About the Execution of ITS-Tools for S_QuasiCertifProtocol-PT-02
| Execution Summary | |||||
| Max Memory Used (MB) |
Time wait (ms) | CPU Usage (ms) | I/O Wait (ms) | Computed Result | Execution Status |
| 2260.260 | 414725.00 | 422486.00 | 1557.60 | FFFTFTFFFFFFFFFF | normal |
Execution Chart
We display below the execution chart for this examination (boot time has been removed).
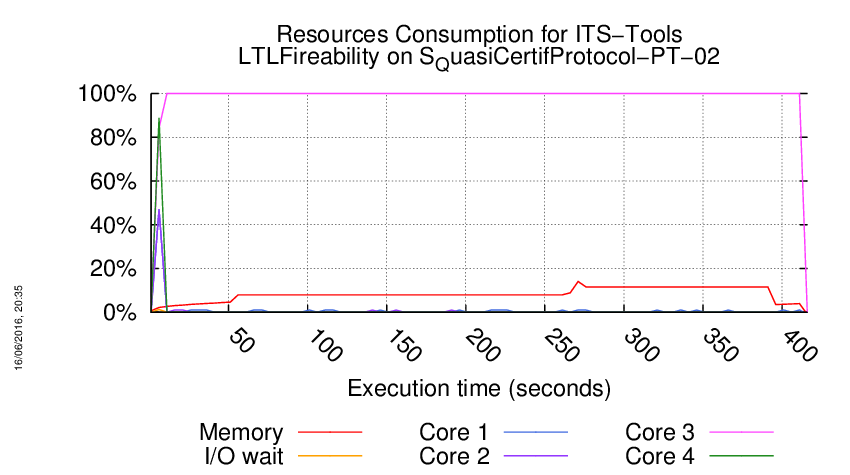
Trace from the execution
Waiting for the VM to be ready (probing ssh)
.................
=====================================================================
Generated by BenchKit 2-2979
Executing tool itstools
Input is S_QuasiCertifProtocol-PT-02, examination is LTLFireability
Time confinement is 3600 seconds
Memory confinement is 16384 MBytes
Number of cores is 4
Run identifier is r181kn-smll-146444110300078
=====================================================================
--------------------
content from stdout:
=== Data for post analysis generated by BenchKit (invocation template)
The expected result is a vector of booleans
BOOL_VECTOR
here is the order used to build the result vector(from text file)
FORMULA_NAME QuasiCertifProtocol-COL-02-LTLFireability-0
FORMULA_NAME QuasiCertifProtocol-COL-02-LTLFireability-1
FORMULA_NAME QuasiCertifProtocol-COL-02-LTLFireability-10
FORMULA_NAME QuasiCertifProtocol-COL-02-LTLFireability-11
FORMULA_NAME QuasiCertifProtocol-COL-02-LTLFireability-12
FORMULA_NAME QuasiCertifProtocol-COL-02-LTLFireability-13
FORMULA_NAME QuasiCertifProtocol-COL-02-LTLFireability-14
FORMULA_NAME QuasiCertifProtocol-COL-02-LTLFireability-15
FORMULA_NAME QuasiCertifProtocol-COL-02-LTLFireability-2
FORMULA_NAME QuasiCertifProtocol-COL-02-LTLFireability-3
FORMULA_NAME QuasiCertifProtocol-COL-02-LTLFireability-4
FORMULA_NAME QuasiCertifProtocol-COL-02-LTLFireability-5
FORMULA_NAME QuasiCertifProtocol-COL-02-LTLFireability-6
FORMULA_NAME QuasiCertifProtocol-COL-02-LTLFireability-7
FORMULA_NAME QuasiCertifProtocol-COL-02-LTLFireability-8
FORMULA_NAME QuasiCertifProtocol-COL-02-LTLFireability-9
=== Now, execution of the tool begins
BK_START 1464457564431
its-ltl command run as :
/home/mcc/BenchKit/eclipse/plugins/fr.lip6.move.gal.itstools.binaries_1.0.0.201605191313/bin/its-ltl-linux64 --gc-threshold 2000000 -i /home/mcc/execution/LTLFireability.gal -t CGAL -LTL /home/mcc/execution/LTLFireability.ltl -c -stutter-deadlock
Read 16 LTL properties
Checking formula 0 : !((G(X("a2>=1"))))
Formula 0 simplified : !GX"a2>=1"
4 unique states visited
4 strongly connected components in search stack
4 transitions explored
4 items max in DFS search stack
62 ticks for the emptiness check
Model ,|S| ,Time ,Mem(kb) ,fin. SDD ,fin. DDD ,peak SDD ,peak DDD ,SDD Hom ,SDD cache peak ,DDD Hom ,DDD cachepeak ,SHom cache
STATS,0,0.65923,40124,1,0,200,67063,141,119,2459,54364,226
an accepting run exists (use option '-e' to print it)
Formula 0 is FALSE accepting run found.
FORMULA QuasiCertifProtocol-COL-02-LTLFireability-0 FALSE TECHNIQUES DECISION_DIAGRAMS TOPOLOGICAL
Checking formula 1 : !(((G(X(X("a1>=1"))))U(X(F(G("a2>=1"))))))
Formula 1 simplified : !(GXX"a1>=1" U XFG"a2>=1")
3 unique states visited
3 strongly connected components in search stack
3 transitions explored
3 items max in DFS search stack
14 ticks for the emptiness check
Model ,|S| ,Time ,Mem(kb) ,fin. SDD ,fin. DDD ,peak SDD ,peak DDD ,SDD Hom ,SDD cache peak ,DDD Hom ,DDD cachepeak ,SHom cache
STATS,0,0.799384,44176,1,0,305,78869,148,244,2459,77100,598
an accepting run exists (use option '-e' to print it)
Formula 1 is FALSE accepting run found.
FORMULA QuasiCertifProtocol-COL-02-LTLFireability-1 FALSE TECHNIQUES DECISION_DIAGRAMS TOPOLOGICAL
Checking formula 2 : !(((X(F(X(((((("n9_2_2>=1")&&("n9_1_2>=1"))&&("n9_0_2>=1"))&&("c1_2>=1"))||(((("n9_2_1>=1")&&("n9_1_1>=1"))&&("n9_0_1>=1"))&&("c1_1>=1")))||(((("n9_2_0>=1")&&("n9_1_0>=1"))&&("n9_0_0>=1"))&&("c1_0>=1"))))))U(F(G(G("a4>=1"))))))
Formula 2 simplified : !(XFX(("c1_2>=1" & "n9_0_2>=1" & "n9_1_2>=1" & "n9_2_2>=1") | ("c1_1>=1" & "n9_0_1>=1" & "n9_1_1>=1" & "n9_2_1>=1") | ("c1_0>=1" & "n9_0_0>=1" & "n9_1_0>=1" & "n9_2_0>=1")) U FG"a4>=1")
2 unique states visited
2 strongly connected components in search stack
2 transitions explored
2 items max in DFS search stack
2 ticks for the emptiness check
Model ,|S| ,Time ,Mem(kb) ,fin. SDD ,fin. DDD ,peak SDD ,peak DDD ,SDD Hom ,SDD cache peak ,DDD Hom ,DDD cachepeak ,SHom cache
STATS,0,0.948975,47388,1,0,407,80232,161,384,2460,81347,1005
an accepting run exists (use option '-e' to print it)
Formula 2 is FALSE accepting run found.
FORMULA QuasiCertifProtocol-COL-02-LTLFireability-2 FALSE TECHNIQUES DECISION_DIAGRAMS TOPOLOGICAL
Checking formula 3 : !((F(X((G("Astart>=1"))U(G(((("Sstart_2>=1")&&("n1_2>=1"))||(("n1_1>=1")&&("Sstart_1>=1")))||(("Sstart_0>=1")&&("n1_0>=1"))))))))
Formula 3 simplified : !FX(G"Astart>=1" U G(("Sstart_2>=1" & "n1_2>=1") | ("Sstart_1>=1" & "n1_1>=1") | ("Sstart_0>=1" & "n1_0>=1")))
3 unique states visited
3 strongly connected components in search stack
3 transitions explored
3 items max in DFS search stack
4 ticks for the emptiness check
Model ,|S| ,Time ,Mem(kb) ,fin. SDD ,fin. DDD ,peak SDD ,peak DDD ,SDD Hom ,SDD cache peak ,DDD Hom ,DDD cachepeak ,SHom cache
STATS,0,0.985096,48828,1,0,484,82137,219,511,2502,86331,1390
an accepting run exists (use option '-e' to print it)
Formula 3 is FALSE accepting run found.
FORMULA QuasiCertifProtocol-COL-02-LTLFireability-3 FALSE TECHNIQUES DECISION_DIAGRAMS TOPOLOGICAL
Checking formula 4 : !((X((X(F(((("n4_0>=1")&&("n4_1>=1"))&&("n4_2>=1"))&&("a3>=1"))))U("a2>=1"))))
Formula 4 simplified : !X(XF("a3>=1" & "n4_0>=1" & "n4_1>=1" & "n4_2>=1") U "a2>=1")
8 unique states visited
8 strongly connected components in search stack
8 transitions explored
8 items max in DFS search stack
2 ticks for the emptiness check
Model ,|S| ,Time ,Mem(kb) ,fin. SDD ,fin. DDD ,peak SDD ,peak DDD ,SDD Hom ,SDD cache peak ,DDD Hom ,DDD cachepeak ,SHom cache
STATS,0,1.00554,49372,1,0,549,83931,241,630,2515,92553,1607
an accepting run exists (use option '-e' to print it)
Formula 4 is FALSE accepting run found.
FORMULA QuasiCertifProtocol-COL-02-LTLFireability-4 FALSE TECHNIQUES DECISION_DIAGRAMS TOPOLOGICAL
Checking formula 5 : !((X(F(G(G(F(((((("n8_0_2>=1")&&("n8_0_0>=1"))&&("n8_0_1>=1"))&&("s5_0>=1"))||(((("n8_2_2>=1")&&("n8_2_0>=1"))&&("n8_2_1>=1"))&&("s5_2>=1")))||(((("n8_1_1>=1")&&("n8_1_2>=1"))&&("s5_1>=1"))&&("n8_1_0>=1")))))))))
Formula 5 simplified : !XFGF(("n8_0_0>=1" & "n8_0_1>=1" & "n8_0_2>=1" & "s5_0>=1") | ("n8_2_0>=1" & "n8_2_1>=1" & "n8_2_2>=1" & "s5_2>=1") | ("n8_1_0>=1" & "n8_1_1>=1" & "n8_1_2>=1" & "s5_1>=1"))
4 unique states visited
4 strongly connected components in search stack
4 transitions explored
4 items max in DFS search stack
5 ticks for the emptiness check
Model ,|S| ,Time ,Mem(kb) ,fin. SDD ,fin. DDD ,peak SDD ,peak DDD ,SDD Hom ,SDD cache peak ,DDD Hom ,DDD cachepeak ,SHom cache
STATS,0,1.32984,50828,1,0,609,90065,315,675,2572,101605,1730
an accepting run exists (use option '-e' to print it)
Formula 5 is FALSE accepting run found.
FORMULA QuasiCertifProtocol-COL-02-LTLFireability-5 FALSE TECHNIQUES DECISION_DIAGRAMS TOPOLOGICAL
Checking formula 6 : !((X(((("n2_0>=1")&&("n2_1>=1"))&&("n2_2>=1"))&&("a1>=1"))))
Formula 6 simplified : !X("a1>=1" & "n2_0>=1" & "n2_1>=1" & "n2_2>=1")
4 unique states visited
4 strongly connected components in search stack
4 transitions explored
4 items max in DFS search stack
0 ticks for the emptiness check
Model ,|S| ,Time ,Mem(kb) ,fin. SDD ,fin. DDD ,peak SDD ,peak DDD ,SDD Hom ,SDD cache peak ,DDD Hom ,DDD cachepeak ,SHom cache
STATS,0,1.331,51088,1,0,609,90065,333,675,2585,101606,1732
an accepting run exists (use option '-e' to print it)
Formula 6 is FALSE accepting run found.
FORMULA QuasiCertifProtocol-COL-02-LTLFireability-6 FALSE TECHNIQUES DECISION_DIAGRAMS TOPOLOGICAL
Checking formula 7 : !(((F(("a4>=1")U(((("s5_0>=1")&&("malicious_reservoir>=1"))||(("malicious_reservoir>=1")&&("s5_1>=1")))||(("s5_2>=1")&&("malicious_reservoir>=1")))))U(G(F(X("a4>=1"))))))
Formula 7 simplified : !(F("a4>=1" U (("malicious_reservoir>=1" & "s5_0>=1") | ("malicious_reservoir>=1" & "s5_1>=1") | ("malicious_reservoir>=1" & "s5_2>=1"))) U GFX"a4>=1")
33 unique states visited
33 strongly connected components in search stack
34 transitions explored
33 items max in DFS search stack
4 ticks for the emptiness check
Model ,|S| ,Time ,Mem(kb) ,fin. SDD ,fin. DDD ,peak SDD ,peak DDD ,SDD Hom ,SDD cache peak ,DDD Hom ,DDD cachepeak ,SHom cache
STATS,0,1.38241,51228,1,0,609,90102,339,701,2585,108577,1825
an accepting run exists (use option '-e' to print it)
Formula 7 is FALSE accepting run found.
FORMULA QuasiCertifProtocol-COL-02-LTLFireability-7 FALSE TECHNIQUES DECISION_DIAGRAMS TOPOLOGICAL
Checking formula 8 : !((G(F(((("s5_0>=1")&&("malicious_reservoir>=1"))||(("malicious_reservoir>=1")&&("s5_1>=1")))||(("s5_2>=1")&&("malicious_reservoir>=1"))))))
Formula 8 simplified : !GF(("malicious_reservoir>=1" & "s5_0>=1") | ("malicious_reservoir>=1" & "s5_1>=1") | ("malicious_reservoir>=1" & "s5_2>=1"))
33 unique states visited
33 strongly connected components in search stack
34 transitions explored
33 items max in DFS search stack
3 ticks for the emptiness check
Model ,|S| ,Time ,Mem(kb) ,fin. SDD ,fin. DDD ,peak SDD ,peak DDD ,SDD Hom ,SDD cache peak ,DDD Hom ,DDD cachepeak ,SHom cache
STATS,0,1.41494,52376,1,0,678,95954,358,752,2596,115078,1969
an accepting run exists (use option '-e' to print it)
Formula 8 is FALSE accepting run found.
FORMULA QuasiCertifProtocol-COL-02-LTLFireability-8 FALSE TECHNIQUES DECISION_DIAGRAMS TOPOLOGICAL
Checking formula 9 : !((G(((((("s5_0>=1")&&("malicious_reservoir>=1"))||(("malicious_reservoir>=1")&&("s5_1>=1")))||(("s5_2>=1")&&("malicious_reservoir>=1")))U(((("s2_2>=1")&&("n3_2>=1"))||(("s2_1>=1")&&("n3_1>=1")))||(("s2_0>=1")&&("n3_0>=1"))))U(F(((((("n9_2_2>=1")&&("n9_1_2>=1"))&&("n9_0_2>=1"))&&("c1_2>=1"))||(((("n9_2_1>=1")&&("n9_1_1>=1"))&&("n9_0_1>=1"))&&("c1_1>=1")))||(((("n9_2_0>=1")&&("n9_1_0>=1"))&&("n9_0_0>=1"))&&("c1_0>=1")))))))
Formula 9 simplified : !G(((("malicious_reservoir>=1" & "s5_0>=1") | ("malicious_reservoir>=1" & "s5_1>=1") | ("malicious_reservoir>=1" & "s5_2>=1")) U (("n3_2>=1" & "s2_2>=1") | ("n3_1>=1" & "s2_1>=1") | ("n3_0>=1" & "s2_0>=1"))) U F(("c1_2>=1" & "n9_0_2>=1" & "n9_1_2>=1" & "n9_2_2>=1") | ("c1_1>=1" & "n9_0_1>=1" & "n9_1_1>=1" & "n9_2_1>=1") | ("c1_0>=1" & "n9_0_0>=1" & "n9_1_0>=1" & "n9_2_0>=1")))
3 unique states visited
3 strongly connected components in search stack
3 transitions explored
3 items max in DFS search stack
4 ticks for the emptiness check
Model ,|S| ,Time ,Mem(kb) ,fin. SDD ,fin. DDD ,peak SDD ,peak DDD ,SDD Hom ,SDD cache peak ,DDD Hom ,DDD cachepeak ,SHom cache
STATS,0,409.199,301484,1,0,761,100990,432,809,2653,121399,2119
an accepting run exists (use option '-e' to print it)
Formula 9 is FALSE accepting run found.
FORMULA QuasiCertifProtocol-COL-02-LTLFireability-9 FALSE TECHNIQUES DECISION_DIAGRAMS TOPOLOGICAL
Checking formula 10 : !((F(G(F(F(G(((("malicious_reservoir>=1")&&("Sstart_1>=1"))||(("malicious_reservoir>=1")&&("Sstart_2>=1")))||(("malicious_reservoir>=1")&&("Sstart_0>=1")))))))))
Formula 10 simplified : !FGFG(("Sstart_1>=1" & "malicious_reservoir>=1") | ("Sstart_2>=1" & "malicious_reservoir>=1") | ("Sstart_0>=1" & "malicious_reservoir>=1"))
2 unique states visited
2 strongly connected components in search stack
2 transitions explored
2 items max in DFS search stack
3 ticks for the emptiness check
Model ,|S| ,Time ,Mem(kb) ,fin. SDD ,fin. DDD ,peak SDD ,peak DDD ,SDD Hom ,SDD cache peak ,DDD Hom ,DDD cachepeak ,SHom cache
STATS,0,409.237,301500,1,0,835,103396,458,936,2670,126552,2509
an accepting run exists (use option '-e' to print it)
Formula 10 is FALSE accepting run found.
FORMULA QuasiCertifProtocol-COL-02-LTLFireability-10 FALSE TECHNIQUES DECISION_DIAGRAMS TOPOLOGICAL
Checking formula 11 : !(((F(((((("n9_2_2>=1")&&("n9_1_2>=1"))&&("n9_0_2>=1"))&&("c1_2>=1"))||(((("n9_2_1>=1")&&("n9_1_1>=1"))&&("n9_0_1>=1"))&&("c1_1>=1")))||(((("n9_2_0>=1")&&("n9_1_0>=1"))&&("n9_0_0>=1"))&&("c1_0>=1"))))U("Astart>=1")))
Formula 11 simplified : !(F(("c1_2>=1" & "n9_0_2>=1" & "n9_1_2>=1" & "n9_2_2>=1") | ("c1_1>=1" & "n9_0_1>=1" & "n9_1_1>=1" & "n9_2_1>=1") | ("c1_0>=1" & "n9_0_0>=1" & "n9_1_0>=1" & "n9_2_0>=1")) U "Astart>=1")
1 unique states visited
0 strongly connected components in search stack
0 transitions explored
1 items max in DFS search stack
0 ticks for the emptiness check
Model ,|S| ,Time ,Mem(kb) ,fin. SDD ,fin. DDD ,peak SDD ,peak DDD ,SDD Hom ,SDD cache peak ,DDD Hom ,DDD cachepeak ,SHom cache
STATS,0,409.647,301500,1,0,835,103396,513,936,2722,126552,2513
no accepting run found
Formula 11 is TRUE no accepting run found.
FORMULA QuasiCertifProtocol-COL-02-LTLFireability-11 TRUE TECHNIQUES DECISION_DIAGRAMS TOPOLOGICAL
Checking formula 12 : !((G(X(((("s3_2>=1")&&("n5_2>=1"))||(("s3_1>=1")&&("n5_1>=1")))||(("s3_0>=1")&&("n5_0>=1"))))))
Formula 12 simplified : !GX(("n5_2>=1" & "s3_2>=1") | ("n5_1>=1" & "s3_1>=1") | ("n5_0>=1" & "s3_0>=1"))
4 unique states visited
4 strongly connected components in search stack
4 transitions explored
4 items max in DFS search stack
0 ticks for the emptiness check
Model ,|S| ,Time ,Mem(kb) ,fin. SDD ,fin. DDD ,peak SDD ,peak DDD ,SDD Hom ,SDD cache peak ,DDD Hom ,DDD cachepeak ,SHom cache
STATS,0,409.651,301500,1,0,835,103396,564,936,2765,126555,2518
an accepting run exists (use option '-e' to print it)
Formula 12 is FALSE accepting run found.
FORMULA QuasiCertifProtocol-COL-02-LTLFireability-12 FALSE TECHNIQUES DECISION_DIAGRAMS TOPOLOGICAL
Checking formula 13 : !(("Astart>=1"))
Formula 13 simplified : !"Astart>=1"
1 unique states visited
0 strongly connected components in search stack
0 transitions explored
1 items max in DFS search stack
0 ticks for the emptiness check
Model ,|S| ,Time ,Mem(kb) ,fin. SDD ,fin. DDD ,peak SDD ,peak DDD ,SDD Hom ,SDD cache peak ,DDD Hom ,DDD cachepeak ,SHom cache
STATS,0,409.651,301500,1,0,835,103396,564,936,2765,126555,2518
no accepting run found
Formula 13 is TRUE no accepting run found.
FORMULA QuasiCertifProtocol-COL-02-LTLFireability-13 TRUE TECHNIQUES DECISION_DIAGRAMS TOPOLOGICAL
Checking formula 14 : !((X(G(X(("a4>=1")U(((("s3_2>=1")&&("n5_2>=1"))||(("s3_1>=1")&&("n5_1>=1")))||(("s3_0>=1")&&("n5_0>=1"))))))))
Formula 14 simplified : !XGX("a4>=1" U (("n5_2>=1" & "s3_2>=1") | ("n5_1>=1" & "s3_1>=1") | ("n5_0>=1" & "s3_0>=1")))
34 unique states visited
34 strongly connected components in search stack
35 transitions explored
34 items max in DFS search stack
0 ticks for the emptiness check
Model ,|S| ,Time ,Mem(kb) ,fin. SDD ,fin. DDD ,peak SDD ,peak DDD ,SDD Hom ,SDD cache peak ,DDD Hom ,DDD cachepeak ,SHom cache
STATS,0,409.658,301500,1,0,835,103440,570,936,2769,126610,2522
an accepting run exists (use option '-e' to print it)
Formula 14 is FALSE accepting run found.
FORMULA QuasiCertifProtocol-COL-02-LTLFireability-14 FALSE TECHNIQUES DECISION_DIAGRAMS TOPOLOGICAL
Checking formula 15 : !((F(F(((("n2_0>=1")&&("n2_1>=1"))&&("n2_2>=1"))&&("a1>=1")))))
Formula 15 simplified : !F("a1>=1" & "n2_0>=1" & "n2_1>=1" & "n2_2>=1")
2 unique states visited
2 strongly connected components in search stack
2 transitions explored
2 items max in DFS search stack
1 ticks for the emptiness check
Model ,|S| ,Time ,Mem(kb) ,fin. SDD ,fin. DDD ,peak SDD ,peak DDD ,SDD Hom ,SDD cache peak ,DDD Hom ,DDD cachepeak ,SHom cache
STATS,0,409.664,301504,1,0,845,103775,576,954,2769,127359,2578
an accepting run exists (use option '-e' to print it)
Formula 15 is FALSE accepting run found.
FORMULA QuasiCertifProtocol-COL-02-LTLFireability-15 FALSE TECHNIQUES DECISION_DIAGRAMS TOPOLOGICAL
BK_STOP 1464457979156
--------------------
content from stderr:
+ export BINDIR=/home/mcc/BenchKit/
+ BINDIR=/home/mcc/BenchKit/
++ pwd
+ export MODEL=/home/mcc/execution
+ MODEL=/home/mcc/execution
+ [[ LTLFireability = StateSpace ]]
+ /home/mcc/BenchKit//runeclipse.sh /home/mcc/execution LTLFireability -its
+ ulimit -s 65536
+ java -Dosgi.requiredJavaVersion=1.6 -XX:MaxPermSize=512m -Xss8m -Xms40m -Xmx8192m -Declipse.pde.launch=true -Dfile.encoding=UTF-8 -classpath /home/mcc/BenchKit//eclipse/plugins/org.eclipse.equinox.launcher_1.3.100.v20150511-1540.jar org.eclipse.equinox.launcher.Main -application fr.lip6.move.gal.application.pnmcc -data /home/mcc/BenchKit//workspace -os linux -ws gtk -arch x86_64 -nl en_US -consoleLog -pnfolder /home/mcc/execution -examination LTLFireability -z3path /home/mcc/BenchKit//z3/bin/z3 -yices2path /home/mcc/BenchKit//yices/bin/yices -its
Java HotSpot(TM) 64-Bit Server VM warning: ignoring option MaxPermSize=512m; support was removed in 8.0
May 28, 2016 5:46:08 PM fr.lip6.move.gal.application.Application transformPNML
INFO: Parsing pnml file : /home/mcc/execution/model.pnml
May 28, 2016 5:46:08 PM fr.lip6.move.gal.nupn.PTNetReader loadFromXML
INFO: Load time of PNML (sax parser for PT used): 41 ms
May 28, 2016 5:46:08 PM fr.lip6.move.gal.pnml.togal.PTGALTransformer handlePage
INFO: Transformed 86 places.
May 28, 2016 5:46:08 PM fr.lip6.move.gal.pnml.togal.PTGALTransformer handlePage
INFO: Transformed 56 transitions.
May 28, 2016 5:46:08 PM fr.lip6.move.gal.instantiate.GALRewriter flatten
INFO: Flatten gal took : 76 ms
May 28, 2016 5:46:08 PM fr.lip6.move.serialization.SerializationUtil systemToFile
INFO: Time to serialize gal into /home/mcc/execution/LTLFireability.gal : 175 ms
May 28, 2016 5:46:08 PM fr.lip6.move.serialization.SerializationUtil serializePropertiesForITSLTLTools
INFO: Time to serialize properties into /home/mcc/execution/LTLFireability.ltl : 3 ms
Sequence of Actions to be Executed by the VM
This is useful if one wants to reexecute the tool in the VM from the submitted image disk.
set -x
# this is for BenchKit: configuration of major elements for the test
export BK_INPUT="S_QuasiCertifProtocol-PT-02"
export BK_EXAMINATION="LTLFireability"
export BK_TOOL="itstools"
export BK_RESULT_DIR="/root/BK_RESULTS/OUTPUTS"
export BK_TIME_CONFINEMENT="3600"
export BK_MEMORY_CONFINEMENT="16384"
# this is specific to your benchmark or test
export BIN_DIR="$HOME/BenchKit/bin"
# remove the execution directoty if it exists (to avoid increse of .vmdk images)
if [ -d execution ] ; then
rm -rf execution
fi
tar xzf /home/mcc/BenchKit/INPUTS/S_QuasiCertifProtocol-PT-02.tgz
mv S_QuasiCertifProtocol-PT-02 execution
# this is for BenchKit: explicit launching of the test
cd execution
echo "====================================================================="
echo " Generated by BenchKit 2-2979"
echo " Executing tool itstools"
echo " Input is S_QuasiCertifProtocol-PT-02, examination is LTLFireability"
echo " Time confinement is $BK_TIME_CONFINEMENT seconds"
echo " Memory confinement is 16384 MBytes"
echo " Number of cores is 4"
echo " Run identifier is r181kn-smll-146444110300078"
echo "====================================================================="
echo
echo "--------------------"
echo "content from stdout:"
echo
echo "=== Data for post analysis generated by BenchKit (invocation template)"
echo
if [ "LTLFireability" = "UpperBounds" ] ; then
echo "The expected result is a vector of positive values"
echo NUM_VECTOR
elif [ "LTLFireability" != "StateSpace" ] ; then
echo "The expected result is a vector of booleans"
echo BOOL_VECTOR
else
echo "no data necessary for post analysis"
fi
echo
if [ -f "LTLFireability.txt" ] ; then
echo "here is the order used to build the result vector(from text file)"
for x in $(grep Property LTLFireability.txt | cut -d ' ' -f 2 | sort -u) ; do
echo "FORMULA_NAME $x"
done
elif [ -f "LTLFireability.xml" ] ; then # for cunf (txt files deleted;-)
echo echo "here is the order used to build the result vector(from xml file)"
for x in $(grep '
echo "FORMULA_NAME $x"
done
fi
echo
echo "=== Now, execution of the tool begins"
echo
echo -n "BK_START "
date -u +%s%3N
echo
timeout -s 9 $BK_TIME_CONFINEMENT bash -c "/home/mcc/BenchKit/BenchKit_head.sh 2> STDERR ; echo ; echo -n \"BK_STOP \" ; date -u +%s%3N"
if [ $? -eq 137 ] ; then
echo
echo "BK_TIME_CONFINEMENT_REACHED"
fi
echo
echo "--------------------"
echo "content from stderr:"
echo
cat STDERR ;

