstart_1 + -Cstart_0 + -Cstart_11 + -Cstart_12 + -Cstart_13 + -Cstart_14 + -Cstart_15 + -Cstart_16 + -Cstart_17 + -Cstart_18 + -Cstart_10 + s4_10 + s4_11 + s4_12 + s4_13 + s4_14 + s4_15 + s4_16 + s4_17 + s4_18 + s4_9 + s4_8 + s4_7 + s4_6 + s4_5 + s4_4 + s4_3 + s4_2 + s4_1 + s4_0 <= 0 OR (-a2 <= -... (shortened)
lola: ========================================
lola: SUBTASK
lola: checking invariance
lola: Planning: workflow for reachability check: stateequation||search (--findpath=off)
lola: STORE
lola: using a bit-perfect encoder (--encoder=bit)
lola: using 1180 bytes per marking, with 0 unused bits
lola: using a prefix tree store (--store=prefix)
lola: SEARCH
lola: using reachability graph (--search=depth)
lola: using reachability preserving stubborn set method with insertion algorithm (--stubborn=tarjan)
lola: RUNNING
lola: Transformation into DNF: expect 5 literals
lola: write sara problem file to QuasiCertifProtocol-COL-18-ReachabilityCardinality-7.sara
lola: calling and running sara
sara: try reading problem file QuasiCertifProtocol-COL-18-ReachabilityCardinality-7.sara.
sara: place or transition ordering is non-deterministic
lola: sara:solution produced
lola: SUBRESULT
lola: result: no
lola: The predicate is not invariant.
lola: ========================================
lola: subprocess 8 will run for 411 seconds at most (--localtimelimit=0)
lola: ========================================
lola: ...considering subproblem: EF ((-n7_5_9 + -n7_5_8 + -n7_5_7 + -n7_5_6 + -n7_5_5 + -n7_5_4 + -n7_5_3 + -n7_5_2 + -n7_5_1 + -n7_5_0 + -n7_6_1 + -n7_16_9 + -n7_16_8 + -n7_16_7 + -n7_16_6 + -n7_16_5 + -n7_16_4 + -n7_16_3 + -n7_16_2 + -n7_16_1 + -n7_16_0 + -n7_9_18 + -n7_9_17 + -n7_9_16 + -n7_9_15 + -n7_9_14 + -n7_9_13 + -n7_9_12 + -n7_9_11 + -n7_9_10 + -n7_15_18 + -n7_15_17 + -n7_15_16 + -n7_15_15 + -n7_15_14 + -n7_15_13 + -n7_... (shortened)
lola: ========================================
lola: SUBTASK
lola: checking reachability
lola: Planning: workflow for reachability check: stateequation||search (--findpath=off)
lola: STORE
lola: using a bit-perfect encoder (--encoder=bit)
lola: using 1180 bytes per marking, with 0 unused bits
lola: using a prefix tree store (--store=prefix)
lola: SEARCH
lola: using reachability graph (--search=depth)
lola: using reachability preserving stubborn set method with insertion algorithm (--stubborn=tarjan)
lola: RUNNING
lola: SUBRESULT
lola: result: yes
lola: The predicate is reachable.
lola: Transformation into DNF: expect 4 literals
lola: write sara problem file to QuasiCertifProtocol-COL-18-ReachabilityCardinality-8.sara
lola: subprocess 9 will run for 470 seconds at most (--localtimelimit=0)
lola: ========================================
lola: ...considering subproblem: AG (-CstopAbort > -3)
lola: ========================================
lola: SUBTASK
lola: checking invariance
lola: Planning: workflow for reachability check: stateequation||search (--findpath=off)
lola: STORE
lola: using a bit-perfect encoder (--encoder=bit)
lola: using 1180 bytes per marking, with 0 unused bits
lola: using a prefix tree store (--store=prefix)
lola: SEARCH
lola: using reachability graph (--search=depth)
lola: ========================================
lola: using reachability preserving stubborn set method with insertion algorithm (--stubborn=tarjan)
lola: lola: calling and running saraRUNNING
lola: Transformation into DNF: expect 1 literals
lola: write sara problem file to QuasiCertifProtocol-COL-18-ReachabilityCardinality-9.sara
lola: calling and running sara
lola: SUBRESULT
lola: result: no
lola: The predicate is not invariant.
lola: ========================================
sara: try reading problem file QuasiCertifProtocol-COL-18-ReachabilityCardinality-8.sara.
lola: subprocess 10 will run for 548 seconds at most (--localtimelimit=0)
lola: ========================================
lola: ...considering subproblem: AG (((-s2_10 + -s2_11 + -s2_12 + -s2_13 + -s2_14 + -s2_15 + -s2_16 + -s2_17 + -s2_18 + a3 + -s2_0 + -s2_1 + -s2_2 + -s2_3 + -s2_4 + -s2_5 + -s2_6 + -s2_7 + -s2_8 + -s2_9 > 0 AND a4 + -Sstart_18 + -Sstart_17 + -Sstart_16 + -Sstart_15 + -Sstart_14 + -Sstart_13 + -Sstart_12 + -Sstart_11 + -Sstart_10 + -Sstart_0 + -Sstart_1 + -Sstart_2 + -Sstart_3 + -Sstart_4 + -Sstart_5 + -Sstart_6 + -Sstart_7 + -Sst... (shortened)
lola: ========================================
lola: SUBTASK
lola: checking invariance
lola: Planning: workflow for reachability check: stateequation||search (--findpath=off)
lola: STORE
lola: using a bit-perfect encoder (--encoder=bit)
lola: using 1180 bytes per marking, with 0 unused bits
lola: using a prefix tree store (--store=prefix)
lola: SEARCH
lola: using reachability graph (--search=depth)
lola: using reachability preserving stubborn set method with insertion algorithm (--stubborn=tarjan)
lola: RUNNING
lola: Transformation into DNF: expect 6 literals
lola: write sara problem file to QuasiCertifProtocol-COL-18-ReachabilityCardinality-10.sara
lola: calling and running sara
sara: try reading problem file QuasiCertifProtocol-COL-18-ReachabilityCardinality-10.sara.
sara: place or transition ordering is non-deterministic
sara: place or transition ordering is non-deterministic
lola: local time limit reached - aborting
lola: Child process aborted or communication problem between parent and child process
lola: subprocess 11 will run for 548 seconds at most (--localtimelimit=0)
lola: ========================================
lola: ...considering subproblem: AG ((-a5 <= -2 OR -CstopOK_18 + -CstopOK_17 + -CstopOK_16 + -CstopOK_15 + -CstopOK_14 + -CstopOK_13 + -CstopOK_12 + -CstopOK_11 + -CstopOK_10 + -CstopOK_9 + -CstopOK_8 + -CstopOK_7 + -CstopOK_6 + -CstopOK_5 + -CstopOK_4 + -CstopOK_3 + -CstopOK_2 + -CstopOK_1 + -CstopOK_0 + a5 <= 0))
lola: ========================================
lola: SUBTASK
lola: checking invariance
lola: Planning: workflow for reachability check: stateequation||search (--findpath=off)
lola: STORE
lola: using a bit-perfect encoder (--encoder=bit)
lola: using 1180 bytes per marking, with 0 unused bits
lola: using a prefix tree store (--store=prefix)
lola: SEARCH
lola: using reachability graph (--search=depth)
lola: using reachability preserving stubborn set method with insertion algorithm (--stubborn=tarjan)
lola: RUNNING
lola: Transformation into DNF: expect 2 literals
lola: write sara problem file to QuasiCertifProtocol-COL-18-ReachabilityCardinality-11.sara
lola: SUBRESULT
lola: result: no
lola: The predicate is not invariant.
lola: ========================================
lola: subprocess 12 will run for 685 seconds at most (--localtimelimit=0)
lola: ========================================
lola: ...considering subproblem: AG ((-CstopAbort + a1 > 0 OR (-c1_9 + -c1_10 + -c1_11 + -c1_12 + -c1_13 + -c1_14 + -c1_15 + -c1_16 + -c1_17 + -c1_18 + -c1_0 + -c1_1 + -c1_2 + -c1_3 + -c1_4 + -c1_5 + -c1_6 + -c1_7 + -c1_8 > -3 OR -n3_18 + -n3_17 + -n3_16 + -n3_15 + -n3_14 + -n3_13 + -n3_12 + -n3_11 + -n3_10 + AstopOK + -n3_0 + -n3_1 + -n3_2 + -n3_3 + -n3_4 + -n3_5 + -n3_6 + -n3_7 + -n3_8 + -n3_9 <= 0)))
lola: ========================================
lola: SUBTASK
lola: checking invariance
lola: Planning: workflow for reachability check: stateequation||search (--findpath=off)
lola: STORE
lola: using a bit-perfect encoder (--encoder=bit)
lola: using 1180 bytes per marking, with 0 unused bits
lola: using a prefix tree store (--store=prefix)
lola: SEARCH
lola: using reachability graph (--search=depth)
lola: using reachability preserving stubborn set method with insertion algorithm (--stubborn=tarjan)
lola: RUNNING
lola: Transformation into DNF: expect 3 literals
lola: write sara problem file to QuasiCertifProtocol-COL-18-ReachabilityCardinality-12.sara
lola: calling and running sara
sara: try reading problem file QuasiCertifProtocol-COL-18-ReachabilityCardinality-12.sara.
sara: place or transition ordering is non-deterministic
lola: sara:solution produced
lola: SUBRESULT
lola: result: no
lola: The predicate is not invariant.
lola: ========================================
lola: subprocess 13 will run for 914 seconds at most (--localtimelimit=0)
lola: ========================================
lola: ...considering subproblem: AG (-n8_10_9 + -n8_10_8 + -n8_10_7 + -n8_10_6 + -n8_10_5 + -n8_10_4 + -n8_10_3 + -n8_10_2 + -n8_10_1 + -n8_10_0 + -n8_14_11 + -n8_14_12 + -n8_14_13 + -n8_14_14 + -n8_14_15 + -n8_14_16 + -n8_14_17 + -n8_14_18 + -n8_0_18 + -n8_0_17 + -n8_0_16 + -n8_0_15 + -n8_0_14 + -n8_0_13 + -n8_0_12 + -n8_0_11 + -n8_0_10 + -n8_11_1 + -n8_11_2 + -n8_11_3 + -n8_11_4 + -n8_11_5 + -n8_11_6 + -n8_11_7 + -n8_11_8 + -n8... (shortened)
lola: ========================================
lola: SUBTASK
lola: checking invariance
lola: Planning: workflow for reachability check: stateequation||search (--findpath=off)
lola: STORE
lola: using a bit-perfect encoder (--encoder=bit)
lola: using 1180 bytes per marking, with 0 unused bits
lola: using a prefix tree store (--store=prefix)
lola: SEARCH
lola: using reachability graph (--search=depth)
lola: using reachability preserving stubborn set method with insertion algorithm (--stubborn=tarjan)
lola: RUNNING
lola: Transformation into DNF: expect 1 literals
lola: write sara problem file to QuasiCertifProtocol-COL-18-ReachabilityCardinality-13.sara
lola: SUBRESULT
lola: result: no
lola: The predicate is not invariant.
lola: ========================================
lola: subprocess 14 will run for 1371 seconds at most (--localtimelimit=0)
lola: ========================================
lola: ...considering subproblem: AG (CstopAbort + -s4_10 + -s4_11 + -s4_12 + -s4_13 + -s4_14 + -s4_15 + -s4_16 + -s4_17 + -s4_18 + -s4_9 + -s4_8 + -s4_7 + -s4_6 + -s4_5 + -s4_4 + -s4_3 + -s4_2 + -s4_1 + -s4_0 <= 0)
lola: ========================================
lola: SUBTASK
lola: checking invariance
lola: Planning: workflow for reachability check: stateequation||search (--findpath=off)
lola: STORE
lola: using a bit-perfect encoder (--encoder=bit)
lola: using 1180 bytes per marking, with 0 unused bits
lola: using a prefix tree store (--store=prefix)
lola: SEARCH
lola: using reachability graph (--search=depth)
lola: using reachability preserving stubborn set method with insertion algorithm (--stubborn=tarjan)
lola: RUNNING
lola: Transformation into DNF: expect 1 literals
lola: write sara problem file to QuasiCertifProtocol-COL-18-ReachabilityCardinality-14.sara
lola: calling and running sara
sara: try reading problem file QuasiCertifProtocol-COL-18-ReachabilityCardinality-14.sara.
sara: place or transition ordering is non-deterministic
lola: sara:solution produced
lola: SUBRESULT
lola: result: no
lola: The predicate is not invariant.
lola: ========================================
lola: subprocess 15 will run for 2742 seconds at most (--localtimelimit=0)
lola: ========================================
lola: ...considering subproblem: EF ((-AstopAbort <= -3 AND -n5_9 + -n5_8 + -n5_7 + -n5_6 + -n5_5 + -n5_4 + -n5_3 + -n5_2 + -n5_1 + -n5_0 + -n5_18 + -n5_17 + -n5_16 + -n5_15 + -n5_14 + -n5_13 + -n5_12 + -n5_11 + c1_9 + c1_10 + c1_11 + c1_12 + c1_13 + c1_14 + c1_15 + c1_16 + c1_17 + c1_18 + c1_0 + c1_1 + c1_2 + c1_3 + c1_4 + c1_5 + c1_6 + c1_7 + c1_8 + -n5_10 <= 0))
lola: ========================================
lola: SUBTASK
lola: checking reachability
lola: Planning: workflow for reachability check: stateequation||search (--findpath=off)
lola: STORE
lola: using a bit-perfect encoder (--encoder=bit)
lola: using 1180 bytes per marking, with 0 unused bits
lola: using a prefix tree store (--store=prefix)
lola: SEARCH
lola: using reachability graph (--search=depth)
lola: using reachability preserving stubborn set method with insertion algorithm (--stubborn=tarjan)
lola: RUNNING
lola: Transformation into DNF: expect 2 literals
lola: write sara problem file to QuasiCertifProtocol-COL-18-ReachabilityCardinality-15.sara
lola: calling and running sara
sara: try reading problem file QuasiCertifProtocol-COL-18-ReachabilityCardinality-15.sara.
sara: place or transition ordering is non-deterministic
lola: sara:solution impossible
lola: SUBRESULT
lola: result: no
lola: The predicate is unreachable.
lola: ========================================
lola: RESULT
lola: summary: no unknown yes yes no yes no no yes no unknown no no no no no
BK_STOP 1463705324373
--------------------
content from stderr:
Sequence of Actions to be Executed by the VM
This is useful if one wants to reexecute the tool in the VM from the submitted image disk.
set -x
# this is for BenchKit: configuration of major elements for the test
export BK_INPUT="QuasiCertifProtocol-PT-18"
export BK_EXAMINATION="ReachabilityCardinality"
export BK_TOOL="lola"
export BK_RESULT_DIR="/root/BK_RESULTS/OUTPUTS"
export BK_TIME_CONFINEMENT="3600"
export BK_MEMORY_CONFINEMENT="16384"
# this is specific to your benchmark or test
export BIN_DIR="$HOME/BenchKit/bin"
# remove the execution directoty if it exists (to avoid increse of .vmdk images)
if [ -d execution ] ; then
rm -rf execution
fi
tar xzf /home/mcc/BenchKit/INPUTS/QuasiCertifProtocol-PT-18.tgz
mv QuasiCertifProtocol-PT-18 execution
# this is for BenchKit: explicit launching of the test
cd execution
echo "====================================================================="
echo " Generated by BenchKit 2-2979"
echo " Executing tool lola"
echo " Input is QuasiCertifProtocol-PT-18, examination is ReachabilityCardinality"
echo " Time confinement is $BK_TIME_CONFINEMENT seconds"
echo " Memory confinement is 16384 MBytes"
echo " Number of cores is 4"
echo " Run identifier is r098kn-smll-146369140300106"
echo "====================================================================="
echo
echo "--------------------"
echo "content from stdout:"
echo
echo "=== Data for post analysis generated by BenchKit (invocation template)"
echo
if [ "ReachabilityCardinality" = "UpperBounds" ] ; then
echo "The expected result is a vector of positive values"
echo NUM_VECTOR
elif [ "ReachabilityCardinality" != "StateSpace" ] ; then
echo "The expected result is a vector of booleans"
echo BOOL_VECTOR
else
echo "no data necessary for post analysis"
fi
echo
if [ -f "ReachabilityCardinality.txt" ] ; then
echo "here is the order used to build the result vector(from text file)"
for x in $(grep Property ReachabilityCardinality.txt | cut -d ' ' -f 2 | sort -u) ; do
echo "FORMULA_NAME $x"
done
elif [ -f "ReachabilityCardinality.xml" ] ; then # for cunf (txt files deleted;-)
echo echo "here is the order used to build the result vector(from xml file)"
for x in $(grep '
echo "FORMULA_NAME $x"
done
fi
echo
echo "=== Now, execution of the tool begins"
echo
echo -n "BK_START "
date -u +%s%3N
echo
timeout -s 9 $BK_TIME_CONFINEMENT bash -c "/home/mcc/BenchKit/BenchKit_head.sh 2> STDERR ; echo ; echo -n \"BK_STOP \" ; date -u +%s%3N"
if [ $? -eq 137 ] ; then
echo
echo "BK_TIME_CONFINEMENT_REACHED"
fi
echo
echo "--------------------"
echo "content from stderr:"
echo
cat STDERR ;

